Introduction to Email
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Securing Your Email in 13 Steps: the Email Security Checklist Handbook Securing Your Email in 13 Steps
HANDBOOK Securing Your Email in 13 Steps: The Email Security Checklist handbook Securing Your Email in 13 Steps overview You’ve hardened your servers, locked down your website and are ready to take on the internet. But all your hard work was in vain, because someone fell for a phishing email and wired money to a scammer, while another user inadvertently downloaded and installed malware from an email link that opened a backdoor into the network. Email is as important as the website when it comes to security. As a channel for social engineering, malware delivery and resource exploitation, a combination of best practices and user education should be enacted to reduce the risk of an email-related compromise. By following this 13 step checklist, you can make your email configuration resilient to the most common attacks and make sure it stays that way. 2 @UpGuard | UpGuard.com handbook Securing Your Email in 13 Steps 1. Enable SPF How do you know if an email is really from who it says it’s from? There are a couple of ways to answer this question, and Sender Policy Framework (SPF) is one. SPF works by publishing a DNS record of which servers are allowed to send email from a specific domain. 1. An SPF enabled email server receives an email from [email protected] 2. The email server looks up example.com and reads the SPF TXT record in DNS. 3. If the originating server of the email matches one of the allowed servers in the SPF record, the message is accepted. -

Imail V12 Web Client Help
Ipswitch, Inc. Web: www.imailserver.com 753 Broad Street Phone: 706-312-3535 Suite 200 Fax: 706-868-8655 Augusta, GA 30901-5518 Copyrights ©2011 Ipswitch, Inc. All rights reserved. IMail Server – Web Client Help This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the expressed prior written consent of Ipswitch, Inc. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc. also assumes no liability for damages resulting from the use of the information contained in this document. Ipswitch Collaboration Suite (ICS), the Ipswitch Collaboration Suite (ICS) logo, IMail, the IMail logo, WhatsUp, the WhatsUp logo, WS_FTP, the WS_FTP logos, Ipswitch Instant Messaging (IM), the Ipswitch Instant Messaging (IM) logo, Ipswitch, and the Ipswitch logo are trademarks of Ipswitch, Inc. Other products and their brands or company names are or may be trademarks or registered trademarks, and are the property of their respective companies. Update History December 2011 v12 April 2011 v11.5 October 2010 v11.03 May 2010 v11.02 Contents CHAPTER 1 Introduction to IMail Web Client About Ipswitch Web Messaging Help .................................................................................................................. -
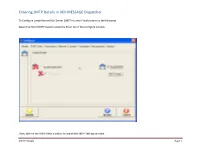
Entering SMTP Details in REV MESSAGE Dispatcher
Entering SMTP Details in REV MESSAGE Dispatcher. To Configure using Internet Mail Server (SMTP) to send Emails please do the following. Select the Email (SMTP) option under the Email tab in the Configure window. Then, click on the SMTP Details button to launch the SMTP Settings window. SMTP details Page 1 Entering SMTP Details in REV MESSAGE Dispatcher. In the User Information enter the Sender Name and the Sender E-mail Address. This is what will appear in the ‘From:’ field when the email is received. For example, we use Message Dispatcher for the Name and [email protected] as the E-mail Address SMTP details Page 2 Entering SMTP Details in REV MESSAGE Dispatcher. Example of what it looks like when the email is viewed. SMTP details Page 3 Entering SMTP Details in REV MESSAGE Dispatcher. The next step is to enter the Outgoing Mail Server SMTP (Simple Mail Transport Protocol) address. You can also use an IP address instead, i.e. 118.208.34.220 SMTP details Page 4 Entering SMTP Details in REV MESSAGE Dispatcher. The final step is to enter your outgoing email account and password information that provided to you by your ISP or Network Administrator. SMTP details Page 5 Entering SMTP Details in REV MESSAGE Dispatcher. There’re also Options for Email Attachment Encoding (MIME and UUEncode) and Email Message Format (HTML Mail Format). To send out long URL link in the email (like we have with the Web Interface link) we recommend you to select the HTML Mail Format option. Now, we just need to click on the Accept button to save these settings SMTP details Page 6 . -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
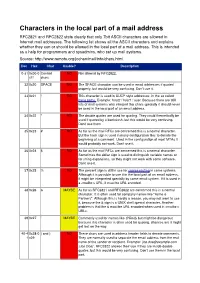
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -

Going Live Tutorial Contents
Going Live Tutorial Contents Going Live with Your Online Business 1 Let’s Get Started 2 Domain names, IP addresses and DNS 2 Some advanced terminology 3 Going Live Step by Step 5 1. Getting a domain name 5 2. Setting up your domain & its email settings 5 2a. Adding your domain name to the system 5 2b. Email settings for your domain 7 3. Setting up email 8 3a. Creating mailboxes 8 3b. Creating aliases 8 4. Pointing your domain to us 9 5. Setting up your email client 10 For Advanced Users - using an external DNS service 11 Going Live with Your Online Business When your site is looking hot and you’re ready to rock, you’ll want to take your site out of trial mode and make it live. Taking a site live means a few things: You’re ready to pay for your site. You’re ready to buy a domain name (www.mybusiness.com) and allow people to access your site by typing that address into their web browser. OR you’ve got a domain name that currently goes to your old site, and you want to switch it over to your brand-spanking-new online business. Who is this for? This guide is for anyone who’s ready to take their site live and show it off to the world! Some sections can be skipped by those with more advanced knowledge - these sections will be marked accordingly. Business Catalyst • Going Live Tutorial 1 Let’s Get Started Domain names, IP addresses and DNS If you already know what a domain name is, what an IP address is and how DNS works, you can skip this section. -

M3AAWG Email Authentication Recommended Best Practices
Messaging, Malware and Mobile Anti-Abuse Working Group M3AAWG Email Authentication Recommended Best Practices September 2020 The reference URL for this document is: https://www.m3aawg.org/sites/default/files/m3aawg-email-authentication-recommended-best-practices- 09-2020.pdf For information on M3AAWG please see www.m3aawg.org. Table of Contents 1. Abstract ..................................................................................................................................................2 2. Introduction ............................................................................................................................................2 3. Scope ......................................................................................................................................................2 4. Executive Summary: A Checklist ...........................................................................................................4 5. Authentication Recommendation Discussion .........................................................................................5 5.1. Senders ...........................................................................................................................................5 5.2. Intermediaries .................................................................................................................................6 5.3. Receivers ........................................................................................................................................7 -

M3AAWG Best Practices for Unicode Abuse Prevention February 2016
Messaging, Malware and Mobile Anti-Abuse Working Group M3AAWG Best Practices for Unicode Abuse Prevention February 2016 Executive Summary For years, visually confusable Unicode characters – e.g., using the Greek omicron (‘ο’ U+03BF) in place of a Latin ‘o’ – have provided the potential to mislead users. Because most functional elements, like links and addresses, were previously limited to ASCII, abuse remained peripheral. However, the scope and definition of this abuse are poised to change with the advent of International Domain Names (IDNs), Internationalized Top-Level Domains (TLDs), and Email Address Internationalization as these non-ASCII and non-Latin characters gain in popularity. This document outlines M3AAWG best practices to curtail the Unicode abuse potential of such spoofing, while supporting the legitimate use cases. The intended audiences for these practices are: email service providers, Internet service providers, and the operators of Software as a Service or others in relations to other Internet-connected applications. A brief tutorial explaining how Unicode characters are used to perpetuate abuse can be found in M3AAWG Unicode Abuse Overview and Tutorial paper. This paper can be downloaded from the Best Practices section of the M3AAWG website. I. Background The M3AAWG best practices approach is to disallow certain characters not in common usage, as well as the combining of confusable scripts within a single label, with exceptions made only for certain visually distinct combinations found in legitimate usage. The intent of this exacting strategy is to inhibit suspicious combinations from taking hold by legitimate users, while ensuring a clean delineation of what constitutes abuse. For consistency and defensibility, these strategies are based on the Unicode Consortium’s standardized “Restriction Levels” definition1, which takes into account expected legitimate combinations of character sets. -

Beginner's Guide to Domain Names
Beginner’s Guide to D O M A I N N A M E S THIS IS ONE OF A SERIES OF GUIDES ABOUT ISSUES OF IMPORTANCE TO INTERNET USERS. EDUCATING NEW USERS ABOUT INTERNET ISSUES IS PART OF ICANN’S MISSION TO ENSURE A STABLE, SECURE, GLOBALLY INTEROPERABLE INTERNET. ICANN PREPARED THIS GUIDE AT THE REQUEST OF THE AT-LARGE ADVISORY COMMITTEE, THE VOICE OF THE INDIVIDUAL INTERNET USER AT ICANN. WE SINCERELY HOPE YOU FIND IT HELPFUL. TA b l E O f C ontents Introduction.................................................................................................................................................................................................................................2 Domain Names...........................................................................................................................................................................................................................3 1 What.is.a.domain.name.and.how.does.it.work?...........................................................................................................................................3 2 ...How.do.I.register.a.domain.name?.......................................................................................................................................................................3 . 3 ...How.do.I.select.a.domain.name.to.register?..................................................................................................................................................4 4 What.is.a.registrar.and.how.do.I.select.one?...................................................................................................................................................5 -

XEP-0157: Contact Addresses for XMPP Services
XEP-0157: Contact Addresses for XMPP Services Peter Saint-Andre Jacek Konieczny mailto:xsf@stpeter:im mailto:jajcus@jajcus:net xmpp:peter@jabber:org xmpp:jajcus@jabber:bnet:pl http://stpeter:im/ 2021-03-04 Version 1.1.1 Status Type Short Name Active Informational N/A This document defines a method for specifying contact addresses related to an XMPP service. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. Warranty ## NOTE WELL: This Specification is provided on an ”AS IS” BASIS, WITHOUT WARRANTIES OR CONDI- TIONS OF ANY KIND, express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE.