Lecture 7 Datalink – Ethernet, Home Ethernet Physical Refresher
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1) What Is the Name of an Ethernet Cable That Contains Two
1) What is the name of an Ethernet cable that contains two electrical conductors ? A coaxial cable 2) What are the names of the two common conditions that degrade the signals on c opper-based cables? Crosstal and attenuation 3) Which topology requires the use of terminators? Bus 4) Which of the following topologies is implemented only logically, not physical ly? Ring 5) How many wire pairs are actually used on a typical UTP Ethernet network? Two 6) What is the name of the process of building a frame around network layer info rmation? Data encapsulation 7) Which of the connectors on a network interface adapter transmits data in para llel? The System bus connector 8) Which two of the following hardware resources do network interface adapters a lways require? I/O port address and IRQ 9) What is the name of the process by which a network interface adapter determin es when it should transmit its data over the network? Media Access Control 10) Which bus type is preferred for a NIC that will be connected to a Fast Ether net network? PCI 11) A passive hub does not do which of the following? Transmit management information using SNMP 12) To connect two Ethernet hubs together, you must do which of the following? Connect the uplink port in one hub to a standard port on the other 13) Which term describes a port in a Token Ring MAU that is not part of the ring ? Intelligent 14) A hub that functions as a repeater inhibits the effect of____________? Attenuation 15) You can use which of the following to connect two Ethernet computers togethe r using UTP -

Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern
Switched, Fast, and Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern.. Page 1 of 36 [Figures are not included in this sample chapter] Switched, Fast, and Gigabit Ethernet - 3 - Ethernet, Fast Ethernet, and Gigabit Ethernet Standards This chapter discusses the theory and standards of the three versions of Ethernet around today: regular 10Mbps Ethernet, 100Mbps Fast Ethernet, and 1000Mbps Gigabit Ethernet. The goal of this chapter is to educate you as a LAN manager or IT professional about essential differences between shared 10Mbps Ethernet and these newer technologies. This chapter focuses on aspects of Fast Ethernet and Gigabit Ethernet that are relevant to you and doesn’t get into too much technical detail. Read this chapter and the following two (Chapter 4, "Layer 2 Ethernet Switching," and Chapter 5, "VLANs and Layer 3 Switching") together. This chapter focuses on the different Ethernet MAC and PHY standards, as well as repeaters, also known as hubs. Chapter 4 examines Ethernet bridging, also known as Layer 2 switching. Chapter 5 discusses VLANs, some basics of routing, and Layer 3 switching. These three chapters serve as a precursor to the second half of this book, namely the hands-on implementation in Chapters 8 through 12. After you understand the key differences between yesterday’s shared Ethernet and today’s Switched, Fast, and Gigabit Ethernet, evaluating products and building a network with these products should be relatively straightforward. The chapter is split into seven sections: l "Ethernet and the OSI Reference Model" discusses the OSI Reference Model and how Ethernet relates to the physical (PHY) and Media Access Control (MAC) layers of the OSI model. -

Ethernet and Wifi
Ethernet and WiFi hp://xkcd.com/466/ CSCI 466: Networks • Keith Vertanen • Fall 2011 Overview • Mul?ple access networks – Ethernet • Long history • Dominant wired technology – 802.11 • Dominant wireless technology 2 Classic Ethernet • Ethernet – luminferous ether through which electromagne?c radiaon once thought to propagate – Carrier Sense, Mul?ple Access with Collision Detec?on (CSMA/CD) – IEEE 802.3 Robert Metcalfe, co- inventor of Ethernet 3 Classic Ethernet • Ethernet – Xerox Ethernet standardized as IEEE 802.3 in 1983 – Xerox not interested in commercializing – Metcalfe leaves and forms 3Com 4 Ethernet connec?vity • Shared medium – All hosts hear all traffic on cable – Hosts tapped the cable – 2500m maximum length – May include repeaters amplifying signal – 10 Mbps bandwidth 5 Classic Ethernet cabling Cable aSer being "vampire" tapped. Thick Ethernet cable (yellow), 10BASE-5 transceivers, cable tapping tool (orange), 500m maximum length. Thin Ethernet cable (10BASE2) with BNC T- connector, 185m maximum length. 6 Ethernet addressing • Media Access Control address (MAC) – 48-bit globally unique address • 281,474,976,710,656 possible addresses • Should last ?ll 2100 • e.g. 01:23:45:67:89:ab – Address of all 1's is broadcast • FF:FF:FF:FF:FF:FF 7 Ethernet frame format • Frame format – Manchester encoded – Preamble products 10-Mhz square wave • Allows clock synch between sender & receiver – Pad to at least 64-bytes (collision detec?on) Ethernet 802.3 AlternaWng 0's 48-bit MAC and 1's (except addresses SoF of 11) 8 Ethernet receivers • Hosts listens to medium – Deliver to host: • Any frame with host's MAC address • All broadcast frames (all 1's) • Mul?cast frames (if subscribed to) • Or all frames if in promiscuous mode 9 MAC sublayer • Media Access Control (MAC) sublayer – Who goes next on a shared medium – Ethernet hosts can sense if medium in use – Algorithm for sending data: 1. -

Gigabit Ethernet
Ethernet Technologies and Gigabit Ethernet Professor John Gorgone Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 1 Topics • Origins of Ethernet • Ethernet 10 MBS • Fast Ethernet 100 MBS • Gigabit Ethernet 1000 MBS • Comparison Tables • ATM VS Gigabit Ethernet •Ethernet8SummaryCopyright 1998, John T. Gorgone, All Rights Reserved 2 Origins • Original Idea sprang from Abramson’s Aloha Network--University of Hawaii • CSMA/CD Thesis Developed by Robert Metcalfe----(1972) • Experimental Ethernet developed at Xerox Palo Alto Research Center---1973 • Xerox’s Alto Computers -- First Ethernet Ethernet8systemsCopyright 1998, John T. Gorgone, All Rights Reserved 3 DIX STANDARD • Digital, Intel, and Xerox combined to developed the DIX Ethernet Standard • 1980 -- DIX Standard presented to the IEEE • 1980 -- IEEE creates the 802 committee to create acceptable Ethernet Standard Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 4 Ethernet Grows • Open Standard allows Hardware and Software Developers to create numerous products based on Ethernet • Large number of Vendors keeps Prices low and Quality High • Compatibility Problems Rare Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 5 What is Ethernet? • A standard for LANs • The standard covers two layers of the ISO model – Physical layer – Data link layer Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 6 What is Ethernet? • Transmission speed of 10 Mbps • Originally, only baseband • In 1986, broadband was introduced • Half duplex and full duplex technology • Bus topology Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 7 Components of Ethernet • Physical Medium • Medium Access Control • Ethernet Frame Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 8 CableCable DesignationsDesignations 10 BASE T SPEED TRANSMISSION MAX TYPE LENGTH Ethernet8 Copyright 1998, John T. -
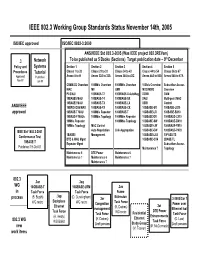
IEEE 802.3 Working Group Standards Status November 14Th, 2005
IEEE 802.3 Working Group Standards Status November 14th, 2005 ISO/IEC approved ISO/IEC 8802-3:2000 ANSI/IEEE Std 802.3-2005 (Was IEEE project 802.3REVam) th .3 Network To be published as 5 Books (Sections) Target publication date – 9 December Policy and Systems Section 1 Section 2 Section 3 Section 4 Section 5 Procedures Tutorial Clause 1 to 20 Clause 21 to 33 Clause 34 to 43 Clause 44 to 54 Clause 56 to 67 Approved Published Annex A to H Annex 22A to 32A Annex 36A to 43C Annex 44A to 50A Annex 58A to 67A Nov-97 Jun-95 CSMA/CD Overview 100Mb/s Overview 1000Mb/s Overview 10Gb/s Overview Subscriber Access MAC MII GMII MDC/MDIO Overview PLS/AUI 100BASE-T2 1000BASE-X AutoNeg XGMII OAM 10BASE5 MAU 100BASE-T4 1000BASE-SX XAUI Multi-point MAC 10BASE2 MAU 100BASE-TX 1000BASE-LX XSBI Control ANSI/IEEE 10BROAD36 MAU 100BASE-FX 1000BASE-CX 10GBASE-SR 100BASE-LX10 approved 10BASE-T MAU 100Mb/s Repeater 1000BASE-T 10GBASE-LR 100BASE-BX10 10BASE-F MAUs 100Mb/s Topology 1000Mb/s Repeater 10GBASE-ER 1000BASE-LX10 10Mb/s Repeater 1000Mb/s Topology 10GBASE-SW 1000BASE-BX10 10Mb/s Topology MAC Control 10GBASE-LW 1000BASE-PX10 IEEE Std 1802.3-2001 Auto Negotiation Link Aggregation 10GBASE-EW 1000BASE-PX20 Conformance Test 1BASE5 Management 10GBASE-LX4 10PASS-TS DTE & MAU Mgmt 10GBASE-CX4 2BASE-TL 10BASE-T Repeater Mgmt Subscriber Access Published 19-Oct-01 Maintenance 7 Topology Maintenance 6 DTE Power Maintenance 6 Maintenance 7 Maintenance 6 Maintenance 7 Maintenance 7 802.3 .3an .3aq WG 10GBASE-T 10GBASE-LRM .3as in Task Force Task Force Frame .3ap process (B. -

Datasheet - Public
Marvell® Alaska® 88E1510/88E1518/88E1512/88E1514 Integrated 10/100/1000 Mbps Energy Efficient Ethernet Transceiver Datasheet - Public Doc. No. MV-S107146-U0 Rev. E June 3, 2021 Document Classification: Public Cover Alaska 88E1510/88E1518/88E1512/88E1514 Datasheet - Public THIS DOCUMENT AND THE INFORMATION FURNISHED IN THIS DOCUMENT ARE PROVIDED "AS IS" WITHOUT ANY WARRANTY. MARVELL AND ITS AFFILIATES EXPRESSLY DISCLAIM AND MAKE NO WARRANTIES OR GUARANTEES, WHETHER EXPRESS, ORAL, IMPLIED, STATUTORY, ARISING BY OPERATION OF LAW, OR AS A RESULT OF USAGE OF TRADE, COURSE OF DEALING, OR COURSE OF PERFORMANCE, INCLUDING THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT. This document, including any software or firmware referenced in this document, is owned by Marvell or Marvell's licensors, and is protected by intellectual property laws. No license, express or implied, to any Marvell intellectual property rights is granted by this document. The information furnished in this document is provided for reference purposes only for use with Marvell products. It is the user's own responsibility to design or build products with this information. Marvell products are not authorized for use as critical components in medical devices, military systems, life or critical support devices, or related systems. Marvell is not liable, in whole or in part, and the user will indemnify and hold Marvell harmless for any claim, damage, or other liability related to any such use of Marvell products. Marvell assumes no responsibility for the consequences of use of such information or for any infringement of patents or other rights of third parties that may result from its use. -

TR-200 Using EPON in the Context of TR-101
TECHNICAL REPORT TR-200 Using EPON in the Context of TR-101 Issue: 1 Corrigendum 1 Issue Date: July 2011 © The Broadband Forum. All rights reserved. Using EPON in the Context of TR-101 TR-200 Issue 1 Corrigendum 1 Notice The Broadband Forum is a non-profit corporation organized to create guidelines for broadband network system development and deployment. This Broadband Forum Technical Report has been approved by members of the Forum. This Broadband Forum Technical Report is not binding on the Broadband Forum, any of its members, or any developer or service provider. This Broadband Forum Technical Report is subject to change, but only with approval of members of the Forum. This Technical Report is copyrighted by the Broadband Forum, and all rights are reserved. Portions of this Technical Report may be copyrighted by Broadband Forum members. This Broadband Forum Technical Report is provided AS IS, WITH ALL FAULTS. ANY PERSON HOLDING A COPYRIGHT IN THIS BROADBAND FORUM TECHNICAL REPORT, OR ANY PORTION THEREOF, DISCLAIMS TO THE FULLEST EXTENT PERMITTED BY LAW ANY REPRESENTATION OR WARRANTY, EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTY: (A) OF ACCURACY, COMPLETENESS, MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, OR TITLE; (B) THAT THE CONTENTS OF THIS BROADBAND FORUM TECHNICAL REPORT ARE SUITABLE FOR ANY PURPOSE, EVEN IF THAT PURPOSE IS KNOWN TO THE COPYRIGHT HOLDER; (C) THAT THE IMPLEMENTATION OF THE CONTENTS OF THE TECHNICAL REPORT WILL NOT INFRINGE ANY THIRD PARTY PATENTS, COPYRIGHTS, TRADEMARKS OR OTHER RIGHTS. By using this Broadband Forum Technical Report, users acknowledge that implementation may require licenses to patents. -

Physical Layer Compliance Testing for 1000BASE-T Ethernet
Physical Layer Compliance Testing for 1000BASE-T Ethernet –– APPLICATION NOTE Physical Layer Compliance Testing for 1000BASE-T Ethernet APPLICATION NOTE Engineers designing or validating the 1000BASE-T Ethernet 1000BASE-T Physical Layer physical layer on their products need to perform a wide range Compliance Standards of tests, quickly, reliably and efficiently. This application note describes the tests that ensure validation, the challenges To ensure reliable information transmission over a network, faced while testing multi-level signals, and how oscilloscope- industry standards specify requirements for the network’s resident test software enables significant efficiency physical layer. The IEEE 802.3 standard defines an array of improvements with its wide range of tests, including return compliance tests for 1000BASE-T physical layer. These tests loss, fast validation cycles, and high reliability. are performed by placing the device under test in test modes specified in the standard. The Basics of 1000BASE-T Testing While it is recommended to perform as many tests as Popularly known as Gigabit Ethernet, 1000BASE-T has been possible, the following core tests are critical for compliance: experiencing rapid growth. With only minimal changes to IEEE 802.3 Test Mode Test the legacy cable structure, it offers 100 times faster data Reference rates than 10BASE-T Ethernet signals. Gigabit Ethernet, in Peak 40.6.1.2.1 combination with Fast Ethernet and switched Ethernet, offers Test Mode-1 Droof 40.6.1.2.2 Template 40.6.1.2.3 a cost-effective alternative to slow networks. Test Mode-2 Master Jitter 40.6.1.2.5 Test Mode-3 Slave Jitter 1000BASE-T uses four signal pairs for full-duplex Distortion 40.6.1.2.4 transmission and reception over CAT-5 balanced cabling. -

Latticesc/M Broadcom® 2.5 Gbe Physical Layer Interoperability Over CX-4
LatticeSC/M Broadcom® 2.5 GbE Physical Layer Interoperability Over CX-4 August 2007 Technical Note TN1156 Introduction This technical note describes a 1000BASE-X physical layer Gigabit Ethernet interoperability test between a Lat- ticeSC/M device and the Broadcom BCM56580 network switch. The test was limited to the physical layer (up to GMII) of the Gigabit Ethernet protocol stack. Specifically, the document discusses the following topics: • Overview of LatticeSC™ and LatticeSCM™ devices and Broadcom BCM56580 network switch • 1000BASE-X physical layer interoperability setup and results Two significant aspects of the interoperability test need to be highlighted: • The BCM56580 uses a CX-4 HiGig™ port, whereas the LatticeSC Communications Platform Evaluation Board provides an SMA connector. A CX-4 to SMA conversion board was used as a physical medium interface to cre- ate a physical link between both boards. The SMA side of the CX-4 to SMA conversion board has four differential TX/RX channels (10 Gbps bandwidth total), but only one SMA channel (channel 0) was connected to the Lat- ticeSC side. • The 1000BASE-X physical layer interoperability ran at a 2.5-Gbps data rate (3.125-Gbps aggregated rate). Both Lattice and Broadcom support this rate by running a faster speed reference clock that extends the bandwidth capability of 1-Gigabit Ethernet. Gigabit Ethernet Physical Layer The IEEE 802.3-2002 Gigabit Ethernet standard is organized along architectural lines, emphasizing the large-scale separation of the system into two parts: the Media Access Control (MAC) sublayer of the Data Link Layer and the Physical Layer. Figure 1 highlights the sub-layers that constitute the Gigabit Ethernet Physical Layer. -

Towards 100 Gbps Ethernet: Development of Ethernet / Physical Layer Aspects
SEMINAR ON TOPICS IN COMMUNICATIONS ENGINEERING 1 Towards 100 Gbps Ethernet: Development of Ethernet / Physical Layer Aspects Ömer Bulakci Abstract — Physical layer features of Ethernet from the first released clauses and ongoing architecture researches for 100 realization towards the 100 Gb Ethernet (100 GbE) development GbE are elaborated. have been considered. Comparisons of these features are made according to the standardized data rates. Feasible physical layer TABLE I options are then discussed for high data rates. Milestones of 802.3 IEEE Standard I. INTRODUCTION Clause Date of Bit Physical THERNET is the most widely deployed Local Area Name Release Rate Medium Network (LAN) protocol and has been extended to E 802.3a Single Metropolitan Area Networks (MAN) and Wide Area (Thin Ethernet) 1985 10 Mbps Thin Coaxial Networks (WAN) [1]. The major advantages that characterize (Cheapernet) Cable Ethernet can be stated as its cost efficiency, traditional tenfold bit rate increase (from 10 Mbps to 100 Gbps), simplicity, high 802.3i 1990 10 Mbps TP Copper transmission reliability and worldwide interoperability 802.3j 1993 10 Mbps Two MMFs between vendors [2]. TP Copper The first experimental Ethernet was developed during the 802.3u 1995 100 Mbps Two Fibers early 1970s by XEROX Corporation in a coaxial cable (Fast Ethernet) (MMF,SMF) network with a data rate about 3 Mbps [3]. The initial 802.3z 1998 1 Gbps MMF, SMF standardization process of Ethernet was started in 1979 by (Gigabit Ethernet) Digital Equipment Corporation (DEC), Intel and Xerox. In 802.3ab 1999 1 Gbps TP Copper 1980, DIX Standard known as the “Thick Ethernet” was 802.3ae 2002 10 Gbps MMF,SMF released. -

An Ethernet Physical Layer Transceiver for Space
SEPHY: An Ethernet Physical Layer Transceiver for Space J. Lopeza , P.Reviriegob, M. Sánchez-Renedo c, V. Petrovicd, J.F.Dufoure ,J.S.Weilf aArquimea Ingenieria S.L.U, Spain bUniversidad Nebrija, Spain cThales Alenia Space, Spain dIHP microelectronics, Germany eTTT Computerterchnik AG, Austria fAtmel, France [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] Abstract The IEEE 802.3 standard defines many PHYs covering different transmission media and speeds. The most commonly Since its development, Ethernet has experienced an used media in Ethernet are Unshielded Twisted Pairs (UTP). impressive growth and has become the dominant technology Assuming that the space PHY will use UTP, the IEEE 802.3 for wired local area networks. It has also more recently standard provides several alternatives. The most relevant ones expanded beyond computer networks to cover also industrial are: 10BASE-T defined in IEEE 802.3i , 100BASE-TX and automotive networks. This adoption is driven by the defined in IEEE 802.3u, 1000BASE-T defined in IEEE lower costs enabled by reusing existing technology. For 802.3ab and 10GBASE-T defined in IEEE 802.3an. Each of critical applications, Ethernet has to be extended to ensure those standards provides a 10x speed increase over the timely and reliable delivery of frames. A number of previous one, starting with the 10 Mb/s of 10BASE-T. From a technologies that can solve the reliability and real time issues performance point of view, the best would be to select the have been proposed, for example Time Triggered Ethernet highest speed PHY for rad-hard implementation. -

Dp83843 Phyter
DP83843 DP83843 PHYTER Literature Number: SNLS021B DP83843BVJE PHYTER Nov 2013 DP83843BVJE PHYTER General Description Features TheDP83843BVJEisafullfeaturePhysicalLayerdevice —IEEE 802.3 ENDEC with AUI/10BASE-T transceivers withintegratedPMDsublayerstosupportboth10BASE-T and built-in filters and 100BASE-X Ethernet protocols. —IEEE 802.3u 100BASE-TX compatible - directly drives ThisVLSIdeviceisdesignedforeasyimplementationof standard Category 5 UTP, no need for external 10/100Mb/sEthernetLANs.ItinterfacesdirectlytoTwisted 100BASE-TX transceiver Pairmediathroughanexternaltransformerortofiber —Fully Integrated and fully compliant ANSI X3.263 TP- mediaviaindustrystandardelectrical/opticalfiberPMD PMD physical sublayer which includes adaptive equal- transceivers.Thisdevicealsointerfacesdirectlytothe ization and BLW compensation MAClayerthroughtheIEEE802.3ustandardMediaInde- —IEEE802.3u100BASE-FXcompatible-connectsdirect- pendentInterface(MII),ensuringinteroperabilitybetween ly to industry standard Electrical/Optical transceivers products from different vendors. —IEEE 802.3u Auto-Negotiation for automatic speed se- TheDP83843isdesignedwithNationalSemiconductor's lection advancedCMOSprocess.Itssystemarchitectureisbased ontheintegrationofseveralofNational'sindustryproven —IEEE 802.3u compatible Media Independent Interface core technologies: (MII) with Serial Management Interface —IEEE 802.3 ENDEC with AUI/10BASE-T transceiver —Integrated high performance 100 Mb/s clock recovery module to provide the 10 Mb/s functions circuitry requiring no external