How to Accelerate Your Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Proceedings of the Bsdcon 2002 Conference
USENIX Association Proceedings of the BSDCon 2002 Conference San Francisco, California, USA February 11-14, 2002 THE ADVANCED COMPUTING SYSTEMS ASSOCIATION © 2002 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Flexible Packet Filtering: Providing a Rich Toolbox Kurt J. Lidl Deborah G. Lidl Paul R. Borman Zero Millimeter LLC Wind River Systems Wind River Systems Potomac, MD Potomac, MD Mendota Heights, MN [email protected] [email protected] [email protected] Abstract The BSD/OS IPFW packet filtering system is a well engineered, flexible kernel framework for filtering (accepting, rejecting, logging, or modifying) IP packets. IPFW uses the well understood, widely available Berkeley Packet Filter (BPF) system as the basis of its packet matching abilities, and extends BPF in several straightforward areas. Since the first implementation of IPFW, the system has been enhanced several times to support additional functions, such as rate filtering, network address translation (NAT), and traffic flow monitoring. This paper examines the motivation behind IPFW and the design of the system. Comparisons with some contemporary packet filtering systems are provided. Potential future enhancements for the IPFW system are discussed. 1 Packet Filtering: An Overview might choose to copy only this data. -

Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern
Switched, Fast, and Gigabit Ethernet - CH 3 - Ethernet, Fast Ethernet, and Gigabit Ethern.. Page 1 of 36 [Figures are not included in this sample chapter] Switched, Fast, and Gigabit Ethernet - 3 - Ethernet, Fast Ethernet, and Gigabit Ethernet Standards This chapter discusses the theory and standards of the three versions of Ethernet around today: regular 10Mbps Ethernet, 100Mbps Fast Ethernet, and 1000Mbps Gigabit Ethernet. The goal of this chapter is to educate you as a LAN manager or IT professional about essential differences between shared 10Mbps Ethernet and these newer technologies. This chapter focuses on aspects of Fast Ethernet and Gigabit Ethernet that are relevant to you and doesn’t get into too much technical detail. Read this chapter and the following two (Chapter 4, "Layer 2 Ethernet Switching," and Chapter 5, "VLANs and Layer 3 Switching") together. This chapter focuses on the different Ethernet MAC and PHY standards, as well as repeaters, also known as hubs. Chapter 4 examines Ethernet bridging, also known as Layer 2 switching. Chapter 5 discusses VLANs, some basics of routing, and Layer 3 switching. These three chapters serve as a precursor to the second half of this book, namely the hands-on implementation in Chapters 8 through 12. After you understand the key differences between yesterday’s shared Ethernet and today’s Switched, Fast, and Gigabit Ethernet, evaluating products and building a network with these products should be relatively straightforward. The chapter is split into seven sections: l "Ethernet and the OSI Reference Model" discusses the OSI Reference Model and how Ethernet relates to the physical (PHY) and Media Access Control (MAC) layers of the OSI model. -

Campus Networking Best Practices Session 5: Wireless
Campus Networking Best Practices Session 5: Wireless LAN Hervey Allen Dale Smith NSRC & University of Oregon University of Oregon & NSRC [email protected] [email protected] Wireless LAN • Provide wireless network across your campus that has the following characteristics: – Authentication – only allow your users – Roaming – allow users to start up in one section of your network, then move to another location – Runs on your campus network Firewall/ Border Traffic Shaper Router Wireless REN switch Authentication Core Gateway Router Core Servers Network Access Control (NAC) Enterprise Identity Management • Processes and Documentation of users. – Now you must deal with this. – What to use as the back-end user store? • LDAP • Active Directory • Kerberos • Other? – Will this play nice with future use? • email, student/staff information, resource access, ... Identity Management Cont. • An example of such a project can be seen here: – http://ccadmin.uoregon.edu/idm/ • This is a retrofit on to an already retrofitted system. • Learn from others and try to avoid this situation if possible. A Wireless Captive Portal The Wireless Captive Portal • Previous example was very simple. • A Captive Portal is your chance to: – Explain your Acceptable Use Policies – Decide if you must authenticate, or – Allow users on your network and monitor for problems instead (alternate solution). – Anything else? Branding? What's Happening? • remember our initial network diagrams...? • Do you think our hotel built their own solution? • Probably not... Commercial Solutions • Aruba http://www.arubanetworks.com/ • Bradford Networks – http://www.bradfordnetworks.com/ • Cisco NAC Appliance (Clean Access) – http://www.cisco.com/en/US/products/ps6128/ • Cisco Wireless LAN Controllers – http://www.cisco.com/en/US/products/hw/wireless/ • Enterasys http://www.enterasys.com/ • Vernier http://www.verniernetworks.com Open Source Solutions • CoovaChilli (morphed from Chillispot) – http://coova.org/wiki/index.php/CoovaChilli – Uses RADIUS for access and accounting. -

Análise De Usabilidade Da Ferramenta Ipfirewall Para Firewall
Furin e Machado Junior (2011). ANÁLISE DE USABILIDADE DA FERRAMENTA IPFIREWALL PARA FIREWALL Marcelo Antonio Ferreira Furin Graduado em Sistemas de Informação pela LIBERTAS Faculdades Integradas. Dorival Moreira Machado Junior Mestra em Sistemas de Informação e professor da LIBERTAS Faculdades Integradas. 1. INTRODUÇÃO A importância do firewall evidencia-se pela expansão da internet e o consequente aumento de usuários, muitas vezes, sem o conhecimento acerca da proteção de sua rede e sua máquina. Com isso, por meio da ferramenta IPFIREWALL, um filtro de pacotes do sistema operacional FreeBSD, será analisado suas funcionalidades nativas. Outro ponto de destaque para a importância do firewall é evitar que o craker (é o termo usado para designar quem pratica a quebra (ou cracking) de um sistema de segurança, de forma ilegal ou sem ética) invadam os arquivos não autorizados. Dentre as razões para se utilizar o firewall é ajudar a proteger à rede ou computador do usuário de acessos maliciosos de hacker (são indivíduos que elaboram e modificam software e hardware de computadores, seja desenvolvendo funcionalidades novas, seja adaptando as antigas). 2. PROBLEMA DE PESQUISA Utilizando a ferramenta IPFIREWALL para firewall, sem usar quaisquer, ferramentas para auxílio, tem-se o ambiente no qual se origina a pergunta de pesquisa que norteará o presente estudo: No que é possível fazer com as funcionalidades nativas do IPFW? 2.1 OBJETIVO GERAL O objetivo deste trabalho é descrever todas as funcionalidades nativas do IPFW, o qual vem como firewall padrão no sistema operacional FreeBSD, e comprovar que é 100 Furin e Machado Junior (2011). possível fazer o mesmo trabalho realizado pelo IPTABLES gerando um script com as regras. -

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

Ethernet and Wifi
Ethernet and WiFi hp://xkcd.com/466/ CSCI 466: Networks • Keith Vertanen • Fall 2011 Overview • Mul?ple access networks – Ethernet • Long history • Dominant wired technology – 802.11 • Dominant wireless technology 2 Classic Ethernet • Ethernet – luminferous ether through which electromagne?c radiaon once thought to propagate – Carrier Sense, Mul?ple Access with Collision Detec?on (CSMA/CD) – IEEE 802.3 Robert Metcalfe, co- inventor of Ethernet 3 Classic Ethernet • Ethernet – Xerox Ethernet standardized as IEEE 802.3 in 1983 – Xerox not interested in commercializing – Metcalfe leaves and forms 3Com 4 Ethernet connec?vity • Shared medium – All hosts hear all traffic on cable – Hosts tapped the cable – 2500m maximum length – May include repeaters amplifying signal – 10 Mbps bandwidth 5 Classic Ethernet cabling Cable aSer being "vampire" tapped. Thick Ethernet cable (yellow), 10BASE-5 transceivers, cable tapping tool (orange), 500m maximum length. Thin Ethernet cable (10BASE2) with BNC T- connector, 185m maximum length. 6 Ethernet addressing • Media Access Control address (MAC) – 48-bit globally unique address • 281,474,976,710,656 possible addresses • Should last ?ll 2100 • e.g. 01:23:45:67:89:ab – Address of all 1's is broadcast • FF:FF:FF:FF:FF:FF 7 Ethernet frame format • Frame format – Manchester encoded – Preamble products 10-Mhz square wave • Allows clock synch between sender & receiver – Pad to at least 64-bytes (collision detec?on) Ethernet 802.3 AlternaWng 0's 48-bit MAC and 1's (except addresses SoF of 11) 8 Ethernet receivers • Hosts listens to medium – Deliver to host: • Any frame with host's MAC address • All broadcast frames (all 1's) • Mul?cast frames (if subscribed to) • Or all frames if in promiscuous mode 9 MAC sublayer • Media Access Control (MAC) sublayer – Who goes next on a shared medium – Ethernet hosts can sense if medium in use – Algorithm for sending data: 1. -

Gigabit Ethernet
Ethernet Technologies and Gigabit Ethernet Professor John Gorgone Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 1 Topics • Origins of Ethernet • Ethernet 10 MBS • Fast Ethernet 100 MBS • Gigabit Ethernet 1000 MBS • Comparison Tables • ATM VS Gigabit Ethernet •Ethernet8SummaryCopyright 1998, John T. Gorgone, All Rights Reserved 2 Origins • Original Idea sprang from Abramson’s Aloha Network--University of Hawaii • CSMA/CD Thesis Developed by Robert Metcalfe----(1972) • Experimental Ethernet developed at Xerox Palo Alto Research Center---1973 • Xerox’s Alto Computers -- First Ethernet Ethernet8systemsCopyright 1998, John T. Gorgone, All Rights Reserved 3 DIX STANDARD • Digital, Intel, and Xerox combined to developed the DIX Ethernet Standard • 1980 -- DIX Standard presented to the IEEE • 1980 -- IEEE creates the 802 committee to create acceptable Ethernet Standard Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 4 Ethernet Grows • Open Standard allows Hardware and Software Developers to create numerous products based on Ethernet • Large number of Vendors keeps Prices low and Quality High • Compatibility Problems Rare Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 5 What is Ethernet? • A standard for LANs • The standard covers two layers of the ISO model – Physical layer – Data link layer Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 6 What is Ethernet? • Transmission speed of 10 Mbps • Originally, only baseband • In 1986, broadband was introduced • Half duplex and full duplex technology • Bus topology Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 7 Components of Ethernet • Physical Medium • Medium Access Control • Ethernet Frame Ethernet8 Copyright 1998, John T. Gorgone, All Rights Reserved 8 CableCable DesignationsDesignations 10 BASE T SPEED TRANSMISSION MAX TYPE LENGTH Ethernet8 Copyright 1998, John T. -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Wireless Authentication
Wireless Authentication Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Overview Define authentication Strengths and weaknesses of captive portals How captive portals work What is Authentication? Verifying the claim that an entity is allowed to act on behalf of a given known identity More simply: • Is this person/device who they say they are? • Can they prove it • for example, with password, signature? • In our case, the entity is the software, acting on behalf of the user controlling the computer. Why Is Auth So Complicated? I am on a computer. Am I its owner? • Device is not the same as person. I am a network administrator • Should I have access to the finance system? I am connecting to the network from home • Should I have access to all my work resources? I am a printer • Should I be able to scp files to the network? Authentication Core Concepts These are all different concepts: • Confidentiality • Access Control • Authorization • Authentication Confidentiality Ensure that only those who should have access to information can indeed do so (usually encryption) Access Control Access control is the mechanisms by which rights & restrictions are controlled & enforced Authorization Authorization defines what an entity (a user, a device) is authorized (allowed), to access • Which networks (ACLs/filters) • Which systems, which files ? (FS ACLs, permissions) • When can they do that (time policies) ? • Can they run an application or access a service ? Authentication We want to know: WHO, WHERE(*), WHEN • Which entity? • What AP did they associate with? • When did they log on ? • What IP number did they have? PSK (Pre-Shared Key) cannot tell us this. -
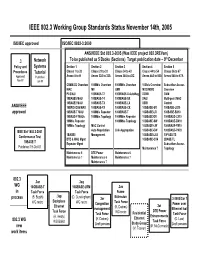
IEEE 802.3 Working Group Standards Status November 14Th, 2005
IEEE 802.3 Working Group Standards Status November 14th, 2005 ISO/IEC approved ISO/IEC 8802-3:2000 ANSI/IEEE Std 802.3-2005 (Was IEEE project 802.3REVam) th .3 Network To be published as 5 Books (Sections) Target publication date – 9 December Policy and Systems Section 1 Section 2 Section 3 Section 4 Section 5 Procedures Tutorial Clause 1 to 20 Clause 21 to 33 Clause 34 to 43 Clause 44 to 54 Clause 56 to 67 Approved Published Annex A to H Annex 22A to 32A Annex 36A to 43C Annex 44A to 50A Annex 58A to 67A Nov-97 Jun-95 CSMA/CD Overview 100Mb/s Overview 1000Mb/s Overview 10Gb/s Overview Subscriber Access MAC MII GMII MDC/MDIO Overview PLS/AUI 100BASE-T2 1000BASE-X AutoNeg XGMII OAM 10BASE5 MAU 100BASE-T4 1000BASE-SX XAUI Multi-point MAC 10BASE2 MAU 100BASE-TX 1000BASE-LX XSBI Control ANSI/IEEE 10BROAD36 MAU 100BASE-FX 1000BASE-CX 10GBASE-SR 100BASE-LX10 approved 10BASE-T MAU 100Mb/s Repeater 1000BASE-T 10GBASE-LR 100BASE-BX10 10BASE-F MAUs 100Mb/s Topology 1000Mb/s Repeater 10GBASE-ER 1000BASE-LX10 10Mb/s Repeater 1000Mb/s Topology 10GBASE-SW 1000BASE-BX10 10Mb/s Topology MAC Control 10GBASE-LW 1000BASE-PX10 IEEE Std 1802.3-2001 Auto Negotiation Link Aggregation 10GBASE-EW 1000BASE-PX20 Conformance Test 1BASE5 Management 10GBASE-LX4 10PASS-TS DTE & MAU Mgmt 10GBASE-CX4 2BASE-TL 10BASE-T Repeater Mgmt Subscriber Access Published 19-Oct-01 Maintenance 7 Topology Maintenance 6 DTE Power Maintenance 6 Maintenance 7 Maintenance 6 Maintenance 7 Maintenance 7 802.3 .3an .3aq WG 10GBASE-T 10GBASE-LRM .3as in Task Force Task Force Frame .3ap process (B. -

M0n0wall and PPTP Preface
M0n0wall and PPTP December 8, 2003 Version 1.0 Francisco Artes [email protected] Preface: ............................................................................................................................... 1 Audience: ............................................................................................................................ 1 Assumptions:....................................................................................................................... 2 Subnetting and VLAN routing:........................................................................................... 2 Setup of m0n0wall software: .............................................................................................. 3 PPTP User Setup:................................................................................................................5 PPTP Firewall Rules:.......................................................................................................... 6 Example of filtered PPTP Rules: .................................................................................... 9 Setting up a PPTP Client on Windows XP™:................................................................... 11 Testing our PPTP Connection in Windows ™: ............................................................ 14 Some things I have found not to work over the PPTP Connection: ................................. 17 Preface: This document is intended to outline several different PPTP VPN type setups, it includes a how-to on setting up a -

Modern Ethernet
Color profile: Generic CMYK printer profile Composite Default screen All-In-One / Network+ Certification All-in-One Exam Guide / Meyers / 225345-2 / Chapter 6 CHAPTER Modern Ethernet 6 The Network+ Certification exam expects you to know how to • 1.2 Specify the main features of 802.2 (Logical Link Control) [and] 802.3 (Ethernet): speed, access method, topology, media • 1.3 Specify the characteristics (for example: speed, length, topology, and cable type) of the following cable standards: 10BaseT and 10BaseFL; 100BaseTX and 100BaseFX; 1000BaseTX, 1000BaseCX, 1000BaseSX, and 1000BaseLX; 10GBaseSR, 10GBaseLR, and 10GBaseER • 1.4 Recognize the following media connectors and describe their uses: RJ-11, RJ-45, F-type, ST,SC, IEEE 1394, LC, MTRJ • 1.6 Identify the purposes, features, and functions of the following network components: hubs, switches • 2.3 Identify the OSI layers at which the following network components operate: hubs, switches To achieve these goals, you must be able to • Define the characteristics, cabling, and connectors used in 10BaseT and 10BaseFL • Explain how to connect multiple Ethernet segments • Define the characteristics, cabling, and connectors used with 100Base and Gigabit Ethernet Historical/Conceptual The first generation of Ethernet network technologies enjoyed substantial adoption in the networking world, but their bus topology continued to be their Achilles’ heel—a sin- gle break anywhere on the bus completely shut down an entire network. In the mid- 1980s, IBM unveiled a competing network technology called Token Ring. You’ll get the complete discussion of Token Ring in the next chapter, but it’s enough for now to say that Token Ring used a physical star topology.