OCG Computer E .Indd
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Business Process Outsourcing Connecting with New Markets
Business Process Outsourcing Connecting with new markets Edition 2017/2018 KEY FACTS Official name: Inflation rate, 2016: The Republic of Moldova 6.4 % Autonomous Territorial Unit of Gagauzia (ATU) Unique tax of 7% for IT park residents Area: 1,848 km² Corporate tax: in Free Economic Zones: 12 % 6%, 0% Population: 162,000 inhabitants VAT: in Free Economic Zones: 20%, 8% 0% Language: Gagauzian (Turkic Language Family), Employment rate: Russian and Romanian are most 32% commonly spoken languages in Gagauzia The average gross monthly wage in IT sector:* Capital of ATU Gagauzia: 650 EUR Comrat (26,200 inhabitants) Currency: Moldovan Leu (MDL) *Source: www.statistica.md CONTENT Key Facts 1 Why bussiness process outsoursing to Gagauzia? 3 Bussines process outsourcing (BPO) and ICT 5 Telecommunications 8 Telephony 9 Internet 9 Incentives in ICT sector 11 Bussiness partners 12 Association of ICT companies 12 Invest in Moldova & Invest Gagauzia help you 13 WHY BUSINESS PROCESS OUTSOURCING TO GAGAUZIA? Human capital • Gagauzia is an autonomous region of the Republic of Moldova. The region has a population of 162,000 inhabitants. Comrat municipality is the administrative center of Autonomous Territorial Unit with 23,556 inhabitants. Over 80 percent of the total population speaks Gagauz language which is closely linked to Turkic language family. That enables Gagauz people to speak and understand Turkish and Azerbaijani languages. Russian and Romanian are second most spoken languages in Gagauzia. English is widely spoken and understood by the youth; • Work force – the employable population constitutes 104.8 thousand people, which make up for 64.8 % of total population; • Yearly, circa 750 students graduate from the State University of Comrat, two colleges and three vocational schools. -

Digitalization of Public Services in Moldova in the Covid-19 Era
UNITED NATIONS DEVELOPMENT PROGRAMME DIGITALIZATION OF PUBLIC SERVICES IN MOLDOVA IN THE COVID-19 ERA The Impact of COVID-19 It is now six months since the COVID-19 pandemic engulfed our world. It has now become clear that our lives are unlikely to return quickly, if ever, to our previous normality. The COVID-19 pandemic has exposed flaws and limitations in our existing systems and norms. Everybody has either witnessed or experienced large-scale lockdowns. And although the world is re-opening now, COVID-19 is still spreading around the world. Our societies will have to adapt to a “new normal” in practically everything we do. Public services are vital for people’s livelihoods. Everyday people need public services to help them access services, register for retraining programmes or receive social benefits. In this “new normal” the government should make long-term improvements to public services, with a focus on filling the gaps in infrastructure and designing personalized public services. Virtual communication and connectedness will not end with the end of the lockdown. Face-to-face communication will still be important in service provision. However, the government should gradually create the conditions when people will not feel a radical difference between virtual (digital) and physical delivery of public services. To achieve this, it is crucial for the Government to bring the spirit of human interaction and connectedness to digital public services. How do we combine all of this and make public services efficient, personalized, trustworthy, human and most importantly safe in the post-COVID era in Moldova? We attempt to address these questions in this brief. -

The State of the Internet in France
2020 TOME 3 2020 REPORT The state of the Internet in France French Republic - June 2020 2020 REPORT The state of the Internet in France TABLE OF CONTENTS EDITORIAL 06 CHAPTER 3 ACCELERATING Editorial by Sébastien Soriano, THE TRANSITION TO IPV6 40 President of Arcep 06 1. Phasing out IPv4: the indispensable transition to IPv6 40 NETWORKS DURING 2. Barometer of the transition HET COVID-19 CRISIS 08 to IPv6 in France 47 3. Creation of an IPv6 task force 54 PART 1 000012 gathering the Internet ecosystem ENSURING THE INTERNET FUNCTIONS PROPERLY PART 2 58 CHAPTER 1 ENSURING IMPROVING INTERNET INTERNET OPENNESS QUALITY MEASUREMENT 14 CHAPTER 4 1. Potential biases of quality of service GUARANTEEING measurement 15 NET NEUTRALITY 60 2. Implementing an API in customer 1. Net neutrality outside of France 60 boxes to characterise the user environment 15 2. Arcep’s involvement in European works 65 3. Towards more transparent and robust measurement 3. Developing Arcep’s toolkit 68 18 methodologies 4. Inventory of observed practices 70 4. Importance of choosing the right test servers 22 CHAPTER 5 5. Arcep’s monitoring of mobile DEVICES AND PLATFORMS, Internet quality 26 TWO STRUCTURAL LINKS IN THE INTERNET ACCESS CHAPTER 2 CHAIN 72 SUPERVISING DATA 1. Device neutrality: progress report 72 INTERCONNECTION 29 2. Structural digital platforms 74 1. How the Internet’s architecture has evolved over time 29 2. State of interconnection in France 33 PART 3 76 TACKLE THE DIGITAL TECHNOLOGY’S ENVIRONMENTAL CHALLENGE CHAPTER 6 INTEGRATE DIGITAL TECH’S ENVIRONMENTAL FOOTPRINT INTO THE REGULATION 78 1. -

Moldova Internet Governance Forum Report 2020
MOLDOVA INTERNET GOVERNANCE FORUM REPORT 2020 November 23 – 24, 2020 Chisinau, Digital Park _________________ Hybrid event www.igf.md CONTENTS INTRODUCTORY SECTION ................................................................................................................ 2 WHAT IS THE INTERNET GOVERNANCE FORUM? ................................................................... 3 WHY MOLDOVA IGF? ......................................................................................................................... 4 MIGF 2020 PREPARATORY ACTIVITIES ........................................................................................ 6 AGENDA .................................................................................................................................................. 7 DAY 1 - Opening & Welcome session .................................................................................................... 7 DAY 1 - Session 1 ................................................................................................................................... 10 DAY 1 - Session 2 ................................................................................................................................... 11 DAY 1 - Session 3 ................................................................................................................................... 13 DAY 1 - Session 4 ................................................................................................................................... 15 DAY -

Introduction to Internet Governance
For easy reference: a list of frequently The history of this book is long, in Internet time. The used abbreviations and acronyms original text and the overall approach, including AN INTRODUCTION TO TO AN INTRODUCTION the five-basket methodology, were developed APEC Asia-Pacific Economic Co-operation in 1997 for a training course on information ccTLD country code Top-Level Domain AN INTRODUCTION TO and communications technology (ICT) policy CIDR Classless Inter-Domain Routing for government officials from Commonwealth DMCA Digital Millennium Copyright Act countries. In 2004, Diplo published a print version DNS Domain Name System of its Internet governance materials, in a booklet DRM Digital Rights Management INTERNET entitled Internet Governance – Issues, Actors and GAC Governmental Advisory Committee Divides. This booklet formed part of the Information gTLD generic Top-Level Domain INTERNET Society Library, a Diplo initiative driven by Stefano HTML HyperText Markup Language Baldi, Eduardo Gelbstein, and Jovan Kurbalija. IANA Internet Assigned Numbers Authority GOVERNANCE Special thanks are due to Eduardo Gelbstein, who ICANN Internet Corporation for Assigned made substantive contributions to the sections Names and Numbers GOVERNANCE dealing with cybersecurity, spam, and privacy, and ICC International Chamber of Commerce AN INTRODUCTION TO INTERNET GOVERNANCE Jovan Kurbalija to Vladimir Radunovic, Ginger Paque, and Stephanie aICT Information and Communications Jovan Kurbalija Borg-Psaila who updated the course materials. Technology Comments and suggestions from other colleagues IDN Internationalized Domain Name are acknowledged in the text. Stefano Baldi, Eduardo IETF Internet Engineering Task Force An Introduction to Internet Governance provides a comprehensive overview Gelbstein, and Vladimir Radunovic all contributed IGF Internet Governance Forum of the main issues and actors in this field. -

World Bank Document
Document of The World Bank FOR OFFICIAL USE ONLY Public Disclosure Authorized Report No: 59591-MD PROJECT APPRAISAL DOCUMENT ON A PROPOSED CREDIT Public Disclosure Authorized IN THE AMOUNT OF SDR 12.7 MILLION (US$20.0 MILLION EQUIVALENT) TO THE REPUBLIC OF MOLDOVA Public Disclosure Authorized FOR THE GOVERNANCE E-TRANSFORMATION PROJECT May 7, 2011 Public Disclosure Authorized This document has a restricted distribution and may be used by recipients only in the performance of their official duties. Its contents may not otherwise be disclosed without World Bank authorization. CURRENCY EQUIVALENTS (Exchange Rate Effective March 31, 2011) Currency Unit = Moldova Lei (MDL) MDL 11.94 = $1 US $1.59 = SDR 1 FISCAL YEAR January 1 – December 31 ABBREVIATIONS AND ACRONYMS $ All dollars are United States’ dollars unless otherwise indicated APPS Applications BIZTAR The Business Regulatory and Tax Administration Reform Project C/B Cost benefit ratio CEED2 Competitiveness Enhancement and Enterprise Development Project 2 CIO Chief Information Officer CLRA Cadastre and Land Relations Agency CNAM National Company of Medical Insurance CNAS National Office of Social Insurance CoA Court of Accounts CPS Country Partnership Strategy CQ Consultant’s qualifications CTS Center of Special Telecommunications eGC e-Government Center EOI Expression of interest FM Financial management GeT Governance e-Transformation GoM Government of Moldova G2B Government-to-business G2C Government-to-citizens G2G Government-to-government GPN General procurement notice ICB International -
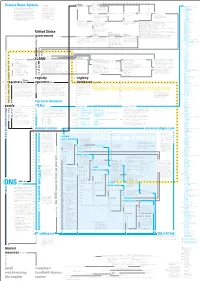
Domain Name System Concept
8 originally chartered standards charters 0 Concept Map organizations include ISoc members form 243 active ccTLDs Domain Name System rely on .ac Ascension Island (licensed) 28 Internet Society (ISoc) is a professional .ad Andorra A concept map is a web of terms. Verbs membership society with more than 150 This diagram is a model of the Domain .ae United Arab Emirates connect nouns to form propositions. organizations and 11,000 individual mem- .af Afghanistan 27 Name System (DNS), a system vital to the Groups of propositions form larger struc- bers from over 182 countries. tures. Examples and details accompany .ag Antigua and Barbuda smooth operation of the Internet. The goal most terms. More important terms re- .ai Anguilla of the diagram is to explain what DNS ceive visual emphasis; less important 11 .al Albania terms, details, and examples are in gray. IETF sponsors working groups are managed by IESG decisions can be appealed to IAB provides advice to IANA functions were moved to .am Armenia is, how it works, and how it’s governed. Terms related to names and addresses write approves .an Netherlands Antilles The diagram knits together many facts (the heart of DNS) are in blue. Terms Internet Engineering Task Force (IETF) Internet Engineering Steering Internet Architecture Board (IAB) Internet Assigned Numbers .ao Angola followed by a number link to terms pre- is a voluntary, non-commercial organization Group (IESG) Authority (IANA) originally handled .aq Antarctica about DNS in hopes of presenting a com- ceded by the same number. comprised of individuals concerned with the many of the functions that are now 626,000 .ar Argentina prehensive picture of the system and the evolution of the architecture and operation ICANN’s responsibility. -

Eap Media Freedom Watch MOLDOVA Fifth Reporting Period
EaP Media Freedom Watch MOLDOVA Fifth Reporting Period April–June 2014 The Media Freedom Index, report and expert recommendations are edited as part of the ENP East Media Freedom Watch project implemented by the Independent Journalism Center (IJC) in partnership with Internews Ukraine and with support from the European Union. This publication has been produced with the assistance of the European Union. The contents of this publication are the sole responsibility of its authors and do not necessarily reflect the views of the European Union. Contents: 1. Introductory Note 2. Panel of Experts 3. Brief Overview 4. Media Freedom Index 5. Conclusions 6. Roadmap 1. Introductory Note The Media Freedom Index and expert recommendations provided in the report are the product of the ENP East Media Freedom Watch project implemented with support from the European Union (EU). The two-year project focuses on rating media freedom in the six Eastern Partnership countries (EaP) based on quarterly questionnaires on four broad topics (politics, practice, broadcasting and Internet and new media) completed by media experts in each of the six countries. The experts rate 55 indicators from 0 to 30 for a possible total of 1,650 points. Based on the total, each country is ranked from 1 to 7 on the Index. The project is intended to contribute to media freedom and to freedom of expression by increasing regional and international awareness about the state of press freedom and journalists’ rights in all EaP countries. 2. Panel of Experts 1. Petru Macovei, Director, Association of Independent Press 2. Ludmila Andronic, Chair, Press Council 3. -

Fighting Educational Corruption in Moldova
Fighting Educational Corruption in Moldova Ihab Bennar - Morocco (American University of Beirut) Margaret Gottlieb - United States (University of Maryland) Sandra Nyanchoka - Kenya (University of Maryland) Ramz Sahuri - Jordan (American University of Beirut) A proposal for the United Nations Development Progamme by the 2014 Salzburg Academy on Media & Global Change 1 INTRODUCTION UNDP country offices in Moldova, Serbia, and Armenia have partnered on an international effort to reduce corruption across sectors. Called Youth Bridge, it is conceived as a platform for anti-corruption programs in all three countries, targeted specifically at youth between the ages of 15-24. It will be comprised of multiple projects, from games, to social media campaigns to mobile applications. The Salzburg Academy for Media and Global Change was tasked with creating specific ideas and processes that could contribute to the Youth Bridge platform. PART I: FRAMING THE PROBLEM Country: Republic of Moldova Issue: Corruption in the Education System Rationale According to a study carried out by the National Anti-Corruption Center in 2013, the most common corruption crimes in Moldova are influence paddling (32%), passive corruption (26%) and abuse of power or abuse of service (16%). Less common crimes include falsifying public documents (8%) and appropriation/embezzlement by use of official position (6%). Active corruption is rarely found in the documented criminal cases. Thus, only 3% of corruption cases are filed on active corruption, and 0.4% on taking bribes. Educational corruption is an issue everyone can find engaging because education is, for the most part, a universal experience. Corruption in the Republic of Moldova has become imprinted within society to the point of normalization. -

Intellectual Property on the Internet: a Survey of Issues
INTELLECTUAL PROPERTY ON THE INTERNET: A SURVEY OF ISSUES December 2002 WORLD INTELLECTUAL PROPERTY ORGANIZATION INTELLECTUAL PROPERTY ON THE INTERNET: A SURVEY OF ISSUES December 2002 WORLD INTELLECTUAL PROPERTY ORGANIZATION TABLE OF CONTENTS lll lll lll 3 INTRODUCTION 6 I. THE INTERNET AND THE DEVELOPMENT OF THE DIGITAL SOCIETY 8 II. THE MIGRATION OF INTELLECTUAL PROPERTY TO THE INTERNET 17 III. (a) COPYRIGHT AND RELATED RIGHTS 24 (i) INTRODUCTION TO DIGITAL COPYRIGHT 25 (ii) THE WIPO INTERNET TREATIES 26 (a) Scope of Rights 26 (b) Enforcement and Management of Rights 27 (c) Status of the WIPO Internet Treaties 29 (iii) EMERGING COPYRIGHT ISSUES 30 (a) Scope of Copyright Protection in the Digital Environment 30 (b) Liability of Internet Service Providers 32 (c) Rights of Performers in a Digital Environment 33 (d) Rights of Digital Broadcasters 34 (e) Linking of Copyright Information Online 35 (f) Protection of Databases 36 (g) Peer-to-Peer File Sharing – Napster 37 (iv) LICENSING AND RIGHTS MANAGEMENT IN THE DIGITAL ARENA 38 (a) Licensing and Collective Management of Rights 38 (b) Digital Rights Management 39 (c) Trends in Licensing and Rights Management 39 III. (b) TRADEMARKS AND OTHER RIGHTS IN DISTINCTIVE SIGNS 41 (i) IMPORTANCE OF TRADEMARKS ONLINE 41 (ii) DEVELOPMENTS IN USE OF TRADEMARKS ONLINE 41 (a) Use of Trademarks as Meta Tags 42 (b) Sale of Trademarks as Keywords 43 (c) Pop-Up Advertisements 43 (d) Mousetrapping 43 (e) Linking and framing 44 (iii) PRINCIPLE OF TERRITORIALITY AND USE OF TRADEMARKS ONLINE 44 (a) Acquisition -

MOLDOVA Mapping Digital Media: Moldova
COUNTRY REPORT MAPPING DIGITAL MEDIA: MOLDOVA Mapping Digital Media: Moldova A REPORT BY THE OPEN SOCIETY FOUNDATIONS WRITTEN BY Victor Gotisan (lead reporter) Olivia Pirt‚ac, Vitalie Dogaru, Roxana Teodorcic, Cristina Mogîldea, Tatiana Et‚co (reporters) EDITED BY Marius Dragomir and Mark Thompson (Open Society Media Program editors) Rita Rudusˇa (Regional Editor) EDITORIAL COMMISSION Yuen-Ying Chan, Christian S. Nissen, Dusˇan Reljic´, Russell Southwood, Michael Starks, Damian Tambini The Editorial Commission is an advisory body. Its members are not responsible for the information or assessments contained in the Mapping Digital Media texts OPEN SOCIETY MEDIA PROGRAM TEAM Meijinder Kaur, program assistant; Morris Lipson, senior legal advisor; and Gordana Jankovic, director OPEN SOCIETY INFORMATION PROGRAM TEAM Vera Franz, senior program manager; Darius Cuplinskas, director 10 January 2012 Contents Mapping Digital Media ..................................................................................................................... 4 Executive Summary ........................................................................................................................... 6 Context ............................................................................................................................................. 10 Social Indicators ................................................................................................................................ 12 Economic Indicators ........................................................................................................................ -

The Internet Naming System
Boston University School of Law Scholarly Commons at Boston University School of Law Faculty Scholarship 2004 Governing by Negotiation: The Internet Naming System Tamar Frankel Boston University School of Law Follow this and additional works at: https://scholarship.law.bu.edu/faculty_scholarship Part of the Internet Law Commons Recommended Citation Tamar Frankel, Governing by Negotiation: The Internet Naming System, 12 Cardozo Journal of International and Comparative Law 449 (2004). Available at: https://scholarship.law.bu.edu/faculty_scholarship/913 This Article is brought to you for free and open access by Scholarly Commons at Boston University School of Law. It has been accepted for inclusion in Faculty Scholarship by an authorized administrator of Scholarly Commons at Boston University School of Law. For more information, please contact [email protected]. GOVERNING BY NEGOTIATION: THE INTERNET NAMING SYSTEM Tamar Frankel* I. INTRODUCTION This Article is about the governance of the Internet naming system. The subject is fascinating, not simply because the naming system is an important system affecting the Internet, although it is; and not because the Internet is important, although it is. The sub- ject is fascinating because it offers a rare opportunity to examine and learn from the evolution of an incoherent governance struc- ture. The naming system is special in that it is the product of a new technology; it reflects the changes and pressures brought by the new technology, and involves the interests of government and pri- vate entities, domestic and international. And while this combina- tion is complex and special, the players are known and their motivations are quite familiar: a quest for power and money, a pro- fessional pride and national patriotism, and deep commitments to various ideologies.