Network Connectivity Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

View the Bloomberg Terminal User Guide
Press the <HELP> key twice for instant Helpx2 live assistance. bloomberg.com Frankfurt New York Singapore +49 69 9204 1210 +1 212 318 2000 +65 6212 1000 Hong Kong San Francisco Sydney +852 2977 6000 +1 415 912 2960 +61 2 9777 8600 London São Paulo Tokyo GETTING +44 20 7330 7500 +55 11 3048 4500 +81 3 3201 8900 The BLOOMBERG PROFESSIONAL service, BLOOMBERG Data and BLOOMBERG Order Management Systems (the “Services”) are owned and distributed locally by Bloomberg Finance L.P. (“BFLP”) and its subsidiaries in all jurisdictions other than Argentina, Bermuda, China, India, STARTED Japan and Korea (the “BLP Countries”). BFLP is a wholly-owned subsidiary of Bloomberg L.P. (“BLP”). BLP provides BFLP with all global marketing and operational support and service for the Services and distributes the Services either directly or through a non-BFLP subsidiary in the BLP Countries. BLOOMBERG, BLOOMBERG PROFESSIONAL, BLOOMBERG MARKETS, BLOOMBERG NEWS, BLOOMBERG ANYWHERE, BLOOMBERG TRADEBOOK, BLOOMBERG BONDTRADER, BLOOMBERG TELEVISION, BLOOMBERG RADIO, BLOOMBERG PRESS and BLOOMBERG.COM are trademarks and service marks of BFLP or its subsidiaries. ©2007 Bloomberg Finance L.P. All rights reserved. 26443337 1107 10006030 02 The Bloomberg Keyboard Keyboard and Navigation 04 Creating a Login Name and Password 06 Finding Information Autocomplete and the <HELP> Key 06 The Global Help Desk: 24/7 Interact with the Bloomberg Help Desk 08 Broad Market Perspectives Top Recommended Functions 09 Analyzing a Company Basic Functions for Bonds and Equities 10 Communication The BLOOMBERG PROFESSIONAL® Service Message System 11 Tips, Tricks, and Fun 12 Customer Support If you are not using a Bloomberg-provided keyboard, press the Alt + K buttons simultaneously to view an image of your keyboard. -

How to Find out the IP Address of an Omron
Communications Middleware/Network Browser How to find an Omron Controller’s IP address Valin Corporation | www.valin.com Overview • Many Omron PLC’s have Ethernet ports or Ethernet port options • The IP address for a PLC is usually changed by the programmer • Most customers do not mark the controller with IP address (label etc.) • Very difficult to communicate to the PLC over Ethernet if the IP address is unknown. Valin Corporation | www.valin.com Simple Ethernet Network Basics IP address is up to 12 digits (4 octets) Ex:192.168.1.1 For MOST PLC programming applications, the first 3 octets are the network address and the last is the node address. In above example 192.168.1 is network address, 1 is node address. For devices to communicate on a simple network: • Every device IP Network address must be the same. • Every device node number must be different. Device Laptop EX: Omron PLC 192.168.1.1 192.168.1.1 Device Laptop EX: Omron PLC 127.27.250.5 192.168.1.1 Device Laptop EX: Omron PLC 192.168.1.3 192.168.1.1 Valin Corporation | www.valin.com Omron Default IP Address • Most Omron Ethernet devices use one of the following IP addresses by default. Omron PLC 192.168.250.1 OR 192.168.1.1 Valin Corporation | www.valin.com PING Command • PING is a way to check if the device is connected (both virtually and physically) to the network. • Windows Command Prompt command. • PC must use the same network number as device (See previous) • Example: “ping 172.21.90.5” will test to see if a device with that IP address is connected to the PC. -

Xerox® Colorqube 8580/8880 Color Printer 3 System Administrator Guide
Xerox® ColorQube® 8580 / 8880 Color Printer Imprimante couleur System Administrator Guide Guide de l’administrateur système © 2015 Xerox Corporation. All rights reserved. Unpublished rights reserved under the copyright laws of the United States. Contents of this publication may not be reproduced in any form without permission of Xerox Corporation. Copyright protection claimed includes all forms of matters of copyrightable materials and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs which are displayed on the screen such as styles, templates, icons, screen displays, looks, and so on. Xerox® and Xerox and Design®, Phaser®, PhaserSMART®, PhaserMatch®, PhaserCal®, PhaserMeter™, CentreWare®, PagePack®, eClick®, PrintingScout®, Walk-Up®, WorkCentre®, FreeFlow®, SMARTsend®, Scan to PC Desktop®, MeterAssistant®, SuppliesAssistant®, Xerox Secure Access Unified ID System®, Xerox Extensible Interface Platform®, ColorQube®, Global Print Driver®, and Mobile Express Driver® are trademarks of Xerox Corporation in the United States and/or other countries. Adobe® Reader®, Adobe® Type Manager®, ATM™, Flash®, Macromedia®, Photoshop®, and PostScript® are trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple, Bonjour, EtherTalk, TrueType, iPad, iPhone, iPod, iPod touch, Mac and Mac OS are trademarks of Apple Inc., registered in the U.S. and other countries. AirPrint and the AirPrint logo are trademarks of Apple Inc. HP-GL®, HP-UX®, and PCL® are trademarks of Hewlett-Packard Corporation in the United States and/or other countries. IBM® and AIX® are trademarks of International Business Machines Corporation in the United States and/or other countries. Microsoft®, Windows Vista®, Windows®, and Windows Server® are trademarks of Microsoft Corporation in the United States and other countries. -

Cs-204: Computer Networks
CS-204: COMPUTER NETWORKS Lecture 5 Chapter 19- Network Layer: Logical Addressing Instructor: Dr. Vandana Kushwaha 1. INTRODUCTION Communication at the network layer is host-to-host (computer-to-computer); a computer somewhere in the world needs to communicate with another computer somewhere else in the world. Usually, computers communicate through the Internet. The packet transmitted by the sending computer may pass through several LANs or WANs before reaching the destination computer. For this level of communication, we need a global addressing scheme; we called this logical addressing or IP address. 2. IPv4 ADDRESSES An IPv4 address is a 32-bit address that uniquely and universally defines the connection of a device (for example, a computer or a router) to the Internet. IPv4 addresses are unique. They are unique in the sense that each address defines one, and only one, connection to the Internet. Two devices on the Internet can never have the same address at the same time. But by using some strategies, an address may be assigned to a device for a time period and then taken away and assigned to another device. On the other hand, if a device operating at the network layer has m connections to the Internet, it needs to have m addresses. A router is such a device which needs as many IP addresses as the number of ports are there in it. 2.1. Address Space A protocol such as IPv4 that defines addresses has an address space. An address space is the total number of addresses used by the protocol. If a protocol uses N bits to define an address, the address space is 2N because each bit can have two different values (0 or 1) and N bits can have 2N values. -

The Internet in Transition: the State of the Transition to Ipv6 in Today's
Please cite this paper as: OECD (2014-04-03), “The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4”, OECD Digital Economy Papers, No. 234, OECD Publishing, Paris. http://dx.doi.org/10.1787/5jz5sq5d7cq2-en OECD Digital Economy Papers No. 234 The Internet in Transition: The State of the Transition to IPv6 in Today's Internet and Measures to Support the Continued Use of IPv4 OECD FOREWORD This report was presented to the OECD Working Party on Communication, Infrastructures and Services Policy (CISP) in June 2013. The Committee for Information, Computer and Communications Policy (ICCP) approved this report in December 2013 and recommended that it be made available to the general public. It was prepared by Geoff Huston, Chief Scientist at the Asia Pacific Network Information Centre (APNIC). The report is published on the responsibility of the Secretary-General of the OECD. Note to Delegations: This document is also available on OLIS under reference code: DSTI/ICCP/CISP(2012)8/FINAL © OECD 2014 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 TABLE OF CONTENTS FOREWORD ................................................................................................................................................... 2 THE INTERNET IN TRANSITION: THE STATE OF THE TRANSITION TO IPV6 IN TODAY'S INTERNET AND MEASURES TO SUPPORT THE CONTINUED USE OF IPV4 .......................... 4 -

Multitech Bluetooth Network Access Point Administrator Guide S000619 Rev 1.2 for Use with Model: MT200B2E
MultiTech Bluetooth® Network Access Point Administrator Guide MultiTech Bluetooth Network Access Point Administrator Guide S000619 Rev 1.2 For use with model: MT200B2E Copyright This publication may not be reproduced, in whole or in part, without the specific and express prior written permission signed by an executive officer of Multi-Tech Systems, Inc. All rights reserved. Copyright © 2015 by Multi-Tech Systems, Inc. Multi-Tech Systems, Inc. makes no representations or warranties, whether express, implied or by estoppels, with respect to the content, information, material and recommendations herein and specifically disclaims any implied warranties of merchantability, fitness for any particular purpose and non- infringement. Multi-Tech Systems, Inc. reserves the right to revise this publication and to make changes from time to time in the content hereof without obligation of Multi-Tech Systems, Inc. to notify any person or organization of such revisions or changes. Trademarks MultiTech, MultiConnect, and the MultiTech logo are registered trademarks of Multi-Tech Systems, Inc. Bluetooth is a registered trademark of Bluetooth SIG, Inc. All other brand and product names are trademarks or registered trademarks of their respective companies. Contacting MultiTech Knowledge Base The Knowledge Base provides immediate access to support information and resolutions for all MultiTech products. Visit http://www.multitech.com/kb.go. Support Portal To create an account and submit a support case directly to our technical support team, visit: https://support.multitech.com Support Business Hours: M-F, 9am to 5pm CT Country By Email By Phone Europe, Middle East, Africa: [email protected] +(44) 118 959 7774 U.S., Canada, all others: [email protected] (800) 972-2439 or (763) 717-5863 World Headquarters Multi-Tech Systems, Inc. -

INTRODUCTION to SUBNETTING How to Maximize Network Addresses
Volume 1 • Issue 8 September–October 2000 Introduction to Industrial Ethernet, Part 5. Part 4 was featured in Issue 6, the MAY–JUNE 2000. If you would like a copy, please send your request to EXTENSION [email protected] A Technical Supplement to control NETWORK © 2000 Contemporary Control Systems, Inc. INTRODUCTION TO SUBNETTING How to maximize network addresses. By George Thomas, Contemporary Controls INTRODUCTION address to distinguish it from the Class Addressing other computers. With IP In a previous article we discussed addressing, servers and IPv4 is called a classful system the Internet Protocol and the workstations are all termed hosts under RFC 761 with IP addresses structure of IP addresses. An IP but each address not only identifies being defined as belonging to one address identifies the source and a host but the address of the of five classes A, B, C, D or E. destination of a directed or unicast network on which the host resides. Classes A, B and C define different possible combinations of network message and is defined in RFC 761. This is because IP is an and host addresses. Class D is IPv4 is the most common version internetworking protocol that not reserved for multicasting. of IP addressing requiring 32-bit only allows communication Multicasting is the ability of one addresses. Although IPv6, the 128- between hosts on the same host to communicate with many bit version, will be used in the network, but communication other hosts with one transmission future, this article will restrict the between hosts on different and is beyond the scope of this discussion to IPv4. -

Empirical Analysis of the Effects and the Mitigation of Ipv4 Address Exhaustion
TECHNISCHE UNIVERSITÄT BERLIN FAKULTÄT FÜR ELEKTROTECHNIK UND INFORMATIK LEHRSTUHL FÜR INTELLIGENTE NETZE UND MANAGEMENT VERTEILTER SYSTEME Empirical Analysis of the Effects and the Mitigation of IPv4 Address Exhaustion vorgelegt von M.Sc. Philipp Richter geboren in Berlin von der Fakultät IV – Elektrotechnik und Informatik der Technischen Universität Berlin zur Erlangung des akademischen Grades DOKTOR DER NATURWISSENSCHAFTEN -DR. RER. NAT.- genehmigte Dissertation Promotionsausschuss: Vorsitzender: Prof. Dr.-Ing. Sebastian Möller, Technische Universität Berlin Gutachterin: Prof. Anja Feldmann, Ph.D., Technische Universität Berlin Gutachter: Prof. Vern Paxson, Ph.D., University of California, Berkeley Gutachter: Prof. Steve Uhlig, Ph.D., Queen Mary University of London Tag der wissenschaftlichen Aussprache: 2. August 2017 Berlin 2017 Abstract IP addresses are essential resources for communication over the Internet. In IP version 4, an address is represented by 32 bits in the IPv4 header; hence there is a finite pool of roughly 4B addresses available. The Internet now faces a fundamental resource scarcity problem: The exhaustion of the available IPv4 address space. In 2011, the Internet Assigned Numbers Authority (IANA) depleted its pool of available IPv4 addresses. IPv4 scarcity is now reality. In the subsequent years, IPv4 address scarcity has started to put substantial economic pressure on the networks that form the Internet. The pools of available IPv4 addresses are mostly depleted and today network operators have to find new ways to satisfy their ongoing demand for IPv4 addresses. Mitigating IPv4 scarcity is not optional, but mandatory: Networks facing address shortage have to take action in order to be able to accommodate additional subscribers and customers. Thus, if not confronted, IPv4 scarcity has the potential to hinder further growth of the Internet. -

Fireware Configuration Example
Configuration Example Use a Branch Office VPN for Failover From a Private Network Link Example configuration files created with — WSM v11.10.1 Revised — 7/22/2015 Use Case In this configuration example, an organization has networks at two sites and uses a private network link to send traffic between the two networks. To make their network configuration more fault-tolerant, they want to set up a secondary route between the networks to use as a backup if the private network link fails, but they do not want to spend money on a second private network connection. To solve this problem, they can use a branch office VPN with dynamic routing. This configuration example provides a model of how you could set up your network to automatically fail over to a branch office VPN if a primary private network connection between two sites becomes unavailable. To use the branch office VPN connection for automatic failover, you must enable dynamic routing on the Firebox at each site. You can use any supported dynamic routing protocol (RIP v1, RIP v2, OSPF, or BGP v4). This configuration example is provided as a guide. Additional configuration settings could be necessary, or more appropriate, for your network environment. Solution Overview A routing protocol is the method routers use to communicate with each other and share information about the status of network routing tables. On the Firebox, static routes are persistent and do not change, even if the link to the next hop goes down. When you enable dynamic routing, the Firebox automatically updates the routing table based on the status of the connection. -

New Techniques to Enhance the Capabilities of the Socks Network Security Protocol
NEW TECHNIQUES TO ENHANCE THE CAPABILITIES OF THE SOCKS NETWORK SECURITY PROTOCOL Mukund Sundararajan and Mohammad S. Obaidat Computer Science Department, Monmouth University, West Long Branch, NJ, U.S.A. Keywords: Security protocols for computer networks, SOCKS, telecommunications, multicast, UDP tunneling. Abstract: SOCKS is an industry standard network security protocol used in private networks to allow secure traversal of application layer traffic through the boundaries of the network. Standardized by IETF in Request for Comments (RFC) 1928 (Leech et al., 1996) as SOCKS Version 5, this protocol has found widespread use in various security frameworks to allow a variety of application layer protocols to securely traverse a firewall. This paper is the result of research performed on the usability of the protocol in application domains such as multicast. We discuss some of the shortcomings of the SOCKS protocol and provide a framework and the methods for enhancing the capabilities of the protocol in areas such as multicast and advanced TCP and UDP capabilities not addressed by the current standard of the protocol. The methods proposed are being implemented in a reference implementation by the authors. 1 INTRODUCTION Operating in a client server mode, application nodes or computers within a SOCKS protected In today’s global and geographically dispersed network are ‘socksified’ by a socks client library that organizational world, network security is a key provides a transparent abstraction layer between the concern to organizations and individuals. With application and the kernel socket library and hides advances in technology, most of today’s the implementation details of the socks protocol from organizations have their key resources and data the application. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -
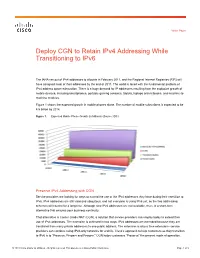
Deploy CGN to Retain Ipv4 Addressing While Transitioning to Ipv6
White Paper Deploy CGN to Retain IPv4 Addressing While Transitioning to IPv6 The IANA ran out of IPv4 addresses to allocate in February 2011, and the Regional Internet Registries (RIR) will have assigned most of their addresses by the end of 2011. The world is faced with the fundamental problem of IPv4 address space exhaustion. There is a huge demand for IP addresses resulting from the explosive growth of mobile devices, including smartphones, portable gaming consoles, tablets, laptops and netbooks, and machine-to- machine modules. Figure 1 shows the expected growth in mobile phones alone. The number of mobile subscribers is expected to be 4.5 billion by 2014. Figure 1. Expected Mobile Phone Growth (in Millions) (Source: IDC) Preserve IPv4 Addressing with CGN Service providers are looking for ways to extend the use of the IPv4 addresses they have during their transition to IPv6. IPv4 addresses are still valid and ubiquitous, and not everyone is using IPv6 yet, so the two addressing schemes will coexist for a long time. Although new IPv4 addresses are not available, there is a short-term alternative that ensures your business continuity. That alternative is Carrier Grade NAT (CGN), a solution that service providers can employ today to extend their use of IPv4 addresses. The extension is achieved in two ways: IPv4 addresses are extended because they are translated from many private addresses to one public address. The extension is also a time extension–-service providers can continue using IPv4-only networks for a while. Cisco’s approach to help customers as they transition to IPv6 is to “Preserve, Prepare and Prosper.” CGN helps customers “Preserve” the present mode of operation.