Passmark Intel Vs AMD CPU Benchmarks - High End
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AMD's Llano Fusion
AMD’S “LLANO” FUSION APU Denis Foley, Maurice Steinman, Alex Branover, Greg Smaus, Antonio Asaro, Swamy Punyamurtula, Ljubisa Bajic Hot Chips 23, 19th August 2011 TODAY’S TOPICS . APU Architecture and floorplan . CPU Core Features . Graphics Features . Unified Video decoder Features . Display and I/O Capabilities . Power Gating . Turbo Core . Performance 2 | LLANO HOT CHIPS | August 19th, 2011 ARCHITECTURE AND FLOORPLAN A-SERIES ARCHITECTURE • Up to 4 Stars-32nm x86 Cores • 1MB L2 cache/core • Integrated Northbridge • 2 Chan of DDR3-1866 memory • 24 Lanes of PCIe® Gen2 • x4 UMI (Unified Media Interface) • x4 GPP (General Purpose Ports) • x16 Graphics expansion or display • 2 x4 Lanes dedicated display • 2 Head Display Controller • UVD (Unified Video Decoder) • 400 AMD Radeon™ Compute Units • GMC (Graphics Memory Controller) • FCL (Fusion Control Link) • RMB (AMD Radeon™ Memory Bus) • 227mm2, 32nm SOI • 1.45BN transistors 4 | LLANO HOT CHIPS | August 19th, 2011 INTERNAL BUS . Fusion Control Link (FCL) – 128b (each direction) path for IO access to memory – Variable clock based on throughput (LCLK) – GPU access to coherent memory space – CPU access to dedicated GPU framebuffer . AMD Radeon™ Memory Bus (RMB) – 256b (each direction) for each channel for GMC access to memory – Runs on Northbridge clock (NCLK) – Provides full bandwidth path for Graphics access to system memory – DRAM friendly stream of reads and write – Bypasses coherency mechanism 5 | LLANO HOT CHIPS | August 19th, 2011 Dual-channel DDR3 Unified Video DDR3 UVD Decoder NB CPU CPU Graphics SIMD Integrated Integrated GPU, Display Northbridge Array Controller I/O Controllers L2 Display L2 I/OMultimedia Controllers L2 PCI Express I/O - 24 lanes, optional 1 MB L2 cache L2 I/O per core digital display interfaces CPU CPU Digital display interfaces 4 Stars-32nm PCIe CPU cores PPL Display PCIe PCIe Display 6 | LLANO HOT CHIPS | August 19th, 2011 CPU, GPU, UVD AND IO FEATURES STARS-32nm CPU CORE FEATURES . -

Motherboard Gigabyte Ga-A75n-Usb3
Socket AM3+ - AMD 990FX - GA-990FXA-UD5 (rev. 1.x) Socket AM3+ Pagina 1/3 GA- Model 990FXA- Motherboard UD5 PCB 1.x Since L2 L3Core System vendor CPU Model Frequency Process Stepping Wattage BIOS Name Cache Cache Bus(MT/s) Version AMD FX-8150 3600MHz 1MBx8 8MB Bulldozer 32nm B2 125W 5200 F5 AMD FX-8120 3100MHz 1MBx8 8MB Bulldozer 32nm B2 125W 5200 F5 AMD FX-8120 3100MHz 1MBx8 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-8100 2800MHz 1MBx8 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-6100 3300MHz 1MBx6 8MB Bulldozer 32nm B2 95W 5200 F5 AMD FX-4100 3600MHz 1MBx4 8MB Bulldozer 32nm B2 95W 5200 F5 Socket AM3 GA- Model 990FXA- Motherboard UD5 PCB 1.x Since L2 L3Core System vendor CPU Model Frequency Process Stepping Wattage BIOS Name Cache Cache Bus(MT/s) Version AMD Phenom II X6 1100T 3300MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1090T 3200MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1075T 3000MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1065T 2900MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1055T 2800MHz 512KBx6 6MB Thuban 45nm E0 125W 4000 F2 AMD Phenom II X6 1055T 2800MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1045T 2700MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X6 1035T 2600MHz 512KBx6 6MB Thuban 45nm E0 95W 4000 F2 AMD Phenom II X4 980 3700MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F6 AMD Phenom II X4 975 3600MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F2 AMD Phenom II X4 970 3500MHz 512KBx4 6MB Deneb 45nm C3 125W 4000 F2 AMD Phenom II X4 965 3400MHz 512KBx4 -
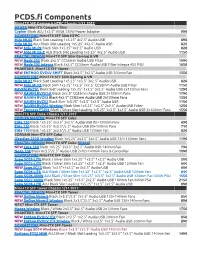
Components © 2017
PCDS.fi Components Mini-ITX SFF Gaming & HTPC Chassis 1/11 2017 AKASA Mini-ITX Compact Thin Cypher Black ALU 1x2.5” VESA 120W Power Adapter 99€ S ILVERSTONE Mini-ITX SFF Slim HTPC Milo ML0 5 Black Slot Loading 1x5.25” 4x2.5” Audio USB 69€ Milo ML0 6 ALU Black Slot Loading 1x5.25” 4x2.5” Audio USB 82€ NEW Milo ML0 9 Black Slim 1x5.25” 4x2.5” Audio USB 82€ NEW Milo ML0 6-E ALU Black Slot Loading 1x5.25” 4x2.5” Audio USB 115€ FRACTAL DESIGN Mini-ITX SFF Slim Gaming & VR NEW Node 202 Black 2x2.5” CC56mm Audio USB Filter 109€ NEW Node 20 2 Integra Black 2x2.5” CC56mm Audio USB Filter Integra 450 PSU 165€ PHANTEKS Mini-ITX SFF Tower NEW ENTHOO EVOLV SHIFT Black 2x3.5” 1x2.5” Audio USB 200mm Fan 135€ S ILVERSTONE Mini-ITX SFF Slim Gaming & VR Milo ML0 7 Black Slot Loading 1x5.25” 1x3.5” 3x2.5” Audio USB 82€ NEW Milo ML0 8 Black Slim 1x5.25” 1x3.5” 2x2.5” CC58mm Audio USB Filter 115€ R AVEN RVZ01 Black Slot Loading 1x5.25” 1x3.5” 3x2.5” Audio USB 2x120mm Fans 129€ NEW R AVEN RVZ01- E Black 3x2.5” CC83mm Audio USB 2x120mm Fans 129€ NEW RAVEN RVZ03 Black 4x2.5” CC83mm Audio USB 2x120mm Fans 135€ NEW R AVEN RVZ0 2 Black Slim 1x5.25” 1x3.5” 2x2.5” Audio USB 115€ NEW R AVEN RVZ0 2 Window Black Slim 1x5.25” 1x3.5” 2x2.5” Audio USB Filter 125€ NEW Fortress FTZ 01 Black / Silver Slot Loading 1x5.25” 1x3.5” 3x2.5” Audio USB 3x120mm Fans 155€ Mini-ITX SFF Cube Chassis 1/11 2017 COOLER MASTER Mini-ITX SFF Cube Elite 1 3 0 Black 1x5.25” 2x3.5” 3x2.5” Audio USB 80+120mm Fans 69€ Elite 1 2 0 Black 1x5.25” 3x3.5”/2.5” Audio USB 80+120mm Fans 71€ Elite 110 Black -

Multiprocessing Contents
Multiprocessing Contents 1 Multiprocessing 1 1.1 Pre-history .............................................. 1 1.2 Key topics ............................................... 1 1.2.1 Processor symmetry ...................................... 1 1.2.2 Instruction and data streams ................................. 1 1.2.3 Processor coupling ...................................... 2 1.2.4 Multiprocessor Communication Architecture ......................... 2 1.3 Flynn’s taxonomy ........................................... 2 1.3.1 SISD multiprocessing ..................................... 2 1.3.2 SIMD multiprocessing .................................... 2 1.3.3 MISD multiprocessing .................................... 3 1.3.4 MIMD multiprocessing .................................... 3 1.4 See also ................................................ 3 1.5 References ............................................... 3 2 Computer multitasking 5 2.1 Multiprogramming .......................................... 5 2.2 Cooperative multitasking ....................................... 6 2.3 Preemptive multitasking ....................................... 6 2.4 Real time ............................................... 7 2.5 Multithreading ............................................ 7 2.6 Memory protection .......................................... 7 2.7 Memory swapping .......................................... 7 2.8 Programming ............................................. 7 2.9 See also ................................................ 8 2.10 References ............................................. -

I Processori Amd Trinity
UNIVERSITA’ DEGLI STUDI DI PADOVA __________________________________________________ Facoltà di Ingegneria Corso di laurea in Ingegneria Informatica I PROCESSORI AMD TRINITY Laureando Relatore Luca Marzaro Prof. Sergio Congiu ___________________________________________________________ ANNO ACCADEMICO 2012/2013 ii iii A Giulia, mamma, papà e Diego iv Indice 1. Introduzione 1 1.1 Cenni storici AMD . 1 1.2 Evoluzione del processore: dall' Am386 alle APU Trinity . 2 2. Trinity: Architettura 5 2.1 Introduzione . 5 2.2 Da Llano a Trinity: architettura Piledriver . 6 2.3 Graphics Memory Controller: architettura VLIW4 . 8 2.4 Un nuovo socket: FM2 . 12 3. Specifiche tecniche 15 3.1 Modelli e dati tecnici . 15 3.2 Comparazione con Llano e Intel core i3 . 17 4. Prestazioni 19 4.1 Introduzione . 19 4.2 Applicazioni multimediali . 22 4.3 Calcolo e compressione . 25 4.4 Consumi . 30 5. Considerazioni finali 35 vi INDICE Bibliografia 37 Capitolo 1 Introduzione 1.1 Cenni storici AMD AMD (Advanced Micro Devices) è una multinazionale americana produttrice di semiconduttori la cui sede si trova a Sunnyvale in California. La peculiarità di tale azienda è la produzione di microprocessori, workstation e server, di chip grafici e di chipset. Si classifica seconda al mondo Figura 1.1: Jerry Sanders nella produzione di microprocessori con architettuta x86 dopo Intel. Il primo maggio 1969 Jerry Sanders (vedi Figura 1.1) e sette amici fondano la AMD. Sei anni più tardi, lanciano nel mercato la prima memoria RAM marchiata AMD, la Am9102 e presentano AMD 8080, una variante dell'INTEL 8080 che lancia l'azienda nel mondo dei microprocessori. Dal 1980 AMD si impone come uno dei principali concorrenti di Intel nel mercato dei processori x86- compatibili. -

TA790GXB3 Motherboard TA790GXB3 Specifcation
TA790GXB3 Motherboard • Supported Socket AM3 processors AMD Phenom II X4 / Phenom II X3 / Athlon II processor • AMD 125W processor support • AMD 790GX Chipset with ATI Radeon HD 3300 Graphics • Dual-Channel DDR3 -1600(OC)/1333/1066/800 • ATI Hybrid Graphics Support • Integrated DVI interface with HDCP Support 1080P HD Video Experience • AMD OverDrive Utility Support • Optional DVI to HDMI adapter • AMD OverDrive™ with ACC feature (Advanced Clock Calibration) supported TA790GXB3 Specifcation CPU SUPPORT AMD Phenom™ II X4 Processor AMD Phenom™ II X3 Processor AMD Phenom™ II X2 Processor AMD Athlon™ II X4 Processor AMD Athlon™ II X3 Processor AMD Athlon™ II X2 Processor Maximum CPU TDP (Thermal Design Power) : 125Watt HT BIOSTARSupport HT 5.2G MEMORY Support Dual Channel DDR3 800/1066/1333/1600(OC) MHz 4 x DDR3 DIMM Memory Slot Max. Supports up to 16GB Memory INTEGRATED VIDEO ATI Radeon™ HD3300 Graphics , Max. Memory Share Up to 512 MB Support ATI Hybrid Crossfire STORAGE 6 x SATA II Connector 1 x IDE Connector Support SATA RAID: 0,1,5,10 LAN Realtek RTL8111DL - 10/100/1000 Controller AUDIO CODEC Realtek ALC662 6-Channel HD Audio USB 4 x USB 2.0 Port 3 x USB 2.0 Header EXPANSION SLOT 1 x PCI-E 2.0 x16 Slot 2 x PCI-E 2.0 x1 Slot 3 x PCI Slot REAR I/O 1 x PS/2 Mouse 1 x PS/2 Keyboard 4 x USB 2.0 Port 1 x DVI Connector 1 x VGA Port 1 x LAN Port 3 x Audio Jacks INTERNAL I/O 3 x USB 2.0 Header 6 x SATA II Connector (3Gb/s ) 1 x IDE Connector 1 x Floppy Connector 1 x Front Audio Header 1 x Front Panel Header 1 x CD-IN Header 1 x S/PDIF-Out Header -

AMD's Early Processor Lines, up to the Hammer Family (Families K8
AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) Dezső Sima October 2018 (Ver. 1.1) Sima Dezső, 2018 AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) • 1. Introduction to AMD’s processor families • 2. AMD’s 32-bit x86 families • 3. Migration of 32-bit ISAs and microarchitectures to 64-bit • 4. Overview of AMD’s K8 – K10.5 (Hammer-based) families • 5. The K8 (Hammer) family • 6. The K10 Barcelona family • 7. The K10.5 Shanghai family • 8. The K10.5 Istambul family • 9. The K10.5-based Magny-Course/Lisbon family • 10. References 1. Introduction to AMD’s processor families 1. Introduction to AMD’s processor families (1) 1. Introduction to AMD’s processor families AMD’s early x86 processor history [1] AMD’s own processors Second sourced processors 1. Introduction to AMD’s processor families (2) Evolution of AMD’s early processors [2] 1. Introduction to AMD’s processor families (3) Historical remarks 1) Beyond x86 processors AMD also designed and marketed two embedded processor families; • the 2900 family of bipolar, 4-bit slice microprocessors (1975-?) used in a number of processors, such as particular DEC 11 family models, and • the 29000 family (29K family) of CMOS, 32-bit embedded microcontrollers (1987-95). In late 1995 AMD cancelled their 29K family development and transferred the related design team to the firm’s K5 effort, in order to focus on x86 processors [3]. 2) Initially, AMD designed the Am386/486 processors that were clones of Intel’s processors. -
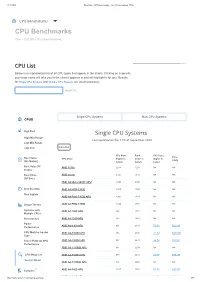
CPU Benchmarks - List of Benchmarked Cpus
11.09.2020 PassMark - CPU Benchmarks - List of Benchmarked CPUs CPU Benchmarks CPU Benchmarks Over 1,000,000 CPUs Benchmarked CPU List Below is an alphabetical list of all CPU types that appear in the charts. Clicking on a specific processor name will take you to the chart it appears in and will highlight it for you. Results for Single CPU Systems and Multiple CPU Systems are listed separately. Find CPU Single CPU Systems Multi CPU Systems CPUS High End Single CPU Systems High Mid Range Last updated on the 11th of September 2020 Low Mid Range Low End Column CPU Mark Rank CPU Value Price Best Value CPU Name (higher is (lower is (higher is (USD) (On Market) better) better) better) Best Value XY AMD 3015e 2,678 1285 NA NA Scatter Best Value AMD 3020e 2,721 1272 NA NA (All time) AMD A4 Micro-6400T APU 1,004 2126 NA NA New Desktop AMD A4 PRO-3340B 1,519 1790 NA NA New Laptop AMD A4 PRO-7300B APU 1,421 1839 NA NA Single Thread AMD A4 PRO-7350B 1,024 2108 NA NA Systems with AMD A4-1200 APU 445 2572 NA NA Multiple CPUs Overclocked AMD A4-1250 APU 432 2583 NA NA Power AMD A4-3300 APU 994 2131 76.50 $12.99 Performance CPU Mark by Socket AMD A4-3300M APU 665 2394 22.19 $29.99* Type Cross-Platform CPU AMD A4-3305M APU 807 2273 38.78 $20.81 Performance AMD A4-3310MX APU 844 2239 NA NA CPU Mega List AMD A4-3320M APU 877 2212 23.77 $36.90 Search Model AMD A4-3330MX APU 816 2265 NA NA 0 1,067 2078 Compare AMD A4-3400 APU 53.35 $20.00 https://www.cpubenchmark.net/cpu_list.php AMD A4 3420 APU 8 01 $12 9 * 1/87 11.09.2020 PassMark - CPU Benchmarks - List -

Take a Way: Exploring the Security Implications of AMD's Cache Way
Take A Way: Exploring the Security Implications of AMD’s Cache Way Predictors Moritz Lipp Vedad Hadžić Michael Schwarz Graz University of Technology Graz University of Technology Graz University of Technology Arthur Perais Clémentine Maurice Daniel Gruss Unaffiliated Univ Rennes, CNRS, IRISA Graz University of Technology ABSTRACT 1 INTRODUCTION To optimize the energy consumption and performance of their With caches, out-of-order execution, speculative execution, or si- CPUs, AMD introduced a way predictor for the L1-data (L1D) cache multaneous multithreading (SMT), modern processors are equipped to predict in which cache way a certain address is located. Conse- with numerous features optimizing the system’s throughput and quently, only this way is accessed, significantly reducing the power power consumption. Despite their performance benefits, these op- consumption of the processor. timizations are often not designed with a central focus on security In this paper, we are the first to exploit the cache way predic- properties. Hence, microarchitectural attacks have exploited these tor. We reverse-engineered AMD’s L1D cache way predictor in optimizations to undermine the system’s security. microarchitectures from 2011 to 2019, resulting in two new attack Cache attacks on cryptographic algorithms were the first mi- techniques. With Collide+Probe, an attacker can monitor a vic- croarchitectural attacks [12, 42, 59]. Osvik et al. [58] showed that tim’s memory accesses without knowledge of physical addresses an attacker can observe the cache state at the granularity of a cache or shared memory when time-sharing a logical core. With Load+ set using Prime+Probe. Yarom et al. [82] proposed Flush+Reload, Reload, we exploit the way predictor to obtain highly-accurate a technique that can observe victim activity at a cache-line granu- memory-access traces of victims on the same physical core. -

Beyond the Ordinary
Beyond the ordinary HP Recommends Windows® 7. HP Compaq 6005 Pro Business PC Designed to Packed with high performance features, Easy to deploy and manage the HP Compaq 6005 Pro Business PC is Streamline business processes while deliver energy efficient and well equipped to go lowering IT costs and operating uncompromised beyond meeting your daily business expenses with DASH and other demands. Enabled for manageability with manageability features that allow for results with energy DASH 1.1, you can also choose the more efficient planning, deployment, efficiency features productivity and security features that best and transition of your PCs. You get suit your everyday needs with a PC access to a suite of client management and high-end designed to exceed your expectations. tools, 12+ month product lifecycle, and global SKUs to meet your world-wide capabilities Designed to deliver needs. Enhance your capabilities with the latest AMD Business Class technology: Simplified serviceability comes in the processors and chipset that provide form of tool-less hood removal, drive exceptional performance while operating bays and slots as well as internal quick as efficiently as possible. Integrated ATI release latches, green pull tabs, and Radeon 4200 graphics with ATI Avivo™ color coordinated cables and and DirectX 10.1 provide a stunning connectors. visual experience. Dual monitor capability Security that’s right for you also comes standard for easier mutli- Help your investments be more secure tasking. with the embedded TPM 1.2 security chip Use less, save more that helps provide enhanced data Improve your bottom line with energy protection and limits system access efficient features like an optional 89% through hardware-based encryption. -

Comparatif Des Processeurs
Comparatif des processeurs Le microprocesseur (ou processeur) est un composant essentiel de votre ordinateur. Pourtant sur les étiquettes, cet élément est rarement mis en avant, car commercialement ce n'est pas toujours vendeur, les gens font plus attention à la capacité du disque dur, au look de l'ordinateur, ou éventuellement à la puce vidéo. Alors attention quand même, le processeur ne fait pas tout. De la même façon qu'on ne choisit pas une voiture uniquement en fonction du moteur, on ne choisit pas non plus un ordinateur uniquement en fonction du processeur, mais c'est un élément qu'il faut savoir évaluer, au risque de se retrouver avec un ordinateur que vous trouverez toujours trop lent alors qu'il avait l'air très performant en rayon ;) Ce tableau vous aidera à évaluer une grande partie des processeurs existants. La liste des processeurs est triée par ordre alphabétique, et la colonne de droite indique le « score » du processeur. Le score à lui tout seul ne veut rien dire, mais c'est lui qui vous permettra de comparer un processeur par rapport à un autre. Plus le score est élevé, mieux c'est ! Le modèle de microprocesseur est affiché dans les propriétés système et sur l'étiquette en rayon Notez bien sa référence, une seule lettre peut tout changer ! Marque et modèle du processeur Score AMD A10 Micro-6700T APU 1875 AMD A10 PRO-7350B APU 3354 AMD A10 PRO-7800B APU 5313 AMD A10 PRO-7850B APU 5630 AMD A10-4600M APU 3121 AMD A10-4655M APU 2566 AMD A10-4657M APU 3449 AMD A10-5700 APU 4220 AMD A10-5745M APU 2788 AMD A10-5750M APU 3377 -
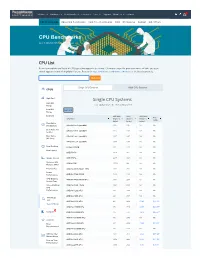
CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android Ios / Iphone
Software Hardware Benchmarks Services Store Support About Us Forums 0 CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone CPU Benchmarks Over 1,000,000 CPUs Benchmarked CPU List Below is an alphabetical list of all CPU types that appear in the charts. Clicking on a specific processor name will take you to the chart it appears in and will highlight it for you. Results for Single CPU Systems and Multiple CPU Systems are listed separately. Find CPU Single CPU Systems Multi CPU Systems CPUS High End Single CPU Systems High Mid Range Last updated on the 28th of May 2021 Low Mid Column Range Low End CPU Mark Rank CPU Value Price CPU Name (higher is (lower is (higher is (USD) better) better) better) Best Value (On Market) AArch64 rev 0 (aarch64) 2,335 1605 NA NA Best Value XY AArch64 rev 1 (aarch64) 2,325 1606 NA NA Scatter Best Value AArch64 rev 2 (aarch64) 1,937 1807 NA NA (All time) AArch64 rev 4 (aarch64) 1,676 1968 NA NA New Desktop AC8257V/WAB 693 2730 NA NA New Laptop AMD 3015e 2,678 1472 NA NA Single Thread AMD 3020e 2,637 1481 NA NA Systems with AMD 4700S 17,756 222 NA NA Multiple CPUs Overclocked AMD A4 Micro-6400T APU 1,004 2445 NA NA Power Performance AMD A4 PRO-3340B 1,706 1938 NA NA CPU Mark by AMD A4 PRO-7300B APU 1,481 2097 NA NA Socket Type Cross-Platform AMD A4 PRO-7350B 1,024 2428 NA NA CPU Performance AMD A4-1200 APU 445 2969 NA NA AMD A4-1250 APU 428 2987 NA NA CPU Mega List AMD A4-3300 APU 961 2494 53.40 $18.00* Search Model AMD A4-3300M APU 686 2740 22.86 $29.99* 0 Compare AMD