Strategic Interactions in Dram and Risc Technology: a Network Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AIX® Version 6.1 Performance Toolbox Guide Limiting Access to Data Suppliers
AIX Version 6.1 Performance Toolbox Version 3 Guide and Reference AIX Version 6.1 Performance Toolbox Version 3 Guide and Reference Note Before using this information and the product it supports, read the information in Appendix G, “Notices,” on page 431. This edition applies to AIX Version 6.1 and to all subsequent releases and modifications until otherwise indicated in new editions. (c) Copyright AT&T, 1984, 1985, 1986, 1987, 1988, 1989. All rights reserved. Copyright Sun Microsystems, Inc., 1985, 1986, 1987, 1988. All rights reserved. The Network File System (NFS) was developed by Sun Microsystems, Inc. This software and documentation is based in part on the Fourth Berkeley Software Distribution under license from The Regents of the University of California. We acknowledge the following institutions for their role in its development: the Electrical Engineering and Computer Sciences Department at the Berkeley Campus. The Rand MH Message Handling System was developed by the Rand Corporation and the University of California. Portions of the code and documentation described in this book were derived from code and documentation developed under the auspices of the Regents of the University of California and have been acquired and modified under the provisions that the following copyright notice and permission notice appear: Copyright Regents of the University of California, 1986, 1987, 1988, 1989. All rights reserved. Redistribution and use in source and binary forms are permitted provided that this notice is preserved and that due credit is given to the University of California at Berkeley. The name of the University may not be used to endorse or promote products derived from this software without specific prior written permission. -

System Administration
System Administration Varian NMR Spectrometer Systems With VNMR 6.1C Software Pub. No. 01-999166-00, Rev. C0503 System Administration Varian NMR Spectrometer Systems With VNMR 6.1C Software Pub. No. 01-999166-00, Rev. C0503 Revision history: A0800 – Initial release for VNMR 6.1C A1001 – Corrected errors on pg 120, general edit B0202 – Updated AutoTest B0602 – Added additional Autotest sections including VNMRJ update B1002 – Updated Solaris patch information and revised section 21.7, Autotest C0503 – Add additional Autotest sections including cryogenic probes Applicability: Varian NMR spectrometer systems with Sun workstations running Solaris 2.x and VNMR 6.1C software By Rolf Kyburz ([email protected]) Varian International AG, Zug, Switzerland, and Gerald Simon ([email protected]) Varian GmbH, Darmstadt, Germany Additional contributions by Frits Vosman, Dan Iverson, Evan Williams, George Gray, Steve Cheatham Technical writer: Mike Miller Technical editor: Dan Steele Copyright 2001, 2002, 2003 by Varian, Inc., NMR Systems 3120 Hansen Way, Palo Alto, California 94304 1-800-356-4437 http://www.varianinc.com All rights reserved. Printed in the United States. The information in this document has been carefully checked and is believed to be entirely reliable. However, no responsibility is assumed for inaccuracies. Statements in this document are not intended to create any warranty, expressed or implied. Specifications and performance characteristics of the software described in this manual may be changed at any time without notice. Varian reserves the right to make changes in any products herein to improve reliability, function, or design. Varian does not assume any liability arising out of the application or use of any product or circuit described herein; neither does it convey any license under its patent rights nor the rights of others. -

4010, 237 8514, 226 80486, 280 82786, 227, 280 a AA. See Anti-Aliasing (AA) Abacus, 16 Accelerated Graphics Port (AGP), 219 Acce
Index 4010, 237 AIB. See Add-in board (AIB) 8514, 226 Air traffic control system, 303 80486, 280 Akeley, Kurt, 242 82786, 227, 280 Akkadian, 16 Algebra, 26 Alias Research, 169 Alienware, 186 A Alioscopy, 389 AA. See Anti-aliasing (AA) All-In-One computer, 352 Abacus, 16 All-points addressable (APA), 221 Accelerated Graphics Port (AGP), 219 Alpha channel, 328 AccelGraphics, 166, 273 Alpha Processor, 164 Accel-KKR, 170 ALT-256, 223 ACM. See Association for Computing Altair 680b, 181 Machinery (ACM) Alto, 158 Acorn, 156 AMD, 232, 257, 277, 410, 411 ACRTC. See Advanced CRT Controller AMD 2901 bit-slice, 318 (ACRTC) American national Standards Institute (ANSI), ACS, 158 239 Action Graphics, 164, 273 Anaglyph, 376 Acumos, 253 Anaglyph glasses, 385 A.D., 15 Analog computer, 140 Adage, 315 Anamorphic distortion, 377 Adage AGT-30, 317 Anatomic and Symbolic Mapper Engine Adams Associates, 102 (ASME), 110 Adams, Charles W., 81, 148 Anderson, Bob, 321 Add-in board (AIB), 217, 363 AN/FSQ-7, 302 Additive color, 328 Anisotropic filtering (AF), 65 Adobe, 280 ANSI. See American national Standards Adobe RGB, 328 Institute (ANSI) Advanced CRT Controller (ACRTC), 226 Anti-aliasing (AA), 63 Advanced Remote Display Station (ARDS), ANTIC graphics co-processor, 279 322 Antikythera device, 127 Advanced Visual Systems (AVS), 164 APA. See All-points addressable (APA) AED 512, 333 Apalatequi, 42 AF. See Anisotropic filtering (AF) Aperture grille, 326 AGP. See Accelerated Graphics Port (AGP) API. See Application program interface Ahiska, Yavuz, 260 standard (API) AI. -

A Survey of Distributed File Systems
A Survey of Distributed File Systems M. Satyanarayanan Department of Computer Science Carnegie Mellon University February 1989 Abstract Abstract This paper is a survey of the current state of the art in the design and implementation of distributed file systems. It consists of four major parts: an overview of background material, case studies of a number of contemporary file systems, identification of key design techniques, and an examination of current research issues. The systems surveyed are Sun NFS, Apollo Domain, Andrew, IBM AIX DS, AT&T RFS, and Sprite. The coverage of background material includes a taxonomy of file system issues, a brief history of distributed file systems, and a summary of empirical research on file properties. A comprehensive bibliography forms an important of the paper. Copyright (C) 1988,1989 M. Satyanarayanan The author was supported in the writing of this paper by the National Science Foundation (Contract No. CCR-8657907), Defense Advanced Research Projects Agency (Order No. 4976, Contract F33615-84-K-1520) and the IBM Corporation (Faculty Development Award). The views and conclusions in this document are those of the author and do not represent the official policies of the funding agencies or Carnegie Mellon University. 1 1. Introduction The sharing of data in distributed systems is already common and will become pervasive as these systems grow in scale and importance. Each user in a distributed system is potentially a creator as well as a consumer of data. A user may wish to make his actions contingent upon information from a remote site, or may wish to update remote information. -

Ross Technology RT6224K User Manual 1 (Pdf)
Full-service, independent repair center -~ ARTISAN® with experienced engineers and technicians on staff. TECHNOLOGY GROUP ~I We buy your excess, underutilized, and idle equipment along with credit for buybacks and trade-ins. Custom engineering Your definitive source so your equipment works exactly as you specify. for quality pre-owned • Critical and expedited services • Leasing / Rentals/ Demos equipment. • In stock/ Ready-to-ship • !TAR-certified secure asset solutions Expert team I Trust guarantee I 100% satisfaction Artisan Technology Group (217) 352-9330 | [email protected] | artisantg.com All trademarks, brand names, and brands appearing herein are the property o f their respective owners. Find the Ross Technology RT6224K-200/512S at our website: Click HERE 830-0016-03 Rev A 11/15/96 PRELIMINARY Colorado 4 RT6224K hyperSPARC CPU Module Features D Based on ROSS’ fifth-generation D SPARC compliant — Zero-wait-state, 512-Kbyte or hyperSPARC processor — SPARC Instruction Set Architec- 1-Mbyte 2nd-level cache — RT620D Central Processing Unit ture (ISA) Version 8 compliant — Demand-paged virtual memory (CPU) — Conforms to SPARC Reference management — RT626 Cache Controller, Memory MMU Architecture D Module design Management, and Tag Unit — Conforms to SPARC Level 2 MBus — MBus-standard form factor: 3.30” (CMTU) Module Specification (Revision 1.2) (8.34 cm) x 5.78” (14.67 cm) — Four (512-Kbyte) or eight D Dual-clock architecture — Provides CPU upgrade path at (1-Mbyte) RT628 Cache Data Units module level (CDUs) Ċ CPU scaleable up to -

APPENDIX a Aegis and Unix Commands
APPENDIX A Aegis and Unix Commands FUNCTION AEGIS BSD4.2 SYSS ACCESS CONTROL AND SECURITY change file protection modes edacl chmod chmod change group edacl chgrp chgrp change owner edacl chown chown change password chpass passwd passwd print user + group ids pst, lusr groups id +names set file-creation mode mask edacl, umask umask umask show current permissions acl -all Is -I Is -I DIRECTORY CONTROL create a directory crd mkdir mkdir compare two directories cmt diff dircmp delete a directory (empty) dlt rmdir rmdir delete a directory (not empty) dlt rm -r rm -r list contents of a directory ld Is -I Is -I move up one directory wd \ cd .. cd .. or wd .. move up two directories wd \\ cd . ./ .. cd . ./ .. print working directory wd pwd pwd set to network root wd II cd II cd II set working directory wd cd cd set working directory home wd- cd cd show naming directory nd printenv echo $HOME $HOME FILE CONTROL change format of text file chpat newform compare two files emf cmp cmp concatenate a file catf cat cat copy a file cpf cp cp Using and Administering an Apollo Network 265 copy std input to std output tee tee tee + files create a (symbolic) link crl In -s In -s delete a file dlf rm rm maintain an archive a ref ar ar move a file mvf mv mv dump a file dmpf od od print checksum and block- salvol -a sum sum -count of file rename a file chn mv mv search a file for a pattern fpat grep grep search or reject lines cmsrf comm comm common to 2 sorted files translate characters tic tr tr SHELL SCRIPT TOOLS condition evaluation tools existf test test -

Multiple Instruction Issue in the Nonstop Cyclone System
~TANDEM Multiple Instruction Issue in the NonStop Cyclone System Robert W. Horst Richard L. Harris Robert L. Jardine Technical Report 90.6 June 1990 Part Number: 48007 Multiple Instruction Issue in the NonStop Cyclone Processorl Robert W. Horst Richard L. Harris Robert L. Jardine Tandem Computers Incorporated 19333 Vallco Parkway Cupertino, CA 95014 Abstract This paper describes the architecture for issuing multiple instructions per clock in the NonStop Cyclone Processor. Pairs of instructions are fetched and decoded by a dual two-stage prefetch pipeline and passed to a dual six-stage pipeline for execution. Dynamic branch prediction is used to reduce branch penalties. A unique microcode routine for each pair is stored in the large duplexed control store. The microcode controls parallel data paths optimized for executing the most frequent instruction pairs. Other features of the architecture include cache support for unaligned double precision accesses, a virtually-addressed main memory, and a novel precise exception mechanism. lA previous version of this paper was published in the conference proceedings of The 17th Annual International Symposium on Computer Architecture, May 28-31, 1990, Seattle, Washington. Dynabus+ Dynabus X Dvnabus Y IIIIII I 20 MBIS Parallel I I II 100 MbiVS III I Serial Fibers CPU CPU CPU CPU 0 3 14 15 MEMORY ••• MEMORY • •• MEMORY MEMORY ~IIIO PROC110 IIPROC1,0 PROC1,0 ROC PROC110 IIPROC1,0 PROC110 F11IOROC o 1 o 1 o 1 o 1 I DISKCTRL ~ DISKCTRL I I Q~ / \. I DISKCTRL I TAPECTRL : : DISKCTRL : I 0 1 2 3 /\ o 1 2 3 0 1 2 3 0 1 2 3 Section 0 Section 3 Figure 1. -
Timeline of Computer History
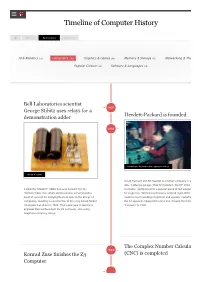
Timeline of Computer History By Year By Category Search AI & Robotics (55) Computers (145)(145) Graphics & Games (48) Memory & Storage (61) Networking & The Popular Culture (50) Software & Languages (60) Bell Laboratories scientist 1937 George Stibitz uses relays for a Hewlett-Packard is founded demonstration adder 1939 Hewlett and Packard in their garage workshop “Model K” Adder David Packard and Bill Hewlett found their company in a Alto, California garage. Their first product, the HP 200A A Called the “Model K” Adder because he built it on his Oscillator, rapidly became a popular piece of test equipm “Kitchen” table, this simple demonstration circuit provides for engineers. Walt Disney Pictures ordered eight of the 2 proof of concept for applying Boolean logic to the design of model to test recording equipment and speaker systems computers, resulting in construction of the relay-based Model the 12 specially equipped theatres that showed the movie I Complex Calculator in 1939. That same year in Germany, “Fantasia” in 1940. engineer Konrad Zuse built his Z2 computer, also using telephone company relays. The Complex Number Calculat 1940 Konrad Zuse finishes the Z3 (CNC) is completed Computer 1941 The Zuse Z3 Computer The Z3, an early computer built by German engineer Konrad Zuse working in complete isolation from developments elsewhere, uses 2,300 relays, performs floating point binary arithmetic, and has a 22-bit word length. The Z3 was used for aerodynamic calculations but was destroyed in a bombing raid on Berlin in late 1943. Zuse later supervised a reconstruction of the Z3 in the 1960s, which is currently on Operator at Complex Number Calculator (CNC) display at the Deutsches Museum in Munich. -

12 MULTICHIP MODULES (Mcms)
12 MULTICHIP MODULES (MCMs) HISTORICAL PERSPECTIVE Virtually every large computer manufacturer, telecommunications products manufacturer, high volume consumer electronics manufacturer and aerospace products manufacturer is working on or considering designs that include multichip modules. There has been a dramatic increase in activity over the last five years, with entire conferences being dedicated to multichip modules. MCMs have gone through three phases in their growth. Phase one was the widespread use in mainframe and super computer products. Some examples of MCMs used for these high-end applications are shown in Figure 12-1. The primary driving force was performance. These systems were predominately ECL based, with relatively low inte- gration levels. The MCM implementation allowed the Òre-integrationÓ of the LSI chips into VLSI modules, while keeping the wiring delays small. Source: DEC Source: IBM Source: Motorola/Siemens Source: ICE, “Roadmaps of Packaging Technology” 22555 Figure 12-1. Early MCMs in ECL Mainframe Computers in the Mid 1980Õs INTEGRATED CIRCUIT ENGINEERING CORPORATION 12-1 Multichip Modules (MCMs) Using a conventional single chip package and circuit board interconnect strategy, the package and interconnects took up over 50% of the timing budget. Decreases in the chip delays could not have much impact on system performance without a significant decrease in the interconnect delays as well. The use of MCMs reduced the interconnect delays significantly. This is shown in Figure 12-2 com- paring the delays in the IBM 3033 with a CPU using single chip packages and four circuit boards, and the IBM 3081, the first mainframe that used the Thermal Conduction Module (TCM). -

Fault Tolerance in Tandem Computer Systems
1'TANDEM Fault Tolerance in Tandem Computer Systems Joel Bartlett * Wendy Bartlett Richard Carr Dave Garcia Jim Gray Robert Horst Robert Jardine Dan Lenoski DixMcGuire • Preselll address: Digital Equipmelll CorporQlioll Western Regional Laboralory. Palo Alto. California Technical Report 90.5 May 1990 Part Number: 40666 ~ TANDEM COMPUTERS Fault Tolerance in Tandem Computer Systems Joel Bartlett* Wendy Bartlett Richard Carr Dave Garcia Jim Gray Robert Horst Robert Jardine Dan Lenoski Dix McGuire * Present address: Digital Equipment Corporation Western Regional Laboratory, Palo Alto, California Technical Report 90.5 May 1990 Part Nurnber: 40666 Fault Tolerance in Tandem Computer Systems! Wendy Bartlett, Richard Carr, Dave Garcia, Jim Gray, Robert Horst, Robert Jardine, Dan Lenoski, Dix McGuire Tandem Computers Incorporated Cupertino, California Joel Bartlett Digital Equipment Corporation, Western Regional Laboratory Palo Alto, California Tandem Technical Report 90.5, Tandem Part Number 40666 March 1990 ABSTRACT Tandem produces high-availability, general-purpose computers that provide fault tolerance through fail fast hardware modules and fault-tolerant software2. This chapter presents a historical perspective of the Tandem systems' evolution and provides a synopsis of the company's current approach to implementing these systems. The article does not cover products announced since January 1990. At the hardware level, a Tandem system is a loosely-coupled multiprocessor with fail-fast modules connected with dual paths. A system can include a range of processors, interconnected through a hierarchical fault-tolerant local network. A system can also include a variety of peripherals, attached with dual-ported controllers. A novel disk subsystem allows a choice between low cost-per-byte and low cost-per-access. -

Hypersparc Module Installation Guide E ROSS Technology, Inc
TM hyperSPARC Module Installation Guide E ROSS Technology, Inc. 5316 Highway 290 West Austin, Texas 78735 U.S.A. All rights reserved. This product and related documentation is protected by copyright and distributed under licenses re- stricting its use, copying, distribution, and decompilation. No part of this product or related documentation may be repro- duced in any form by any means without prior written authorization of ROSS Technology and its licensors, if any. Portions of this product may be derived from the UNIXR and Berkeley 4.3 BSD systems, licensed from UNIX Systems Laboratories, Inc. and the University of California, respectively. Third party font software in this product is protected by copyright and licensed from Sun’s Font Suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applica- tions. TRADEMARKS: ROSS, ROSS Technology, and the ROSS Technology, Inc. logo are registered trademarks of ROSS Technology, Inc. hyperSPARC is a trademark of SPARC International, Inc. and is licensed exclusively to ROSS Technology, Inc. Sun, Sun Microsystems, and the Sun logo are trademarks or registered trademarks of Sun Microsystems, Inc. UNIX, and OPEN LOOK are registered trademarks of UNIX System Laboratories, Inc. All other product names mentioned herein are the trademarks of their respective owners. All SPARC trademarks, including the SCD Compliant Logo, are trademarks or registered trademarks of SPARC Interna- tional, Inc. -

Computer Architectures an Overview
Computer Architectures An Overview PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 25 Feb 2012 22:35:32 UTC Contents Articles Microarchitecture 1 x86 7 PowerPC 23 IBM POWER 33 MIPS architecture 39 SPARC 57 ARM architecture 65 DEC Alpha 80 AlphaStation 92 AlphaServer 95 Very long instruction word 103 Instruction-level parallelism 107 Explicitly parallel instruction computing 108 References Article Sources and Contributors 111 Image Sources, Licenses and Contributors 113 Article Licenses License 114 Microarchitecture 1 Microarchitecture In computer engineering, microarchitecture (sometimes abbreviated to µarch or uarch), also called computer organization, is the way a given instruction set architecture (ISA) is implemented on a processor. A given ISA may be implemented with different microarchitectures.[1] Implementations might vary due to different goals of a given design or due to shifts in technology.[2] Computer architecture is the combination of microarchitecture and instruction set design. Relation to instruction set architecture The ISA is roughly the same as the programming model of a processor as seen by an assembly language programmer or compiler writer. The ISA includes the execution model, processor registers, address and data formats among other things. The Intel Core microarchitecture microarchitecture includes the constituent parts of the processor and how these interconnect and interoperate to implement the ISA. The microarchitecture of a machine is usually represented as (more or less detailed) diagrams that describe the interconnections of the various microarchitectural elements of the machine, which may be everything from single gates and registers, to complete arithmetic logic units (ALU)s and even larger elements.