Method for Scalar Multiplication
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Thierry Moreau
Compilation and Hardware Support for Approximate Acceleration Thierry Moreau, Adrian Sampson, Andre Baixo, Mark Wyse, Ben Ransford, Jacob Nelson, Hadi Esmaeilzadeh (Georgia Tech), Luis Ceze and Mark Oskin University of Washington [email protected] Theme: 2384.004 1 Thierry Moreau Approximate Computing Aims to exploit application resilience to trade-off quality for efficiency 2 Thierry Moreau Approximate Computing 3 Thierry Moreau Approximate Computing ✅ Accurate ✅ Approximate ❌ Expensive ✅ Cheap 4 Thierry Moreau 5 Thierry Moreau 6 Thierry Moreau 7 Thierry Moreau Neural Networks as Approximate Accelerators CPU Esmaeilzadeh et al. [MICRO 2012] 8 Thierry Moreau Neural Acceleration float foo (float a, float b) { AR F … NPUM P G return val; approximation acceleration } 9 Thierry Moreau Neural Acceleration compiler-support float foo (float a, float b) { AR F … NPUM P G return val; approximation acceleration } ACCEPT* *Sampson et. al [UW-TR] 10 Thierry Moreau Neural Acceleration compiler-support HW-support float foo (float a, float b) { AR F … NPUM P G return val; approximation acceleration } ACCEPT SNNAP* *Moreau et. al [HPCA2015] 11 Thierry Moreau Neural Acceleration compiler-support HW-support float foo (float a, float b) { AR F … NPUM P G return val; approximation acceleration } ACCEPT SNNAP 3.8x speedup and 2.8x efficiency - 10% error 12 Thierry Moreau Talk Outline Introduction Compiler Support with ACCEPT SNNAP Accelerator design Evaluation & Comparison with HLS 13 Thierry Moreau Compilation Overview code 1. Region detection annotation 14 Thierry Moreau Compilation Overview ACCEPT code region detection 1. Region detection & program annotation instrumentation 15 Thierry Moreau Compilation Overview ACCEPT code region detection 1. Region detection & program annotation instrumentation back prop. -

Heater Element Specifications Bulletin Number 592
Technical Data Heater Element Specifications Bulletin Number 592 Topic Page Description 2 Heater Element Selection Procedure 2 Index to Heater Element Selection Tables 5 Heater Element Selection Tables 6 Additional Resources These documents contain additional information concerning related products from Rockwell Automation. Resource Description Industrial Automation Wiring and Grounding Guidelines, publication 1770-4.1 Provides general guidelines for installing a Rockwell Automation industrial system. Product Certifications website, http://www.ab.com Provides declarations of conformity, certificates, and other certification details. You can view or download publications at http://www.rockwellautomation.com/literature/. To order paper copies of technical documentation, contact your local Allen-Bradley distributor or Rockwell Automation sales representative. For Application on Bulletin 100/500/609/1200 Line Starters Heater Element Specifications Eutectic Alloy Overload Relay Heater Elements Type J — CLASS 10 Type P — CLASS 20 (Bul. 600 ONLY) Type W — CLASS 20 Type WL — CLASS 30 Note: Heater Element Type W/WL does not currently meet the material Type W Heater Elements restrictions related to EU ROHS Description The following is for motors rated for Continuous Duty: For motors with marked service factor of not less than 1.15, or Overload Relay Class Designation motors with a marked temperature rise not over +40 °C United States Industry Standards (NEMA ICS 2 Part 4) designate an (+104 °F), apply application rules 1 through 3. Apply application overload relay by a class number indicating the maximum time in rules 2 and 3 when the temperature difference does not exceed seconds at which it will trip when carrying a current equal to 600 +10 °C (+18 °F). -

K-12 Individual No. Name Team Gr Rate Pts Tbrk1 Tbrk2 Tbrk3 Tbrk4
K-12 Individual No. Name Team Gr Rate Pts TBrk1 TBrk2 TBrk3 TBrk4 Rnd1 Rnd2 Rnd3 Rnd4 Rnd5 Rnd6 1 Chakraborty, Dipro 11 2299 5.5 21 24 43 20.5 W27 W12 W5 W32 W8 D3 State Champion, AZ Denker Representative 2 Yim, Tony Sung BASISS 8 2135 5 20.5 23.5 38.5 17.5 W24 W10 D3 D16 W11 W9 3 Aletheia-Zomlefer, Soren CHANPR 11 1961 5 20 23 35.5 18.5 W25 W26 D2 W40 W15 D1 4 Desmarais, Nicholas Eduard NOTRED 10 1917 5 18 20 33 18 W39 W23 W18 L15 W10 W8 5 Wong, Kinsleigh Phillip CFHS 10 1992 4.5 20 20 24.5 15 -X- W17 L1 W26 D7 W15 6 Todd, Bryce BASISC 10 1923 4.5 17 19 26.5 14.5 W38 D18 L9 W23 W21 W16 7 Chaliki, Kalyan DSMTHS 9 1726 4.5 17 18.5 26 15 W46 L16 W28 W22 D5 W17 8 Li, Bohan UHS 9 2048 4 22 25 29 18 W30 W11 W45 W9 L1 L4 9 Mittal, Rohan CFHS 9 1916 4 19.5 20.5 23 17 W47 W22 W6 L8 W20 L2 10 Pennock, Joshua CFHS 10 1682 4 19 22 24 14 W31 L2 W25 W21 L4 W29 11 Aradhyula, Sumhith CFHS 9 1631 4 18 20 22 14 W41 L8 W38 W13 L2 W19 12 Johnston, Nicolas Godfrey CFHS 9 1803 4 18 19.5 21 13 W43 L1 W29 L17 W24 W20 13 Martis, Tyler BRHS 12 1787 4 17 18 21 13 W42 L15 W24 L11 W18 W22 14 Plumb, Justin Rodney GCLACA 10 1700 4 16 17 20 13 W51 L32 W19 L20 W28 W27 15 Martinez, Isaac GLPREP 10 2159 3.5 21.5 24.5 27.5 16 W28 W13 D16 W4 L3 L5 16 Chen, Derek H CFHS 10 1965 3.5 21 23.5 26 15.5 W35 W7 D15 D2 D17 L6 17 Woodson, Tyler GILBHS 1640 3.5 19 19 17.5 14 W50 L5 W30 W12 D16 L7 18 Cancio, Aiya CFHS 9 1469 3.5 18.5 20 17.5 12.5 W36 D6 L4 W46 L13 W25 AZ Girls' Invitational Representative 19 Folden, Kurt CHANPR 10 1207 3 14 18 12 10 L32 W50 L14 W31 W23 L11 20 Thornton, -

Contemporary German Literature Collection) Brian Vetruba Washington University in St Louis, [email protected]
Washington University in St. Louis Washington University Open Scholarship University Libraries Publications University Libraries 2015 Twenty-ninth Annual Bibliography 2015 (Contemporary German Literature Collection) Brian Vetruba Washington University in St Louis, [email protected] Paul Michael Lützeler Washington University in St. Louis, [email protected] Katharina Böhm Washington University in St. Louis, [email protected] Follow this and additional works at: https://openscholarship.wustl.edu/lib_papers Part of the German Literature Commons, and the Library and Information Science Commons Recommended Citation Vetruba, Brian; Lützeler, Paul Michael; and Böhm, Katharina, "Twenty-ninth Annual Bibliography 2015 (Contemporary German Literature Collection)" (2015). University Libraries Publications. 20. https://openscholarship.wustl.edu/lib_papers/20 This Bibliography is brought to you for free and open access by the University Libraries at Washington University Open Scholarship. It has been accepted for inclusion in University Libraries Publications by an authorized administrator of Washington University Open Scholarship. For more information, please contact [email protected]. Max Kade Center for Contemporary German Literature Max Kade Zentrum für deutschsprachige Gegenwartsliteratur Director: Paul Michael Lützeler Twenty-ninth Annual Bibliography 2015 Editor: Brian W. Vetruba Editorial Assistant: Katharina Böhm February 28, 2017 Washington University in St. Louis Department of Germanic Languages and Literatures Max Kade Center -
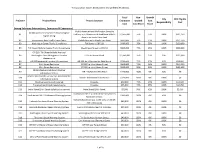
Draft Project List 2017-04-24
Transportation System Development Charge (TSDC) Project List Total Non- Growth City SDC Eligible Project # Project Name Project Location Estimated Growth Cost Responsibility Cost Cost Cost Share Share Driving Solutions (Intersections, Extensions & Expansions) Molalla Avenue from Washington Street to Molalla Avenue/ Beavercreek Road Adaptive D1 Gaffney Lane; Beavercreek Road from Molalla $1,565,000 75% 25% 100% $391,250 Signal Timing Avenue to Maple Lane Road D2 Beavercreek Road Traffic Surveillance Molalla Avenue to Maple Lane Road $605,000 75% 25% 100% $151,250 D3 Washington Street Traffic Surveillance 7th Street to OR 213 $480,000 75% 25% 100% $120,000 D4 7th Street/Molalla Avenue Traffic Surveillance Washington Street to OR 213 $800,000 75% 25% 100% $200,000 OR 213/ 7th Street-Molalla Avenue/ D5 Washington Street Integrated Corridor I-205 to Henrici Road $1,760,000 75% 25% 30% $132,000 Management D6 OR 99E Integrated Corridor Management OR 224 (in Milwaukie) to 10th Street $720,000 75% 25% 30% $54,000 D7 14th Street Restriping OR 99E to John Adams Street $845,000 74% 26% 100% $216,536 D8 15th Street Restriping OR 99E to John Adams Street $960,000 80% 20% 100% $192,000 OR 213/Beavercreek Road Weather D9 OR 213/Beavercreek Road $120,000 100% 0% 30% $0 Information Station Warner Milne Road/Linn Avenue Road Weather D10 Warner Milne Road/Linn Avenue $120,000 100% 0% 100% $0 Information Station D11 Optimize existing traffic signals Citywide $50,000 75% 25% 100% $12,500 D12 Protected/permitted signal phasing Citywide $65,000 75% 25% 100% -

Likely to Be Funded Transportation System
Table 2: Likely to be Funded Transportation System Project # Project Description Project Extent Project Elements Priority Further Study Identify and evaluate circulation options to reduce motor OR 213/Beavercreek Road Refinement OR 213 from Redland Road to Molalla D0 vehicle congestion along the corridor. Explore alternative Short-term Plan Avenue mobility targets. Identify and evaluate circulation options to reduce motor I-205 at the OR 99E and OR 213 Ramp vehicle congestion at the interchanges. Explore alternative D00 I-205 Refinement Plan Short-term Terminals mobility targets, and consider impacts related to a potential MMA Designation for the Oregon City Regional Center. Driving Solutions (Intersection and Street Management- see Figure 16) Molalla Avenue from Washington Street to Molalla Avenue/ Beavercreek Road Deploy adaptive signal timing that adjusts signal timings to D1 Gaffney Lane; Beavercreek Road from Molalla Short-term Adaptive Signal Timing match real-time traffic conditions. Avenue to Maple Lane Road Option 1: Convert 14th Street to one-way eastbound between McLoughlin Boulevard and John Adams Street: • Convert the Main Street/14th Street intersection to all-way stop control (per project D13). • From McLoughlin Boulevard to Main Street, 14th Street would be restriped to include two 12-foot eastbound travel lanes, a six-foot eastbound bike lane, a six-foot westbound contra-flow bike lane, and an eight-foot landscaping buffer on the north side • From Main Street to Washington Street, 14th Street would be restriped to include -

Nuclear Matters. a Practical Guide 5B
NUCLEAR MATTERS A Practical Guide Form Approved Report Documentation Page OMB No. 0704-0188 Public reporting burden for the collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington Headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington VA 22202-4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to a penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. 1. REPORT DATE 3. DATES COVERED 2. REPORT TYPE 2008 00-00-2008 to 00-00-2008 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER Nuclear Matters. A Practical Guide 5b. GRANT NUMBER 5c. PROGRAM ELEMENT NUMBER 6. AUTHOR(S) 5d. PROJECT NUMBER 5e. TASK NUMBER 5f. WORK UNIT NUMBER 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING ORGANIZATION Office of the Deputy Assistant to the Secretary of Defense (Nuclear REPORT NUMBER Matters),The Pentagon Room 3B884,Washington,DC,20301-3050 9. SPONSORING/MONITORING AGENCY NAME(S) AND ADDRESS(ES) 10. SPONSOR/MONITOR’S ACRONYM(S) 11. SPONSOR/MONITOR’S REPORT NUMBER(S) 12. DISTRIBUTION/AVAILABILITY STATEMENT Approved for public release; distribution unlimited 13. SUPPLEMENTARY NOTES 14. ABSTRACT 15. SUBJECT TERMS 16. SECURITY CLASSIFICATION OF: 17. -

Download Spec Sheet
THE SATURDAY UP-SLOPE ARM WITH LARGE FRONT RAIL • 2” LEGS 52520 52535 52530 52580 108lbs. LOVESEAT 115lbs. APARTMENT SOFA 140lbs. 86" SOFA 170lbs. 96" SOFA TOTAL W59" D37" H32" TOTAL W76" D37" H32" TOTAL W86" D37" H32" TOTAL W96" D37" H32" SEAT W53" D22" H18" SEAT W68" D22" H18" SEAT W78" D22" H18" SEAT W88" D22" H18" ARMS --- --- H24" ARMS --- --- H24" ARMS --- --- H24" ARMS --- --- H24" SATURDAY UP-SLOPE ARM ALSO AVAILABLE WITH THIN FRONT RAIL AND 7" LEGS AS 575 GROUP. SEE 1:1 BOOKLET FOR MORE INFORMATION. SEE REVERSE FOR SECTIONAL OPTIONS. EST. 1989 // AUTHENTIC HAND BUILT FURNITURE // THOMASVILLE, NORTH CAROLINA 50009 52511 52512 50013 80lbs. CORNER CHAIR 80lbs. RIGHT ARM CHAIR 80lbs. LEFT ARM CHAIR 80lbs. ARMLESS CHAIR TOTAL W37" D37" H32" TOTAL W30" D37" H32" TOTAL W30" D37" H32" TOTAL W26" D37" H32" SEAT W22" D22" H18" SEAT W26" D22" H18" SEAT W26" D22" H18" SEAT W26" D22" H18" ARMS --- --- --- ARMS --- --- H24" ARMS --- --- H24" ARMS --- --- --- 52521 52522 50023 52531 108lbs. R. ARM LOVESEAT 108lbs. L. ARM LOVESEAT 95lbs. ARMLESS LOVESEAT 180lbs. R. CORNER SOFA TOTAL W56" D37" H32" TOTAL W56" D37" H32" TOTAL W52" D37" H32" TOTAL W92" D37" H32" SEAT W53" D22" H18" SEAT W53" D22" H18" SEAT W52" D22" H18" SEAT W79" D22" H18" ARMS --- --- H24" ARMS --- --- H24" ARMS --- --- --- ARMS --- --- H24" 52532 50033 52533 52534 180lbs. L. CORNER SOFA 120lbs. ARMLESS SOFA 125lbs. R. ARM SOFA 125lbs. L. ARM SOFA TOTAL W92" D37" H32" TOTAL W78" D37" H32" TOTAL W82" D37" H32" TOTAL W82" D37" H32" SEAT W79" D22" H18" SEAT W78" D22" H18" SEAT W78" D22" H18" SEAT W78" D22" H18" ARMS --- --- H24" ARMS --- --- --- ARMS --- --- H24" ARMS --- --- H24" 50035 52536 52537 50039 100lbs. -

Product News
PRODUCT NEWS ROSS CONTROLS® Improves Low Temperature Ratings of Valves ¾ Expands Application Range ¾ Broadens Base of Potential Customers ¾ Compliments Circuits using Low Temp Series 21 Products ROSS CONTROLS® World Headquarters (November 2018) - Customers worldwide have long considered ROSS® products as best-in-class for extreme and harsh environments. ROSS® has earned a reputation for rugged reliability and long service life in these challenging applications. For decades ROSS® Series 21 valves have successfully operated in -40°F (-40°C) conditions. Similarly, many ROSS® legacy products have been effectively installed in circuits with the Series 21, even though the applications were well below the conservative temperature ratings published in our catalogs. It is well-known, water vapor in an air system has the potential to cause the formation of ice when operating at temperatures below +40°F (4°C). ROSS® has historically used this principle to guide the low temperature ratings of many legacy products instead of using the actual temperature capability of the valve design. Today, ROSS CONTROLS® is pleased to announce modernized low temperature ratings for many of our legacy products. Literature on the ROSS® website has been updated to reflect the lower temperature range for the valves on Page 2 of this announcement. No design or component changes have been made, so any valves on your shelf will operate at these lower temperatures. OEM business. Even if you sell ROSS® products in a warm climate where USER customers do not operate at low temperatures, you may have OEM customers who design & build equipment for cold weather applications outside of your territory. -

PC Cake Perform Pump
PC Cake Perform Pump Progressing cavity process pump, designed to be maintained in place without disconnecting from pipework. For pumping of highly viscous materials such as sludges, slurries, thick non-flowing pastes and dewatered sludge cake, in municipal and industrial process applications. Construction Materials of construction, available in cast iron, with a choice of rotor and stator materials to suit individual applications e.g. hard chrome plated rotor or natural rubber stator. Applications Typical applications for the PC cake perform pump include: • Heavy sludge cake transfer for greater than 30% dry solids concentration. • Dewatered and thickened sludge transfer. • Sludge blending. • Imported and organic waste sludge transfer. • Industrial process sludge with high percentage dry solids concentration. Performance Features Capacity, for flows up to 216 gpm (49 m3/h) and differential pressure • Maintain-in-place design allows for quick and easy removal of up to 350 psi (24 bar), to operate in a range of process temperatures rotating parts, and clearing of rag build-up, without disconnecting from 14 °F (-10 °C), up to 212 °F (100 °C). from pipework. • An auger screw conveyor for efficient feeding of the pump when Performance data handling high percentage dry solid sludge concentrations. • Gentle pumping action, minimises shear and crush damage to the 216 pumped product. GPM WA2 • Supplied with a baseplate to ease installation, or optional without. 176 • Fully sealed drive train to maximise life and minimise downtime. • Hard faced, single mechanical seal as standard, with packed W92 gland as an option. 150 • Designed to accommodate optional hopper or bridge breaker W82 W84 attachments. -

Keyword Index
Neuropsychopharmacology (2012) 38, S479–S521 & 2012 American College of Neuropsychopharmacology. All rights reserved 0893-133X/12 www.neuropsychopharmacology.org S479 Keyword Index 10b-Hydroxyestra-14-diene-3-one . W87 M114, M115, M116, M119, M123, M130, M131, M132, M134, M140, M142, 13C magnetic resonance spectroscopy . W34 M143, M144, M145, M146, M149, M150, M151, M152, M154, M155, M156, M157, M158, M159, M166, M168, M172, M174, M178, M179, M181, M182, 22q11 deletion . T123 M185, M186, M187, M188, M193, M197, M198, M199, M200, M201, M202, 2-AG . .23.2, 23.3, M145, T69, T161 M205, M212, T3, T5, T8, T13, T16, T17, T20, T22, T24, T25, T27, T31, T35, 3-MT . M182 T44, T49, T51, T58, T60, T66, T67, T72, T75, T77, T79, T80, T82, T83, T86, T88, T91, T95, T98, T99, T103, T109, T111, T113, T114, T116, T117, T119, 5-HT . 14.2, 17.4, 44.2, 52, M19, M45, M64, M72, M75, M91, T121, T125, T126, T128, T138, T140, T144, T147, T148, T151, T153, T154, M115, M144, M147, M154, M157, M161, M162, M183, M185, M186, T17, T49, T158, T161, T166, T167, T171, T173, T176, T177, T179, T181, T185, T188, T53, T120, T163, T194, W54, W125, W165, W176, W191 T189, T192, T194, T197, T198, T202, T203, T209, T210, W3, W5, W8, W10, 5-HT6 . .W125 W18, W20, W31, W32, W45, W46, W53, W54, W57, W64, W71, W72, W75, W76, W81, W83, W84, W87, W93, W94, W97, W100, W103, W104, W105, A W106, W107, W115, W116, W117, W118, W120, W124, W129, W137, W138, W143, W154, W158, W159, W160, W169, W172, W173, W176, W177, W186, W188, W195, W197, W199, W201, W203, W208, W214, W218 AAV . -

Supplementary Information
Supplementary Information Table S1. Antimicrobial Activity of the Pseudovibrio RAPD group representatives against the pathogen S. aureus NCDO 949, with Pseudovibrio isolates grown on MA vs. SYP-SW. Pseudovibrio Isolate MA SYP-SW JIC5 ++ <+ JIC6 ++ - JIC17 + <+ W10 + <+ W19 - - W62 ++ + W63 ++ <+ W64 +++ <+ W65 ++ + W69 ++ - W71 + <+ W74 ++ <+ W85 ++ <+ W78 + <+ W89 +++ <+ W94 ++ + W96 + <+ W99 ++ <+ WM31 ++ + WM33 + <+ WM34 ++ <+ WM40 ++ + WM50 - - WC13 ++ <+ WC15 + - WC21 ++ <+ WC22 ++ - WC30 + <+ WC32 ++ - WC41 ++ + WC43 ++ <+ HC6 ++ + HMMA3 + <+ Diameter Inhibition: <+ = <1 mm; + = ≥1 mm; ++ = ≥2 mm; +++ = ≥4 mm. Mar. Drugs 2014, 12 S2 Table S2. Indicator strains used for testing bioactivity of marine isolates. Strain Description Source/Reference Yersinia ruckerri Type strain DSMZ # Edwardsialla tarda Type strain DSMZ Vibrio anguillarum LMG 4410 Type strain DSMZ Escherichia coli MUH 103 Clinical Isolate MUH * Escherichia coli NCIMB 15943 Type strain MDCC UCC Morganella morganii MUH 988 Clinical isolate MUH Salmonella Typhimurium LT2 Type strain MDCC UCC Salmonella Typhimurium C5369 Type strain MDCC UCC Pandoraea sputorum LMG18819 CF clinical Isolate E. Caraher § Salmonella arizonae Type strain Shinfield, UK/MDCC UCC Staphylococcus aureus NCDO 949 Type strain Shinfield, UK/MDCC UCC # DSM Collection, Deutsche Sammlung von Mikroorganismen und Zellkulturen GmbH, Braunschweig, Germany; * Mercy University Hospital, Cork; § Centre of Microbial Host Interactions, ITT Dublin, Tallaght, Dublin 24, Ireland; ^ Microbiology Department Culture Collection,