Local Security and Permissions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Report: 7.1.6 Configure Windows Defender
Lab Report: 7.1.6 Configure Windows Defender Your Performance Your Score: 0 of 6 (0%) Pass Status: Not Passed Elapsed Time: 12 seconds Required Score: 100% Task Summary Perform a full scan once per week Hide Details Perform the scan on Saturday Perform the scan at midnight (12:00 am) Perform a full system scan Check for updates before scanning Configure default actions to take Hide Details Remove severe alert items Remove high alert items Remove medium alert items Allow low alert items Apply recommended actions to items detected during a scan Configure advanced options Hide Details Scan email Scan removable drives Display items from all users of this computer Perform a quick scan Explanation In this lab, your task is to configure Windows Defender as follows: Automatic scanning setting: Frequency: Saturday Approximate time: 12:00 am Type: Full scan (A quick scan checks the areas of the computer that spyware is likely to affect, and a full scan checks all files and programs on the computer) Check for updated definitions before scanning: Enabled Default actions settings: Severe alert items: Remove High alert items: Remove Medium alert items: Remove Low alert items: Allow Apply recommended actions: Enabled Advanced settings: Scan email: Enabled Scan removable drives: Enabled Administrator settings: Display items from all users of this computer: Enabled Complete this lab as follows: 1. Right-click Start > Control Panel. 2. In the top right corner under View by, select Small icons from the drop-down list. 3. Select Windows Defender. 4. Select Tools. 5. Under Settings, select Options. 6. Make sure Automatically scan my computer (recommended) is selected to allow Windows Defender to scan the computer automatically. -

Turning on Bitlocker Drive Encryption on Windows Computers Before You
Turning on BitLocker drive encryption on Windows computers Before you start a couple of VERY important notes... a) Make sure you have backups before you start just in case anything goes wrong (as it’s much harder, usually impossible, to recover data from an encrypted drive - as you would hope and expect). b) Make sure you keep a safe copy of the encryption key And please provide a copy for the IT Office to store for use in the event of a problem or, if you choose to let Microsoft keep it, make sure you know your login details for Microsoft. If you forget the passwords and can not recover a copy of your key you will loose all your files (which is another reason to keep backups). If you reset BitLocker and a new encryption key is set - please remember to provide a copy to the IT Office Windows 7, 8 and 10 have BitLocker Built in, this can be used to encrypt the hard drive. It just needs to be activated following the steps shown below. 1) Enable BitLocker for a Drive The easiest way to enable BitLocker for a drive is to right-click the drive in a File Explorer window, and then choose the “Turn on BitLocker” command. If you don’t see this option on your context menu. Then click on the windows icon and where it says “Type here to search” type in “encryption” and click on “Manage BitLocker” from the list of options that appears. It’s just that simple. The wizard that pops up walks you through selecting several options, which we’ve broken down into the sections that follow. -

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Mitigating Service Account Credential Theft on Windows
Mitigating Service Account Credential Theft on Windows Reducing the risk of automated authentication against untrusted endpoints Version 1.0.0 Last Updated: 2014-09-16 Mitigating Service Account Credential Theft on Windows Disclaimer This document is for informational purposes only. The authors make no warranties, express, implied, or statutory as to the information in the document. This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet website references, may change without notice. You bear the risk of using it. This document is provided under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors HD Moore Joe Bialek Ashwath Murthy Rapid7 Microsoft Palo Alto Networks Contents Executive Summary ................................................................................................................................................................ 1 Introduction ............................................................................................................................................................................ 2 Attacks .................................................................................................................................................................................... 2 Kerberos ............................................................................................................................................................................. -

Microsoft Windows FIPS 140 Validation Security Policy Document
Secure Kernel Code Integrity Security Policy Document Microsoft Windows FIPS 140 Validation Microsoft Windows 10 (Creators Update, Fall Creators Update, April 2018 Update) Microsoft Windows Server (versions 1703, 1709, and 1803) Non-Proprietary Security Policy Document Version Number 1.4 Updated On April 4, 2019 © 2018 Microsoft. All Rights Reserved Page 1 of 24 This Security Policy is non-proprietary and may be reproduced only in its original entirety (without revision). Secure Kernel Code Integrity Security Policy Document The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Windows Server Security Best Practices
Windows Server Security – Best Practices v.3.0.5 Windows Server Security Best Practices Revised – February 7, 2020 Version 2.0.0 ______________________________________________________________________________________ Page 1 of 10 Windows Server Security – Best Practices v.3.0.5 Initial Document Created by: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised by: 2019 Windows Server Security Best Practices Committee Revision Date: February 7, 2020 Version Number: 2.0.0 Acknowledgments The final release document is a collaborative work between the following committee members: Freddie Lewis Khushbu Desai Theodore McDonald Tanya Sootes Usage The ever-changing nature of information technology prevents this document from being entirely inclusive but should serve as a general guideline. This document is not intended to supersede or replace policy. Please feel free to query the Windows Server Team ([email protected]) or the Systems Administrator Group ([email protected]) for additional guidance. ______________________________________________________________________________________ Page 2 of 10 Windows Server Security – Best Practices v.3.0.5 Table of Contents Initial Document 2 Revision 2 Acknowledgments 2 Usage 2 1. Security Best Practices 5 1.1. User Environment 5 1.1.1. Server Account Control 5 1.1.2. Administrator and Equivalents 5 1.1.3. Delegating Control 5 1.1.4. Password Policy 5 1.2. File and Print Serving 5 1.2.1. Folder and NTFS Permissions 5 1.2.2. Print Management 6 1.3. Remote Access 6 1.3.1. Remote Desktop 6 1.3.2. Off-Campus Access 6 1.4. OS Configuration and Maintenance 6 1.4.1. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -
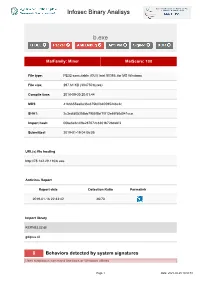
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

Invalid Class String Error
Tib4231 July, 2001 TECHNICAL INFORMATION BULLETIN Invalid Class String Error KODAK DC215, KODAK DC240, KODAK DC280, DC3400, and DC5000 Zoom Digital Cameras An Invalid Class String error may occur when you try to launch the camera software for the first time, or the Mounter or Camera Properties software may not operate properly.This error is caused when the program RegSvr32.exe is not located in the C:\Windows\System folder, preventing the DLL files from being registered. Use this document to help you properly locate the RegSvr32.exe program in your system, and if necessary, manually register the DLL files. The instructions in this document assume that you are familiar with copying and moving files in your computer, and installing software. Relocating RegSvr32.exe 1. Go to Start > Find > Files and Folders and search for regsvr32*.* Note the location of the program. 2. In WINDOWS Explorer or My Computer, copy RegSvr32.exe to the C:\Windows\System folder if it is not already there. When the file is in place, go on to Step 3. 3. Uninstall the KODAK software using the KODAK Uninstall application, or go to Start > Settings > Control Panel > Add / Remove Programs. 4. Close all background programs except Explorer and Systray by pressing Ctrl Alt Del, selecting each program one at a time, and clicking End Task after each. 5. Install the KODAK camera software. 6. Start the KODAK Camera Mounter and Camera Properties software for your camera. If the Invalid Class String error appears, manually register the DLL file using the procedure that follows for your camera. -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

Copyrighted Material
Index Numerics Address Resolution Protocol (ARP), 1052–1053 admin password, SOHO network, 16-bit Windows applications, 771–776, 985, 1011–1012 900, 902 Administrative Tools window, 1081–1083, 32-bit (x86) architecture, 124, 562, 769 1175–1176 64-bit (x64) architecture, 124, 562, 770–771 administrative tools, Windows, 610 administrator account, 1169–1170 A Administrators group, 1171 ADSL (Asynchronous Digital Subscriber Absolute Software LoJack feature, 206 Line), 1120 AC (alternating current), 40 Advanced Attributes window, NTFS AC adapters, 311–312, 461, 468–469 partitions, 692 Accelerated Graphics Port (AGP), 58 Advanced Computing Environment (ACE) accelerated video cards (graphics initiative, 724 accelerator cards), 388 Advanced Confi guration and Power access points, wireless, 996, 1121 Interface (ACPI) standard, 465 access time, hard drive, 226 Advanced Graphics Port (AGP) card, access tokens, 1146–1147 391–392 Account Operators group, 1172 Advanced Graphics Port (AGP) port, 105 ACE (Advanced Computing Environment) Advanced Host Controller Interface (AHCI), initiative, 724 212–213 ACPI (Advanced Confi guration and Power Advanced Micro Devices (AMD), 141–144 Interface) standard, 465 Advanced Packaging Tool (APT), 572 Action Center, 1191–1192 Advanced Power Management (APM) Active Directory Database, 1145–1146, 1183 standard, 465 active heat sink, 150 Advanced Programmable Interrupt active matrix display, LCD (thin-fi lm Controller (APIC), 374 transistor (TFT) display), 470 Advanced RISC Computing Specifi cation active partition, 267,