Linux Journal | January 2016 | Issue
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FY 2011 Annual Report
We're software roadies. Software Freedom Conservancy is a public charity that acts as a non-profit home for dozens of Free, Libre, and Open Source Software (FLOSS) projects. Conservancy©s charitable mission is to help improve, develop, and defend FLOSS, and we do that by providing business, legal, and administrative services to our member projects. We have the honor of working with member projects comprised of, in our humble opinion, many of the best software developers in the world. Some of our member projects develop system software so ubiquitous that it permeates virtually every part of our society©s electronics-driven lifestyle. Other member projects are redefining how software will be written and even how computer science will be taught to the next generation of developers. Still others find their niche by solving a small-but- persistent problem better than anyone else ± and attract a cult following of users because of it. And, best of all, all of our member projects release their software under a license that allows the public to study, use, improve, and share the source code. Conservancy provides all of our ªrock starº member projects with a comprehensive suite of services, and then we get out of their way to let them do what they do best: write great software for the public©s benefit. Our structure. Conservancy acts as a fiscal sponsor to our member projects. We©ve engaged the leadership of each member project©s developer community and executed a fiscal sponsorship agreement that allows us to adopt that project as an official part of Conservancy©s corporate structure. -

Linux Journal | August 2014 | Issue
™ SPONSORED BY Since 1994: The Original Magazine of the Linux Community AUGUST 2014 | ISSUE 244 | www.linuxjournal.com PROGRAMMING HOW-TO: + OpenGL Build, Develop Programming and Validate Creation of RPMs USE VAGRANT Sysadmin Cloud for an Easier Troubleshooting Development with dhclient Workflow Tips for PROMISE Becoming a THEORY Web Developer An In-Depth A Rundown Look of Linux for Recreation V WATCH: ISSUE OVERVIEW LJ244-Aug2014.indd 1 7/23/14 6:56 PM Get the automation platform that makes it easy to: Build Infrastructure Deploy Applications Manage In your data center or in the cloud. getchef.com LJ244-Aug2014.indd 2 7/23/14 11:41 AM Are you tiredtiered of of dealing dealing with with proprietary proprietary storage? storage? ® 9%2Ä4MHÆDCÄ2SNQ@FD ZFS Unified Storage zStax StorCore from Silicon - From modest data storage needs to a multi-tiered production storage environment, zStax StorCore zStax StorCore 64 zStax StorCore 104 The zStax StorCore 64 utilizes the latest in The zStax StorCore 104 is the flagship of the dual-processor Intel® Xeon® platforms and fast zStax product line. With its highly available SAS SSDs for caching. The zStax StorCore 64 configurations and scalable architecture, the platform is perfect for: zStax StorCore 104 platform is ideal for: VPDOOPHGLXPRIILFHILOHVHUYHUV EDFNHQGVWRUDJHIRUYLUWXDOL]HGHQYLURQPHQWV VWUHDPLQJYLGHRKRVWV PLVVLRQFULWLFDOGDWDEDVHDSSOLFDWLRQV VPDOOGDWDDUFKLYHV DOZD\VDYDLODEOHDFWLYHDUFKLYHV TalkTalk with with an anexpert expert today: today: 866-352-1173 866-352-1173 - http://www.siliconmechanics.com/zstax LJ244-Aug2014.indd 3 7/23/14 11:41 AM AUGUST 2014 CONTENTS ISSUE 244 PROGRAMMING FEATURES 64 Vagrant 74 An Introduction to How to use Vagrant to create a OpenGL Programming much easier development workflow. -

Download This Issue
Editorial Dru Lavigne, Thomas Kunz, François Lefebvre Open is the New Closed: How the Mobile Industry uses Open Source to Further Commercial Agendas Andreas Constantinou Establishing and Engaging an Active Open Source Ecosystem with the BeagleBoard Jason Kridner Low Cost Cellular Networks with OpenBTS David Burgess CRC Mobile Broadcasting F/LOSS Projects François Lefebvre Experiences From the OSSIE Open Source Software Defined Radio Project Carl B. Dietrich, Jeffrey H. Reed, Stephen H. Edwards, Frank E. Kragh The Open Source Mobile Cloud: Delivering Next-Gen Mobile Apps and Systems Hal Steger The State of Free Software in Mobile Devices Startups Bradley M. Kuhn Recent Reports Upcoming Events March Contribute 2010 March 2010 Editorial Dru Lavigne, Thomas Kunz, and François Lefebvre discuss the 3 editorial theme of Mobile. Open is the New Closed: How the Mobile Industry uses Open Source to Further Commercial Agendas Andreas Constantinou, Research Director at VisionMobile, PUBLISHER: examines the many forms that governance models can take and 5 The Open Source how they are used in the mobile industry to tightly control the Business Resource is a roadmap and application of open source projects. monthly publication of the Talent First Network. Establishing and Engaging an Active Open Source Ecosystem with Archives are available at the BeagleBoard the website: Jason Kridner, open platforms principal architect at Texas 9 http://www.osbr.ca Instruments Inc., introduces the BeagleBoard open source community. EDITOR: Low Cost Cellular Networks with OpenBTS Dru Lavigne David Burgess, Co-Founder of The OpenBTS Project, describes 14 [email protected] how an open source release may have saved the project. -

Programmability Configuration Guide, Cisco IOS XE Bengaluru 17.6.X
Programmability Configuration Guide, Cisco IOS XE Bengaluru 17.6.x First Published: 2021-07-31 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Linux Journal | February 2016 | Issue
™ A LOOK AT KDE’s KStars Astronomy Program Since 1994: The Original Magazine of the Linux Community FEBRUARY 2016 | ISSUE 262 | www.linuxjournal.com + Programming Working with Command How-Tos Arguments in Your Program a Shell Scripts BeagleBone Interview: Katerina Black Barone-Adesi on to Help Brew Beer Developing the Snabb Switch Network Write a Toolkit Short Script to Solve a WATCH: ISSUE Math Puzzle OVERVIEW V LJ262-February2016.indd 1 1/21/16 5:26 PM NEW! Agile Improve Product Business Development Processes with an Enterprise Practical books Author: Ted Schmidt Job Scheduler for the most technical Sponsor: IBM Author: Mike Diehl Sponsor: people on the planet. Skybot Finding Your DIY Way: Mapping Commerce Site Your Network Author: to Improve Reuven M. Lerner Manageability GEEK GUIDES Sponsor: GeoTrust Author: Bill Childers Sponsor: InterMapper Combating Get in the Infrastructure Fast Lane Sprawl with NVMe Author: Author: Bill Childers Mike Diehl Sponsor: Sponsor: Puppet Labs Silicon Mechanics & Intel Download books for free with a Take Control Linux in simple one-time registration. of Growing the Time Redis NoSQL of Malware http://geekguide.linuxjournal.com Server Clusters Author: Author: Federico Kereki Reuven M. Lerner Sponsor: Sponsor: IBM Bit9 + Carbon Black LJ262-February2016.indd 2 1/21/16 5:26 PM NEW! Agile Improve Product Business Development Processes with an Enterprise Practical books Author: Ted Schmidt Job Scheduler for the most technical Sponsor: IBM Author: Mike Diehl Sponsor: people on the planet. Skybot Finding Your DIY Way: Mapping Commerce Site Your Network Author: to Improve Reuven M. Lerner Manageability GEEK GUIDES Sponsor: GeoTrust Author: Bill Childers Sponsor: InterMapper Combating Get in the Infrastructure Fast Lane Sprawl with NVMe Author: Author: Bill Childers Mike Diehl Sponsor: Sponsor: Puppet Labs Silicon Mechanics & Intel Download books for free with a Take Control Linux in simple one-time registration. -

Wetek Tutorial
Tutorial 2014_v1 How to install OpenELEC on WeTek Play Prerequisites: ● WeTek Play ● Micro SD (minimum 4 GB) ● PC/Mac Introduction: WeTek Play is Android TV device, which beside of Android, support booting of Linux based XBMC and OpenELEC from NAND flash and Micro SD too. Basically, if you are going to install Linux XBMC or OpenELEC to MicroSD, it means that you can always have Android running on NAND flash, and Linux XBMC or OpenELEC running from MicroSD. Software and Tools: • OpenELEC for WeTek Play - http://goo.gl/NgFSOM • Win32 Disk Imagger - http://sourceforge.net/projects/win32diskimager/ Installation: 1. Download OpenELEC for WeTek from link above 2. When file wetek-openelec.ar.bz2 is downloaded, extract it with Winrar or 7-Zip, and keep in mind location where you extracted this archive. 3. Insert Micro SD in PC or Notebook 4. Download and Install Win32 Disk Imager application, then run it as Administrator. (Right-click on app icon and select Run as Administrator) Note: After installation Win32 Disk Imager application is located at: Windows 64 bit: C:\Program Files (x86)\ImageWriter Windows 32 bit: C:\Program Files\ImageWriter 5. Click on blue Folder icon and browse for wetek-openelec folder, where inside you will find .img file, and select it. 6. Now, you should select from Devices dropdown menu, letter which represents inserted Micro SD card. 7. Once when You selected Micro SD card, click on Write, confirm everything what Image Wrier may ask you and wait that application burn .img file to Micro SD. 8. Once when burning process is done, remove Micro SD from PC, and insert it in WeTek Play 9. -

Open Source in the Enterprise
Open Source in the Enterprise Andy Oram and Zaheda Bhorat Beijing Boston Farnham Sebastopol Tokyo Open Source in the Enterprise by Andy Oram and Zaheda Bhorat Copyright © 2018 O’Reilly Media. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online edi‐ tions are also available for most titles (http://oreilly.com/safari). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Michele Cronin Interior Designer: David Futato Production Editor: Kristen Brown Cover Designer: Karen Montgomery Copyeditor: Octal Publishing Services, Inc. July 2018: First Edition Revision History for the First Edition 2018-06-18: First Release The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Open Source in the Enterprise, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. The views expressed in this work are those of the authors, and do not represent the publisher’s views. While the publisher and the authors have used good faith efforts to ensure that the informa‐ tion and instructions contained in this work are accurate, the publisher and the authors disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. If any code samples or other technology this work contains or describes is subject to open source licenses or the intellectual property rights of others, it is your responsibility to ensure that your use thereof complies with such licenses and/or rights. -

DM-Relay - Safe Laptop Mode Via Linux Device Mapper
' $ DM-Relay - Safe Laptop Mode via Linux Device Mapper Study Thesis by cand. inform. Fabian Franz at the Faculty of Informatics Supervisor: Prof. Dr. Frank Bellosa Supervising Research Assistant: Dipl.-Inform. Konrad Miller Day of completion: 04/05/2010 &KIT – Universitat¨ des Landes Baden-Wurttemberg¨ und nationales Forschungszentrum in der Helmholtz-Gemeinschaft www.kit.edu % I hereby declare that this thesis is my own original work which I created without illegitimate help by others, that I have not used any other sources or resources than the ones indicated and that due acknowledgment is given where reference is made to the work of others. Karlsruhe, April 5th, 2010 Contents Deutsche Zusammenfassung xi 1 Introduction 1 1.1 Problem Definition . .1 1.2 Objectives . .1 1.3 Methodology . .1 1.4 Contribution . .2 1.5 Thesis Outline . .2 2 Background 3 2.1 Problems of Disk Power Management . .3 2.2 State of the Art . .4 2.3 Summary of this chapter . .8 3 Analysis 9 3.1 Pro and Contra . .9 3.2 A new approach . 13 3.3 Analysis of Proposal . 15 3.4 Summary of this chapter . 17 4 Design 19 4.1 Common problems . 19 4.2 System-Design . 21 4.3 Summary of this chapter . 21 5 Implementation of a dm-module for the Linux kernel 23 5.1 System-Architecture . 24 5.2 Log suitable for Flash-Storage . 28 5.3 Using dm-relay in practice . 31 5.4 Summary of this chapter . 31 vi Contents 6 Evaluation 33 6.1 Methodology . 33 6.2 Benchmarking setup . -

Continuous Auditing of SSH Servers to Mitigate Brute-Force Attacks Phuong M
CAUDIT: Continuous Auditing of SSH Servers To Mitigate Brute-Force Attacks Phuong M. Cao, Yuming Wu, and Subho S. Banerjee, UIUC; Justin Azoff and Alex Withers, NCSA; Zbigniew T. Kalbarczyk and Ravishankar K. Iyer, UIUC https://www.usenix.org/conference/nsdi19/presentation/cao This paper is included in the Proceedings of the 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’19). February 26–28, 2019 • Boston, MA, USA ISBN 978-1-931971-49-2 Open access to the Proceedings of the 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’19) is sponsored by CAUDIT: Continuous Auditing of SSH Servers to Mitigate Brute-Force Attacks Phuong M. Cao1, Yuming Wu1, Subho S. Banerjee1, Justin Azoff2;3, Alexander Withers3, Zbigniew T. Kalbarczyk1, Ravishankar K. Iyer1 1University of Illinois at Urbana-Champaign, 2Corelight, 3National Center for Supercomputing Applications Abstract While only a small fraction of such attempts succeed, they This paper describes CAUDIT1, an operational system have led to major misuses in 51% of 1,800 surveyed organi- deployed at the National Center for Supercomputing Applica- zations, with a financial impact of up to $500,000 per organi- tions (NCSA) at the University of Illinois. CAUDIT is a fully zation [7]. automated system that enables the identification and exclusion This paper describes the production deployment of of hosts that are vulnerable to SSH brute-force attacks. Its CAUDIT at the National Center for Supercomputing Ap- key features include: 1) a honeypot for attracting SSH-based plications (NCSA) at the University of Illinois over a period attacks over a /16 IP address range and extracting key meta- of 463 days. -

Raspberry Pi Technology
International Journal of Innovative and Emerging Research in Engineering Volume 2, Issue 3, 2015 Available online at www.ijiere.com International Journal of Innovative and Emerging Research in Engineering e-ISSN: 2394 - 3343 p-ISSN: 2394 - 5494 Raspberry Pi Technology: A Review Harshada Chaudhari Student of Third Year of Computer Engineering, Shri Sant Gadge Baba College of Engineering and Technology, Bhusawal, North Maharashtra University, Jalgaon, Maharashtra, India E-mail: [email protected] ABSTRACT: The Raspberry Pi is a very powerful, small computer having the dimensions of credit card which is invented with the hope of inspiring generation of learners to be creative. This computer uses ARM (Advanced RISC Machines) processor, the processor at the heart of the Raspberry Pi system is a Broadcom BCM2835 system- on-chip (SoC) multimedia processor. This review paper provides a description of the raspberry pi technology which is a very powerful computer. Also it introduces the overall system architecture and the design of hardware components are presented in details. Keywords: ARM, SoC , NOOBS, SD, GP, RPi. I. INTRODUCTION The Raspberry Pi is a small computer, same as the computers with which you’re already familiar. It uses a many different kinds of processors, so can’t install Microsoft Windows on it. But can install several versions of the Linux operating system that appear and feel very much like Windows. Raspberry Pi is also used to surf the internet, to send an email to write a letter using a word processor, but you can too do so much more. Simple to use but powerful, affordable and in addition difficult to break, Raspberry Pi is the perfect device for aspiring computer scientists [1]. -
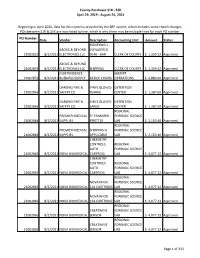
Purchases from $1K-$5K
County Purchases $1K - $5K April 29, 2019 - August 31, 2021 Beginning in April 2020, data for this report is provided by the ERP system, which includes some report changes. POs between $1K & $5K are now listed by line, which is why there may be multiple lines for each PO number. PO Number Date Vendor Description Accounting Unit Amount Status HONEYWELL ABOVE & BEYOND VOYAGERCG 21002855 8/2/2021 ELECTRONICS LLC 9540 - BAR CLERK OF COURTS $ 1,359.12 Approved ABOVE & BEYOND 21002855 8/2/2021 ELECTRONICS LLC SHIPPING CLERK OF COURTS $ 1,359.12 Approved INDEPENDENCE SHERIFF 21002859 8/2/2021 BUSINESS SUPPLY OFFICE CHAIRS OPERATIONS $ 4,880.00 Approved DARLING FIRE & VINYL GLOVES- DETENTION 21002862 8/2/2021 SAFETY CO XLARGE CENTER $ 1,387.60 Approved DARLING FIRE & VINYL GLOVES- DETENTION 21002862 8/2/2021 SAFETY CO LARGE CENTER $ 1,387.60 Approved REGIONAL PREMIER MEDICAL 3" TRANSFER FORENSIC SCIENCE 21002864 8/2/2021 SUPPLIES PIPETTES LAB $ 2,150.40 Approved REGIONAL PREMIER MEDICAL SHIPPING IF FORENSIC SCIENCE 21002864 8/2/2021 SUPPLIES APPLICABLE LAB $ 2,150.40 Approved CHEMISTRY CONTROLS REGIONAL AUTO FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CARTRIDG LAB $ 4,077.12 Approved CHEMISTRY CONTROLS REGIONAL AUTO FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CARTRIDG LAB $ 4,077.12 Approved REGIONAL NOVA PHOX FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CAL CARTRIDGE LAB $ 4,077.12 Approved REGIONAL NOVA PHOX FORENSIC SCIENCE 21002869 8/2/2021 NOVA BIOMEDICAL CAL CARTRIDGE LAB $ 4,077.12 Approved REGIONAL CREATININE FORENSIC -

Praise for the Official Ubuntu Book
Praise for The Official Ubuntu Book “The Official Ubuntu Book is a great way to get you started with Ubuntu, giving you enough information to be productive without overloading you.” —John Stevenson, DZone Book Reviewer “OUB is one of the best books I’ve seen for beginners.” —Bill Blinn, TechByter Worldwide “This book is the perfect companion for users new to Linux and Ubuntu. It covers the basics in a concise and well-organized manner. General use is covered separately from troubleshooting and error-handling, making the book well-suited both for the beginner as well as the user that needs extended help.” —Thomas Petrucha, Austria Ubuntu User Group “I have recommended this book to several users who I instruct regularly on the use of Ubuntu. All of them have been satisfied with their purchase and have even been able to use it to help them in their journey along the way.” —Chris Crisafulli, Ubuntu LoCo Council, Florida Local Community Team “This text demystifies a very powerful Linux operating system . in just a few weeks of having it, I’ve used it as a quick reference a half dozen times, which saved me the time I would have spent scouring the Ubuntu forums online.” —Darren Frey, Member, Houston Local User Group This page intentionally left blank The Official Ubuntu Book Sixth Edition This page intentionally left blank The Official Ubuntu Book Sixth Edition Benjamin Mako Hill Matthew Helmke Amber Graner Corey Burger With Jonathan Jesse, Kyle Rankin, and Jono Bacon Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks.