Software-Based Undervolting Faults in AMD Zen Processors Fehler in AMD Zen Prozessoren Durch Software-Basierte Unterspannung
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

High Performance Linpack Benchmark on AMD EPYC™ Processors
High Performance Linpack Benchmark on AMD EPYC™ Processors This document details running the High Performance Linpack (HPL) benchmark using the AMD xhpl binary. HPL Implementation: The HPL benchmark presents an opportunity to demonstrate the optimal combination of multithreading (via the OpenMP library) and MPI for scientific and technical high-performance computing on the EPYC architecture. For MPI applications where the per-MPI-rank work can be further parallelized, each L3 cache is an MPI rank running a multi-threaded application. This approach results in fewer MPI ranks than using one rank per core, and results in a corresponding reduction in MPI overhead. The ideal balance is for the number of threads per MPI rank to be less than or equal to the number of CPUs per L3 cache. The exact maximum thread count per MPI rank depends on both the specific EPYC SKU (e.g. 32 core parts have 4 physical cores per L3, 24 core parts have 3 physical cores per L3) and whether SMT is enabled (e.g. for a 32 core part with SMT enabled there are 8 CPUs per L3). HPL performance is primarily determined by DGEMM performance, which is in turn primarily determined by SIMD throughput. The Zen microarchitecture of the EPYC processor implements one SIMD unit per physical core. Since HPL is SIMD limited, when SMT is enabled using a second HPL thread per core will not directly improve HPL performance. However, leaving SMT enabled may indirectly allow slightly higher performance (1% - 2%) since the OS can utilize the SMT siblings as needed without pre-empting the HPL threads. -

AMD's Early Processor Lines, up to the Hammer Family (Families K8
AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) Dezső Sima October 2018 (Ver. 1.1) Sima Dezső, 2018 AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) • 1. Introduction to AMD’s processor families • 2. AMD’s 32-bit x86 families • 3. Migration of 32-bit ISAs and microarchitectures to 64-bit • 4. Overview of AMD’s K8 – K10.5 (Hammer-based) families • 5. The K8 (Hammer) family • 6. The K10 Barcelona family • 7. The K10.5 Shanghai family • 8. The K10.5 Istambul family • 9. The K10.5-based Magny-Course/Lisbon family • 10. References 1. Introduction to AMD’s processor families 1. Introduction to AMD’s processor families (1) 1. Introduction to AMD’s processor families AMD’s early x86 processor history [1] AMD’s own processors Second sourced processors 1. Introduction to AMD’s processor families (2) Evolution of AMD’s early processors [2] 1. Introduction to AMD’s processor families (3) Historical remarks 1) Beyond x86 processors AMD also designed and marketed two embedded processor families; • the 2900 family of bipolar, 4-bit slice microprocessors (1975-?) used in a number of processors, such as particular DEC 11 family models, and • the 29000 family (29K family) of CMOS, 32-bit embedded microcontrollers (1987-95). In late 1995 AMD cancelled their 29K family development and transferred the related design team to the firm’s K5 effort, in order to focus on x86 processors [3]. 2) Initially, AMD designed the Am386/486 processors that were clones of Intel’s processors. -

AMD Raven Ridge
DELIVERING A NEW LEVEL OF VISUAL PERFORMANCE IN AN SOC AMD “RAVEN RIDGE” APU Dan Bouvier, Jim Gibney, Alex Branover, Sonu Arora Presented by: Dan Bouvier Corporate VP, Client Products Chief Architect AMD CONFIDENTIAL RAISING THE BAR FOR THE APU VISUAL EXPERIENCE Up to MOBILE APU GENERATIONAL 200% MORE CPU PERFORMANCE PERFORMANCE GAINS Up to 128% MORE GPU PERFORMANCE Up to 58% LESS POWER FIRST “Zen”-based APU CPU Performance GPU Performance Power HIGH-PERFORMANCE AMD Ryzen™ 7 2700U 7th Gen AMD A-Series APU On-die “Vega”-based graphics Scaled GPU Managed Improved Upgraded Increased LONG BATTERY LIFE and CPU up to power delivery memory display package Premium form factors reach target and thermal bandwidth experience performance frame rate dissipation efficiency density 2 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | * See footnotes for details. “RAVEN RIDGE” APU AMD “ZEN” x86 CPU CORES CPU 0 “ZEN” CPU CPU 1 (4 CORE | 8 THREAD) USB 3.1 NVMe PCIe FULL PCIe GPP ----------- ----------- Discrete SYSTEM 4MB USB 2.0 SATA GFX CONNECTIVITY CPU 2 CPU 3 L3 Cache X64 DDR4 HIGH BANDWIDTH SOC FABRIC System Infinity Fabric & MEMORY Management SYSTEM Unit ACCELERATED Platform Multimedia Security MULTIMEDIA Processor Engines AMD GFX+ 1MB L2 EXPERIENCE X64 DDR4 (11 COMPUTE UNITS) Cache Video Audio Sensor INTEGRATED CU CU CU CU CU CU Display Codec ACP Fusion Controller Next SENSOR Next Hub FUSION HUB CU CU CU CU CU AMD “VEGA” GPU UPGRADED DISPLAY ENGINE 3 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | SIGNIFICANT DENSITY INCREASE “Raven Ridge” die BGA Package: 25 x 35 x 1.38mm Technology: GLOBALFOUNDRIES 14nm – 11 layer metal Transistor count: 4.94B 59% 16% Die Size: 209.78mm2 more transistors smaller die than prior generation “Bristol Ridge” APU 4 | AMD Ryzen™ Processors with Radeon™ Vega Graphics - Hot Chips 30 | * See footnotes for details. -

SMBIOS Specification
1 2 Document Identifier: DSP0134 3 Date: 2019-10-31 4 Version: 3.4.0a 5 System Management BIOS (SMBIOS) Reference 6 Specification Information for Work-in-Progress version: IMPORTANT: This document is not a standard. It does not necessarily reflect the views of the DMTF or its members. Because this document is a Work in Progress, this document may still change, perhaps profoundly and without notice. This document is available for public review and comment until superseded. Provide any comments through the DMTF Feedback Portal: http://www.dmtf.org/standards/feedback 7 Supersedes: 3.3.0 8 Document Class: Normative 9 Document Status: Work in Progress 10 Document Language: en-US 11 System Management BIOS (SMBIOS) Reference Specification DSP0134 12 Copyright Notice 13 Copyright © 2000, 2002, 2004–2019 DMTF. All rights reserved. 14 DMTF is a not-for-profit association of industry members dedicated to promoting enterprise and systems 15 management and interoperability. Members and non-members may reproduce DMTF specifications and 16 documents, provided that correct attribution is given. As DMTF specifications may be revised from time to 17 time, the particular version and release date should always be noted. 18 Implementation of certain elements of this standard or proposed standard may be subject to third party 19 patent rights, including provisional patent rights (herein "patent rights"). DMTF makes no representations 20 to users of the standard as to the existence of such rights, and is not responsible to recognize, disclose, 21 or identify any or all such third party patent right, owners or claimants, nor for any incomplete or 22 inaccurate identification or disclosure of such rights, owners or claimants. -

AMD Introduces World's Most Powerful 16- Core
November 7, 2019 AMD Introduces World’s Most Powerful 16- core Consumer Desktop Processor, the AMD Ryzen™ 9 3950X – AMD Ryzen™ 9 3950X rounds out 3rd Gen Ryzen desktop processor series, arriving November 25 – – New AMD Athlon™ 3000G processor to provide everyday users with unmatched performance per dollar, coming November 19 – SANTA CLARA, Calif., Nov. 07, 2019 (GLOBE NEWSWIRE) -- Today, AMD announced the release of the highly anticipated flagship 16-core AMD Ryzen 9 3950X processor, available worldwide November 25, 2019. AMD Ryzen 9 3950X processor brings the ultimate processor for gamers with effortless 1080P gaming in select titles1 and up to 2X more energy efficient processing power compared to the competition2 as the world’s fastest 16- core consumer desktop processor3. In addition, AMD also announced a significant performance uplift4 coming for mainstream desktop users with the new AMD Athlon 3000G, arriving November 19, 2019. “We are excited to bring the AMD Ryzen™ 9 3950X to market later this month, offering enthusiasts the most powerful 16-core desktop processor ever,” said Chris Kilburn, corporate vice president and general manager, client channel, AMD. “We are focused on offering the best solutions at every level of the market, including the AMD Athlon 3000G for everyday PC users that delivers great performance at an incredible price point.” AMD Ryzen 9 3950X: Fastest 16-core Consumer Desktop Processor Offering up to 22% performance increase over previous generations5, the AMD Ryzen 9 3950X offers faster 1080p gaming in select titles1 and content creation6 than the competition. Built on the industry-leading “Zen 2” architecture, the AMD Ryzen 9 3950X also excels in power efficiency3 with a TDP7 of 105W. -

Take a Way: Exploring the Security Implications of AMD's Cache Way
Take A Way: Exploring the Security Implications of AMD’s Cache Way Predictors Moritz Lipp Vedad Hadžić Michael Schwarz Graz University of Technology Graz University of Technology Graz University of Technology Arthur Perais Clémentine Maurice Daniel Gruss Unaffiliated Univ Rennes, CNRS, IRISA Graz University of Technology ABSTRACT 1 INTRODUCTION To optimize the energy consumption and performance of their With caches, out-of-order execution, speculative execution, or si- CPUs, AMD introduced a way predictor for the L1-data (L1D) cache multaneous multithreading (SMT), modern processors are equipped to predict in which cache way a certain address is located. Conse- with numerous features optimizing the system’s throughput and quently, only this way is accessed, significantly reducing the power power consumption. Despite their performance benefits, these op- consumption of the processor. timizations are often not designed with a central focus on security In this paper, we are the first to exploit the cache way predic- properties. Hence, microarchitectural attacks have exploited these tor. We reverse-engineered AMD’s L1D cache way predictor in optimizations to undermine the system’s security. microarchitectures from 2011 to 2019, resulting in two new attack Cache attacks on cryptographic algorithms were the first mi- techniques. With Collide+Probe, an attacker can monitor a vic- croarchitectural attacks [12, 42, 59]. Osvik et al. [58] showed that tim’s memory accesses without knowledge of physical addresses an attacker can observe the cache state at the granularity of a cache or shared memory when time-sharing a logical core. With Load+ set using Prime+Probe. Yarom et al. [82] proposed Flush+Reload, Reload, we exploit the way predictor to obtain highly-accurate a technique that can observe victim activity at a cache-line granu- memory-access traces of victims on the same physical core. -

EPYC: Designed for Effective Performance
EPYC: Designed for Effective Performance By Linley Gwennap Principal Analyst June 2017 www.linleygroup.com EPYC: Designed for Effective Performance By Linley Gwennap, Principal Analyst, The Linley Group Measuring server-processor performance using clock speed (GHz) or even the traditional SPEC_int test can be misleading. AMD’s new EPYC processor is designed to deliver strong performance across a wide range of server applications, meeting the needs of modern data centers and enterprises. These design capabilities include advanced branch prediction, data prefetching, coherent interconnect, and integrated high-bandwidth DRAM and I/O interfaces. AMD sponsored the creation of this white paper, but the opinions and analysis are those of the author. Trademark names are used in an editorial fashion and are the property of their respective owners. Although many PC users can settle for “good enough” performance, data-center opera- tors are always seeking more. Web searches demand more performance as the Internet continues to expand. Newer applications such as voice recognition (for services such as Alexa and Siri) and analyzing big data also require tremendous performance. Neural networks are gaining in popularity for everything from image recognition to self-driving cars, but training these networks can tie up hundreds of servers for days at a time. Processor designers must meet these greater performance demands while staying within acceptable electrical-power ratings. Server processors are often characterized by core count and clock speed (GHz), but these characteristics provide only a rough approximation of application performance. As important as speed is, the amount of work that a processor can accomplish with each tick of the clock, a parameter known as instructions per cycle (IPC), is equally important. -

AMD Zen Rohin, Vijay, Brandon Outline
AMD Zen Rohin, Vijay, Brandon Outline 1. History and Overview 2. Datapath Structure 3. Memory Hierarchy 4. Zen 2 Improvements History and Overview AMD History ● IBM production too large, forced Intel to license their designs to 3rd parties ● AMD fills the gap, produces clones for 15ish years - legal battles ensued ● K5 first in-house x86 chip in 1996 ● Added more features like out of order, L2 caches, etc ● Current CPUs are Zen* tomshardware.com/picturestory/71 3-amd-cpu-history.html Zen Brand ● Performance desktop and mobile computing ○ Athlon ○ Ryzen 3, Ryzen 5, Ryzen 7, Ryzen 9 ○ Ryzen Threadripper ● Server ○ EPYC https://en.wikichip.org/wiki/amd/microarchitectures/zen Zen History ● Aimed to replace two of AMD’s older chips ○ Excavator: high performance architecture ○ Puma: low power architecture https://en.wikichip.org/wiki/amd/microarchitectures/zen#Block_Diagram Zen Architecture ● Quad-core ● Fetch 4 instructions/cycle ● Op cache 2k instructions ● 168 physical integer registers ● 72 out of order loads ● Large shared L3 cache ● 2 threads per core https://www.slideshare.net/AMD/amd-epyc-microp rocessor-architecture Datapath Structure Fetch ● Decoupled branch predictor ○ Runs ahead of fetches ○ Successful predictions help latency and memory parallelism ○ Mispredictions incur power penalty ● 3 layer TLB ○ L0: 8 entries ○ L1: 64 entries ○ L2: 512 entries https://www.anandtech.com/show/10591/amd-zen-microarchiture-p art-2-extracting-instructionlevel-parallelism/3 Branch Predictor ● Perceptron: simple neural network ● Table of perceptrons, each a vector of weights ● Branch address used to access perceptron table ● Dot product between weight vector and branch history vector Perceptron Branch Predictor ● ~10% improve prediction rates over gshare predictor - (2, 2) correlating predictor ● Can utilize longer branch histories ○ Hardware requirements scale linearly whereas they scale exponentially for other predictors D. -

Optimizing for AMD Ryzen
AMD RYZEN™ CPU OPTIMIZATION Presented by Ken Mitchell & Elliot Kim AMD RYZEN™ CPU OPTIMIZATION ABSTRACT Join AMD ISV Game Engineering team members for an introduction to the AMD Ryzen™ CPU followed by advanced optimization topics. Learn about the “Zen” microarchitecture, power management, and CodeXL profiler. Gain insight into code optimization opportunities using hardware performance-monitoring counters. Examples may include assembly and C/C++. ‒ Ken Mitchell is a Senior Member of Technical Staff in the Radeon Technologies Group/AMD ISV Game Engineering team where he focuses on helping game developers utilize AMD CPU cores efficiently. Previously, he was tasked with automating & analyzing PC applications for performance projections of future AMD products. He studied computer science at the University of Texas at Austin. ‒ Elliot Kim is a Senior Member of Technical Staff in the Radeon Technologies Group/AMD ISV Game Engineering team where he focuses on helping game developers utilize AMD CPU cores efficiently. Previously, he worked as a game developer at Interactive Magic and has since gained extensive experience in 3D technology and simulations programming. He holds a BS in Electrical Engineering from Northeastern University in Boston. 3 | GDC17 AMD RYZEN CPU OPTIMIZATION | 2017-03-02 | AMD AGENDA Introduction ‒Microarchitecture ‒Power Management ‒Profiler Optimization ‒Compiler ‒Concurrency ‒Shader Compiler ‒Prefetch ‒Data Cache 4 | GDC17 AMD RYZEN CPU OPTIMIZATION | 2017-03-02 | AMD Introduction Microarchitecture “Zen” MICROARCHITECTURE AN UNPRECEDENTED IPC IMPROVEMENT Updated Feb 28, 2017: Generatinal IPCuplift for the “Zen” architecture vs. “Piledriver” architecture is +52% with an estimated SPECint_base2006 score compiled with GCC 4.6 –O2 at a fixed 3.4GHz. Generational IPC uplift for the “Zen” architecture vs. -

B450 Steel Legend.Pdf
Version 1.1 Published November 2020 Copyright©2020 ASRock INC. All rights reserved. Copyright Notice: No part of this documentation may be reproduced, transcribed, transmitted, or translated in any language, in any form or by any means, except duplication of documentation by the purchaser for backup purpose, without written consent of ASRock Inc. Products and corporate names appearing in this documentation may or may not be registered trademarks or copyrights of their respective companies, and are used only for identification or explanation and to the owners’ benefit, without intent to infringe. Disclaimer: Specifications and information contained in this documentation are furnished for informational use only and subject to change without notice, and should not be constructed as a commitment by ASRock. ASRock assumes no responsibility for any errors or omissions that may appear in this documentation. With respect to the contents of this documentation, ASRock does not provide warranty of any kind, either expressed or implied, including but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall ASRock, its directors, officers, employees, or agents be liable for any indirect, special, incidental, or consequential damages (including damages for loss of profits, loss of business, loss of data, interruption of business and the like), even if ASRock has been advised of the possibility of such damages arising from any defect or error in the documentation or product. This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. -

Cs433 Amd Zen 2
CS433 AMD ZEN 2 Hyoungwook Nam (hn5) Anjana Suresh Kumar (anjanas3) Vibhor Dodeja (vdodeja2) Namrata Mantri (nmantri2) Table of Contents 1. Overview 2. Pipeline Structure 3. Memory Hierarchy 4. Security and Power 5. Takeaways Overview History of AMD's x86 microarchitectures (1) K5 - K7 (95~02) K8 (03~08) K10 (09~11) x86 frontend, RISC backend Introduced x86-64 ISA Up to 6 cores Superscalar, OoO, speculation Dual-core (Athlon 64 X2) Shared L3 cache SIMD, L2 cache (K6) Integrated memory controller GPU integrated APUs (Fusion) https://www.tomshardware.com/picturestory/713-amd-cpu-history.html History of AMD's x86 microarchitectures (2) Bulldozer (11~16) Zen (17 ~ ) Multi-core module (MCM) Simultaneous Multi-thread (SMT) Two cores per module Two threads per core Shared FP and L2 in a module Higher single-thread performance AMD Financial Analyst Day, May 2015 Multi-core Module (MCM) Structure of Zen Single EPYC Package Single Die (Chiplet) Multiple dies in a package, 2 core complexes (ccx) per die, and up to 4 cores per ccx. (~4c8t per die) Fully connected NUMA between dies with infinity fabric (IF) which also interconnects ccx. https://www.slideshare.net/AMD/amd-epyc-microprocessor-architecture Zen 2 Changes Over Zen 1 and Zen+ Dedicated IO chiplet using hybrid process - TSMC 7nm CPU cores + GF 14nm IO chiplet 2x more cores per package - up to 16 for consumer and 64 for server More ILP - Better predictor, wider execution, deeper window, etc. 2x Larger L3 and faster IF2 Extra security features against spectre attacks https://www.pcgamesn.com/amd/amd-zen-2-release-date-specs-performance -
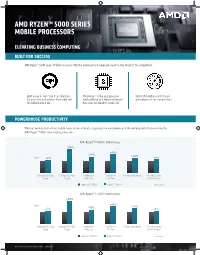
Amd Ryzentm 5000 Series Mobile Processors
AMD RYZENTM 5000 SERIES MOBILE PROCESSORS ELEVATING BUSINESS COMPUTING BUILT FOR SUCCESS AMD Ryzen™ 5000 Series Mobile Processors offer the advanced technology you need to stay ahead of the competition. Built on up to 7nm “Zen 3” architecture AMD Ryzen™ is the only processor Up to 90% higher multi-thread for processor performance leadership and family with up to 8 high performance performance vs the competition.2 incredible battery life. X86 cores for ultrathin notebooks.1 POWERHOUSE PRODUCTIVITY Whether working from office, huddle room, home or hotel, stay productive everywhere with the winning performance offered by AMD Ryzen™ 5000 series mobile processors. AMD RyzenTM 7 5800U Performance +90% +49% +30% +23% Up to +2% +9% .......................................................................................................................................................................................................... Cinebench R20 Single Cinebench R20 Multi- GeekBench v5 PassMark 10 PCMark 10 Benchmark MS Office Overall Thread Thread Multi-Core CPU Mark PCMark 10 Apps Intel Core i7-1165G7 RyzenTM 7 5800U See endnote 2 AMD RyzenTM 5 5600U Performance +90% +43% Up to +29% +5% +19% +8% .......................................................................................................................................................................................................... Cinebench R20 Single Cinebench R20 Multi- GeekBench v5 PassMark 10 PCMark 10 Benchmark MS Office Overall Thread Thread Multi-Core CPU Mark PCMark 10 Apps