Volume Shadow Copy and Registry Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LS-09EN. OS Permissions. SUID/SGID/Sticky. Extended Attributes
Operating Systems LS-09. OS Permissions. SUID/SGID/Sticky. Extended Attributes. Operating System Concepts 1.1 ys©2019 Linux/UNIX Security Basics Agenda ! UID ! GID ! Superuser ! File Permissions ! Umask ! RUID/EUID, RGID/EGID ! SUID, SGID, Sticky bits ! File Extended Attributes ! Mount/umount ! Windows Permissions ! File Systems Restriction Operating System Concepts 1.2 ys©2019 Domain Implementation in Linux/UNIX ! Two types domain (subjects) groups ! User Domains = User ID (UID>0) or User Group ID (GID>0) ! Superuser Domains = Root ID (UID=0) or Root Group ID (root can do everything, GID=0) ! Domain switch accomplished via file system. ! Each file has associated with it a domain bit (SetUID bit = SUID bit). ! When file is executed and SUID=on, then Effective UID is set to Owner of the file being executed. When execution completes Efective UID is reset to Real UID. ! Each subject (process) and object (file, socket,etc) has a 16-bit UID. ! Each object also has a 16-bit GID and each subject has one or more GIDs. ! Objects have access control lists that specify read, write, and execute permissions for user, group, and world. Operating System Concepts 1.3 ys©2019 Subjects and Objects Subjects = processes Objects = files (regular, directory, (Effective UID, EGID) devices /dev, ram /proc) RUID (EUID) Owner permissions (UID) RGID-main (EGID) Group Owner permissions (GID) +RGID-list Others RUID, RGID Others ID permissions Operating System Concepts 1.4 ys©2019 The Superuser (root) • Almost every Unix system comes with a special user in the /etc/passwd file with a UID=0. This user is known as the superuser and is normally given the username root. -

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Linux Filesystem Hierarchy Chapter 1
Linux Filesystem Hierarchy Chapter 1. Linux Filesystem Hierarchy 1.1. Foreward When migrating from another operating system such as Microsoft Windows to another; one thing that will profoundly affect the end user greatly will be the differences between the filesystems. What are filesystems? A filesystem is the methods and data structures that an operating system uses to keep track of files on a disk or partition; that is, the way the files are organized on the disk. The word is also used to refer to a partition or disk that is used to store the files or the type of the filesystem. Thus, one might say I have two filesystems meaning one has two partitions on which one stores files, or that one is using the extended filesystem, meaning the type of the filesystem. The difference between a disk or partition and the filesystem it contains is important. A few programs (including, reasonably enough, programs that create filesystems) operate directly on the raw sectors of a disk or partition; if there is an existing file system there it will be destroyed or seriously corrupted. Most programs operate on a filesystem, and therefore won't work on a partition that doesn't contain one (or that contains one of the wrong type). Before a partition or disk can be used as a filesystem, it needs to be initialized, and the bookkeeping data structures need to be written to the disk. This process is called making a filesystem. Most UNIX filesystem types have a similar general structure, although the exact details vary quite a bit. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -
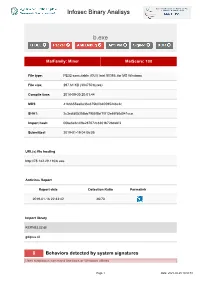
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

Autodesk Alias 2016 Hardware Qualification
Autodesk Alias 2016 Hardware Qualification Updated June 1, 2015 Windows Mac OSX Build Information Products Platform Version Software Date Build Number • Autodesk AutoStudio • Autodesk Alias Surface 64-bit 2016 March 6, 2015 201503061129-441529 • Autodesk Alias Design Supported Operating Systems and CPU Platforms Operating System CPU Platform Windows 7 SP1 Intel Xeon (Enterprise, Ultimate or Professional) 64-bit Intel Core AMD Opteron Windows 8.0 or 8.1 Intel Xeon (Enterprise or Professional) 64-bit Intel Core AMD Opteron Important Notes • Alias AutoStudio, Automotive, Surface and Design fully support 64-bit environments. Running the 64-bit native version requires Windows 8 or 8.1 64-bit or Windows 7 64-bit operating system. • Certain 3rd party software may alter the processor affinity settings, affecting multi-cpu systems running Alias.exe and its spawned processes. To check the affinity setting, right-click on the Alias.exe process inside the Windows Task Manager and select Set Affinity... ensure that all available CPUs are enabled. • Alias or its component programs may not launch successfully depending on your Windows security settings. If this occurs, you may either unblock the program via the Windows Firewall Security Alert dialog, or add it as an Exception in the Exceptions Tab in the Windows Firewall dialog box. For more information, please see the Microsoft Update. Similar configurations are necessary for any third party firewall software, Please Read • It may be possible to successfully use Alias for Windows with a non-qualified configuration, however, Support and Maintenance programs will be subject to the Autodesk Support services guidelines. • The configurations shown are subject to change, and additional qualified configurations may be added after qualification testing has been carried out. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard Filesystem Hierarchy Standard Group Edited by Rusty Russell Daniel Quinlan Filesystem Hierarchy Standard by Filesystem Hierarchy Standard Group Edited by Rusty Russell and Daniel Quinlan Published November 4 2003 Copyright © 1994-2003 Daniel Quinlan Copyright © 2001-2003 Paul ’Rusty’ Russell Copyright © 2003 Christopher Yeoh This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Table of Contents 1. Introduction........................................................................................................................................................1 1.1. -

Open Directory Administration for Version 10.5 Leopard Second Edition
Mac OS X Server Open Directory Administration For Version 10.5 Leopard Second Edition Apple Inc. © 2008 Apple Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid-for support services. Every effort has been made to make sure that the information in this manual is correct. Apple Inc., is not responsible for printing or clerical errors. Apple 1 Infinite Loop Cupertino CA 95014-2084 www.apple.com The Apple logo is a trademark of Apple Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, iCal, iChat, Leopard, Mac, Macintosh, QuickTime, Xgrid, and Xserve are trademarks of Apple Inc., registered in the U.S. and other countries. Finder is a trademark of Apple Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. UNIX is a registered trademark of The Open Group. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. -

Hardening Windows 2000
Hardening Windows 2000 Philip Cox ([email protected]) Version 1.3 March 14, 2002 Abstract Determining what steps need to be taken to secure a system is one of the most frustrating things that system administrators have to do. This white paper provides a method for getting a Win2K server to a “secure” baseline. From this baseline you can work forward to install additional services. The focus of this white paper is on the Win2K server, but much of the information is applicable to Win2K Professional as well. This paper is excerpted and modified from Chapter 21 of the “Windows 2000 Security Handbook” (ISBN: 0-07- 212433-4, copyright Osborne/McGraw-Hill) authored by Phil Cox and Tom Sheldon (www.windows2000securityhandbook.com). Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2002. All rights reserved. All trademarks used herein are the property of their respective owners. Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2001. Table of Contents Abstract......................................................................................................................................................................1 Table Of Contents......................................................................................................................................................2 The Requirements ......................................................................................................................................................3 -

TOCTTOU Attacks
CS 380S TOCTTOU Attacks Don Porter Some slides courtesy Vitaly Shmatikov and Emmett Witchel slide 1 Definitions TOCTTOU – Time of Check To Time of Use Check – Establish some precondition (invariant), e.g., access permission Use – Operate on the object assuming that the invariant is still valid Essentially a race condition Most famously in the file system, but can occur in any concurrent system 2 UNIX File System Security Access control: user should only be able to access a file if he has the permission to do so But what if user is running as setuid-root? • E.g., a printing program is usually setuid-root in order to access the printer device – Runs “as if” the user had root privileges • But a root user can access any file! • How does the printing program know that the user has the right to read (and print) any given file? UNIX has a special access() system call slide 3 TOCTTOU Example – setuid Victim checks file, if its good, opens it Attacker changes interpretation of file name Victim reads secret file Victim Attacker if(access(“foo”)) { symlink(“secret”, “foo”); fd = open(“foo”); read(fd,…); … time } 4 access()/open() Exploit Goal: trick setuid-root program into opening a normally inaccessible file Create a symbolic link to a harmless user file • access() will say that file is Ok to read After access(), but before open() switch symbolic link to point to /etc/shadow • /etc/shadow is a root-readable password file Attack program must run concurrently with the victim and switch the link at exactly the right time • Interrupt victim between access() and open() • How easy is this in practice? slide 5 Broken passwd [Bishop] Password update program on HP/UX and SunOS (circa 1996) When invoked with password file as argument… 1.