Take a Way: Exploring the Security Implications of AMD's Cache Way
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AMD's Llano Fusion
AMD’S “LLANO” FUSION APU Denis Foley, Maurice Steinman, Alex Branover, Greg Smaus, Antonio Asaro, Swamy Punyamurtula, Ljubisa Bajic Hot Chips 23, 19th August 2011 TODAY’S TOPICS . APU Architecture and floorplan . CPU Core Features . Graphics Features . Unified Video decoder Features . Display and I/O Capabilities . Power Gating . Turbo Core . Performance 2 | LLANO HOT CHIPS | August 19th, 2011 ARCHITECTURE AND FLOORPLAN A-SERIES ARCHITECTURE • Up to 4 Stars-32nm x86 Cores • 1MB L2 cache/core • Integrated Northbridge • 2 Chan of DDR3-1866 memory • 24 Lanes of PCIe® Gen2 • x4 UMI (Unified Media Interface) • x4 GPP (General Purpose Ports) • x16 Graphics expansion or display • 2 x4 Lanes dedicated display • 2 Head Display Controller • UVD (Unified Video Decoder) • 400 AMD Radeon™ Compute Units • GMC (Graphics Memory Controller) • FCL (Fusion Control Link) • RMB (AMD Radeon™ Memory Bus) • 227mm2, 32nm SOI • 1.45BN transistors 4 | LLANO HOT CHIPS | August 19th, 2011 INTERNAL BUS . Fusion Control Link (FCL) – 128b (each direction) path for IO access to memory – Variable clock based on throughput (LCLK) – GPU access to coherent memory space – CPU access to dedicated GPU framebuffer . AMD Radeon™ Memory Bus (RMB) – 256b (each direction) for each channel for GMC access to memory – Runs on Northbridge clock (NCLK) – Provides full bandwidth path for Graphics access to system memory – DRAM friendly stream of reads and write – Bypasses coherency mechanism 5 | LLANO HOT CHIPS | August 19th, 2011 Dual-channel DDR3 Unified Video DDR3 UVD Decoder NB CPU CPU Graphics SIMD Integrated Integrated GPU, Display Northbridge Array Controller I/O Controllers L2 Display L2 I/OMultimedia Controllers L2 PCI Express I/O - 24 lanes, optional 1 MB L2 cache L2 I/O per core digital display interfaces CPU CPU Digital display interfaces 4 Stars-32nm PCIe CPU cores PPL Display PCIe PCIe Display 6 | LLANO HOT CHIPS | August 19th, 2011 CPU, GPU, UVD AND IO FEATURES STARS-32nm CPU CORE FEATURES . -
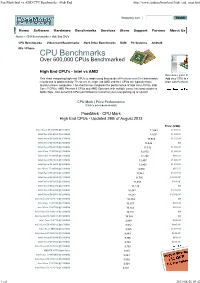
Passmark Intel Vs AMD CPU Benchmarks - High End
PassMark Intel vs AMD CPU Benchmarks - High End http://www.cpubenchmark.net/high_end_cpus.html Shopping cart | Search Home Software Hardware Benchmarks Services Store Support Forums About Us Home » CPU Benchmarks » High End CPU's CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone CPU Benchmarks Over 600,000 CPUs Benchmarked High End CPU's - Intel vs AMD How does your CPU compare? This chart comparing high end CPU's is made using thousands of PerformanceTest benchmark Add your CPU to our benchmark results and is updated daily. These are the high end AMD and Intel CPUs are typically those chart with PerformanceTest V8 found in newer computers. The chart below compares the performance of Intel Xeon CPUs, Intel Core i7 CPUs, AMD Phenom II CPUs and AMD Opterons with multiple cores. Intel processors vs ---- Select A Page ---- AMD chips - find out which CPU's performance is best for your new gaming rig or server! CPU Mark | Price Performance (Click to select desired chart) PassMark - CPU Mark High End CPUs - Updated 26th of August 2013 Price (USD) Intel Xeon E5-2687W @ 3.10GHz 14,564 $1,929.99 Intel Xeon E5-2690 @ 2.90GHz 14,511 $1,920.99 Intel Xeon E5-2680 @ 2.70GHz 13,949 $1,725.99 Intel Xeon E5-2689 @ 2.60GHz 13,444 NA Intel Xeon E5-2670 @ 2.60GHz 13,312 $1,509.00 Intel Core i7-3970X @ 3.50GHz 12,873 $1,006.99 Intel Core i7-3960X @ 3.30GHz 12,749 $965.99 Intel Xeon E5-1660 @ 3.30GHz 12,457 $1,086.99 Intel Xeon E5-2665 @ 2.40GHz 12,453 $1,499.99 Intel Core i7-3930K @ 3.20GHz 12,086 $567.27 Intel Xeon -

Motherboard Gigabyte Ga-A75n-Usb3
Socket AM3+ - AMD 990FX - GA-990FXA-UD5 (rev. 1.x) Socket AM3+ Pagina 1/3 GA- Model 990FXA- Motherboard UD5 PCB 1.x Since L2 L3Core System vendor CPU Model Frequency Process Stepping Wattage BIOS Name Cache Cache Bus(MT/s) Version AMD FX-8150 3600MHz 1MBx8 8MB Bulldozer 32nm B2 125W 5200 F5 AMD FX-8120 3100MHz 1MBx8 8MB Bulldozer 32nm B2 125W 5200 F5 AMD FX-8120 3100MHz 1MBx8 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-8100 2800MHz 1MBx8 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-6100 3300MHz 1MBx6 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-4100 3600MHz 1MBx4 8MB Bulldozer 32nm B2 95W 5200 F5 Socket AM3 GA- Model 990FXA- Motherboard UD5 PCB 1.x Since L2 L3Core System vendor CPU Model Frequency Process Stepping Wattage BIOS Name Cache Cache Bus(MT/s) Version AMD Phenom II X6 1100T 3300MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1090T 3200MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1075T 3000MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1065T 2900MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1055T 2800MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1055T 2800MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1045T 2700MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1035T 2600MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X4 980 3700MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F6 AMD Phenom II X4 975 3600MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F2 AMD Phenom II X4 970 3500MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F2 AMD Phenom II X4 965 3400MHz 512KBx4 -

Multiprocessing Contents
Multiprocessing Contents 1 Multiprocessing 1 1.1 Pre-history .............................................. 1 1.2 Key topics ............................................... 1 1.2.1 Processor symmetry ...................................... 1 1.2.2 Instruction and data streams ................................. 1 1.2.3 Processor coupling ...................................... 2 1.2.4 Multiprocessor Communication Architecture ......................... 2 1.3 Flynn’s taxonomy ........................................... 2 1.3.1 SISD multiprocessing ..................................... 2 1.3.2 SIMD multiprocessing .................................... 2 1.3.3 MISD multiprocessing .................................... 3 1.3.4 MIMD multiprocessing .................................... 3 1.4 See also ................................................ 3 1.5 References ............................................... 3 2 Computer multitasking 5 2.1 Multiprogramming .......................................... 5 2.2 Cooperative multitasking ....................................... 6 2.3 Preemptive multitasking ....................................... 6 2.4 Real time ............................................... 7 2.5 Multithreading ............................................ 7 2.6 Memory protection .......................................... 7 2.7 Memory swapping .......................................... 7 2.8 Programming ............................................. 7 2.9 See also ................................................ 8 2.10 References ............................................. -

Amd Athlon Ii X2 270 Manual
Amd Athlon Ii X2 270 Manual Specifications. Please visit AMD Athlon II X2 215 (rev. C3) and AMD Athlon II X2 270 pages for more detailed specifications. Review, Differences, Benchmarks, Specifications, Comments Athlon II X2 270. CPUBoss recommends the AMD Athlon II X2 270 based on its. See full details. Specifications. Please visit AMD Athlon II X2 270 and AMD Athlon II X2 280 pages for more detailed specifications of both. Far Cry 4 on AMD Athlon x2 340(Dual Core) 4GB RAM HD 6570 PC Specifications. Specifications. Please visit AMD Athlon II X2 270 and AMD FX-6300 pages for more detailed specifications of both. AMD Athlon II x2 260 (3.2GHz) Although the specifications of this cpu list 74C as the max temp, i prefer to stick to the old "65C max" rule-of-thumb for amd cpus. Amd Athlon Ii X2 270 Manual Read/Download AMD Athlon II X2 270u. 2 GHz, Dual core. Front view of AMD Athlon II X2 270u. 5.9 Out of 10. VS Review, Differences, Benchmarks, Specifications, Comments. Photos of the AMD Athlon II X2 270 Black Edition from the KitGuru Price Comparison Engine. Specifications. Please visit AMD Athlon II X2 270 and AMD FX-4300 pages for more detailed specifications of both. SPECIFICATIONS : Model : AMD Athlon II X2 270. CPU Clock Speed : 3.4 GHz. Core : 2. Total L2 Cache : 2 MB Sockets : Socket AM2+,Socket AM3 Supported. up vote -5 down vote favorite. These are my specifications: AMD Athlon II x2 270 CPU, AMD 760g GPU, 4GB RAM. grand-theft-auto-5. -

AMD Multi-Core Processors Providing Multiple Benefits for the Future
hard hat area | white paper AMD Multi-Core Processors Providing Multiple Benefits For The Future y now you probably have heard of variations this year. In 2007 the chipmakers (page 50). This month, we’ll focus on what dual- and multi-core processors. expect to introduce several multi-core AMD has planned for 2006 and beyond. B Both AMD and Intel released chips, beginning with quad-core offerings. dual-core chips in 2005, and both have We discussed Intel’s multi-core proces- Dual-Core Chips plans to release dozens more dual-core chip sors in the January 2006 issue of CPU In April 2005, AMD released its first dual-core chip aimed at the server and workstation market, the Opteron proces- Direct Connect Architecture vs. sor. There are several Opteron dual-core Legacy Systems 90nm processors ranging in clock speeds from 1.6GHz to 2.4GHz. Direct Connect Architecture lives up to its name by providing a for the past few years in its single-core chips. direct connection between the processor, the memory But now AMD has extended the use of Direct Connect Architecture to controller, and the I/O area to improve overall system connect the cores on a dual- or multi-core chip die and to connect each performance. AMD has used Direct Connect Architecture core to its memory controller. ▲ With multi-core architecture, each core on the chip has its own memory con- When using a dual-processor x86 legacy architecture, troller, which significantly improves memory performance. Using Direct Connect however, two processors then have to share the same Architecture to make a connection with the memory controller eliminates most memory control hub, which creates bottlenecks in data bottlenecks and makes multitasking easier. -
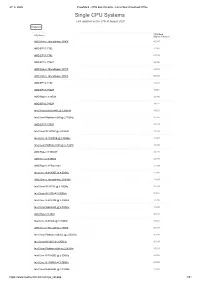
Single CPU Systems Last Updated on the 27Th of August 2020
27. 8. 2020 PassMark - CPU Benchmarks - List of Benchmarked CPUs Single CPU Systems Last updated on the 27th of August 2020 Column CPU Mark CPU Name (higher is better) AMD Ryzen Threadripper 3990X 80,087 AMD EPYC 7702 71,362 AMD EPYC 7742 67,185 AMD EPYC 7702P 64,395 AMD Ryzen Threadripper 3970X 64,009 AMD Ryzen Threadripper 3960X 55,707 AMD EPYC 7452 53,478 AMD EPYC 7502P 48,021 AMD Ryzen 9 3950X 39,246 AMD EPYC 7402P 39,118 Intel Xeon Gold 6248R @ 3.00GHz 38,521 Intel Xeon Platinum 8280 @ 2.70GHz 37,575 AMD EPYC 7302P 37,473 Intel Xeon W-3275M @ 2.50GHz 37,104 Intel Core i9-10980XE @ 3.00GHz 33,967 Intel Xeon Platinum 8168 @ 2.70GHz 33,398 AMD Ryzen 9 3900XT 33,292 AMD Ryzen 9 3900X 32,845 AMD Ryzen 9 PRO 3900 31,989 Intel Core i9-9990XE @ 4.00GHz 31,941 AMD Ryzen Threadripper 2990WX 31,899 Intel Xeon W-3175X @ 3.10GHz 31,814 Intel Xeon W-2295 @ 3.00GHz 31,724 Intel Core i9-9980XE @ 3.00GHz 31,395 Intel Xeon Gold 6248 @ 2.50GHz 31,285 AMD Ryzen 9 3900 30,816 Intel Core i9-9960X @ 3.10GHz 30,663 AMD Ryzen Threadripper 2950X 30,488 Intel Xeon Platinum 8259CL @ 2.50GHz 30,250 Intel Xeon W-3265 @ 2.70GHz 30,105 Intel Xeon Platinum 8268 @ 2.90GHz 30,103 Intel Core i9-7980XE @ 2.60GHz 29,746 Intel Core i9-10940X @ 3.30GHz 29,559 Intel Xeon Gold 6254 @ 3.10GHz 29,356 https://www.cpubenchmark.net/cpu_list.php 1/81 27. -

CNPS8700 NT More
CNPS8700 NT More Compatible with Slim Tower / Low Profile Home Theatre PC Enclosures. Pentium 4, Celeron D, Pentium D, Core 2 Duo, Core 2 Quad, Core 2 Extreme, Sempron, Athlon 64, Athlon 64 X2, Athlon 64 FX, Opteron, Dual-Core Opteron Zalman CNPS8700 NT CPU Cooler The Best of 2007: X-bit Labs Reader¡¯s Choice Awards Socket CPU CPU Compatibility Celeron D Pentium 4 Pentium D Intel 775 Supports all speeds Core 2 Duo Core 2 Quad Core 2 Extreme Sempron Athlon 64 AM2 Supports all speeds Athlon 64 X2 Athlon 64 FX Sempron 754 Supports all speeds Athlon 64 Athlon 64 AMD Athlon 64 X2 939 Athlon 64 FX Supports all speeds Opteron Dual-Core Opteron Athlon 64 FX 940 Opteron Supports all speeds Dual-Core Opteron No motherboard components such as the PSU, disk drives, VGA card, and RAM with a height greater than 39mm should be present within a 61.5mm radius from the center of the CPU. Dimensions 120(L) x 123(W) x 67(H) mm Weight 475g Base Material Pure Copper Dissipation Area 3,300§² Bearing Type 2 Ball-Bearing Speed 1,150rpm ~ 2,100rpm ¡¾ 10 % Noise Level(1) 17.5dBA ~30.0dBA ¡¾ 10% Control Method PWM Control, Auto Restart (1) Measured 1m distance away from source. Compatible with all single, dual, and quad core CPUs for Intel socket 775 and AMD socket AM2/754/939/940. Compatible with Slim Tower / Low Profile Home Theatre PC Enclosures. Automatic Fan Speed Control feature included in the Ultra Quiet 110mm PWM(Pulse Width Modulation) enabled fan. -

Amd(Amd.Us)18Q1 点评 2018 年 07 月 30 日
海外公司报告 | 公司动态研究 证券研究报告 AMD(AMD.US)18Q1 点评 2018 年 07 月 30 日 作者 AMD 7 年最佳,10 年翻身,重申买入,TP 上调至 何翩翩 分析师 23 美元 SAC 执业证书编号:S1110516080002 [email protected] 业绩超预期,7 年来最佳盈利季 雷俊成 分析师 SAC 执业证书编号:S1110518060004 AMD 18Q2 实现 7 年来最佳盈利季度,non-GAAP EPS 0.14 美元,营收 17.6 [email protected] 亿美元同比大涨 53%,均超过华尔街预期的 EPS 0.13 美元和营收 17.2 亿美 马赫 分析师 SAC 执业证书编号:S1110518070001 元。计算与图形业务同比大涨 64%至 10.9 亿美元好于市场预期的 10.6 亿, [email protected] 但受 Q2 区块链相关贡献进一步减弱带来该业务环比跌 3%。挖矿业务本季 董可心 联系人 营收占比从上季的 10%降低为 6%,公司进一步看淡下半年需求。EESC 业务 [email protected] 同比涨 37%至 6.7 亿美元,好于预期的 6.61 亿,EPYC 逐步进入放量阶段, 公司维持到年底会实现中单位数份额的预测。Q2 毛利率提升至 37%,Q3 指引营收 17 亿美元,同比增长 7%,略低于市场预期的 17.6 亿,毛利率提 相关报告 升至约 38%;全年指引营收增速保持 25%,我们认为公司指引基于 17Q3 的 1 《AMD(AMD.US)点评:EPYC“从 高基数较为保守,且区块链影响作为一次性业务逐渐消弭也会进一步减少 零到一”终实现,7nm 产品周期全方位 业绩不确定性,我们看好 EPYC 会在下半年至 Q4 迎来关键放量。 回归“传奇”;TP 上调至 22 美元,重 服务器市场 AMD 与 Intel“荣辱互见” 申买入》2018-06-20 2 《AMD(AMD.US)点评:公布 7nm 服务器市场 AMD 与 Intel“荣辱互见”,EPYC 服务器随着 Cisco、HPE 适配 GPU 加入 AI 计算抢滩战,Ryzen+EPYC 以及超级云计算客户的需求能见度提高,Q2 出货量和营收均环比提高超 50%,目前与 AMD 合作的 5 个云计算巨头成主要推动力。我们认为 AMD “双子星”仍是中流砥柱;TP 上调至 将继续通过单插槽服务器高核心数和低功耗打造性价比优势,下半年加速 18 美元,重申买入》2018-06-08 市场渗透蚕食 Intel 份额,进入明年则等待 7nm 的第二代 EPYC 面市,面对 3 《AMD(AMD.US)18Q1 点评:2018 已将 10nm Cannon Lake 量产时点延后至明年的 Intel,AMD 将终于实现制 开门红,业绩指引均超预期,Ryzen 继 程反超,加速量价齐升。“从零到一”抢占 20 亿美元以上的市场份额。 续扎实闪耀,EPYC 仍待升级放量,重 反观 Intel Q2 数据中心业务收入 55.5 亿美元,虽然在整体行业高景气度下 申买入》2018-04-30 同比增长 27%,但仍低于市场预期的 56.3 亿美元。业绩发布会上 Intel 更为 4 《2017 扭亏为盈业绩迎拐点,2018 明确消费级 10nm 产品会到 19 年下半年节日旺季才推向市场,让市场情绪 厚积待薄发,Ryzen+EPYC 继续双星闪 愈加悲观的同时也给了 AMD 足够的时间窗口。 耀,重申买入》2018-02-01 Ryzen 继续攻城略地,进一步打开笔记本市场 5 《AMD(AMD.US)点评:合作英特 -

Software-Based Undervolting Faults in AMD Zen Processors Fehler in AMD Zen Prozessoren Durch Software-Basierte Unterspannung
Software-based Undervolting Faults in AMD Zen Processors Fehler in AMD Zen Prozessoren durch Software-basierte Unterspannung Bachelorarbeit im Rahmen des Studiengangs IT-Sicherheit der Universität zu Lübeck vorgelegt von Anja Rabich ausgegeben und betreut von Prof. Dr. Thomas Eisenbarth mit Unterstützung von Luca Wilke Lübeck, den 31. August 2020 Abstract Dynamic Voltage and Frequency Scaling (DVFS) is a powerful performance enhance- ment method used by modern processors, allowing them to scale voltage or frequency as needed based on the power requirements of the CPU. This not only saves power, but also prevents processors from overheating. However, the continued integration of soft- ware interfaces giving a user direct access to this functionality has been shown to be a potential security risk, allowing a privileged adversary to indirectly tamper with sensitive computations. This thesis summarizes the results of various papers showing that using DVFS features, unsuitable voltage/frequency values can be set for the processor leading to hardware faults and calculation errors which can be used to undermine the integrity of Trusted Execution Environments (TEE). Results are partially replicated for Intel’s TEE implementation SGX, followed by extending the same methodology to AMD’s Zen Pro- cessors, on which there is currently no information. Results show that undervolting is an unlikely attack vector. iii Zusammenfassung Dynamische Spannungs- und Frequenzskalierung (engl. DVFS) ist ein in modernen Prozessoren vorhandener Leistungs- und Stromverwaltungsmechanismus, womit Span- nung und Frequenz der CPU je nach Bedarf skaliert werden können. Somit wird nicht nur Strom gespart, sondern auch zusätzlich verhindert, dass der Prozessor überhitzt. Die zunehmende Integration von Softwareschnittstellen zu diesen Mechanismen die dem Nutzer Einstellungsmöglichkeiten anbieten, haben sich zunehmend als potenzielle Sicherheitslücke erwiesen. -

High Performance Linpack Benchmark on AMD EPYC™ Processors
High Performance Linpack Benchmark on AMD EPYC™ Processors This document details running the High Performance Linpack (HPL) benchmark using the AMD xhpl binary. HPL Implementation: The HPL benchmark presents an opportunity to demonstrate the optimal combination of multithreading (via the OpenMP library) and MPI for scientific and technical high-performance computing on the EPYC architecture. For MPI applications where the per-MPI-rank work can be further parallelized, each L3 cache is an MPI rank running a multi-threaded application. This approach results in fewer MPI ranks than using one rank per core, and results in a corresponding reduction in MPI overhead. The ideal balance is for the number of threads per MPI rank to be less than or equal to the number of CPUs per L3 cache. The exact maximum thread count per MPI rank depends on both the specific EPYC SKU (e.g. 32 core parts have 4 physical cores per L3, 24 core parts have 3 physical cores per L3) and whether SMT is enabled (e.g. for a 32 core part with SMT enabled there are 8 CPUs per L3). HPL performance is primarily determined by DGEMM performance, which is in turn primarily determined by SIMD throughput. The Zen microarchitecture of the EPYC processor implements one SIMD unit per physical core. Since HPL is SIMD limited, when SMT is enabled using a second HPL thread per core will not directly improve HPL performance. However, leaving SMT enabled may indirectly allow slightly higher performance (1% - 2%) since the OS can utilize the SMT siblings as needed without pre-empting the HPL threads. -

Low-Power X86 Solutions for Networked Storage and Media Servers
Low-Power x86 Solutions for Networked Storage and Media Servers OVERVIEW fEAtuRE-RIch cApAbIlItIEs Whether at the office or at home, everyone seems to be using, AMD Processors support Microsoft® and Linux® operating systems creating, and sharing content. Information such as financial that are tailored for these markets to be easy-to-use, protect data records, email, marketing collateral, home video, music and and serve applications. For SMB users, Windows® Small Business pictures must be organized, secure and accessible. And this Server 2011 Essentials is an ideal fit. Automatic backup and information must be protected from hardware failures using recovery protects business information. Organize information, techniques such as RAID and protected from software issues serve business applications such as accounting software and by using snapshots and backup to ensure nothing is lost. connect to online services such as email and CRM. This content requires new embedded solutions to manage, Windows® Home Server organizes, protects and streams digital manipulate and store data. This embedded network storage media content throughout the home. Centralize the iTunes® folder, appliance needs to be affordable, scalable, and easy to use videos, photos and financial spreadsheets. Automatically backup for managing information for business and home users. files to a server to protect from system disk failure or recover from a software or virus attack. AMD plAtfORM sOlutIOns To help meet the wide range of performance, power and price AMD’s pROcEssOR sOlutIOns provide thE fOllowing requirements for SoHo and home users, AMD offers a selection bEnEfIts fOR nEtworkED stORAgE AnD MEDIA sERVERs ™ of processor and chipset solutions.