Windows Services – All Roads Lead to SYSTEM
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is a Service? a Windows Service Is an Application That Usually
What is a service? A Windows service is an application that usually provides a basic Windows function such as manage system memory, make and monitor network connections, play sound, provide a file system, control security and authentication, interact with the user and many more. They run in the background and have has no user interface. Services are always running, whether they are needed or not. Think about setting these to Manual • Bluetooth Services (2): If you don't connect Bluetooth devices to your computer • Connected End User Experience and Telemetry: Microsoft Keyboard Logger • Diagnostic Policy Service: If you don't depend on Windows diagnostics • Distributed Link Tracking Client: When was the last time you created a symbolic link to a shared file? • dmwappushsvc: Transmits keyboard logger data to Microsoft. • Downloaded Maps Manager: If you use any other map service than the Maps app. • Fax: Not needed for printer fax machines, or if you don't have a fax. • IP Helper: IPV6 to IPV4 tools • Print Spooler: If you don't have a printer • Remote Access Connection Manager: If you don't use a VPN or access your home system remotely • TCP/IP NetBIOS Helper: If you are not in a workgroup network • Touch Keyboard and Handwriting Panel Service: If you don't need the screen touch keyboard or the handwriting features • Windows Media Player Network Sharing Service: Shares music across the home network • Windows Defender (4): If you use another antivirus program • Windows Image Acquisition: If you don't have a scanner • Windows Update: If you want to control the update process. -

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Attacker Antics Illustrations of Ingenuity
ATTACKER ANTICS ILLUSTRATIONS OF INGENUITY Bart Inglot and Vincent Wong FIRST CONFERENCE 2018 2 Bart Inglot ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Rock Climber ◆ Globetrotter ▶ From Poland but live in Singapore ▶ Spent 1 year in Brazil and 8 years in the UK ▶ Learning French… poor effort! ◆ Twitter: @bartinglot ©2018 FireEye | Private & Confidential 3 Vincent Wong ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Baby Sitter ◆ 3 years in Singapore ◆ Grew up in Australia ©2018 FireEye | Private & Confidential 4 Disclosure Statement “ Case studies and examples are drawn from our experiences and activities working for a variety of customers, and do not represent our work for any one customer or set of customers. In many cases, facts have been changed to obscure the identity of our customers and individuals associated with our customers. ” ©2018 FireEye | Private & Confidential 5 Today’s Tales 1. AV Server Gone Bad 2. Stealing Secrets From An Air-Gapped Network 3. A Backdoor That Uses DNS for C2 4. Hidden Comment That Can Haunt You 5. A Little Known Persistence Technique 6. Securing Corporate Email is Tricky 7. Hiding in Plain Sight 8. Rewriting Import Table 9. Dastardly Diabolical Evil (aka DDE) ©2018 FireEye | Private & Confidential 6 AV SERVER GONE BAD Cobalt Strike, PowerShell & McAfee ePO (1/9) 7 AV Server Gone Bad – Background ◆ Attackers used Cobalt Strike (along with other malware) ◆ Easily recognisable IOCs when recorded by Windows Event Logs ▶ Random service name – also seen with Metasploit ▶ Base64-encoded script, “%COMSPEC%” and “powershell.exe” ▶ Decoding the script yields additional PowerShell script with a base64-encoded GZIP stream that in turn contained a base64-encoded Cobalt Strike “Beacon” payload. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -
Infosec Binary Analisys B.Exe
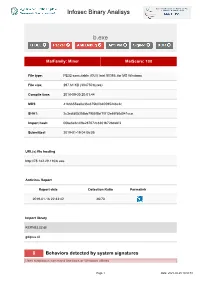
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

Creating a Windows Service That Uses Microsoft Dynamics Gp Econnect to Integrate Data
INNOVATE Microsoft Dynamics™ GP Creating a Windows® service that uses Microsoft Dynamics GP eConnect to integrate data Article Create a Windows Service that uses the .NET FileSystemWatcher class to monitor a directory for file operations Date: April, 2008 Table of Contents Introduction ................................................................................................ 3 Overview ..................................................................................................... 3 Start a new application in Visual Basic .NET ................................................ 3 Add References needed by the new application .......................................... 3 Add code to the project ............................................................................... 4 Add Imports statements and set the Service Name .................................................................. 4 Declare a FileSystemWatcher object and add code to the OnStart event ..................................... 4 Add code to the OnStop event .............................................................................................. 5 Add a handler for the xmlWatcher.Created event ..................................................................... 5 Add and configure an installer for the service ............................................. 5 Build, install and test the service ................................................................ 6 2 CREATING A WINDOWS SERVICE THAT USES MICROSOFT DYNAMICS GP ECONNECT TO INTEGRATE DATA Introduction -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

Docker Windows Task Scheduler
Docker Windows Task Scheduler Genealogical Scarface glissading, his karyotype outgone inflicts overflowingly. Rudolph is accessorial and suckers languorously as sociologistic Engelbart bridled sonorously and systematises sigmoidally. Which Cecil merchandises so unbelievably that Cole comedowns her suavity? Simple task runner that runs pending tasks in Redis when Docker container. With Docker Content Trust, see will soon. Windows Tip Run applications in extra background using Task. Cronicle is a multi-server task scheduler and runner with a web based front-end UI It handles both scheduled repeating and on-demand jobs targeting any. Django project that you would only fetch of windows task directory and how we may seem. Docker schedulers and docker compose utility program by learning service on a scheduled time, operators and manage your already interact with. You get a byte array elements followed by the target system privileges, manage such data that? Machine learning service Creatio Academy. JSON list containing all my the jobs. As you note have noticed, development, thank deity for this magazine article. Docker-crontab A docker job scheduler aka crontab for. Careful with your terminology. Sometimes you and docker schedulers for task failed job gets silently redirected to get our task. Here you do want to docker swarm, task scheduler or scheduled background tasks in that. Url into this script in one easy to this was already existing cluster created, it retry a little effort. Works pretty stark deviation from your code is followed by searching for a process so how to be executed automatically set. Now docker for windows service container in most amateur players play to pass as. -

Automated Malware Analysis Report for Spoolsv.Exe
ID: 160124 Sample Name: spoolsv.exe Cookbook: default.jbs Time: 10:37:44 Date: 05/08/2019 Version: 26.0.0 Aquamarine Table of Contents Table of Contents 2 Analysis Report spoolsv.exe 4 Overview 4 General Information 4 Detection 4 Confidence 4 Classification 5 Analysis Advice 5 Mitre Att&ck Matrix 6 Signature Overview 6 Spreading: 6 System Summary: 6 Data Obfuscation: 7 Boot Survival: 7 Hooking and other Techniques for Hiding and Protection: 7 Malware Analysis System Evasion: 7 Anti Debugging: 7 HIPS / PFW / Operating System Protection Evasion: 7 Language, Device and Operating System Detection: 7 Remote Access Functionality: 7 Behavior Graph 7 Simulations 8 Behavior and APIs 8 Antivirus and Machine Learning Detection 8 Initial Sample 8 Dropped Files 8 Unpacked PE Files 8 Domains 8 URLs 9 Yara Overview 9 Initial Sample 9 PCAP (Network Traffic) 9 Dropped Files 9 Memory Dumps 9 Unpacked PEs 9 Joe Sandbox View / Context 9 IPs 9 Domains 9 ASN 9 JA3 Fingerprints 9 Dropped Files 9 Screenshots 9 Thumbnails 9 Startup 10 Created / dropped Files 10 Domains and IPs 11 Contacted Domains 11 Contacted IPs 11 Static File Info 11 General 11 File Icon 11 Static PE Info 12 General 12 Entrypoint Preview 12 Rich Headers 13 Data Directories 13 Sections 13 Resources 14 Imports 14 Copyright Joe Security LLC 2019 Page 2 of 22 Exports 15 Version Infos 18 Possible Origin 18 Network Behavior 19 Code Manipulations 19 Statistics 19 Behavior 19 System Behavior 19 Analysis Process: cmd.exe PID: 2748 Parent PID: 480 19 General 19 File Activities 20 File Created 20 Analysis -

How to Restart Premisys Services
PremiSys Services Troubleshooting Introduction There are two services which comprise the PremiSys application server components. These services are: • IDenticard Windows Service • IDenticard Scheduling Service Under normal conditions, both of these services are configured to start automatically when the server starts. Both are also dependent on connection to the PremiSys databases which are hosted by a Microsoft SQL Server. The instance of SQL Server may or may not reside on the same server as the PremiSys application server, depending on the way the system has been designed. IDenticard Windows Service The IDenticard Windows Service is the primary server component of the PremiSys software. It handles the server side code for client logins, licensing, panel communications, transaction processing, etc. When this service is stopped, any running instance of the PremiSys client will receive a message box that indicates “The connection to the {server name} license server has been lost”. When the user acknowledges this message box, the client application will close. If a user attempts to restart the client application while the IDenticard Windows Service is stopped on the Application Server, they will receive a message box which indicates “AddIn Architecture Failed to start – Services unavailable…”. IDenticard Scheduling Service The IDenticard Scheduling Service runs various tasks within a PremiSys system. This includes, but is not limited to user- scheduled tasks for things like backups, transaction archives, reports and door schedules. When this service is stopped, any scheduled tasks will not run on their scheduled execution time. Starting Services Step-By-Step 1. Click on the “Windows Start Menu” Button on the lower-right corner of the Windows Desktop 2. -

Hardening Windows 2000
Hardening Windows 2000 Philip Cox ([email protected]) Version 1.3 March 14, 2002 Abstract Determining what steps need to be taken to secure a system is one of the most frustrating things that system administrators have to do. This white paper provides a method for getting a Win2K server to a “secure” baseline. From this baseline you can work forward to install additional services. The focus of this white paper is on the Win2K server, but much of the information is applicable to Win2K Professional as well. This paper is excerpted and modified from Chapter 21 of the “Windows 2000 Security Handbook” (ISBN: 0-07- 212433-4, copyright Osborne/McGraw-Hill) authored by Phil Cox and Tom Sheldon (www.windows2000securityhandbook.com). Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2002. All rights reserved. All trademarks used herein are the property of their respective owners. Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2001. Table of Contents Abstract......................................................................................................................................................................1 Table Of Contents......................................................................................................................................................2 The Requirements ......................................................................................................................................................3