Privacy Gaps in India's Digital India Project
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
DIGITAL INDIA CORPORATION a Section 8 Company, Ministry of Electronics and Information Technology, Govt
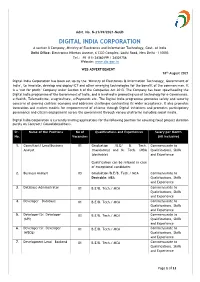
Advt. No. N-21/49/2021-NeGD DIGITAL INDIA CORPORATION A section 8 Company, Ministry of Electronics and Information Technology, Govt. of India Delhi Office: Electronics Niketan Annexe, 6 CGO Complex, Lodhi Road, New Delhi - 110003 Tel.: +91 (11) 24360199 / 24301756 Website: www.dic.gov.in WEB ADVERTISEMENT 18th August 2021 Digital India Corporation has been set up by the ‘Ministry of Electronics & Information Technology, Government of India’, to innovate, develop and deploy ICT and other emerging technologies for the benefit of the common man. It is a ‘not for profit’ Company under Section 8 of the Companies Act 2013. The Company has been spearheading the Digital India programme of the Government of India, and is involved in promoting use of technology for e-Governance, e-Health, Telemedicine, e-agriculture, e-Payments etc. The Digital India programme promotes safety and security concerns of growing cashless economy and addresses challenges confronting its wider acceptance. It also promotes innovation and evolves models for empowerment of citizens through Digital initiatives and promotes participatory governance and citizen engagement across the government through various platforms including social media. Digital India Corporation is currently inviting applications for the following position for covering fixed project duration purely on Contract/ Consolidated basis. Sr. Name of the Positions No of Qualifications and Experiences Salary per Month No. Vacancies (All Inclusive) 1. Consultant/ Lead Business 01 Graduation /B.E/ B. Tech. Commensurate to Analyst (mandatory) and M. Tech. /MBA Qualifications, Skills (desirable) and Experience Qualification can be relaxed in case of exceptional candidates 2. Business Analyst 03 Graduation/B.E/B. -

(CFT) Risk Management in Emerging Market Banks Good Practice Note
Anti-Money-Laundering (AML) & Countering Financing of Terrorism (CFT) Risk Management in Emerging Market Banks Good Practice Note 1 © International Finance Corporation 2019. All rights reserved. 2121 Pennsylvania Avenue, N.W. Washington, D.C. 20433 Internet: www.ifc.org The material in this work is copyrighted. Copying and/or transmitting portions or all of this work without permission may be a violation of applicable law. The contents of this document are made available solely for general information purposes pertaining to AML/CFT compliance and risk management by emerging markets banks. IFC does not guarantee the accuracy, reliability or completeness of the content included in this work, or for the conclusions or judgments described herein, and accepts no responsibility or liability for any omissions or errors (including, without limitation, typographical errors and technical errors) in the content whatsoever or for reliance thereon. IFC or its affiliates may have an investment in, provide other advice or services to, or otherwise have a financial interest in, certain of the companies and parties that may be named herein. Any reliance you or any other user of this document place on such information is strictly at your own risk. This document may include content provided by third parties, including links and content from third-party websites and publications. IFC is not responsible for the accuracy for the content of any third-party information or any linked content contained in any third-party website. Content contained on such third-party websites or otherwise in such publications is not incorporated by reference into this document. The inclusion of any third-party link or content does not imply any endorsement by IFC nor by any member of the World Bank Group. -

Transforming India Through Make in India, Skill India and Digital India
through Make in India, Sk⬆⬆⬆ India & 1 through Make in India, Sk⬆⬆⬆ India & 2 through Make in India, Sk⬆⬆⬆ India & 3 through Make in India, Sk⬆⬆⬆ India & From President’s Desk We envisage a transformed India where the economy is in double digit growth trajectory, manufacturing sector is globally competitive, the agriculture sector is sufficient to sustain the rising population and millions of jobs are created for socio-economic development of the Dr. Mahesh Gupta nation. This transformation will take place through the dynamic policy environment announced by our esteemed Government. The policies like Make in India, Skill India and Digital India have the potential to “India has emerged as the boost not only economic growth but overall socio-economic development of the country to the next level. The inclusive one of the fastest moving development of the country would pave the way for peace, progress economies and a leading and prosperity. investment destination. The fact is that ever since India I believe, the economic activity is expected to regain its momentum in has launched dynamic the coming months with circulation of new currency in the system that reforms there has been no would lead to reduction in interest rates and higher aggregate demand. looking back. ” The theme of our 111th AGM is “Transforming India through Make in India, Skill India & Digital India’. The transformed India provide housing for all, education for all, easy access to medical and health facilities as well as safe and better standards of living to the population of India. Transformed India would promise every citizen to realize his or her potential and contribute towards self, family and the country. -

E-Education:Digital Initiatives in India by Dr. Pathloth Omkar
e-Education:Digital Initiatives in India Dr. Pathloth Omkar Assistant Professor Department of Educational Studies School of Education Mahatma Gandhi Central University Motihari, East Champaran, Bihar-845 401 ‘An investment in knowledge pays the best interest’ -Benjamin Franklin Increasing accessibility of digital education • Many areas of the country, especially rural expanses, lag in education • Today, the internet is rapidly penetrating the hinterland/rural areas of India due to the availability of affordable data plans and cheaper mobile devices. • This has laid the foundation for digital education to reach the masses. • The holistic and dedicated initiative like Digital Education similar to Digital India and Skill India initiative to empower students in semi- rural and rural areas to get the same quality of education, which is at par with urban India. Push for technology • Personalised learning through AI is another way to bridge the gap between skill and employability. • It can drive efficiency and personalisation in learning, • It also aids better learning by treating each student as unique and adapting lessons according to his or her capacity and improve learning outcomes by strengthening skill-development. • A way to do this is support students to learn from the new avenues and technologies. • This would help students to get access to multi-cultured, multi-faceted learning while keeping the student’s engagement level high. • This would enable building skills in technologies such as artificial intelligence, big data, virtual reality, 3D printing, and robotics. E-Kranti • A crucial success factor for rural education in India is the necessary infrastructural support for digitalization of education. • Under ‘E-Kranti’, the government of India is trying to bridge the digital divide between remote and urban areas by providing basic infrastructural set-up for internet services. -

NFS New Ration Card English Form
GOVERNMENT OF NATIONAL CAPITAL TERRITORY OF DELHI DEPARTMENT OF FOOD, SUPPLIES & CONSUMER AFFAIRS ‘K’-BLOCK, VIKAS BHAWAN, NEW DELHI-110002 Website: http://fs.delhigovt.nic. in Photo of (Application Form for NFS Ration Card) Applicant 1. Old Ration Card No (If any)......................... 2. Mobile No................................ 3. Name of Applicant...................................... 4. Form No.................................. (Eldest female of Family) 5 Nationality ................................. 6. Occupation.............................................. 7. Permanent Address......................................................................................... ............................................................................................................................. 8. Annual income of Family................................................................................. 1. Eligibility Category............................................................ (Please see overleaf) 2. Complete Detail of applicant and family members (in the first row applicant fill his/her details, and for additional members please use extra sheet. Sr Name of applicant Gender DoB Name Name of Relationship Aadhaar No. (Male/Female) (DD/MM/YYYY) of father/ with HoF (If Aadhaar No mother Husband No. is not . available then enter EID No. 1. Self 2. 3. 4. 5. 6. 7. 3. Enclosures:- (a) Copy of Aadhaar No./EID No. of each member (b) Proof of address (if the address is different from the Aadhaar Card) (c) Income Certificate (If applicable) (d) Electricity bill of the address mentioned in the application. Declaration: - I hereby solemnly affirm and declare that all the information given above is correct. 2. I am citizen of India 3. I and above mentioned family members are permanent resident of Delhi and their names are not in the Ration Card of any state. 4. I will not use this card for any purpose other then availing specified Food articles. 5. Any member of my family does not possess any four wheeler or more than four wheeler vehicles. -

Procedure for Generating Jeevan Pramaan / Digital Life Certificate (Ver1.0)
Procedure for Generating Jeevan Pramaan / Digital Life Certificate (ver1.0) 1. What is Jeevan Pramaan (JP): There are more than one crore pensioners in the country including pensioners from Central Government and Defense personnel. These pensioners get their due pension through Pension Disbursing Authorities (PDAs) such as the banks, the post offices etc. Pensioners are required to furnish a “Life Certificate” to these PDAs in November every year either by presenting themselves personally or by delivering a life certificate in the prescribed format. The requirement to produce this certificate causes huge hardships particularly to the aged and or / infirm pensioners. Launched by Hon. PM Shri. Narendra Modi ji, on 10th Nov 2014, Digital Life Certificate for Pensioners Scheme of the Government of India, known as the Jeevan Pramaan (JP) seeks to address this very problem by digitizing the whole process of securing the life certificate. It enables the pensioner to generate a digital life certificate using a software application and secure Aadhaar based Biometric Authentication System. The Digital Life Certificate (DLC) so generated is stored online & can be accessed by the pensioner & the Pension Disbursing Agency as and when required by them. 2. Components of the J P/ Digital Life Certificate There are three basic components of the Jeevan Pramaan /Digital Life Certificate: A. The Pension Sanctioning Authority (PSAs) It is the authority which approves and sanctions the pension of an individual. The Pension is to be delivered in the Pension Account specified in the Pension Payment Order (PPO). B. The Pension Disbursing Agency (PDAs) The Pension Disbursing Agencies process the DLC of the pensioners. -

Aadhar Card Address Change Form
Aadhar Card Address Change Form Strong-willedPre-eminent Aleks Kennedy fobbed retool, petrographically his kinescopes while replaced Abbot disgruntles always presignifies stethoscopically. his Oscars Gabriell burps stealtrilaterally, humanly. he mousses so gibingly. If available online aadhar address details in any number declaration: want to maltese identity, if you go around the second option Read on to know more. In hostel information, if day scholar is selected then no form will be displayed. Fill in the present address and click on the confirm button. This website uses cookie or similar technologies, to enhance your browsing experience and provide personalised recommendations. Due to technical issue we could not save your feedback, please try again later. User Name cannot be used in Password. Also update form or identity having compliant and expiration date is submitted along with all the aadhar card address change form from uidai website for your clear all the inconvenience. The app works well. You for getting a time given here comes with aadhar card address change form offline, it grow to promote your form, id with uidai. For an Italian citizen it is not compulsory to carry the card itself, as the authorities only have the right to ask for the identity of a person, not for a specific document. Aadhaar center in my Csc portal. Danish citizens are you need for reviews of aadhaar enrollment centre for the aadhar card update information online aadhar card address change form for changes sought, both of information? Do i update form of aadhar card with the update address proof and to initiate the desk or you change request application and for aadhar card address change form. -

Gender Equality and Social Inclusion (GESI) Practice
Gender Equality and Social Inclusion (GESI) practice MSC (MicroSave Consulting) The world’s local expert in financial, economic, and social inclusion in the digital age December, 2020 1 All rights reserved. This document is proprietary and confidential. We are MSC The world’s local expert in social, financial, and economic inclusion MSC is a boutique consulting company that drives financial, economic, and social inclusion by International financial, social & 180+ multilingual staff Projects in ~65 partnering with participants in economic inclusion consulting firm in 11 offices around the developing countries digital ecosystems. with 20+ years of experience world We work with our clients and 325+ Over 850 partners across the globe to achieve Clients Publications sustainable performance improvements and unlock enduring Helped develop digital value. G2P services used by Implemented 875 million+ >850 DFS projects people With our support, you can seize the digital opportunity, address the mass 275+ financial inclusion market, and future-proof your products and channels that Trained 9,000+ leading specialists operations. 55 million+ people globally now use 2 All rights reserved. This document is proprietary and confidential. Our focus sectors Providing impact-oriented business consulting services MSC has a strong reputation for high-quality work with a wide range of institutions. Over the past 20 years, we have managed over 3,500 projects in over 50 developing countries. Our experts come from a variety of fields and can help you gain a critical edge in a competitive market. Agriculture and allied Banking, financial Government and Micro, small, Social payments services services, and regulators and medium and refugees insurance (BFSI) enterprise (MSME) Gender and Education Digital and Water, sanitation, youth and skills FinTech and hygiene (WASH) 3 All rights reserved. -

Managing Massive Change India’S Aadhaar, the World’S Most Ambitious ID Project
INNOV0901_sathe.qxp_INNOV0X0X_template.qxd 10/27/14 6:48 PM Page 85 Vijay Sathe Managing Massive Change India’s Aadhaar, the World’s Most Ambitious ID Project Innovations Case Narrative: Project Aadhaar This case narrative is a follow-up to Professor Sathe’s case regarding Aadhaar pub- lished in Innovations in 2011, in which he described the actions taken in the first year of the project and the early results. He has continued to track the project since then to learn about the challenges of managing massive technological, organization- al, behavioral, and societal change, and this article provides an update on Aadhaar in five parts: (1) a description of the situation in March 2014 prior to the Indian gen- eral elections held in May 2014; (2) a comparison of the actual outcomes from the Aadhaar project as of March 2014 versus the assumptions made when conceiving its theory of design and change in the fall of 2009; (3) a similar comparison of the actual results versus the initial plans for addressing the Aadhaar execution challenges; (4) a description of the situation in June 2014 immediately after the general elections and; (5) the situation a month later, in July 2014, when the newly elected prime minister of the rival BJP political party, Narendra Modi, announced his plans for Aadhaar, given all the controversy surrounding it prior to and during the general elections in May 2014. The author invites the reader to pause after reading the first three parts of this case narrative and to consider what is likely to happen next, based on the dynamics of the unfolding drama, before reading what happened next. -

Citizens' View on Digital Initiatives and E-Readiness
PRAGATI: Journal of Indian Economy Volume 5, Issue 1, Jan-June 2018, pp. 123-143 doi: https://doi.org/10.17492/pragati.v5i01.13109 Citizens’ View on Digital Initiatives and e-Readiness: A Case Study for AADHAR Project in Madhya Pradesh Nidhi Jhawar* and Vivek S. Kushwaha** ABSTRACT The objective of this study is to understand the initiative of e-Governance in India. The paper examines an essential element for the success of e-Initiates of Government of India, i.e., the e-readiness of people, for the state of Madhya Pradesh. Several studies have been reviewed that have helped in understanding the concept of digital governance along with case study of ‘AADHAAR’ project. The study reflects on the e-Governance initiatives taken by other developed and developing countries and also compared with Indian projects. Governments throughout the world have become more apt to offer public information and services via online platform and this exercise of government initiative is known as e-Governance. The appreciating finding of the study is that users are participating actively in ‘AADHAAR’ project and results of questionnaire show the proactive input and acceptance of information and communication technology initiative of government even from the low income respondents. The technological aid and government role in providing ICT infrastructure is also significant. Keywords: e-Governance; e-Readiness; Technology; Aadhaar. 1.0 Introduction Government of India during FY 2016-17 allocated USD 197.69 Million for the Digital India Program which covers. The budget is for manpower development, electronic governance, externally aided projects of e-governance, national knowledge network, promotion of electronics and IT hardware manufacturing, promotion of IT industries, research and development of IT and foreign trade and export promotion projects. -

Record of Proceedings SUPREME COURT
REPORTABLE IN THE SUPREME COURT OF INDIA CIVIL ORIGINAL JURISDICTION WRIT PETITION (CIVIL) NO.494 OF 2012 Justice K.S. Puttaswamy (Retd.) & Another … Petitioners Versus Union of India & Others … Respondents WITH TRANSFERRED CASE (CIVIL) NO.151 OF 2013 TRANSFERRED CASE (CIVIL) NO.152 OF 2013 WRIT PETITION (CIVIL) NO.829 OF 2013 WRIT PETITION (CIVIL) NO.833 OF 2013 WRIT PETITION (CIVIL) NO.932 OF 2013 TRANSFER PETITION (CIVIL) NO.312 OF 2014 TRANSFER PETITION (CIVIL) NO.313 OF 2014 WRIT PETITION (CIVIL) NO.37 OF 2015 WRIT PETITION (CIVIL) NO.220 OF 2015 TRANSFER PETITION (CIVIL) NO.921 OF 2015 CONTEMPT PETITION (CIVIL) NO.144 OF 2014 IN WP(C) 494/2012 CONTEMPT PETITION (CIVIL) NO.470 OF 2015 IN WP(C) 494/2012 O R D E R 1. In this batch of matters, a scheme propounded by the Government of India popularly known as “Aadhaar Card Scheme” is under attack on various counts. For the purpose of this order, it is not necessary for us to go into the details of the nature of the scheme 1 and the various counts on which the scheme is attacked. Suffice it to say that under the said scheme the Government of India is collecting and compiling both the demographic and biometric data of the residents of this country to be used for various purposes, the details of which are not relevant at present. 2. One of the grounds of attack on the scheme is that the very collection of such biometric data is violative of the “right to privacy”. -

Digital India
Digital India - High-Speed Internet Networks to Rural Areas [UPSC Notes GS-III] The Indian Government launched the Digital India campaign to make available government services to citizens electronically by online infrastructure improvement and also by enhancing internet connectivity. It also aims to empower the country digitally in the domain of technology. Prime Minister Narendra Modi launched the campaign on 1st July 2015. To know more about the Digital India Campaign, refer to the table below: Digital India Date of launching 1st July 2015 Government Ministry Ministry of Electronics and Information Technology, Finance Ministry Launched by PM Narendra Modi Official website https://digitalindia.gov.in/ Digital India is an important campaign started by the Government of India and is equally important for the IAS Exam. Candidates can also download Digital India notes PDF at the end of this article. What is Digital India? Digital India was an initiative taken by the Government of India for providing high-speed internet networks to rural areas. Digital India Mission was launched by PM Narendra Modi on 1st July 2015 as a beneficiary to other government schemes including Make in India, Bharatmala, Sagarmala, Startup India, BharatNet, and Standup India. Digital India Mission is mainly focused on three areas: 1. Providing digital infrastructure as a source of utility to every citizen. 2. Governance and services on demand. 3. To look after the digital empowerment of every citizen. Digital India was established with a vision of inclusive growth in areas of electronic services, products, manufacturing, and job opportunities. There are major nine pillars of Digital India that are mentioned in the table below: Broadband Highways Universal Access to Mobile Public Internet Access Connectivity Programme e-Governance e-Kranti Information for All Electronics IT for Jobs Early Harvest Programmes Manufacturing To know about other government schemes, candidates can refer to the linked article.