Text Steganography Based on Font Type in MS-Word Documents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cloud Fonts in Microsoft Office
APRIL 2019 Guide to Cloud Fonts in Microsoft® Office 365® Cloud fonts are available to Office 365 subscribers on all platforms and devices. Documents that use cloud fonts will render correctly in Office 2019. Embed cloud fonts for use with older versions of Office. Reference article from Microsoft: Cloud fonts in Office DESIGN TO PRESENT Terberg Design, LLC Index MICROSOFT OFFICE CLOUD FONTS A B C D E Legend: Good choice for theme body fonts F G H I J Okay choice for theme body fonts Includes serif typefaces, K L M N O non-lining figures, and those missing italic and/or bold styles P R S T U Present with most older versions of Office, embedding not required V W Symbol fonts Language-specific fonts MICROSOFT OFFICE CLOUD FONTS Abadi NEW ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Abadi Extra Light ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Note: No italic or bold styles provided. Agency FB MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Agency FB Bold ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Note: No italic style provided Algerian MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ 01234567890 Note: Uppercase only. No other styles provided. Arial MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Italic ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Bold ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Bold Italic ABCDEFGHIJKLMNOPQRSTUVWXYZ -

Suitcase Fusion 8 Getting Started
Copyright © 2014–2018 Celartem, Inc., doing business as Extensis. This document and the software described in it are copyrighted with all rights reserved. This document or the software described may not be copied, in whole or part, without the written consent of Extensis, except in the normal use of the software, or to make a backup copy of the software. This exception does not allow copies to be made for others. Licensed under U.S. patents issued and pending. Celartem, Extensis, LizardTech, MrSID, NetPublish, Portfolio, Portfolio Flow, Portfolio NetPublish, Portfolio Server, Suitcase Fusion, Type Server, TurboSync, TeamSync, and Universal Type Server are registered trademarks of Celartem, Inc. The Celartem logo, Extensis logos, LizardTech logos, Extensis Portfolio, Font Sense, Font Vault, FontLink, QuickComp, QuickFind, QuickMatch, QuickType, Suitcase, Suitcase Attaché, Universal Type, Universal Type Client, and Universal Type Core are trademarks of Celartem, Inc. Adobe, Acrobat, After Effects, Creative Cloud, Creative Suite, Illustrator, InCopy, InDesign, Photoshop, PostScript, Typekit and XMP are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apache Tika, Apache Tomcat and Tomcat are trademarks of the Apache Software Foundation. Apple, Bonjour, the Bonjour logo, Finder, iBooks, iPhone, Mac, the Mac logo, Mac OS, OS X, Safari, and TrueType are trademarks of Apple Inc., registered in the U.S. and other countries. macOS is a trademark of Apple Inc. App Store is a service mark of Apple Inc. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license. Elasticsearch is a trademark of Elasticsearch BV, registered in the U.S. -

SHOPC Minutes
· IOLu\f\ Clex-~ Kc.J 1 \) 1 Approved May 6, 2020 SJlo Izozo 2 I).' LI J'.W1 3 s 4 ~ ~ 5 THE SOUTHBOROUGH HOUSING OPPORTUNITY PARTNERSHIP COMMITTEE 6 (SHOPC) 7 MEETING MINUTES 8 Wednesday, April 29, 2020 8:30 AM 9 VIRTUAL MEETING/REMO E PARTICIPATION 10 11 Members present: Doriann Jasinski, Lisa Braccio, John Wood, Alex Frisch, Tom Bhisitkul, Tom Marcoulier 12 and Jesse Stein. Also present: Karina Quinn, Town Planner, Sarah Hoecker, Business Administrator I and 13 Kathleen Battles, Recording Secretary. Sarah Hoecker managed virtual connection through ZOOM 14 application. 15 16 CALL TO ORDER: The meeting was called to order at 8:44 AM. 17 18 Ms. Jasinski read the following statement: 19 Pursuant to Governor Baker's March 12, 2020 Order Suspending Certain Provisions of the Open Meeting 20 Law, G.L. c. 30A, &18, and the Governor's March 15, 2020 Order imposing strict limitations on the 21 number of people that may gather in one place, this meeting of the Southborough Housing Opportunity 22 Partnership Committee (SHOPC) is being conducted via remote participation to the greatest extent 23 possible. Specific information and the general guidelines for the remote participation by members of 24 the public and/ or parties with a right and/or requirement to attend this meeting can be found on the 25 Town of Southborough's website, at https://www.southboroughtown.com/. 26 For this meeting, members of the pubic who wish to listen to the meeting or participate in the public 27 hearing may do so in the following manner: 28 https://www.southboroughtown.com/remotemeetings 29 30 No in-person attendance of members of the public will be permitted, but every effort will be made to 31 ensure that the public can adequately access the proceedings in real time, via technological means. -

Suitcase Fusion 9 Getting Started Guide
Legal notices Copyright © 2014–2019 Celartem, Inc., doing business as Extensis. This document and the software described in it are copyrighted with all rights reserved. This document or the software described may not be copied, in whole or part, without the written consent of Extensis, except in the normal use of the software, or to make a backup copy of the software. This exception does not allow copies to be made for others. Licensed under U.S. patents issued and pending. Celartem, Extensis, MrSID, NetPublish, Portfolio Flow, Portfolio NetPublish, Portfolio Server, Suitcase Fusion, Type Server, TurboSync, TeamSync, and Universal Type Server are registered trademarks of Celartem, Inc. The Celartem logo, Extensis logos, Extensis Portfolio, Font Sense, Font Vault, FontLink, QuickFind, QuickMatch, QuickType, Suitcase, Suitcase Attaché, Universal Type, Universal Type Client, and Universal Type Core are trademarks of Celartem, Inc. Adobe, Acrobat, After Effects, Creative Cloud, Creative Suite, Illustrator, InCopy, InDesign, Photoshop, PostScript, and XMP are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apache Tika, Apache Tomcat and Tomcat are trademarks of the Apache Software Foundation. Apple, Bonjour, the Bonjour logo, Finder, iPhone, Mac, the Mac logo, Mac OS, OS X, Safari, and TrueType are trademarks of Apple Inc., registered in the U.S. and other countries. macOS is a trademark of Apple Inc. App Store is a service mark of Apple Inc. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license. Elasticsearch is a trademark of Elasticsearch BV, registered in the U.S. -

Indiana Department of Transportation
INDIANA DEPARTMENT OF TRANSPORTATION CONTRACT INFORMATION BOOK (CIB) PART I CONTRACT NO. LETTING DATE: Certified By: Date: Covering Items in Table of Contents, PART I For Release for Bidding Purposes CONTRACT INFORMATION TABLE OF CONTENTS CONTRACT NO. This book shall be examined to determine that each page set out in the Contract Information Table of Contents, and the Special Provisions Table of Contents is attached, legible, and current. PART I PAGES PROPOSAL PAGE 1 SCHEDULE OF PAY ITEMS 1 – RECURRING PLAN DETAILS 1 - TRAFFIC CONTROL DEVICE REPORT 1 SPECIAL PROVISIONS 1 – PART II CONTACT FOR CONTRACTORS DISTRICT CONSTRUCTION DIRECTOR: *QUESTION FORM Contractors shall submit contract specific questions by completing the Question Form accessed from http://entapps.indot.in.gov/cqa/ The Department will attempt to have an answer on-line within two business days. Retrieve the Question and Answer Form for a specific contract by going on–line in the same manner you retrieve Contract Information Books and Plans. http://erms.indot.in.gov/viewdocs/ will display the interface used for selection of contract letting documents. For the document category, select “Q and A Form”. CONTACTS FOR DISTRICT PERSONNEL ONLY PHONE: PHONE: Indiana Department of Transportation Proposal Date of Letting: April 05, 2017 Time of Letting: 10:00 A.M. Location of Letting: N725 CONF RM, GOVERNMENT CENTER NORTH 100 N. SENATE AVENUE INDIANAPOLIS, INDIANA 46204 State Certified Contract Number: R -36342-A Project Number(s): 1172473 Districts : Greenfield Counties : HOWARD Description: NEW PEDESTRIAN BRIDGE CONSTRUCTION Completion Date or Time ID Description Time Type Liquidated Damages Rate Number of Units 00 COMPLETION DATE 11/9/2018 DT $1,500.00 per Days 01 INTERMEDIATE 11/21/2017 DT $1,500.00 per Days COMPLETION DATE (*) - Indicates Cost Plus Time Site. -

Sketch Block Bold Accord Heavy SF Bold Accord SF Bold Aclonica Adamsky SF AFL Font Pespaye Nonmetric Aharoni Vet Airmole Shaded
Sketch Block Bold Accord Heavy SF Bold Accord SF Bold Aclonica Adamsky SF AFL Font pespaye nonmetric Aharoni Vet Airmole Shaded Airmole Stripe Airstream Alegreya Alegreya Black Alegreya Black Italic Alegreya Bold Alegreya Bold Italic Alegreya Italic Alegreya Sans Alegreya Sans Black Alegreya Sans Black Italic Alegreya Sans Bold Alegreya Sans Bold Italic Alegreya Sans ExtraBold Alegreya Sans ExtraBold Italic Alegreya Sans Italic Alegreya Sans Light Alegreya Sans Light Italic Alegreya Sans Medium Alegreya Sans Medium Italic Alegreya Sans SC Alegreya Sans SC Black Alegreya Sans SC Black Italic Alegreya Sans SC Bold Alegreya Sans SC Bold Italic Alegreya Sans SC ExtraBold Alegreya Sans SC ExtraBold Italic Alegreya Sans SC Italic Alegreya Sans SC Light Alegreya Sans SC Light Italic Alegreya Sans SC Medium Alegreya Sans SC Medium Italic Alegreya Sans SC Thin Alegreya Sans SC Thin Italic Alegreya Sans Thin Alegreya Sans Thin Italic AltamonteNF AMC_SketchyOutlines AMC_SketchySolid Ancestory SF Andika New Basic Andika New Basic Bold Andika New Basic Bold Italic Andika New Basic Italic Angsana New Angsana New Angsana New Cursief Angsana New Vet Angsana New Vet Cursief Annie BTN Another Typewriter Aparajita Aparajita Bold Aparajita Bold Italic Aparajita Italic Appendix Normal Apple Boy BTN Arabic Typesetting Arabolical Archive Arial Arial Black Bold Arial Black Standaard Arial Cursief Arial Narrow Arial Narrow Vet Arial Unicode MS Arial Vet Arial Vet Cursief Aristocrat SF Averia-Bold Averia-BoldItalic Averia-Gruesa Averia-Italic Averia-Light Averia-LightItalic -

Training a Neural Network Using Synthetically Generated Data
DEGREE PROJECT IN TECHNOLOGY, FIRST CYCLE, 15 CREDITS STOCKHOLM, SWEDEN 2020 TRAINING A NEURAL NETWORK USING SYNTHETICALLY GENERATED DATA FREDRIK DIFFNER HOVIG MANJIKIAN KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE Att träna ett neuronnät med syntetiskt genererad data FREDRIK DIFFNER HOVIG MANJIKIAN Degree Project in Computer Science Date: June 2020 Supervisor: Christopher Peters Examiner: Pawel Herman KTH Royal Institute of Technology School of Electrical Engineering and Computer Science Abstract A major challenge in training machine learning models is the gathering and labeling of a sufficiently large training data set. A common solution is the use of synthetically generated data set to expand or replace a real data set. This paper examines the performance of a machine learning model trained on synthetic data set versus the same model trained on real data. This approach was applied to the problem of character recognition using a machine learning model that implements convolutional neural networks. A synthetic data set of 1’240’000 images and two real data sets, Char74k and ICDAR 2003, were used. The result was that the model trained on the synthetic data set achieved an accuracy that was about 50% better than the accuracy of the same model trained on the real data set. Keywords Synthetic data set, Generating synthetic data set, Machine learning, Deep Learning, Convolutional Neural Networks, Machine learning model, Character recognition in natural images, Char74k, ICDAR2003. ii Sammanfattning Vid utvecklandet av maskininlärningsmodeller kan avsaknaden av ett tillräckligt stort dataset för träning utgöra ett problem. En vanlig lösning är att använda syntetiskt genererad data för att antingen utöka eller helt ersätta ett dataset med verklig data. -

(Ō) 016A (Ū) Window 7
Window 7 - Hawaiian Font Support Fonts highlighted in light green contain all of vowel-macron combinations and the ‘okina in its preferred location. Those highlighted in yellow have all vowel-macron combinations but lack the ‘okina in its preferred location. All others have missing vowel-macron combinations. To download a keyboard that will allow you to type Hawaiian using these fonts, visit: http://www.olelo.hawaii.edu/enehana/winkbd.php and select "Download "Hawaiian Unicode Keyboard" For Windows". 02BB (ʻ) 0100 (Ā) 0101 (ā) 0112 (Ē) 0113 (ē) 012A (Ī) 012B (ī) 014C (Ō) 014D (ō) 016A (Ū) 016B (ū) Arabic Typesetting ✖ YES YES YES YES YES YES YES YES YES YES Arial YES YES YES YES YES YES YES YES YES YES YES Arial Black ✖ YES YES YES YES YES YES YES YES YES YES Arial Narrow ✖ YES YES YES YES YES YES YES YES YES YES Arial Unicode MS YES YES YES YES YES YES YES YES YES YES YES Batang ✖ YES YES YES YES YES YES YES YES YES YES BatangChe ✖ YES YES YES YES YES YES YES YES YES YES Berylium ✖ YES YES YES YES YES YES YES YES YES YES Blue Highway ✖ YES YES YES YES YES YES YES YES YES YES Blue Highway Condensed ✖ YES YES YES YES YES YES YES YES YES YES Blue Highway Linocut ✖ YES YES YES YES YES YES YES YES YES YES Book Antiqua ✖ YES YES YES YES YES YES YES YES YES YES Bookman Old Style ✖ YES YES YES YES YES YES YES YES YES YES Calibri YES YES YES YES YES YES YES YES YES YES YES Cambria YES YES YES YES YES YES YES YES YES YES YES Cambria Math YES YES YES YES YES YES YES YES YES YES YES Candara ✖ YES YES YES YES YES YES YES YES YES YES Castellar ✖ YES -
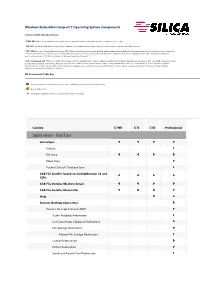
Windows Embedded Compact 7 Operating System Components
Windows Embedded Compact 7 Operating System Components Column and SKU listing Descriptions "C7NR" SKU : Offers key foundational operating system components targeted towards portable navigation devices only. "C7E" SKU : Provides OEMs with a comprehensive package of operating components to develop a wide variety of general embedded devices. "C7G" SKU : Provides Consumer Internet Device (CID) OEMs a competitive package that includes web browsing, media playback and messaging as well as foundati onal and connectivity technologies necessary for internet devices. These SKUs are ideal for set top boxes, portable media players, mobile internet devices, digital picture frames, digital media adapters, and eLearning devices. C7G SKU is available on Windo ws Embedded Compact 7. “C7P” Professional SKU : Offers the richest set of components and applications to enable complex consumer and enterprise class devices. Professional SKU can satisfy complex scenarios such as remote desktop connectivity, data sync via Active Sync, web browsing, media playback, email, contact management, and voice communication. It also includes a software development kit to allow devices to be customized and extended by end customers. Professional SKU is ideal for many device ca tegorie s including thin clients, mobile handheld terminals, and industrial automation controllers. OS Components Table Key Indicates that the corresponding catalog item is included in that particular run -time license. Denotes New Item Designates additional clarification appears at the end of the page -

Suitcase Fusion 8 Guide
Copyright © 2014–2018 Celartem, Inc., doing business as Extensis. This document and the software described in it are copyrighted with all rights reserved. This document or the software described may not be copied, in whole or part, without the written consent of Extensis, except in the normal use of the software, or to make a backup copy of the software. This exception does not allow copies to be made for others. Licensed under U.S. patents issued and pending. Celartem, Extensis, LizardTech, MrSID, NetPublish, Portfolio, Portfolio Flow, Portfolio NetPublish, Portfolio Server, Suitcase Fusion, Type Server, TurboSync, TeamSync, and Universal Type Server are registered trademarks of Celartem, Inc. The Celartem logo, Extensis logos, LizardTech logos, Extensis Portfolio, Font Sense, Font Vault, FontLink, QuickComp, QuickFind, QuickMatch, QuickType, Suitcase, Suitcase Attaché, Universal Type, Universal Type Client, and Universal Type Core are trademarks of Celartem, Inc. Adobe, Acrobat, After Effects, Creative Cloud, Creative Suite, Illustrator, InCopy, InDesign, Photoshop, PostScript, Typekit and XMP are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apache Tika, Apache Tomcat and Tomcat are trademarks of the Apache Software Foundation. Apple, Bonjour, the Bonjour logo, Finder, iBooks, iPhone, Mac, the Mac logo, Mac OS, OS X, Safari, and TrueType are trademarks of Apple Inc., registered in the U.S. and other countries. macOS is a trademark of Apple Inc. App Store is a service mark of Apple Inc. IOS is a trademark or registered trademark of Cisco in the U.S. and other countries and is used under license. Elasticsearch is a trademark of Elasticsearch BV, registered in the U.S. -

American Recycled Plastic, Inc Font Listing
American Recycled Plastic, Inc Font Listing Most Popular Fonts Font Example Arial Rounded MT Bold ABCDEFG abcdefg 1234567890 Century Gothic ABCDEFG abcdefg 1234567890 Comic Sans MS ABCDEFG abcdefg 1234567890 Lucida Sans ABCDEFG abcdefg 1234567890 Tahoma ABCDEFG abcdefg 1234567890 Times New Roman ABCDEFG abcdefg 1234567890 Alphabetical Font List Font Example Agency FB ABCDEFG abcdefg 1234567890 Aharoni ABCDEFG abcdefg 1234567890 Andalus ABCDEFG abcdefg 1234567890 AR BLANCA ABCDEFG abcdefg 1234567890 AR ESSENCE ABCDEFG abcdefg 1234567890 Arial ABCDEFG abcdefg 1234567890 Arial Black ABCDEFG abcdefg 1234567890 Arial Narrow ABCDEFG abcdefg 1234567890 Arial Rounded MT Bold ABCDEFG abcdefg 1234567890 Book Antiqua ABCDEFG abcdefg 1234567890 Century Gothic ABCDEFG abcdefg 1234567890 Comic Sans MS ABCDEFG abcdefg 1234567890 Corbel ABCDEFG abcdefg 1234567890 DokChampa ABCDEFG abcdefg 1234567890 Dotum ABCDEFG abcdefg 1234567890 Ebrima ABCDEFG abcdefg 1234567890 Eras Bold ITC ABCDEFG abcdefg 1234567890 Eras Demi ITC ABCDEFG abcdefg 1234567890 Eras Medium ITC ABCDEFG abcdefg 1234567890 Estrangelo Edessa ABCDEFG abcdefg 1234567890 Franklin Gothic Book ABCDEFG abcdefg 1234567890 Franklin Gothic Demi ABCDEFG abcdefg 1234567890 Garamond ABCDEFG abcdefg 1234567890 Gautami ABCDEFG abcdefg Gill Sans MT ABCDEFG abcdefg 1234567890 Gisha ABCDEFG abcdefg 1234567890 KaiTi ABCDEFG abcdefg 1234567890 Kalinga ABCDEFG abcdefg 1234567890 Kartika ABCDEFG abcdefg 1234567890 Khmer UI ABCDEFG abcdefg 1234567890 Lao UI ABCDEFG abcdefg 1234567890 Latha ABCDEFG abcdefg 1234567890 -

Font Samples
Beyond Sky 28 Days Later 4th and Inches @Premier League with Lion Numbe A Charming Font A Charming Font Expanded A Charming Font Italic A Charming Font Leftleaning A Charming Font Outline A Charming Font Superexpanded Aachen-Bold Action Jackson AdLib BT AdLib WGL4 BT Adobe Arabic Adobe Fan Heiti Std B Adobe Gothic Std B Adobe Hebrew Adobe Heiti Std R Adobe Ming Std L Adobe Myungjo Std M Adobe Song Std L Adobe Thai Adumu Adumu Inline Aerospace BT Aerovias Brasil NF Agency FB Agfa Rotis Sans Serif Airstream Akron Aldine401 BT Aldine721 BdCn BT Aldine721 BT Aldine721 Lt BT Alex Brush Algerian Algerian Basic D Alien Encounters Alien Encounters Solid Allegro BT AlphabetSoup Tilt BT AlternateGothic2 BT Altrincham AltrinchamConReg Amazone BT Amelia BT American Captain Americana BT Americana XBd BT Americana XBdCn BT AmericanText BT AmeriGarmnd BT Amerigo BT Amerigo Md BT Amienne AndrewScript_1.6 ANGEL TEARS Animals 1 Animals 2 Another Round Antlers Demo AquilineTwo Arial Arial Black Arial Narrow Arial Rounded MT Bold Arial Unicode MS Armed and Traitorous Aromatica Aromatica Bold Aromatica ExtraLight Aromatica Light Aromatica Patterns Aromatica Script Aromatica SemiBold Arrows1 Arrows2 Arrus Blk BT Arrus Blk OSF BT Arrus BT Arrus Ext BT Arrus OSF BT Arrus SmCap BT Ashyhouse Assembled From Scratch AURORA Aurora BdCn BT Aurora Cn BT Avenir LT Std 35 Light Avenir LT Std 65 Medium Awards Bad Coma Bad Signal Badger Bold Badger Heavy Badger Light Bahnhof Ultra Bahnschrift Bahnschrift Condensed Bahnschrift Light Bahnschrift Light Condensed Bahnschrift