Hardening Windows 2000
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Experimental Evidence on Predatory Pricing Policies
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Edlin, Aaron S.; Roux, Catherine; Schmutzler, Armin; Thöni, Christian Working Paper Hunting unicorns? Experimental evidence on predatory pricing policies Working Paper, No. 258 Provided in Cooperation with: Department of Economics, University of Zurich Suggested Citation: Edlin, Aaron S.; Roux, Catherine; Schmutzler, Armin; Thöni, Christian (2017) : Hunting unicorns? Experimental evidence on predatory pricing policies, Working Paper, No. 258, University of Zurich, Department of Economics, Zurich, http://dx.doi.org/10.5167/uzh-138188 This Version is available at: http://hdl.handle.net/10419/173418 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. www.econstor.eu University of Zurich Department of Economics Working Paper Series ISSN 1664-7041 (print) ISSN 1664-705X (online) Working Paper No. -

Measuring the Effectiveness of Generic Malware Models
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Fall 2017 Measuring the Effectiveness of Generic Malware Models Naman Bagga San Jose State University Follow this and additional works at: https://scholarworks.sjsu.edu/etd_projects Part of the Computer Sciences Commons Recommended Citation Bagga, Naman, "Measuring the Effectiveness of Generic Malware Models" (2017). Master's Projects. 566. DOI: https://doi.org/10.31979/etd.8486-cfhx https://scholarworks.sjsu.edu/etd_projects/566 This Master's Project is brought to you for free and open access by the Master's Theses and Graduate Research at SJSU ScholarWorks. It has been accepted for inclusion in Master's Projects by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. Measuring the Effectiveness of Generic Malware Models A Project Presented to The Faculty of the Department of Computer Science San Jose State University In Partial Fulfillment of the Requirements for the Degree Master of Science by Naman Bagga December 2017 ○c 2017 Naman Bagga ALL RIGHTS RESERVED The Designated Project Committee Approves the Project Titled Measuring the Effectiveness of Generic Malware Models by Naman Bagga APPROVED FOR THE DEPARTMENTS OF COMPUTER SCIENCE SAN JOSE STATE UNIVERSITY December 2017 Dr. Mark Stamp Department of Computer Science Dr. Jon Pearce Department of Computer Science Dr. Thomas Austin Department of Computer Science ABSTRACT Measuring the Effectiveness of Generic Malware Models by Naman Bagga Malware detection based on machine learning techniques is often treated as a problem specific to a particular malware family. In such cases, detection involves training and testing models for each malware family. -
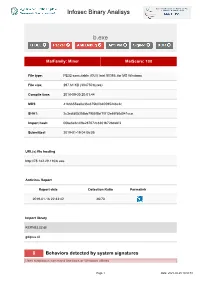
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

01001100 01001100 01001100 01001100
01001100 01001100 01001100 01001100 01010100 01010100 01010100 01010100 01000101 01000101 LTER DATABITS 01000101 01000101 01010010 01010010 01010010 01010010 _______________________________________________________________________________________ Summer 1990 Data Management Newsletter of Long-term Ecological Research Welcome to the summer 1990 issue of DATABITS! This issue features the agenda of the upcoming data manager's meeting, a report on the most recent LTER Coordinating Committee meeting, reports from the sites and some hints on using Unix and MSDOS. From the Sites BNZ-- At BCEF field season has caught up with us, and our efforts are concentrated on data acquisition and storage at a fast and furious pace. -- Phyllis Adams, Bonanza Creek LTER HFR-- A busy field season has begun, with help from summer undergraduates: among other things, we're finishing the current forest inventory, mapping trees for the hurricane pull-down and overstory deadening experiments next fall, and resampling hurricane regeneration plots. Data is entered and analyzed on the computers at the end of each field day. Indoors we're setting up new computers, digitizing GIS overlays, continuing analysis of several GIS projects, and beginning the long task of keyboarding data from the past. -- Emery Boose, Harvard Forest LTER NWT-- Recent construction of our climate database represents a level of accessibility previously unknown. Although these data (38-year record for Niwot Ridge) have been reduced and stored on magnetic tape or floppy disks for several years, difficulties associated with use of the data as stored on these media have discouraged all but the most persistent researchers from resorting to hard copies. The new climate database allows for the rapid creation of files, tailored by individual investigators to meet their parti- cular needs, that are easily loaded into a spreadsheet format. -

Predatory Pricing
UC Berkeley Law and Economics Workshop Title Predatory Pricing Permalink https://escholarship.org/uc/item/22k506ds Author Edlin, Aaron S Publication Date 2010-02-01 eScholarship.org Powered by the California Digital Library University of California Predatory Pricing 2010 Aaron S. Edlin From the Selected Works of Aaron Edlin; http://works.bepress.com/aaron edlin/74 Aaron Edlin Page 1 12/27/09 Predatory Pricing1 Aaron Edlin Richard Jennings Professor of Law and Professor of Economics, UC Berkeley And National Bureau of Economic Research . Forthcoming, Research Handbook on the Economics of Antitrust Law, edited by Einer Elhauge. Abstract Judge Breyer famously worried that aggressive prohibitions of predatory pricing throw away a bird in hand (low prices during the alleged predatory period) for a speculative bird in the bush (preventing higher prices thereafter). Here, I argue that there is no bird in hand because entry cannot be presumed. Moreover, it is plausibly commonplace that post‐entry low prices or the threat of low prices has anticompetitive results by reducing entry and keeping prices high pre‐entry and post‐predation. I analyze three potential standards for identifying predatory pricing. Two are traditional but have been tangled together and must be distinguished. First, a price‐cost test based on sacrifice theory requires that either price or cost be measured by what I describe as “inclusive” measures. A price‐cost test to prevent the exclusion of equally efficient competitors, by contrast, requires that price and cost be measured by more traditional “exclusive” measures. Finally, I describe a Consumer Betterment Standard for monopolization and consider its application to predatory pricing. -

The Sunpc 4.2 User's Guide
SunPC™ 4.2 User’s Guide A Sun Microsystems, Inc. Business 901 San Antonio Road Palo Alto, CA 94303 USA 415 960-1300 fax 415 969-9131 Part No.: 805-2933-10 Revision A, November 1997 Copyright 1997 Sun Microsystems, Inc., 901 San Antonio Road, Palo Alto, California 94303-4900 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. OpenDOS is a trademark of Cadera, Inc. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, AnswerBook, SunDocs, Solaris, OpenWindows, PC-NFS, PC-NFSpro, SunLink, and SunPC are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. -

System Files Version 8.8.0
Thoroughbred BasicTM Customization and Tuning Guide Volume II: System Files Version 8.8.0 46 Vreeland Drive, Suite 1 • Skillman, NJ 08558-2638 Telephone: 732-560-1377 • Outside NJ 800-524-0430 Fax: 732-560-1594 Internet address: http://www.tbred.com Published by: Thoroughbred Software International, Inc. 46 Vreeland Drive, Suite 1 Skillman, New Jersey 08558-2638 Copyright 2013 by Thoroughbred Software International, Inc. All rights reserved. No part of the contents of this document may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Document Number: BC8.8.0M01 The Thoroughbred logo, Swash logo, and Solution-IV Accounting logo, OPENWORKSHOP, THOROUGHBRED, VIP FOR DICTIONARY-IV, VIP, VIPImage, DICTIONARY-IV, and SOLUTION-IV are registered trademarks of Thoroughbred Software International, Inc. Thoroughbred Basic, TS Environment, T-WEB, Script-IV, Report-IV, Query-IV, Source-IV, TS Network DataServer, TS ODBC DataServer, TS ODBC R/W DataServer, TS DataServer for Oracle, TS XML DataServer, GWW, Gateway for Windows™, TS ChartServer, TS ReportServer, TS WebServer, TbredComm, WorkStation Manager, Solution-IV Reprographics, Solution-IV ezRepro, TS/Xpress, and DataSafeGuard are trademarks of Thoroughbred Software International, Inc. Other names, products and services mentioned are the trademarks or registered trademarks of their respective vendors or organizations. Notational Symbols BOLD FACE/UPPERCASE Commands or keywords you must code exactly as shown. For example, CONNECT VIEWNAME. Italic Face Information you must supply. For example, CONNECT viewname. In most cases, lowercase italics denotes values that accept lowercase or uppercase characters. UPPERCASE ITALICS Denotes values you must capitalize. For example, CONNECT VIEWNAME. -

Edlin School Handbook
EDLIN SCHOOL HANDBOOK www.edlinschool.com updated 7-25-2018 Introduction The purpose of this handbook is to outline the major rules, policies, and procedures in effect at Edlin School. Please note that while this handbook should provide answers to most questions about academic policies, disciplinary procedures, and other school practices, it will almost certainly not answer every conceivable question. In cases requiring further clarification, students and parents are encouraged to contact the Director. All parents must read the handbook and explain the policies and procedures to their children where applicable. Mission & Philosophy Edlin School strives to create an environment that fosters academic and personal growth. The students have the opportunity to partake in a diverse and advanced academic curriculum based on the classic core subjects: language arts, mathematics, science, and social studies. In addition students receive instruction in athletics, performing and visual arts, foreign languages, computers, and STEAM. The overall program is an intellectually demanding process that prepares students for the increasingly competitive and demanding further education in high school and beyond. The faculty encourages students to express themselves with confidence, clarity, and critical acumen. An ideal student-to-faculty ratio at Edlin enables teachers to employ a variety of teaching methods and styles designed to help each student reach his or her potential. The staff seeks to provide a familial, nurturing environment that encourages students to grow in self-esteem and values the dignity of each individual. The school is not parochial but does teach and support the universal values of friendliness, cooperation, and social responsibility. The school also encourages students and their families to practice such values in the outside world and hopes it receives complementary parental support. -

Series Five Integrators Kit QUICK REFERENCE GUIDE
[email protected] 1-800-784-9385 Series Five Integrators Kit QUICK REFERENCE GUIDE DESCRIPTION OF KIT The Series Five Integrators Kit from Qualitrol International includes Logicmaster 5 software by GE Fanuc, a Programmer-to-CPU cable, and a Users manual. This kit will allow you to: • Create, Transfer, and Retrieve Series Five ladder logic programs directly from any Series 5 CPU • Add names and annotation to ladder logic programs • Monitor on-line status of the program and I/O references • Save programs to diskette • Print out complete ladder programs with annotation and I/O status tables The software runs on any computer capable of providing a DOS window. The instructions that follow explain how to Install and Initiate communications to a Series Five CPU. 1. Hardware Confi guration Confi guring the CPU Communication Port The CCM port on the CPU module in the Series Five PLC is connected by cable to port 1 (COMl) or port 2 (COM2) on the Logicmaster host computer. The CCM port provides either RS-232 or RS- 422communications. - Locate DIP switch packages on the front of the Series Five CPU, behind the door. - Set the Switches 1, 2, and 3 to the ON position. This sets the DCU to communicate at 9600 baud, RS-232 and CPU ID equal to 1. Attach CPU to the Computer - Plug the 9-pin end of the cable to the COM port on the computer. - Plug the 25-pin end of the cable to the lower communications port on the Series Five CPU. 2. Software Confi guration Logicmaster 5 software is a DOS-based program and needs to be installed and run in a DOS environment Installation on a DOS machine: - Modify the CONFIG.SYS fi le (located in your hard drive’s root directory) in order to add the following lines and then reboot the PC.