Campus Networking Best Practices Session 5: Wireless
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

Iptables with Shorewall!
Iptables with shorewall! Table of Contents 1. Install swarmlab-sec (Home PC) . 1 2. shorewall . 1 2.1. Installation . 2 3. Basic Two-Interface Firewall. 2 4. Shorewall Concepts . 3 4.1. zones — Shorewall zone declaration file . 3 4.2. interfaces — Shorewall interfaces file. 4 4.3. policy — Shorewall policy file . 4 4.4. rules — Shorewall rules file . 4 4.5. Compile then Execute . 4 5. Three-Interface Firewall. 5 5.1. zones . 6 5.2. interfaces . 6 5.3. policy . 7 5.4. rules . 7 5.5. masq - Shorewall Masquerade/SNAT definition file . 7 5.6. snat — Shorewall SNAT/Masquerade definition file . 8 5.7. Compile and Execute . 8 1. Install swarmlab-sec (Home PC) HowTo: See http://docs.swarmlab.io/lab/sec/sec.adoc.html NOTE Assuming you’re already logged in 2. shorewall Shorewall is an open source firewall tool for Linux that builds upon the Netfilter (iptables/ipchains) system built into the Linux kernel, making it easier to manage more complex configuration schemes by providing a higher level of abstraction for describing rules using text files. More: wikipedia 1 NOTE Our docker instances have only one nic to add more nic’s: create netowrk frist docker network create --driver=bridge --subnet=192.168.0.0/16 net1 docker network create --driver=bridge --subnet=192.168.0.0/16 net2 docker network create --driver=bridge --subnet=192.168.0.0/16 net3 then connect network to container connect network created to container docker network connect net1 master docker network connect net1 worker1 docker network connect net2 master docker network connect net2 worker2 now let’s look at the following image 2.1. -

Wireless Authentication
Wireless Authentication Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Overview Define authentication Strengths and weaknesses of captive portals How captive portals work What is Authentication? Verifying the claim that an entity is allowed to act on behalf of a given known identity More simply: • Is this person/device who they say they are? • Can they prove it • for example, with password, signature? • In our case, the entity is the software, acting on behalf of the user controlling the computer. Why Is Auth So Complicated? I am on a computer. Am I its owner? • Device is not the same as person. I am a network administrator • Should I have access to the finance system? I am connecting to the network from home • Should I have access to all my work resources? I am a printer • Should I be able to scp files to the network? Authentication Core Concepts These are all different concepts: • Confidentiality • Access Control • Authorization • Authentication Confidentiality Ensure that only those who should have access to information can indeed do so (usually encryption) Access Control Access control is the mechanisms by which rights & restrictions are controlled & enforced Authorization Authorization defines what an entity (a user, a device) is authorized (allowed), to access • Which networks (ACLs/filters) • Which systems, which files ? (FS ACLs, permissions) • When can they do that (time policies) ? • Can they run an application or access a service ? Authentication We want to know: WHO, WHERE(*), WHEN • Which entity? • What AP did they associate with? • When did they log on ? • What IP number did they have? PSK (Pre-Shared Key) cannot tell us this. -

Sentry Firewall CD HOWTO Sentry Firewall CD HOWTO Table of Contents
Sentry Firewall CD HOWTO Sentry Firewall CD HOWTO Table of Contents Sentry Firewall CD HOWTO............................................................................................................................1 Stephen A. Zarkos, Obsid@Sentry.net....................................................................................................1 1. Introduction..........................................................................................................................................1 2. How the CD Works (Overview)..........................................................................................................1 3. Obtaining the CDROM........................................................................................................................1 4. Using the Sentry Firewall CDROM.....................................................................................................1 5. Overview of Available Configuration Directives................................................................................1 6. Setting Up a Firewall...........................................................................................................................2 7. Troubleshooting...................................................................................................................................2 8. Building a Custom Sentry CD.............................................................................................................2 9. More About the Sentry Firewall Project..............................................................................................2 -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Ubuntu Server Guide Ubuntu Server Guide Copyright © 2010 Canonical Ltd
Ubuntu Server Guide Ubuntu Server Guide Copyright © 2010 Canonical Ltd. and members of the Ubuntu Documentation Project3 Abstract Welcome to the Ubuntu Server Guide! It contains information on how to install and configure various server applications on your Ubuntu system to fit your needs. It is a step-by-step, task-oriented guide for configuring and customizing your system. Credits and License This document is maintained by the Ubuntu documentation team (https://wiki.ubuntu.com/DocumentationTeam). For a list of contributors, see the contributors page1 This document is made available under the Creative Commons ShareAlike 2.5 License (CC-BY-SA). You are free to modify, extend, and improve the Ubuntu documentation source code under the terms of this license. All derivative works must be released under this license. This documentation is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE AS DESCRIBED IN THE DISCLAIMER. A copy of the license is available here: Creative Commons ShareAlike License2. 3 https://launchpad.net/~ubuntu-core-doc 1 ../../libs/C/contributors.xml 2 /usr/share/ubuntu-docs/libs/C/ccbysa.xml Table of Contents 1. Introduction ........................................................................................................................... 1 1. Support .......................................................................................................................... 2 2. Installation ............................................................................................................................ -

M0n0wall and PPTP Preface
M0n0wall and PPTP December 8, 2003 Version 1.0 Francisco Artes [email protected] Preface: ............................................................................................................................... 1 Audience: ............................................................................................................................ 1 Assumptions:....................................................................................................................... 2 Subnetting and VLAN routing:........................................................................................... 2 Setup of m0n0wall software: .............................................................................................. 3 PPTP User Setup:................................................................................................................5 PPTP Firewall Rules:.......................................................................................................... 6 Example of filtered PPTP Rules: .................................................................................... 9 Setting up a PPTP Client on Windows XP™:................................................................... 11 Testing our PPTP Connection in Windows ™: ............................................................ 14 Some things I have found not to work over the PPTP Connection: ................................. 17 Preface: This document is intended to outline several different PPTP VPN type setups, it includes a how-to on setting up a -
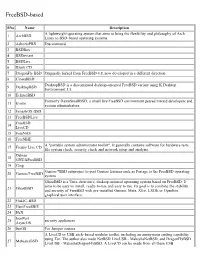
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

How to Accelerate Your Internet
How To Accelerate Your Internet A practical guide to Bandwidth Management and Optimisation using Open Source Software How To Accelerate Your Internet For more information about this project, visit us online at http://bwmo.net/ Editor: Flickenger R. Associate Editors: Belcher M., Canessa E., Zennaro M. Publishers: INASP/ICTP © 2006, BMO Book Sprint Team First edition: October 2006 ISBN: 0-9778093-1-5 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibil- ity for errors or omissions. No liability is assumed for incidental or consequen- tial damages in connection with or arising out of the use of the information con- tained herein. This work is released under the Creative Commons Attribution-ShareAlike 2.5 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/2.5/ Contents Preface ix About This Book xi Introduction 1 Bandwidth, throughput, latency, and speed.............................................................................. 2 Not enough to go around........................................................................................................ -

Introduzione Al Mondo Freebsd Corso Avanzato
Introduzione al mondo FreeBSD corso Avanzato •Struttura •Installazione •Configurazione •I ports •Gestione •Netstudent http://netstudent.polito.it •E.Richiardone [email protected] •Novembre 2012 •CC-by http://creativecommons.org/licenses/by/3.0/it/ The FreeBSD project - 1 • E` un progetto software open • Lo scopo e` mantenere e sviluppare il sistema operativo FreeBSD • Nasce su CDROM come FreeBSD 1.0 nel 1993 • Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 • Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free • Dalla release 4.0 (2000) assume la struttura che ha oggi • Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... • La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 • Erede di 4.4BSD (e` la stessa gente...) • Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato • Documentazione ufficiale ben curata • Licenza molto permissiva, spesso attrae aziende per progetti commerciali: • saltuariamente progetti collaborano con implementazioni ex-novo (i.e. Intel, GEOM, NDISwrapper, ZFS, GNU/Linux emulation) • Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: • Un sistema base • Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali • Sorgenti completi in /usr/src (~500MB) • E` gia` completo (i.e. ipfw, ppp, bind, ...) • Un sistema di gestione per software aggiuntivo • Ports e packages • Documentazione, canali di assistenza, strumenti -

Papers/Openwrt on the Belkin F5D7230-4.Pdf
WHITE PAPER OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development White Paper OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development CONTROL PAGE Document Approvals Approved for Publication: Author Name: Ian Latter 7 November 2004 Document Control Document Name: OpenWRT on the Belkin F5D7230-4; Understanding the Belkin extended firmware for OpenWRT development Document ID: openwrt on the belkin f5d7230-4.doc-Release-0.4(31) Distribution: Unrestricted Distribution Status: Release Disk File: C:\papers\OpenWRT on the Belkin F5D7230-4.doc Copyright: Copyright 2004, Ian Latter Version Date Release Information Author/s 0.4 07-Nov-04 Release / Unrestricted Distribution Ian Latter 0.3 26-Oct-04 Release / Unrestricted Distribution Ian Latter 0.2 24-Oct-04 Release / Unrestricted Distribution Ian Latter Distribution Version Release to 0.4 MidnightCode.org (correction of one grammatical error) 0.3 MidnightCode.org (correction of two minor errors) 0.2 MidnightCode.org Unrestricted Distribution Copyright 2004, Ian Latter Page 2 of 38 White Paper OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development Table of Contents 1 OVERVIEW..................................................................................................................................4 1.1 IN BRIEF .................................................................................................................................4 1.2 HISTORY ................................................................................................................................4 -

Pare-Feu : Architecture Et Déploiement V1.0
Pare-feu : architecture et déploiement V1.0 Pare-feu : Architecture et déploiement V 1.0 Stéphane DUFOUR (Architecte système et sécurité) - 1 - Pare-feu : architecture et déploiement V1.0 Table des matières PARE-FEU : ARCHITECTURE ET DEPLOIEMENT ..............................................................................................................................0 TABLE DES MATIERES...................................................................................................................................................................2 INTRODUCTION ...........................................................................................................................................................................4 CONCEPTS DE BASE......................................................................................................................................................................5 RAPPEL SECURITE .................................................................................................................................................................................5 Les fondamentaux ......................................................................................................................................................................5 Les menaces ................................................................................................................................................................................6 Best practice .............................................................................................................................................................................16