Programmability Configuration Guide, Cisco IOS XE Bengaluru 17.6.X
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux Journal | January 2016 | Issue
™ AUTOMATE Full Disk Encryption Since 1994: The Original Magazine of the Linux Community JANUARY 2016 | ISSUE 261 | www.linuxjournal.com IMPROVE + Enhance File Transfer Client-Side Performance Security for Users Making Sense of Profiles and RC Scripts ABINIT for Computational Chemistry Research Leveraging Ad Blocking WATCH: ISSUE Audit Serial OVERVIEW Console Access V LJ261-January2016.indd 1 12/17/15 8:35 PM Improve Finding Your Business Way: Mapping Processes with Your Network Practical books an Enterprise to Improve Job Scheduler Manageability for the most technical Author: Author: Mike Diehl Bill Childers Sponsor: Sponsor: people on the planet. Skybot InterMapper DIY Combating Commerce Site Infrastructure Sprawl Author: Reuven M. Lerner Author: GEEK GUIDES Sponsor: GeoTrust Bill Childers Sponsor: Puppet Labs Get in the Take Control Fast Lane of Growing with NVMe Redis NoSQL Author: Server Clusters Mike Diehl Author: Sponsor: Reuven M. Lerner Silicon Mechanics Sponsor: IBM & Intel Download books for free with a Linux in Apache Web simple one-time registration. the Time Servers and of Malware SSL Encryption Author: Author: http://geekguide.linuxjournal.com Federico Kereki Reuven M. Lerner Sponsor: Sponsor: GeoTrust Bit9 + Carbon Black LJ261-January2016.indd 2 12/17/15 8:35 PM Improve Finding Your Business Way: Mapping Processes with Your Network Practical books an Enterprise to Improve Job Scheduler Manageability for the most technical Author: Author: Mike Diehl Bill Childers Sponsor: Sponsor: people on the planet. Skybot InterMapper DIY Combating Commerce Site Infrastructure Sprawl Author: Reuven M. Lerner Author: GEEK GUIDES Sponsor: GeoTrust Bill Childers Sponsor: Puppet Labs Get in the Take Control Fast Lane of Growing with NVMe Redis NoSQL Author: Server Clusters Mike Diehl Author: Sponsor: Reuven M. -
Purchases from $1K-$5K
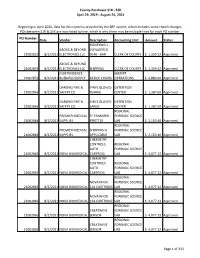
County Purchases $1K - $5K April 29, 2019 - August 31, 2021 Beginning in April 2020, data for this report is provided by the ERP system, which includes some report changes. POs between $1K & $5K are now listed by line, which is why there may be multiple lines for each PO number. PO Number Date Vendor Description Accounting Unit Amount Status HONEYWELL ABOVE & BEYOND VOYAGERCG 21002855 8/2/2021 ELECTRONICS LLC 9540 - BAR CLERK OF COURTS $ 1,359.12 Approved ABOVE & BEYOND 21002855 8/2/2021 ELECTRONICS LLC SHIPPING CLERK OF COURTS $ 1,359.12 Approved INDEPENDENCE SHERIFF 21002859 8/2/2021 BUSINESS SUPPLY OFFICE CHAIRS OPERATIONS $ 4,880.00 Approved DARLING FIRE & VINYL GLOVES- DETENTION 21002862 8/2/2021 SAFETY CO XLARGE CENTER $ 1,387.60 Approved DARLING FIRE & VINYL GLOVES- DETENTION 21002862 8/2/2021 SAFETY CO LARGE CENTER $ 1,387.60 Approved REGIONAL PREMIER MEDICAL 3" TRANSFER FORENSIC SCIENCE 21002864 8/2/2021 SUPPLIES PIPETTES LAB $ 2,150.40 Approved REGIONAL PREMIER MEDICAL SHIPPING IF FORENSIC SCIENCE 21002864 8/2/2021 SUPPLIES APPLICABLE LAB $ 2,150.40 Approved CHEMISTRY CONTROLS REGIONAL AUTO FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CARTRIDG LAB $ 4,077.12 Approved CHEMISTRY CONTROLS REGIONAL AUTO FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CARTRIDG LAB $ 4,077.12 Approved REGIONAL NOVA PHOX FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CAL CARTRIDGE LAB $ 4,077.12 Approved REGIONAL NOVA PHOX FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CAL CARTRIDGE LAB $ 4,077.12 Approved REGIONAL CREATININE FORENSIC -

Free Gnu Linux Distributions
Free gnu linux distributions The Free Software Foundation is not responsible for other web sites, or how up-to-date their information is. This page lists the GNU/Linux distributions that are Linux and GNU · Why we don't endorse some · GNU Guix. We recommend that you use a free GNU/Linux system distribution, one that does not include proprietary software at all. That way you can be sure that you are. Canaima GNU/Linux is a distribution made by Venezuela's government to distribute Debian's Social Contract states the goal of making Debian entirely free. The FSF is proud to announce the newest addition to our list of fully free GNU/Linux distributions, adding its first ever small system distribution. Trisquel, Kongoni, and the other GNU/Linux system distributions on the FSF's list only include and only propose free software. They reject. The FSF's list consists of ready-to-use full GNU/Linux systems whose developers have made a commitment to follow the Guidelines for Free. GNU Linux-libre is a project to maintain and publish % Free distributions of Linux, suitable for use in Free System Distributions, removing. A "live" distribution is a Linux distribution that can be booted The portability of installation-free distributions makes them Puppy Linux, Devil-Linux, SuperGamer, SliTaz GNU/Linux. They only list GNU/Linux distributions that follow the GNU FSDG (Free System Distribution Guidelines). That the software (as well as the. Trisquel GNU/Linux is a fully free operating system for home users, small making the distro more reliable through quicker and more traceable updates. -

Adoption and Use of Free and Open Source Software (FOSS) Globally: an Overview and Analysis of Selected Countries
Vol. 3 No. 1 & 2 (2019): Zambia Journal of Library & Information Science (ZAJLIS) Adoption and Use of Free and Open Source Software (FOSS) Globally: An Overview and Analysis of Selected Countries Tuesday Bwalya [email protected]/ [email protected] Dr. Akakandelwa Akakandelwa [email protected]/ [email protected] Department of Library and Information Science The University of Zambia Dr. Milena Dobreva-McPherson [email protected]/ [email protected] Associate Professor in Library and Information Studies University College London (UCL) Qatar Abstract Institutions, individuals and countries are migrating from commercial software (CS) to FOSS mostly because of two reasons: the increase of costs of purchase and maintenance of commercial software against the backdrop of global economic meltdown, and the increased commitment to open content and technologies in key domains such as research and education. In this regard, some governments have implemented policies that compel government departments, public institutions, and quasi-government institutions to adopt FOSS. The purpose of this article is to summarise the outcomes of a study of an international team of researchers that explores FOSS adoption and policies in some selected countries across the globe. The study is a desk research and qualitative descriptive in nature. Literature on 13 countries’ FOSS policies and adoption was collected and analysed in order to accurately describe the adoption of FOSS in the selected countries. The study findings show that many countries have adopted FOSS because it is less costly in comparison to commercial software. Furthermore, the study identified that countries have approached FOSS policy formulation and implementation in varied ways. -

Časopis O Slobodnom Softveru Broj 25
Мај 2014. iBRE! iBČasoRpis o sElobodn!om softveru L Časopis o slobodnom softveru broj 25 7. maj 2014. 31. maj, 2014. Prvo javno izdanje LXQt-а dostupno je za Objavljen je Linux preuzimanje. Mint 17 „Qiana“. Мај 2014. Creative Commons Autorstvo-Nekomercijalno-Deliti pod istim uslovim1a Reč urednika broj 25 Mediji, FLOSS, LiBRE! i prirodna katastrofa riroda, s vremena na vreme, podseti Radio i televizija bili su glavni informativni, P čoveka koliko je mali, koliko su njegove motivacioni i mobilizacioni faktor u kriznoj rukotvorine beznačajne i podseća čoveka situaciji. da nije gospodar sveta, nego smo jedan njegov mali deo. Suočen sa snagom prirode, Najnovije tehnologije su podbacile. Ni čovek zaboravlja stečene navike i oslanja se internet ni mobilna telefonija nisu bili na bazične instinkte. Kada se nešto ovako iskorišćeni u meri koliko je to moguće u katastrofalno desi, „resetovani” na osnovne širenju prave informacije. Moglo bi se reći instinkte, pokazujemo ko smo zapravo, da su te tehnologije bile čak zlou- koliko znamo tj. ne znamo, koliko smo potrebljene za širenje lažnih i „desta- spretni, organizovani, gde smo ranjivi, kako bilišućih” informacija. Ova kritika ide smo pripremljeni, šta nismo na vreme direktno na račun Vlade Srbije i državnih uradili, a trebalo je, šta smo uradili, a organa. Državni organi još nisu shvatili nismo smeli pa sad trpimo posledice i tako moć ICT-a. Prepuštanje ICT-a stihiji i dalje. nepostojanje zvaničnih informacija mogu samo da dovedu do širenja dezinformacija Glavna opasnost od prirodne nepogode je na internetu, a internet je komunikacioni prošla. Preživelima je sada ostalo da medij broj jedan u svetu. -

Downloaded in Jan 2004; "How Smartphones Work" Symbian Press and Wiley (2006); "Digerati Gliterati" John Wiley and Sons (2001)
HOW OPEN SHOULD AN OPEN SYSTEM BE? Essays on Mobile Computing by Kevin J. Boudreau B.A.Sc., University of Waterloo M.A. Economics, University of Toronto Submitted to the Sloan School of Management in partial fulfillment of the requirements for the degree of MASSACHUBMMIBE OF TECHNOLOGY Doctor of Philosophy at the AUG 2 5 2006 MASSACHUSETTS INSTITUTE OF TECHNOLOGY LIBRARIES June 2006 @ 2006 Massachusetts Institute of Technology. All Rights Reserved. The author hereby grn Institute of Technology permission to and to distribute olo whole or in part. 1 Signature ot Author.. Sloan School of Management 3 May 2006 Certified by. .............................. ............................................ Rebecca Henderson Eastman Kodak LFM Professor of Management Thesis Supervisor Certified by ............. ................ .V . .-.. ' . ................ .... ...... Michael Cusumano Sloan Management Review Professor of Management Thesis Supervisor Certified by ................ Marc Rysman Assistant Professor of Economics, Boston University Thesis Supervisor A ccepted by ........................................... •: °/ Birger Wernerfelt J. C. Penney Professor of Management Science and Chair of PhD Committee ARCHIVES HOW OPEN SHOULD AN OPEN SYSTEM BE? Essays on Mobile Computing by Kevin J. Boudreau Submitted to the Sloan School of Management on 3 May 2006, in partial fulfillment of the requirements for the degree of Doctor of Philosophy Abstract "Systems" goods-such as computers, telecom networks, and automobiles-are made up of mul- tiple components. This dissertation comprises three esssays that study the decisions of system innovators in mobile computing to "open" development of their systems to outside suppliers and the implications of doing so. The first essay considers this issue from the perspective of which components are retained under the control of the original innovator to act as a "platform" in the system. -

Migración a GNU/Linux: Coexistencia En Un Entorno Windows Empresarial
Migración a GNU/Linux: Coexistencia en un entorno Windows empresarial Daniel D’angelo Sabin Grado de Ingeniería Informática Estudios de Informática, Multimedia y Telecomunicación Miquel Colobran Huguet 10/06/2018 Dedicatoria y agradecimientos Dedicado a mi padre, que seguro que se sentiría muy orgulloso. A mi pareja, por quererme, aguantarme y apoyarme en los momentos más difíciles. A mi madre y mi hermano, mi suegra y mi cuñada, por el cariño y sus ánimos. Resumen En el presente trabajo se analiza el sistema informático de una empresa, que actualmente utiliza Microsoft Windows, por lo que es común que surjan situaciones como infección por virus, lentitud o inestabilidad. Por otro lado, los costes del software son una carga difícil de asumir en momentos de crisis e inestabilidad financiera. Como solución, se plantea una migración a software libre, con lo que se pretende ahorrar en los costes de software y de hardware. Se hace un estudio de las necesidades de la empresa y de su estado actual para elegir las soluciones más adecuadas de software libre y permitir una migración exitosa. La empresa objeto del trabajo está situada en Brasil y cuenta con varias sucursales. Se ha propuesto realizar un proyecto piloto en la sucursal más pequeña para probar su viabilidad y, así, en caso de éxito poder replicarlo a toda la organización. Como la empresa y sus clientes están situados en Brasil, la legislación europea de protección de datos no aplica. Actualmente, Brasil no cuenta con una ley de protección de datos (sin embargo, se encuentra actualmente en fase de anteproyecto). -

Macroecological and Macroevolutionary Patterns Emerge in the Universe of GNU/Linux Operating Systems Petr Keil, A
Macroecological and macroevolutionary patterns emerge in the universe of GNU/Linux operating systems Petr Keil, A. A. M. Macdonald, Kelly S. Ramirez, Joanne M. Bennett, Gabriel E. Garcia-Pena, Benjamin Yguel, Bérenger Bourgeois, Carsten Meyer To cite this version: Petr Keil, A. A. M. Macdonald, Kelly S. Ramirez, Joanne M. Bennett, Gabriel E. Garcia-Pena, et al.. Macroecological and macroevolutionary patterns emerge in the universe of GNU/Linux operating systems. Ecography, Wiley, 2018, 41 (11), pp.1788-1800. 10.1111/ecog.03424. hal-02621181 HAL Id: hal-02621181 https://hal.inrae.fr/hal-02621181 Submitted on 26 May 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License doi: 10.1111/ecog.03424 41 1788– 1800 ECOGRAPHY Research Macroecological and macroevolutionary patterns emerge in the universe of GNU/Linux operating systems Petr Keil, A. A. M. MacDonald, Kelly S. Ramirez, Joanne M. Bennett, Gabriel E. García-Peña, Benjamin Yguel, Bérenger Bourgeois and Carsten Meyer P. Keil (http://orcid.org/0000-0003-3017-1858) ([email protected]) and J. M. Bennett, German Centre for Integrative Biodiversity Research (iDiv) Halle- Jena-Leipzig, Leipzig, Germany. -

News from the Fast Moving World of Embedded Linux
tomers and other Internet appliance and Linux software developers will benefit from the new website because it leverages open source technology into non-X86 platforms and ports. Software developers are encouraged to contribute to the embedded, real-time kernel. Content for the website will consist of the real-time kernel source code, documentation, mailing lists and links to similar, helpful Linux websites. Coollogic encourages those interested in the operating system to become contributors to the site, in order to maximize usage of the RT kernel and acceptance of embedded Linux operating systems. “The promotion of the free software as a serious solution and alternative to other operating systems is essential to the success of embedded Linux,” said Powers. Other content to be developed for the site includes directories of News from the fast moving world of compatible hardware and software, online bug tracking, and Embedded Linux . online version control. Coollogic is sponsoring the website, and will manage and contribute to the content of www.rtkernel.org. TeamLinux establishes West Coast presence For more information, go to http://www.coollogic.com/. TeamLinux Corporation announced a new US West Coast pres- ence through its acquisition of Edge Technology Solutions (Edge) New company will focus on Linux-based of Irvine, CA. This move closely follows similar acquisitions in clustered computers Austin, TX and Dayton, OH, announced last month. Alta Technology, a leading developer and supplier of high-per- formance computing solutions, has formed Linux NetworX Inc. The Edge acquisition results in increased revenues, user pro- The new company will use the Linux operating system as it ductivity, customer satisfaction, reliability, and security. -

Getting Started Guide Release 6.X Contents
Getting Started Guide Release 6.x Contents 1 Preface 1 1.1 About the Getting Started Guide...................................1 1.2 Conventions.............................................1 2 About Vortex Opensplice2 2.1 Why Vortex OpenSplice.......................................2 2.2 Vortex OpenSplice Architecture...................................3 2.3 Single Process Library Architecture.................................3 2.4 Shared Memory architecture.....................................4 2.5 Vortex OpenSplice Features and Benefits..............................5 2.6 Conclusion..............................................6 3 Product Details 7 3.1 Key Components...........................................7 3.2 Language and Compiler Bindings..................................8 3.3 Interaction patterns..........................................8 3.4 Support for evolutionary data models................................9 3.5 Building your own C++.......................................9 3.6 Platforms...............................................9 4 Documentation and Support 10 4.1 Vortex OpenSplice Documentation Set............................... 12 4.2 Information Sources......................................... 13 4.3 Support................................................ 13 5 Installation and Configuration 14 5.1 Vortex OpenSplice Development and Run-Time.......................... 14 5.2 Installation for UNIX and Windows Platforms........................... 14 5.3 Installation on Other Platforms................................... 15 5.4 Configuration............................................ -

Building Xenobuntu Linux Distribution for Teaching and Prototyping Real-Time Operating Systems
(IJACSA) International Journal of Advanced Computer Science and Applications, Vol. 2, No.2, February 2011 Building XenoBuntu Linux Distribution for Teaching and Prototyping Real-Time Operating Systems Nabil LITAYEM, Ahmed BEN ACHBALLAH, Slim BEN SAOUD Department of Electrical Engineering - INSAT, University of Carthage, TUNISIA {nabil.litayem, ahmed.achballah, slim.bensaoud}@gmail.com Abstract- This paper describes the realization of a new Linux In this paper, we present the interest of using Xenomai and distribution based on Ubuntu Linux and Xenomai Real-Time Ubuntu as live installable DVD for teaching real-time framework. This realization is motivated by the eminent need of operating systems and rapid real-time applications real-time systems in modern computer science courses. The prototyping. Technical choices and benefits of the chosen majority of the technical choices are made after qualitative solutions will be discussed. comparison. The main goal of this distribution is to offer standard Operating Systems (OS) that include Xenomai The remainder of this paper is organized as follows. infrastructure and the essential tools to begin hard real-time Section 2 presents a survey of RTOS market and discusses application development inside a convivial desktop environment. both of the classic solution and the Linux-based alternatives. The released live/installable DVD can be adopted to emulate The Remastering solutions and available tools are detailed in several classic RTOS Application Program Interfaces (APIs), Section 3. Section 4 describes the realization of our live DVD. directly use and understand real-time Linux in convivial desktop Conclusions and discussion are provided in Section 5. environment and prototyping real-time embedded applications. -

Open Source Used in Cisco Prime Network Analysis Module 6.1
Open Source Used In Cisco Prime Network Analysis Module 6.1 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-54439298 OL-31783-01 Open Source Used In Cisco Prime Network Analysis Module 6.1 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-54439298 Contents 1.1 adduser 3.57 :2.0.1.0704076 1.1.1 Available under license 1.2 anacron 2.3 :9.0.0.0704076 1.2.1 Available under license 1.3 at 3.1.10 :3.0.0.0704076 1.3.1 Available under license 1.4 atm 2.4.1 :1.0.2.0501961 1.4.1 Available under license 1.5 base-passwd 3.5.7 :11.0.0.0704076 1.5.1 Available under license 1.6 bash 3.0 :6.0.2.0801159 1.6.1 Available under license 1.7 bc 1.06 :3.0.0.0702771 1.7.1 Available under license 1.8 beecrypt 4.1.2 :4.0.0.0801182 1.8.1 Available under license 1.9 bind 9.4.0b2 :1.0.0.0704076 1.9.1 Available under license 1.10 bzip2_32 1.0.3 :1.0.0.0704076 1.10.1 Available under license 1.11 coredumper 1.2.1 :1 1.11.1 Available under license 1.12 cracklib-libs 2.7