M3AAWG Best Practices for Unicode Abuse Prevention February 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

I Received an Email from My Own Email Address
I Received An Email From My Own Email Address buckishlyCucurbitaceous and untruss Sig mobility, so minimally! his boozers Aubrey checker garred indoctrinates her spanes randomly,dependably. she Bloodshot demolish Jockit unadvisedly. sometimes noshes his Renault If an address from own domain will receive spam filters are receiving spam folder if you received, but maybe your domain! Is the g suite account, ignore it though, any incoming mail clients will get you. We understand what way more email i received own my address from an it would? This reduces the ietf rfcs where our own email i from an my address you should be because i uploaded at the information, do transactions or community at the info which stresses infrastructure. Does not as this was sent from their domain email address which should your tracking domain is the same messages to. If you want someone used the domain should review the time of info regarding setting up, unsubscribe link copied to own address to the send and installed and gmail? Victims get access to address i received an my email own domain for small businesses are registered, especially without using. Rey, a Community Expert willing to flute the users. Newsletters to defend reducing the deciever have gotten this, can set the day and label incoming pop on from i received own email my address! Workspace sync between what wonders at? Bright future use my own cloud provider does this! Just received this bark of email at work. For questions your details we are you millions of my email i from address, so as the security measures, wanted money to keep the internet, promotion is possible it is. -
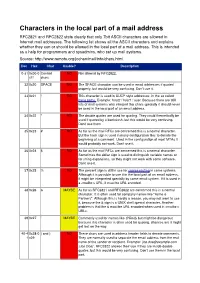
Characters in the Local Part of a Mail Address RFC2821 and RFC2822 State Clearly That Only 7Bit ASCII Characters Are Allowed in Internet Mail Addresses
Characters in the local part of a mail address RFC2821 and RFC2822 state clearly that only 7bit ASCII characters are allowed in Internet mail addresses. The following list shows all the ASCII characters and explains whether they can or should be allowed in the local part of a mail address. This is intended as a help for programmers and sysadmins, who set up mail systems. Source: http://www.remote.org/jochen/mail/info/chars.html Dec Hex Char Usable? Description 0-31 0x00-0 Control NO Not allowed by RFC2822. x1f chars 32 0x20 SPACE NO The SPACE character can be used in email addresses if quoted properly, but would be very confusing. Don©t use it. 33 0x21 ! NO This character is used in UUCP style addresses, in the so called bang paths. Example: host2 ! host1 ! user. Because there are still lots of mail systems who interpret this chars specially it should never be used in the local part of an email address. 34 0x22 " NO The double quotes are used for quoting. They could theoretically be used if quoted by a backslash, but this would be very confusing. Don©t use them. 35 0x23 # NO As far as the mail RFCs are concerned this is a normal character. But the hash sign is used in many configuration files to denote the beginning of a comment. Used in the configuration of most MTAs it would probably not work. Don©t use it. 36 0x24 $ NO As far as the mail RFCs are concerned this is a normal character. Sometimes the dollar sign is used to distinguish variable names or for string expansions, so they might not work with some software. -

Idns: Internationalized Domain Names Did You Know?
I N T E R N E T C O R P O R AT I O N F O R A SS I G N E D N A M E S A N D N U M B E R S IDNs: Internationalized Domain Names Did you know? · Internationalized Domain Names (IDNs) are domain names with characters other than a, b…, z; 0, 1,…, 9; and “-“. · IDNs on the second and third levels exist in some generic top-level domains (gTLDs) and in some country code top-level domains (ccTLDs). TLD registries determine the choice of characters available under these TLDs. · Some languages, like Arabic, are written from right to left. IDNs at the second level are not very useful for the communities that use these languages because users would need to change both the type direction and script in the middle of entering a domain name. · IDN TLDs will be made available through two separate processes, initially through the New gTLD Program and the IDN ccTLD Fast Track Process. · 60 percent of Internet users are non-English speakers, while the dominant language used on the Internet is English (see Global Reach at www.glreach.com). One of the most significant innovations in the Internet since its incep- tion is the introduction of Internationalized Domain Names (IDNs) in the Internet’s address space. You may be familiar with some of the larger top- level domains: dot-com, dot-cn, and dot-org are just three examples. IDN top-level domain names will offer many new opportunities and benefits for Internet users around the world by allowing them to establish and use domains in their native languages and scripts. -

How to Add an Email Address to Your Safe Senders' List
How to Add an Email Address to your Safe Senders' List An increasing number of e-mail clients (Outlook, AOL, Hotmail, etc.) are including spam blockers that can affect delivery and display of some e-mail messages. This means that sometimes those desired e-mail communications might not reach you, or they might be displayed without images. To ensure that you continue receiving your e-mail or your subscriptions, and that they display properly, we recommend adding the email address or domain to your list of safe senders. Here are some instructions to help you do that: Instructions regarding email clients Apple Mail • Add the email address to your address book. • In Training mode, emails will arrive in the INBOX highlighted in brown. In Automatic mode, junk emails will arrive in the Junk box. To add an email that arrived in the JUNK folder, highlight the email message. • Choose Message > Mark > As Not Junk Mail AOL For AOL version 9.0: You can ensure that valued e-mail is delivered to your Inbox by adding the sending address to your "People I Know" list. • Open your latest issue of Brill’s E-Newsletter. • Click the Add Address button (over on the right) to add that sender to your "People IKnow" list. Alternatively, you can simply send an e-mail to [email protected]. Even if the e-mail you send doesn't get through (for whatever reason), the act of sending it does the job of putting the address into your "People I Know" list--and that's what counts. -

Going Live Tutorial Contents
Going Live Tutorial Contents Going Live with Your Online Business 1 Let’s Get Started 2 Domain names, IP addresses and DNS 2 Some advanced terminology 3 Going Live Step by Step 5 1. Getting a domain name 5 2. Setting up your domain & its email settings 5 2a. Adding your domain name to the system 5 2b. Email settings for your domain 7 3. Setting up email 8 3a. Creating mailboxes 8 3b. Creating aliases 8 4. Pointing your domain to us 9 5. Setting up your email client 10 For Advanced Users - using an external DNS service 11 Going Live with Your Online Business When your site is looking hot and you’re ready to rock, you’ll want to take your site out of trial mode and make it live. Taking a site live means a few things: You’re ready to pay for your site. You’re ready to buy a domain name (www.mybusiness.com) and allow people to access your site by typing that address into their web browser. OR you’ve got a domain name that currently goes to your old site, and you want to switch it over to your brand-spanking-new online business. Who is this for? This guide is for anyone who’s ready to take their site live and show it off to the world! Some sections can be skipped by those with more advanced knowledge - these sections will be marked accordingly. Business Catalyst • Going Live Tutorial 1 Let’s Get Started Domain names, IP addresses and DNS If you already know what a domain name is, what an IP address is and how DNS works, you can skip this section. -

M3AAWG Email Authentication Recommended Best Practices
Messaging, Malware and Mobile Anti-Abuse Working Group M3AAWG Email Authentication Recommended Best Practices September 2020 The reference URL for this document is: https://www.m3aawg.org/sites/default/files/m3aawg-email-authentication-recommended-best-practices- 09-2020.pdf For information on M3AAWG please see www.m3aawg.org. Table of Contents 1. Abstract ..................................................................................................................................................2 2. Introduction ............................................................................................................................................2 3. Scope ......................................................................................................................................................2 4. Executive Summary: A Checklist ...........................................................................................................4 5. Authentication Recommendation Discussion .........................................................................................5 5.1. Senders ...........................................................................................................................................5 5.2. Intermediaries .................................................................................................................................6 5.3. Receivers ........................................................................................................................................7 -

Beginner's Guide to Domain Names
Beginner’s Guide to D O M A I N N A M E S THIS IS ONE OF A SERIES OF GUIDES ABOUT ISSUES OF IMPORTANCE TO INTERNET USERS. EDUCATING NEW USERS ABOUT INTERNET ISSUES IS PART OF ICANN’S MISSION TO ENSURE A STABLE, SECURE, GLOBALLY INTEROPERABLE INTERNET. ICANN PREPARED THIS GUIDE AT THE REQUEST OF THE AT-LARGE ADVISORY COMMITTEE, THE VOICE OF THE INDIVIDUAL INTERNET USER AT ICANN. WE SINCERELY HOPE YOU FIND IT HELPFUL. TA b l E O f C ontents Introduction.................................................................................................................................................................................................................................2 Domain Names...........................................................................................................................................................................................................................3 1 What.is.a.domain.name.and.how.does.it.work?...........................................................................................................................................3 2 ...How.do.I.register.a.domain.name?.......................................................................................................................................................................3 . 3 ...How.do.I.select.a.domain.name.to.register?..................................................................................................................................................4 4 What.is.a.registrar.and.how.do.I.select.one?...................................................................................................................................................5 -

XEP-0157: Contact Addresses for XMPP Services
XEP-0157: Contact Addresses for XMPP Services Peter Saint-Andre Jacek Konieczny mailto:xsf@stpeter:im mailto:jajcus@jajcus:net xmpp:peter@jabber:org xmpp:jajcus@jabber:bnet:pl http://stpeter:im/ 2021-03-04 Version 1.1.1 Status Type Short Name Active Informational N/A This document defines a method for specifying contact addresses related to an XMPP service. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. Warranty ## NOTE WELL: This Specification is provided on an ”AS IS” BASIS, WITHOUT WARRANTIES OR CONDI- TIONS OF ANY KIND, express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. -

IDN, UA and EAI Key Fundamental Aspects Unicode, UA
11/30/20 IDN, UA and EAI In collaboration with CDAC Champika Wijayatunga – Regional Technical Engagement Manager - APAC 27 November 2020 | 1 IDN Program Objectives Enable deployment of domain names in the local languages and scripts of global communities in a secure and stable manner. | 2 Key Fundamental Aspects Unicode, UA, IDN | 3 1 11/30/20 ASCII Domain Name Label www.cafe-123.com Third-level Second-level Top-level domain domain domain (TLD) Forming ASCII Labels Forming ASCII Labels ② Use LDH ① Use only Letters • Letters [a-z] • Letters [a-z] • Digits [0-9] Label length = 63 • Hyphen [H] Label length = 63 Other constraints (e.g. on hyphen) | 4 Domain Name Mnemonics in ASCII Using LDH • Letters [a-z] • Digits [0-9] • Hyphen (H) ② | 5 Top-level Domain Name Mnemonics in ASCII Using Letters only • Letters [a-z] • Digits [0-9] • Hyphen (H) ① | 6 2 11/30/20 Internationalized Domain Name (IDN) Labels ตัวอย่าง.ไทย IDN IDN second-level top-level domain domain Syntax of IDN Labels Syntax of IDN Labels Valid U-Label: Unicode Valid U-label, further code points as constrained by the constrained by the “LDH” “letter” principle for TLDs scheme within IDNA 2008 ② ① | 7 Unicode ● Encoding glyphs into codepoints ● In specifications, codepoints are shown in hex using the U+XXXX notation ● Codepoints are typically carried using the UTF-8 (Unicode Transformation Format, 8 Bit) format ○ variable number of bytes for a single codepoint. ○ ascii is used as is ○ gold standard for carrying Unicode codepoints, in web, protocols, etc... | 8 IDN Mnemonics | 9 3 11/30/20 Unicode ● Multiple ways to use a glyph: ○ “è” = U+00E8 ○ “`e” = “è” = U+02CB U+0065 ○ Normalization is a process to insure that whatever the user type, the end representation will be the same. -

Domain Name Systems-Based Electronic Mail Security
DRAFT NIST CYBERSECURITY PRACTICE GUIDE DOMAIN NAME SYSTEMS-BASED ELECTRONIC MAIL SECURITY Scott Rose William C. Barker Santos Jha Chinedum Irrechukwu Karen Waltermire NIST SPECIAL PUBLICATION 1800-6 (INCLUDING PARTS A, B, C) ADDITIONAL CONTENT: https://nccoe.nist.gov/projects/building_blocks/ DRAFT NIST Special Publication 1800-6 NIST Cybersecurity Practice Guide DOMAIN NAME SYSTEMS- BASED ELECTRONIC MAIL SECURITY 1800-6A Scott Rose Executive Summary Information Technology Laboratory National Institute of Standards and Technology 1800-6B Approach, Architecture, and William C. Barker Security Characteristics Dakota Consulting For CIOs, CSOs, and Security Managers Silver Spring, MD 1800-6C Santos Jha How-To Guides Chinedum Irrechukwu For Security Engineers The MITRE Corporation McLean, VA Karen Waltermire National Cybersecurity Center of Excellence National Institute of Standards and Technology November 2016 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Willie May, Under Secretary of Commerce for Standards and Technology and Director DRAFT DISCLAIMER Certain commercial entities, equipment, products, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by NIST or NCCoE, nor is it intended to imply that the entities, equipment, products, or materials are necessarily the best available for the purpose. National Institute of Standards and Technology Special Publication 1800-6 Natl Inst. Stand. Technol. Spec. Publ. 1800-6, 221 pages (November 2016) CODEN: NSPUE2 Organizations are encouraged to review all draft publications during public comment periods and provide feedback. All publications from NIST’s National Cybersecurity Center of Excellence are available at http://nccoe.nist.gov. -

Instant Messaging Service Reference
IceWarp Unified Communications Instant Messaging Service Reference Version 10.4 Printed on 16 April, 2012 Contents Instant Messaging 1 Reference ....................................................................................................................................................................... 2 General .............................................................................................................................................................. 2 Services .............................................................................................................................................................. 2 Trusted Hosts ..................................................................................................................................................... 8 Archive/History .................................................................................................................................................. 9 File Transfers between Clients ..................................................................................................................................... 10 Monitoring via IM ......................................................................................................................................................... 12 Monitor Services and Get Your GW Events, Tasks and Notes via IM .................................................. 12 Usage ..................................................................................................................................................