Monero Mining UDURRANI
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -
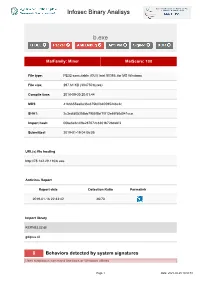
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

Hardening Windows 2000
Hardening Windows 2000 Philip Cox ([email protected]) Version 1.3 March 14, 2002 Abstract Determining what steps need to be taken to secure a system is one of the most frustrating things that system administrators have to do. This white paper provides a method for getting a Win2K server to a “secure” baseline. From this baseline you can work forward to install additional services. The focus of this white paper is on the Win2K server, but much of the information is applicable to Win2K Professional as well. This paper is excerpted and modified from Chapter 21 of the “Windows 2000 Security Handbook” (ISBN: 0-07- 212433-4, copyright Osborne/McGraw-Hill) authored by Phil Cox and Tom Sheldon (www.windows2000securityhandbook.com). Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2002. All rights reserved. All trademarks used herein are the property of their respective owners. Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2001. Table of Contents Abstract......................................................................................................................................................................1 Table Of Contents......................................................................................................................................................2 The Requirements ......................................................................................................................................................3 -

An A-Z Index of the Windows CMD Command Line
An A-Z Index of the Windows CMD command line aaADDUSERSADDUSERS Add or list users to/from a CSV file ADmodcmd Active Directory Bulk Modify ARP Address Resolution Protocol ASSOC Change file extension associations• ASSOCIAT One step file association AT Schedule a command to run at a specific time ATTRIB Change file attributes bb BCDBOOT Create or repair a system partition BCDEDIT Manage Boot Configuration Data BITSADMIN Background Intelligent Transfer Service BOOTCFG Edit Windows boot settings BROWSTAT Get domain, browser and PDC info cc CACLS Change file permissions CALL Call one batch program from another• CERTREQ Request certificate from a certification authority CERTUTIL Utility for certification authority (CA) files and services CD Change Directory - move to a specific Folder• CHANGE Change Terminal Server Session properties CHKDSK Check Disk - check and repair disk problems CHKNTFS Check the NTFS file system CHOICE Accept keyboard input to a batch file CIPHER Encrypt or Decrypt files/folders CleanMgr Automated cleanup of Temp files, recycle bin CLEARMEM Clear memory leaks CLIP Copy STDIN to the Windows clipboard CLS Clear the screen• CLUSTER Windows Clustering CMD Start a new CMD shell CMDKEY Manage stored usernames/passwords COLOR Change colors of the CMD window• COMP Compare the contents of two files or sets of files COMPACT Compress files or folders on an NTFS partition COMPRESS Compress individual files on an NTFS partition CON2PRT Connect or disconnect a Printer CONVERT Convert a FAT drive to NTFS COPY Copy one or more files -

An A-Z Index of the Windows XP Command Line
An A-Z Index of the Windows XP command line ADDUSERS Add or list users to/from a CSV file ARP Address Resolution Protocol ASSOC Change file extension associations• ASSOCIAT One step file association AT Schedule a command to run at a later time ATTRIB Change file attributes b BOOTCFG Edit Windows boot settings BROWSTAT Get domain, browser and PDC info c CACLS Change file permissions CALL Call one batch program from another• CD Change Directory - move to a specific Folder• CHANGE Change Terminal Server Session properties CHKDSK Check Disk - check and repair disk problems CHKNTFS Check the NTFS file system CHOICE Accept keyboard input to a batch file CIPHER Encrypt or Decrypt files/folders CleanMgr Automated cleanup of Temp files, recycle bin CLEARMEM Clear memory leaks CLIP Copy STDIN to the Windows clipboard. CLS Clear the screen• CLUSTER Windows Clustering CMD Start a new CMD shell COLOR Change colors of the CMD window• COMP Compare the contents of two files or sets of files COMPACT Compress files or folders on an NTFS partition COMPRESS Compress individual files on an NTFS partition CON2PRT Connect or disconnect a Printer CONVERT Convert a FAT drive to NTFS. COPY Copy one or more files to another location• CSCcmd Client-side caching (Offline Files) CSVDE Import or Export Active Directory data d DATE Display or set the date• Dcomcnfg DCOM Configuration Utility DEFRAG Defragment hard drive DEL Delete one or more files• DELPROF Delete NT user profiles DELTREE Delete a folder and all subfolders DevCon Device Manager Command Line Utility -

A Records, 244–245, 279 -A Switch in Nbtstat, 190 in Netstat, 186 AAS Deployment Package, 710 .Aas Extension, 712 Abstract
22_InsideWin_Index 13/3/03 9:50 AM Page 1269 Index A A records, 244–245, 279 ACEs (Access Control Entries) -a switch access masks in, 568–570 in Nbtstat, 190 command-line tools for, 572–576 in Netstat, 186 for cumulative permissions, 577 AAS deployment package, 710 for deny permissions, 578 .aas extension, 712 inheritance in, 579–580, 725–728 Abstract classes, 299–300 object ownership in, 572 Accelerated Graphics Port (AGP) adapters, 164 viewing and modifying, 570–571 Access Control Entries. See ACEs (Access ACKs in DHCP, 101–102 Control Entries) ACL Editor, 570, 723 Access control lists (ACLs) Advanced view in Active Directory security, 732–734 for inheritance, 578, 581 objects in, 339 for ownership, 572 in security descriptors, 559 for special permissions, 723–724 Access Control Settings window, 728 Edit view, 725–726 Access masks for permissions inheritance, 578 in ACEs, 568–570 blocking, 579 in DSOs, 733 settings for, 581 Access requests in Kerberos, 621 viewings, 582 Access rights. See also Permissions ACLs (access control lists) in Active Directory security in Active Directory security, 732–734 delegation, 729–732 objects in, 339 types of, 724–725 in security descriptors, 559 for group policies, 682 ACPI (Advanced Configuration and Power Access tokens Interface) contents of, 560–561 compatibility of, 23–28, 148–149 local, 559 kernel version for, 135 SIDs in, 559, 561, 581 for PnP,17, 147–149 ACCM (Asynchronous-Control- ACPIEnable option, 149 Character-Map), 1124 Activation Account domain upgrades, 496–498 in IA64, 130 BDC, 494–496 in installation, 49–50 PDC, 490–493 unattended setup scripts for, 95 Account lockout policies Active Directory, 238 in domain design, 429 bulk imports and exports in, 353–356 in password security, 593–594 DNS deployment in, 242–243 Account logons, auditing, 647 DNS integration in, 238–239 Account management, auditing, 511, 648 dynamic updates, 244–245 Accounts in domain migration. -

Dell EMC DD OS Administration Guide CONTENTS
Dell EMC DD OS Version 7.1 Administration Guide Revision 03 March 2020 Copyright © 2010-2020 Dell Inc. or its subsidiaries All rights reserved. Dell believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. THE INFORMATION IN THIS PUBLICATION IS PROVIDED “AS-IS.” DELL MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND WITH RESPECT TO THE INFORMATION IN THIS PUBLICATION, AND SPECIFICALLY DISCLAIMS IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. USE, COPYING, AND DISTRIBUTION OF ANY DELL SOFTWARE DESCRIBED IN THIS PUBLICATION REQUIRES AN APPLICABLE SOFTWARE LICENSE. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA. Dell EMC Hopkinton, Massachusetts 01748-9103 1-508-435-1000 In North America 1-866-464-7381 www.DellEMC.com 2 Dell EMC DD OS Administration Guide CONTENTS Preface 15 Chapter 1 Introducing DD OS 17 Revision history................................................................................................. 18 System overview............................................................................................... 18 DD OS features................................................................................................. 19 Chapter 2 Getting Started 21 Logging in and out of DD System Manager....................................................... 22 Logging in with a -

A-Z List of Windows CMD Commands — Also Included CMD Commands Commands PDF PDF
A-Z List Of Windows CMD Commands — Also Included CMD Com... https://techlog360.com/all-windows-cmd-commands/?preview_id=43... A-Z List Of Windows CMD Commands — Also Included CMD Commands Commands PDF PDF Sabarinath CMD Commands Function A addusers Used to add and list users in a CSV file admodcmd Used for bulk modifying contents in an active directory Address Resolution Protocol is used to map IP address to arp the hardware address assoc Used to change associations for file extensions associat One step file association at Run a command at a specific time atmadm Display connection info of the ATM adapter attrib Used to change file attributes B bcdboot Used to create and repair a system partition bcdedit Used to manage boot configuration data Used to manage the Background Intelligent Transfer bitsadmin Service bootcfg Used to edit boot configuration in Windows break Enable/Disable break capability (CTRL+C) in CMD C cacls Used to change permissions of files call Used one batch program to call another certreq Used to request a certificate from a certification authority certutil Manage Certification Authority files and services cd Used to change folder (directory) or go to a specific one change Used to change terminal services chcp Displays the number of active console code page chdir Same as cd command chkdsk Used to check and repair issues in the disk chkntfs Used to check the NTFS file system choice Accept user input (via keyboard) to a batch file cipher Used to encrypt/decrypt files and folder cleanmgr Used clean temp files and recycle -

Permission and Activity Auditing
CONTENT PROVIDED BY February 2014 | Redmondmag.com Permission and Activity Auditing for Windows Servers Managing user permissions is critical for security, but tracking who has access to what can easily get out of hand. Simply following best practices might not be enough. Auditing user permissions is necessary, too. Sponsored By R RVP RedmondR Vendor Profi le Unified Identity Where You Want It entrify provides Unifi ed Identity Services across databases, you can get SSO across cloud, mobile and the data center, cloud and mobile that results in on-premise applications from one single vendor. one single login for users and one unifi ed identity infrastructure for IT. Centrify’s solutions Additionally, with Centrify User Service, you need not Creduce costs and increase agility and security by leveraging sacrifi ce control of your corporate identity. Already an organization’s existing identity infrastructure to enable considered the innovative leader in leveraging Active centralized authentication, access control, privilege Directory, Centrify integrates the Centrify Cloud Service management, policy enforcement and compliance. with Active Directory without poking extra holes in your fi rewall or adding devices in your DMZ. And unlike other Because Centrify provides test support and turnkey solutions, Centrify does not make the fundamental integration with thousands of SaaS apps, complete security mistake of duplicating AD into the cloud, mobile app management and on premise plug-ins for maintaining your organization’s identity inside Active SAP NetWeaver, Java and web applications as well as Directory and under your control. Why not try it for free today? R www.centrify.com/saas-free-trial Permission and Activity Auditing for Windows Servers Permission and Activity Auditing for Windows Servers BY Brien M. -

Contents: • Enterprise Event Logging for Smbs
May 2007 Contents: • Enterprise Event Logging for SMBs..............................2 • Vista’s ActiveX Installer...……………….............................5 • Toolbox: Icacls.......................................................…….....8 • Access Denied..................................................................11 • Reader to Reader: Tips to Secure Your Backup Tapes...............................13 May 2007 Security Pro VIP Enterprise Event Logging for SMBs These 6 tools solve your tough log collection and management needs By John Howie In recent articles, I described various tools you can including email messages, network messages, and use to ease the pain of event log collection and Short Message Service (SMS) alerts via a gateway. management (see the Windows IT Pro Web-exclusive In addition, EventsManager has event-filtering article “Collecting and Analyzing Event and System capabilities that include preconfigured event queries Logs,” March 28, 2006, InstantDoc ID 49492, and the as well as a query builder that lets you build your own Windows IT Security article “Security Log Collection,” queries to retrieve events of interest from consolidated November 2006, InstantDoc ID 93330). Small-to- logs. It also lets you color-code significant events. GFI midsized businesses (SMBs) have many free or EventsManager 7.0 requires Microsoft SQL Server inexpensive tools to choose from. However, SMBs 7.0 or later or Microsoft SQL Server Desktop Engine with sophisticated needs might want to consider (MSDE) to store collected events. a log collection and management suite from one of the many vendors that provide tools designed for Even if you’ve considered and discounted previous enterprises. Here are some enterprise-class tools you versions of EventsManager, I recommend you take might want to explore. another look, if you’re in the market for an enterprise event manager.