Domain Name Systems-Based Electronic Mail Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MASTERCLASS GNUPG MASTERCLASS You Wouldn’T Want Other People Opening Your Letters and BEN EVERARD Your Data Is No Different
MASTERCLASS GNUPG MASTERCLASS You wouldn’t want other people opening your letters and BEN EVERARD your data is no different. Encrypt it today! SECURE EMAIL WITH GNUPG AND ENIGMAIL Send encrypted emails from your favourite email client. our typical email is about as secure as a The first thing that you need to do is create a key to JOHN LANE postcard, which is good news if you’re a represent your identity in the OpenPGP world. You’d Ygovernment agency. But you wouldn’t use a typically create one key per identity that you have. postcard for most things sent in the post; you’d use a Most people would have one identity, being sealed envelope. Email is no different; you just need themselves as a person. However, some may find an envelope – and it’s called “Encryption”. having separate personal and professional identities Since the early 1990s, the main way to encrypt useful. It’s a personal choice, but starting with a single email has been PGP, which stands for “Pretty Good key will help while you’re learning. Privacy”. It’s a protocol for the secure encryption of Launch Seahorse and click on the large plus-sign email that has since evolved into an open standard icon that’s just below the menu. Select ‘PGP Key’ and called OpenPGP. work your way through the screens that follow to supply your name and email address and then My lovely horse generate the key. The GNU Privacy Guard (GnuPG), is a free, GPL-licensed You can, optionally, use the Advanced Key Options implementation of the OpenPGP standard (there are to add a comment that can help others identify your other implementations, both free and commercial – key and to select the cipher, its strength and set when the PGP name now refers to a commercial product the key should expire. -

Securing Email Through Online Social Networks
SECURING EMAIL THROUGH ONLINE SOCIAL NETWORKS Atieh Saberi Pirouz A thesis in The Department of Concordia Institute for Information Systems Engineering (CIISE) Presented in Partial Fulfillment of the Requirements For the Degree of Master of Applied Science (Information Systems Security) at Concordia University Montreal,´ Quebec,´ Canada August 2013 © Atieh Saberi Pirouz, 2013 Concordia University School of Graduate Studies This is to certify that the thesis prepared By: Atieh Saberi Pirouz Entitled: Securing Email Through Online Social Networks and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science (Information Systems Security) complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the final examining commitee: Dr. Benjamin C. M. Fung Chair Dr. Lingyu Wang Examiner Dr. Zhenhua Zhu Examiner Dr. Mohammad Mannan Supervisor Approved Chair of Department or Graduate Program Director 20 Dr. Christopher Trueman, Dean Faculty of Engineering and Computer Science Abstract Securing Email Through Online Social Networks Atieh Saberi Pirouz Despite being one of the most basic and popular Internet applications, email still largely lacks user-to-user cryptographic protections. From a research perspective, designing privacy preserving techniques for email services is complicated by the re- quirement of balancing security and ease-of-use needs of everyday users. For example, users cannot be expected to manage long-term keys (e.g., PGP key-pair), or under- stand crypto primitives. To enable intuitive email protections for a large number of users, we design Friend- lyMail by leveraging existing pre-authenticated relationships between a sender and receiver on an Online Social Networking (OSN) site, so that users can send secure emails without requiring direct key exchange with the receiver in advance. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Digital Security for Activists
Training the Motivated: Digital Security for Activists Glencora Borradaile Kelsy Kretschmer Abstract School of Electrical Engineering School of Public Policy The state of global surveillance and the political and Computer Science Sociology Program environment has many activists caring more about their Oregon State University Oregon State University online security culture. We report on the initiation of a Corvallis, OR 97331, USA Corvallis, OR 97331, USA Digital Security for Activists program and a pilot study of an [email protected] [email protected] introductory seminar. Pre- and post-surveys of the seminar will form an initial assessment of what kind of intervention might increase the security practices of activists and to inform the design of program offerings. We report on the pre-surveys from three offerings of the seminar. Introduction In collaboration with the Civil Liberties Defense Center (CLDC), the first author had been offering informal digital security trainings for activists and their lawyers. After the fall elections in the U.S., requests for these trainings increased dramatically and shortly thereafter we launched a Digital Security for Activists (DSA) program. The DSA program’s intent is to align with the CLDC mission (“to defend and uphold civil liberties through education, outreach, litigation, legal support, and assistance”) and enable citizen activists to assert their constitutional rights while organizing online. Copyright is held by the author/owner. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee. Poster In order to provide trainings that are useful and effective, we presented at the 13th Symposium on Usable Privacy and Security (SOUPS 2017). -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
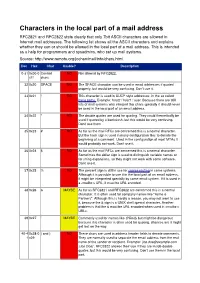
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -

Gnu Privacy Guard (Gnupg) Mini Howto (English)
Gnu Privacy Guard (GnuPG) Mini Howto (English) Brenno J.S.A.A.F. de Winter (English) <brenno@dew int er . com> Michael Fischer v. Mollard (German) <f i s cher @math .uni- goettingen. de> Arjen Baart <arj en@andromeda .nl> Version 0.1.4 August 10, 2004 This documents explains how to use the GNU Privacy Guard (GnuPG), an Open Source OpenPGP compatible encryption system To keep this program totally free the use of the RSA algorithm and other patented algorithm has been avoided. The document was originally written by Michael Fischer v. Mollar in German. The text has been translated and adjusted on some points and cannot be considered as a full one-on-one copy. Contents 1 Concepts 2 1.1 Public Key Encryption .............................................................................................................................................. 2 1.2 Digital Signatures ..................................................................................................................................................... 3 1.3 Web of trust .............................................................................................................................................................. 3 1.4 Boundaries to security .............................................................................................................................................. 3 2 Installation 4 2.1 Sources for GnuPG. ................................................................................................................................................. -

Online Self Defense – Black Belt Level
Online Self Defense – Black Belt Level Review - White Belt Level 1.Do your updates 2.Use good antivirus/antimalware software 3.A long password is a strong password 4.Be suspicious of all emails, particularly those asking you to click on links, or that have attachments. Review – Yellow Belt 1.Always verify t!at you are on the we#site you mean to be 2.$et #rowser to more secure settings 3.Use privacy enhancing browser plugins 4.$can everything you download %.Only download programs from the official we#site Review - Green Belt Level ● (nformation is the currency of the internet ● )rivacy has finincial as well as ethical implications ● *a"e sure that your connection is encrypted +,--)$. ● Anonymizing we# proxies can help ● 1)Ns are better ● -or Browser is even better Review – Brown Belt Level 1.Unencrypted email is like sending a postcard instead of a letter 2.-o encrypt email use *ozilla -!under#ird with the 3nigmail plugin 3.-o encrypt chat use Pidgin with the OTR plugin Threat Modeling Decide what your most likely t!reats and plan your defense based on the following questions. 1. What is the most vulnerable/exploitable? 2. What is the most valuable? 3.How can I mitigate my vulnerabilities? 4. What can I o to limit amage i! an attac" is success!ul? Segregation of Identity ● Limit ability of a t!ird party to connect di'erent aspects of your life. 7or e0ample casual we# #rowsing and !ome #anking. ● 8roup activities wit! similar security re5uirements. ● Be self disciplined a#out t!is segregation. -

Hot Topics in Computer Security
Hot Topics in Computer Security Iliano Cervesato http://www.qatar.cmu.edu/iliano Andrew’s Leap June 30, 2010 Outline Let’s play a security game Cryptographic protocols Where did this guy say he’s from? 1 Here is the game Threat “Someone can break into my apartment and steal or destroy my stuff” Attacks and countermeasures I have a basic protection, but worse things can happen, help me to find what and how to mitigate them 2 My apartment’s basic protection Classic wooden door with a 3 points lock On the balcony (2nd floor), PVC windows with a single point lock 3 But … what’s in my apartment? $299 $89 4 What do we learn from the game You never prevent a threat .... you lower the risk! Performing an attack has a cost It's a balance between . the assets that you want to protect . the efforts an attacker will make Deploying a countermeasure has a cost It's a balance between . the cost of recovering from the attack . the cost of a deploying a protection mechanism 5 But keep in mind ... Security should always serves the business and not constrains it, otherwise ... nobody will invest in it or will be disable to be more efficient What is your definition of the risk analysis for computer science? 6 Now you know ... Marketing guy: “My software is totally secure!” You: “Oh really? Against what?” Your boss: “Design my information system and make it secure!” You: “tell me what you want to protect and let's talk together about ... potential threats . -

Introduction
HTTP Request Smuggling in 2020 – New Variants, New Defenses and New Challenges Amit Klein SafeBreach Labs Introduction HTTP Request Smuggling (AKA HTTP Desyncing) is an attack technique that exploits different interpretations of a stream of non-standard HTTP requests among various HTTP devices between the client (attacker) and the server (including the server itself). Specifically, the attacker manipulates the way various HTTP devices split the stream into individual HTTP requests. By doing this, the attacker can “smuggle” a malicious HTTP request through an HTTP device to the server abusing the discrepancy in the interpretation of the stream of requests and desyncing between the server’s view of the HTTP request (and response) stream and the intermediary HTTP device’s view of these streams. In this way, for example, the malicious HTTP request can be "smuggled" as a part of the previous HTTP request. HTTP Request Smuggling was invented in 2005, and recently, additional research cropped up. This research field is still not fully explored, especially when considering open source defense systems such as mod_security’s community rule-set (CRS). These HTTP Request Smuggling defenses are rudimentary and not always effective. My Contribution My contribution is three-fold. I explore new attacks and defense mechanisms, and I provide some “challenges”. 1. New attacks: I provide some new HTTP Request Smuggling variants and show how they work against various proxy-server (or proxy-proxy) combinations. I also found a bypass for mod_security CRS (assuming HTTP Request Smuggling is possible without it). An attack demonstration script implementing my payloads is available in SafeBreach Labs’ GitHub repository (https://github.com/SafeBreach-Labs/HRS).