Inferring Higher Level Policies from Firewall Rules ∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Campus Networking Best Practices Session 5: Wireless
Campus Networking Best Practices Session 5: Wireless LAN Hervey Allen Dale Smith NSRC & University of Oregon University of Oregon & NSRC [email protected] [email protected] Wireless LAN • Provide wireless network across your campus that has the following characteristics: – Authentication – only allow your users – Roaming – allow users to start up in one section of your network, then move to another location – Runs on your campus network Firewall/ Border Traffic Shaper Router Wireless REN switch Authentication Core Gateway Router Core Servers Network Access Control (NAC) Enterprise Identity Management • Processes and Documentation of users. – Now you must deal with this. – What to use as the back-end user store? • LDAP • Active Directory • Kerberos • Other? – Will this play nice with future use? • email, student/staff information, resource access, ... Identity Management Cont. • An example of such a project can be seen here: – http://ccadmin.uoregon.edu/idm/ • This is a retrofit on to an already retrofitted system. • Learn from others and try to avoid this situation if possible. A Wireless Captive Portal The Wireless Captive Portal • Previous example was very simple. • A Captive Portal is your chance to: – Explain your Acceptable Use Policies – Decide if you must authenticate, or – Allow users on your network and monitor for problems instead (alternate solution). – Anything else? Branding? What's Happening? • remember our initial network diagrams...? • Do you think our hotel built their own solution? • Probably not... Commercial Solutions • Aruba http://www.arubanetworks.com/ • Bradford Networks – http://www.bradfordnetworks.com/ • Cisco NAC Appliance (Clean Access) – http://www.cisco.com/en/US/products/ps6128/ • Cisco Wireless LAN Controllers – http://www.cisco.com/en/US/products/hw/wireless/ • Enterasys http://www.enterasys.com/ • Vernier http://www.verniernetworks.com Open Source Solutions • CoovaChilli (morphed from Chillispot) – http://coova.org/wiki/index.php/CoovaChilli – Uses RADIUS for access and accounting. -

Iptables with Shorewall!
Iptables with shorewall! Table of Contents 1. Install swarmlab-sec (Home PC) . 1 2. shorewall . 1 2.1. Installation . 2 3. Basic Two-Interface Firewall. 2 4. Shorewall Concepts . 3 4.1. zones — Shorewall zone declaration file . 3 4.2. interfaces — Shorewall interfaces file. 4 4.3. policy — Shorewall policy file . 4 4.4. rules — Shorewall rules file . 4 4.5. Compile then Execute . 4 5. Three-Interface Firewall. 5 5.1. zones . 6 5.2. interfaces . 6 5.3. policy . 7 5.4. rules . 7 5.5. masq - Shorewall Masquerade/SNAT definition file . 7 5.6. snat — Shorewall SNAT/Masquerade definition file . 8 5.7. Compile and Execute . 8 1. Install swarmlab-sec (Home PC) HowTo: See http://docs.swarmlab.io/lab/sec/sec.adoc.html NOTE Assuming you’re already logged in 2. shorewall Shorewall is an open source firewall tool for Linux that builds upon the Netfilter (iptables/ipchains) system built into the Linux kernel, making it easier to manage more complex configuration schemes by providing a higher level of abstraction for describing rules using text files. More: wikipedia 1 NOTE Our docker instances have only one nic to add more nic’s: create netowrk frist docker network create --driver=bridge --subnet=192.168.0.0/16 net1 docker network create --driver=bridge --subnet=192.168.0.0/16 net2 docker network create --driver=bridge --subnet=192.168.0.0/16 net3 then connect network to container connect network created to container docker network connect net1 master docker network connect net1 worker1 docker network connect net2 master docker network connect net2 worker2 now let’s look at the following image 2.1. -

Sentry Firewall CD HOWTO Sentry Firewall CD HOWTO Table of Contents
Sentry Firewall CD HOWTO Sentry Firewall CD HOWTO Table of Contents Sentry Firewall CD HOWTO............................................................................................................................1 Stephen A. Zarkos, Obsid@Sentry.net....................................................................................................1 1. Introduction..........................................................................................................................................1 2. How the CD Works (Overview)..........................................................................................................1 3. Obtaining the CDROM........................................................................................................................1 4. Using the Sentry Firewall CDROM.....................................................................................................1 5. Overview of Available Configuration Directives................................................................................1 6. Setting Up a Firewall...........................................................................................................................2 7. Troubleshooting...................................................................................................................................2 8. Building a Custom Sentry CD.............................................................................................................2 9. More About the Sentry Firewall Project..............................................................................................2 -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Ubuntu Server Guide Ubuntu Server Guide Copyright © 2010 Canonical Ltd
Ubuntu Server Guide Ubuntu Server Guide Copyright © 2010 Canonical Ltd. and members of the Ubuntu Documentation Project3 Abstract Welcome to the Ubuntu Server Guide! It contains information on how to install and configure various server applications on your Ubuntu system to fit your needs. It is a step-by-step, task-oriented guide for configuring and customizing your system. Credits and License This document is maintained by the Ubuntu documentation team (https://wiki.ubuntu.com/DocumentationTeam). For a list of contributors, see the contributors page1 This document is made available under the Creative Commons ShareAlike 2.5 License (CC-BY-SA). You are free to modify, extend, and improve the Ubuntu documentation source code under the terms of this license. All derivative works must be released under this license. This documentation is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE AS DESCRIBED IN THE DISCLAIMER. A copy of the license is available here: Creative Commons ShareAlike License2. 3 https://launchpad.net/~ubuntu-core-doc 1 ../../libs/C/contributors.xml 2 /usr/share/ubuntu-docs/libs/C/ccbysa.xml Table of Contents 1. Introduction ........................................................................................................................... 1 1. Support .......................................................................................................................... 2 2. Installation ............................................................................................................................ -

Papers/Openwrt on the Belkin F5D7230-4.Pdf
WHITE PAPER OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development White Paper OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development CONTROL PAGE Document Approvals Approved for Publication: Author Name: Ian Latter 7 November 2004 Document Control Document Name: OpenWRT on the Belkin F5D7230-4; Understanding the Belkin extended firmware for OpenWRT development Document ID: openwrt on the belkin f5d7230-4.doc-Release-0.4(31) Distribution: Unrestricted Distribution Status: Release Disk File: C:\papers\OpenWRT on the Belkin F5D7230-4.doc Copyright: Copyright 2004, Ian Latter Version Date Release Information Author/s 0.4 07-Nov-04 Release / Unrestricted Distribution Ian Latter 0.3 26-Oct-04 Release / Unrestricted Distribution Ian Latter 0.2 24-Oct-04 Release / Unrestricted Distribution Ian Latter Distribution Version Release to 0.4 MidnightCode.org (correction of one grammatical error) 0.3 MidnightCode.org (correction of two minor errors) 0.2 MidnightCode.org Unrestricted Distribution Copyright 2004, Ian Latter Page 2 of 38 White Paper OpenWRT on the Belkin F5D7230-4 Understanding the Belkin extended firmware for OpenWRT development Table of Contents 1 OVERVIEW..................................................................................................................................4 1.1 IN BRIEF .................................................................................................................................4 1.2 HISTORY ................................................................................................................................4 -

Taxonomy of WRT54G(S) Hardware and Custom Firmware
Edith Cowan University Research Online ECU Publications Pre. 2011 2005 Taxonomy of WRT54G(S) Hardware and Custom Firmware Marwan Al-Zarouni Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/ecuworks Part of the Computer Sciences Commons Al-Zarouni, M. (2005). Taxonomy of WRT54G(S) hardware and custom firmware. In Proceedings of 3rd Australian Information Security Management Conference (pp. 1-10). Edith Cowan University. Available here This Conference Proceeding is posted at Research Online. https://ro.ecu.edu.au/ecuworks/2946 Taxonomy of WRT54G(S) Hardware and Custom Firmware Marwan Al-Zarouni School of Computer and Information Science Edith Cowan University E-mail: [email protected] Abstract This paper discusses the different versions of hardware and firmware currently available for the Linksys WRT54G and WRT54GS router models. It covers the advantages, disadvantages, and compatibility issues of each one of them. The paper goes further to compare firmware added features and associated filesystems and then discusses firmware installation precautions and ways to recover from a failed install. Keywords WRT54G, Embedded Linux, Wireless Routers, Custom Firmware, Wireless Networking, Firmware Hacking. BACKGROUND INFORMATION The WRT54G is a 802.11g router that combines the functionality of three different network devices; it can serve as a wireless Access Point (AP), a four-port full-duplex 10/100 switch, and a router that ties it all together (ProductReview, 2005). The WRT54G firmware was based on embedded Linux which is open source. This led to the creation of several sites and discussion forums that were dedicated to the router which in turn led to the creation of several variants of its firmware. -

Introducción a Linux Equivalencias Windows En Linux Ivalencias
No has iniciado sesión Discusión Contribuciones Crear una cuenta Acceder Página discusión Leer Editar Ver historial Buscar Introducción a Linux Equivalencias Windows en Linux Portada < Introducción a Linux Categorías de libros Equivalencias Windows en GNU/Linux es una lista de equivalencias, reemplazos y software Cam bios recientes Libro aleatorio análogo a Windows en GNU/Linux y viceversa. Ayuda Contenido [ocultar] Donaciones 1 Algunas diferencias entre los programas para Windows y GNU/Linux Comunidad 2 Redes y Conectividad Café 3 Trabajando con archivos Portal de la comunidad 4 Software de escritorio Subproyectos 5 Multimedia Recetario 5.1 Audio y reproductores de CD Wikichicos 5.2 Gráficos 5.3 Video y otros Imprimir/exportar 6 Ofimática/negocios Crear un libro 7 Juegos Descargar como PDF Versión para im primir 8 Programación y Desarrollo 9 Software para Servidores Herramientas 10 Científicos y Prog s Especiales 11 Otros Cambios relacionados 12 Enlaces externos Subir archivo 12.1 Notas Páginas especiales Enlace permanente Información de la Algunas diferencias entre los programas para Windows y y página Enlace corto GNU/Linux [ editar ] Citar esta página La mayoría de los programas de Windows son hechos con el principio de "Todo en uno" (cada Idiomas desarrollador agrega todo a su producto). De la misma forma, a este principio le llaman el Añadir enlaces "Estilo-Windows". Redes y Conectividad [ editar ] Descripción del programa, Windows GNU/Linux tareas ejecutadas Firefox (Iceweasel) Opera [NL] Internet Explorer Konqueror Netscape / -

Download Appendix A
Appendix A Resources Links This list includes most of the URLs referenced in this book. For more online resources and further reading, see our website at http://bwmo.net/ Anti-virus & anti-spyware tools • AdAware, http://www.lavasoftusa.com/software/adaware/ • Clam Antivirus, http://www.clamav.net/ • Spychecker, http://www.spychecker.com/ • xp-antispy, http://www.xp-antispy.de/ Benchmarking tools • Bing, http://www.freenix.fr/freenix/logiciels/bing.html • DSL Reports Speed Test, http://www.dslreports.com/stest • The Global Broadband Speed Test, http://speedtest.net/ • iperf, http://dast.nlanr.net/Projects/Iperf/ • ttcp, http://ftp.arl.mil/ftp/pub/ttcp/ 260! The Future Content filters • AdZapper, http://adzapper.sourceforge.net/ • DansGuard, http://dansguardian.org/ • Squidguard, http://www.squidguard.org/ DNS & email • Amavisd-new, http://www.ijs.si/software/amavisd/ • BaSoMail, http://www.baso.no/ • BIND, http://www.isc.org/sw/bind/ • dnsmasq, http://thekelleys.org.uk/dnsmasq/ • DJBDNS, http://cr.yp.to/djbdns.html • Exim, http://www.exim.org/ • Free backup software, http://free-backup.info/ • Life with qmail, http://www.lifewithqmail.org/ • Macallan Mail Server, http://macallan.club.fr/ • MailEnable, http://www.mailenable.com/ • Pegasus Mail, http://www.pmail.com/ • Postfix, http://www.postfix.org/ • qmail, http://www.qmail.org/ • Sendmail, http://www.sendmail.org/ File exchange tools • DropLoad, http://www.dropload.com/ • FLUFF, http://www.bristol.ac.uk/fluff/ Firewalls • IPCop, http://www.ipcop.org/ • L7-filter, http://l7-filter.sourceforge.net/ -

Ubuntu Server Guide Basic Installation Preparing to Install
Ubuntu Server Guide Changes, errors and bugs This is the current edition for Ubuntu 20.04 LTS, Focal Fossa. Ubuntu serverguides for previous LTS versions: 18.04 (PDF), 16.04 (PDF). If you find any errors or have suggestions for improvements to pages, please use the link at thebottomof each topic titled: “Help improve this document in the forum.” This link will take you to the Server Discourse forum for the specific page you are viewing. There you can share your comments or let us know aboutbugs with each page. Offline Download this guide as a PDF Support There are a couple of different ways that Ubuntu Server Edition is supported: commercial support and community support. The main commercial support (and development funding) is available from Canonical, Ltd. They supply reasonably- priced support contracts on a per desktop or per server basis. For more information see the Ubuntu Advantage page. Community support is also provided by dedicated individuals and companies that wish to make Ubuntu the best distribution possible. Support is provided through multiple mailing lists, IRC channels, forums, blogs, wikis, etc. The large amount of information available can be overwhelming, but a good search engine query can usually provide an answer to your questions. See the Ubuntu Support page for more information. Basic installation This chapter provides an overview of installing Ubuntu 20.04 Server Edition. There is more detailed docu- mentation on other installer topics. Preparing to Install This section explains various aspects to consider before starting the installation. System requirements Ubuntu 20.04 Server Edition provides a common, minimalist base for a variety of server applications, such as file/print services, web hosting, email hosting, etc. -
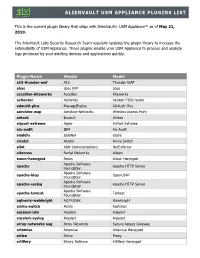
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

List Software Pengganti Windows Ke Linux
Tabel Padanan Aplikasi Windows di Linux Untuk Migrasi Selasa, 18-08-2009 Kesulitan besar dalam melakukan migrasi dari Windows ke Linux adalah mencari software pengganti yang berkesesuaian. Berikut ini adalah tabel padanan aplikasi Windows di Linux yang disusun dalam beberapa kategori. Nama Program Windows Linux 1) Networking. 1) Netscape / Mozilla. 2) Galeon. 3) Konqueror. 4) Opera. [Prop] Internet Explorer, 5) Firefox. Web browser Netscape / Mozilla, Opera 6) Nautilus. [Prop], Firefox, ... 7) Epiphany. 8) Links. (with "-g" key). 9) Dillo. 10) Encompass. 1) Links. 1) Links 2) ELinks. Console web browser 2) Lynx 3) Lynx. 3) Xemacs + w3. 4) w3m. 5) Xemacs + w3. 1) Evolution. 2) Netscape / Mozilla/Thunderbird messenger. 3) Sylpheed / Claws Mail. 4) Kmail. Outlook Express, 5) Gnus. Netscape / Mozilla, 6) Balsa. Thunderbird, The Bat, 7) Bynari Insight GroupWare Suite. Email client Eudora, Becky, Datula, [Prop] Sylpheed / Claws Mail, 8) Arrow. Opera 9) Gnumail. 10) Althea. 11) Liamail. 12) Aethera. 13) MailWarrior. 14) Opera. 1) Evolution. Email client / PIM in MS 2) Bynari Insight GroupWare Suite. Outlook Outlook style [Prop] 3) Aethera. 4) Sylpheed. 5) Claws Mail 1) Sylpheed. 2) Claws Mail Email client in The Bat The Bat 3) Kmail. style 4) Gnus. 5) Balsa. 1) Pine. [NF] 2) Mutt. Mutt [de], Pine, Pegasus, Console email client 3) Gnus. Emacs 4) Elm. 5) Emacs. 1) Knode. 2) Pan. 1) Agent [Prop] 3) NewsReader. 2) Free Agent 4) Netscape / Mozilla Thunderbird. 3) Xnews 5) Opera [Prop] 4) Outlook 6) Sylpheed / Claws Mail. 5) Netscape / Mozilla Console: News reader 6) Opera [Prop] 7) Pine. [NF] 7) Sylpheed / Claws Mail 8) Mutt.