Fortinet Security Solutions for SAP S/4HANA Securing the Intelligent Enterprise
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is the SAP Transformation Navigator?
SAP Transformation Navigator – Representative Transformation Guide What is the SAP Transformation Navigator? The SAP Transformation Navigator is a complimentary, self-service tool which instantly summarizes the specific products a company needs to take its business to the next level of disruptive innovation - using an SAP S/4 HANA- centric landscape. What is this Transformation Guide? The SAP Transformation Navigator generates a custom product map and transformation guide which summarize the model you developed in the tool. This is a sample comprehensive transformation guide which represents a typical customer within this industry. As you explore this guide, imagine how your own company would prioritize business and value drivers and how your landscape might evolve. Designed to serve as your road map to transformation, this 150+ page document includes the following sections: Business guide: Review information on where you want to take your business, where your priorities lie, the value drivers for success, and expected outcomes. Technical guide: Understand how your landscape could evolve, what you need to plan for, and how your migration can happen. Transformation guide: Find out what you are licensed for today and what you need to migrate or add; see customer stories relevant to your choices and get a sample timeline for making the transition to SAP S/4HANA. What are my next steps? Build your own custom product map from the start or by leveraging predefined industry templates, and generate transformation guide using the SAP Transformation Navigator. Access the tool online at www.sap.com/transformationnavigator and log in with your s-user id (note: access is part of your SAP maintenance subscription). -

Product Plan SAP Analytics Cloud and Digital Boardroom Q4 2020
Product Plan SAP Analytics Cloud and Digital Boardroom Q4 2020 PUBLIC Quarterly Release Schedule Updates to the Timeline Since launching in 2015, SAP Analytics Cloud received updates approximately every two weeks. As of version 2018.19, we moved from a bi-weekly release schedule to a Quarterly Release schedule to align with SAP’s global strategy for cloud application releases. This means you can expect a new version once every quarter. The Product Plan timeline shown below will now reflect the current plan based on this Quarterly Release Schedule. Q4/2020 Q1/2021 Future Direction If you are on the Fast-Track subscription (updates every two weeks), please note that features may be available to you earlier than what is listed in the Quarterly Release Schedule timeline. More information can be found here. *The upcoming Q4 2020 release of SAP Analytics Cloud is a dedicated quality and performance release. © 2020 SAP SE or an SAP affiliate company. All rights reserved. ǀ PUBLIC 2 Table of contents ▪ Data integration ▪ Modeling ▪ Data visualization ▪ Reporting ▪ Planning ▪ Smart Assist ▪ Smart Predict / Predictive Planning ▪ Analytics Designer ▪ APIs and Extensions for Developers ▪ Intelligent Enterprise ▪ Mobile ▪ Platform Services ▪ Administration and infrastructure ▪ SAP Digital Boardroom ▪ SAP Analytics Content Network ▪ SAP Microsoft Office Add-ins ▪ Product Plan summary © 2020 SAP SE or an SAP affiliate company. All rights reserved. ǀ PUBLIC 3 Product Description SAP Analytics Cloud ACT WITH CONFIDENCE Business Augmented Enterprise Intelligence -

G-Tec Education Sap Learning
G-TEC EDUCATION ISO 9001:2015 CERTIFIED SAP LEARNING HUB - COURSE LIST SL.NO. COURSE NAME 1 1st Steps in SAP Learning Hub 2 A/R Credit Memos 3 ABAP Details 4 ABAP Development Learning Room 5 ABAP Dialog Prog.Using EnjoySAP Controls 6 ABAP Dictionary 7 ABAP Objects 8 ABAP Programming in Eclipse 9 ABAP Programming with SAP NetWeaver: 1. Start With an Overview 10 ABAP Programming with SAP NetWeaver: 2. Become Competent 11 ABAP Programming with SAP NetWeaver: 3. Stay Current 12 ABAP Workbench Concepts 13 ABAP Workbench Concepts – Part 1 14 ABAP Workbench Concepts – Part 2 15 ABAP Workbench Foundations 16 ABAP Workbench Fundamentals 17 ABAP Workbench Fundamentals – Part 1 18 ABAP Workbench Fundamentals – Part 2 19 Accounting 20 Accounting Customizing II: Special G/L Transactions, Document Parking, Validation & Substitution, Archiving 21 Additional Financial Accounting Configuration in SAP S/4HANA 22 Additional Financial Accounting Configuration in SAPS/4HANA 23 Additional SAP Business One Components 24 Add-On Administration 25 Add-On Certification 26 Add-On Licensing 27 Add-On Packaging 28 Advanced ABAP 29 Advanced ABAP Debugging 30 Advanced Extensibility with SAP Cloud SDK 31 Advanced Extensibility with SAP S/4HANA Cloud SDK 32 Advanced G/L Account Determination 33 Advanced SAP MII (Manufacturing Integration and Intelligence) 34 Advanced SAPUI5 Development G-TEC EDUCATION ISO 9001:2015 CERTIFIED SAP LEARNING HUB - COURSE LIST SL.NO. COURSE NAME 35 Advanced SAPUI5 Development - Exercises 36 Agile Project Delivery 37 Aiging report 38 Alerts -

MDI Gurgaon NMP-Placement Brochure 2017-18.Pdf
National Management Programme & Energy Management Programme Full-Time Residential Executive Post Graduate Programme in Management SS OF 2018 CEMENTA BROCHURE A CL PL IDEATION INNOVATION TRANSFORMATION 02 03 04 Message Message from Message from from the the Chairperson, the Coordinator, Acng Director Placements Execuve Placements 05 06 07 08 09 The Student MDI Naonal Energy Genesis Exchange collaboraons Management Management Programme Programme 10 12 13 EPGPM Professors Alumni Courses Speak Speak Offered 14 16 17 45 60 Batch Recruiters Work Work Work Stascs at MDI Experience Experience Experience 2017-18 5-7 Years 7-10 Years 10+ Years BATCH PROFILE 69 70 72 Industry Placement Life at Connect Process at MDI MDI MDI is a school for: Vision Thought Leaders and Change Masters Academic Excellence and Connuous Innovaon Our Mission is to create, both at individual and organizaonal levels, cung edge management capability through: Mission Value-based Educaon Best Global Pracces Acon-centric Research Value-adding Consulng First Indian B-School Accredited by AMBA The instute is partnering with only the top 5 business schools Internaonal accreditaon by the coveted Associaon of MBAs of any country with a spulaon that the partnering B-School (AMBA) UK was awarded to three Programmes of MDI: PGPM, has an extensive internaonal agenda for its acvies. NMP and PGPM (Part-Time) in 2006. Three other Programmes: PGP-HRM, PGP-IM and PGP-EM also received accreditaon in 70+ Naonally and Internaonally Acclaimed 2011 establishing internaonal quality standards of the Full-TIme Faculty Programmes of the Instute. All these programmes were re- One of the largest communies of full-me faculty brings the accredited again by AMBA, UK in 2016. -

System Availability Percentage
SERVICE LEVEL AGREEMENT FOR SAP CLOUD SERVICES 1. Service Level Agreement This Service Level Agreement for SAP Cloud Services sets forth the System Availability Service Level Agreement (“SLA”) for the productive version of the applicable SAP Cloud Services to which customer has subscribed (“SAP Cloud Services”) in an Order Form with SAP. This Service Level Agreement for SAP Cloud Services shall not apply to any SAP Cloud Service for which a System Availability SLA is explicitly set forth in the applicable Supplemental Terms and Conditions for such SAP Cloud Service or for which the applicability of the System Availability SLA is explicitly excluded in the Agreement. 2. Definitions “Downtime” means the Total Minutes in the Month during which the productive version of the applicable SAP Cloud Service is not available, except for Excluded Downtimes. “Month” means a calendar month. “Monthly Subscription Fees” means the monthly (or 1/12 of the annual fee) subscription fees paid for the Cloud Service which did not meet the System Availability SLA. “Total Minutes in the Month” are measured 24 hours at 7 days a week during a Month. “UTC” means Coordinated Universal Time standard. 3. System Availability SLA and Credits 3.1 Claim process, Reports Customer may claim a credit in the amount described in the table of Section 3.2 below in case of SAP’s failure to meet the System Availability SLA, which credit Customer may apply to a future invoice relating to the SAP Cloud Service that did not meet the System Availability SLA. Claims under this Service Level Agreement for SAP Cloud Services must be made in good faith and by submitting a support case within thirty (30) business days after the end of the relevant Month in which SAP did not meet the System Availability SLA. -

Authorized Information Technology Schedule Pricelist General Purpose Commercial Information Technology Equipment, Software and Services
AUTHORIZED INFORMATION TECHNOLOGY SCHEDULE PRICELIST GENERAL PURPOSE COMMERCIAL INFORMATION TECHNOLOGY EQUIPMENT, SOFTWARE AND SERVICES SPECIAL ITEM NUMBERS OFFERED: Special Item No. 132-32, 132-33, 132-34, 132-40, 132-51 Note: All non-professional labor categories must be incidental to and used solely to support hardware, software and/or professional services, and cannot be purchased separately. ADVANTAGED SOLUTIONS, INC. 1455 PENNSYLVANIA AVE NW SUITE 800 WASHINGTON, DC 20004-3024 PHONE: 202-204-3083 Pricelist current through Modification #_PS-0066______, dated _02/11/2019_______. Products and ordering information in this Authorized Information Technology Schedule Pricelist are also available on the GSA Advantage! System (http://www.gsaadvantage.gov). General Services Administration Federal Acquisition Service Page 1 of 305 SPECIAL ITEM NUMBER 132-33 and 132-32- Perpetual Software License SubSIN Categorie(s): FSC/PSC Class 7030 ADP SOFTWARE • Ancillary Financial Systems Software • Application Software • Communications Software • Core Financial Mangement Software • Electronic Commerce (EC) Software • Large Scale Computers • Microcomputers • Operating System Software • Special Physical, Visual, Speech, and Hearing Aid Software. Provide specific information. • Utility Software SPECIAL ITEM NUMBER 132-34 Maintenance of Software as a Service SubSIN Categorie(s): FSC/PSC Class J070 MAINT/REPAIR/REBUILD OF EQUIPMENT- ADP EQUIPMENT/SOFTWARE/SUPPLIES/SUPPORT EQUIPMENT • Maintenance of Software SPECIAL ITEM NUMBER 132-40 CLOUD COMPUTING SERVICES -

SAP Global Partner Summit Agenda
SAP Global Partner Summit Agenda Monday, May 6, 2019, Orlando, Florida, USA Orange County Convention Center, West Concourse, Hall F 7:30 a.m. Registration and Breakfast (Expert Demo Stations and Networking Open at 8:00 a.m.) 9:00 a.m. Opening Keynote: Next-Generation Partnerships in an X+O World Adaire Fox-Martin, Member of the Executive Board, SAP SE, Global Customer Operations Karl Fahrbach, Chief Partner Officer, SAP Arlen Shenkman, EVP Global Business Development and Ecosystems, SAP 10:00 a.m. Expert Demo Stations and Networking Breakout Theater 1 Breakout Theater 2 Breakout Theater 3 Breakout Theater 4 Microforum A Microforum B 10:30 a.m. The Intelligent Enterprise: Experience Matters to Your SAP PartnerEdge: Next Accelerate Your Business Direct Integration 10:30 a.m. IBM Delivering Data-Driven Customer’s Customer Generation Experience Growth with SAP Qualified with SAP Solutions Businesses Partner-Packaged Solutions 11:00 a.m. HPE Intel Expert Demo Stations and Networking and Networking Stations Demo Expert 11:30 a.m. Why Experience Matters – The Best Build on SAP Customer Success with The Intelligent Enterprise for Generating Training and 11:30 a.m. Human Experiences Through SAP S/4HANA Cloud SMEs: A Small Company Can Leads Enablement Data-Driven Insights Do Big Things 12:00 p.m. Digital Enablement Microsoft 12:30 a.m. SAP and Partners Deliver Join SAP S/4HANA Movement: The Secrets to Driving More Next-Generation Cloud Partner 12:30 p.m. Tech Data on the Promise of the The First Step to the Intelligent Pipeline and Revenue Customer Experience with Business Valuation Intelligent Enterprise Enterprise SAP C/4HANA 1:00 p.m. -
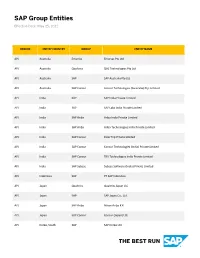
SAP Group Entities Effective Date: May 25, 2021
SAP Group Entities Effective Date: May 25, 2021 REGION ENTITY COUNTRY GROUP ENTITY NAME APJ Australia Emarsys Emarsys Pty Ltd APJ Australia Qualtrics QAL Technologies Pty Ltd APJ Australia SAP SAP Australia Pty Ltd APJ Australia SAP Concur Concur Technologies (Australia) Pty. Limited APJ India SAP SAP India Private Limited APJ India SAP SAP Labs India Private Limited APJ India SAP Ariba Ariba India Private Limited APJ India SAP Ariba Ariba Technologies India Private Limited APJ India SAP Concur ClearTrip Private Limited APJ India SAP Concur Concur Technologies (India) Private Limited APJ India SAP Concur TRX Technologies India Private Limited APJ India SAP Sybase Sybase Software (India) Private Limited APJ Indonesia SAP PT SAP Indonesia APJ Japan Qualtrics Qualtrics Japan LLC APJ Japan SAP SAP Japan Co., Ltd. APJ Japan SAP Ariba Nihon Ariba K.K. APJ Japan SAP Concur Concur (Japan) Ltd. APJ Korea, South SAP SAP Korea Ltd. REGION ENTITY COUNTRY GROUP ENTITY NAME APJ Korea, South SAP SAP Labs Korea, Inc. APJ Malaysia SAP SAP Malaysia Sdn. Bhd. APJ Malaysia SAP Concur CNQR Operations Mexico S. de. R.L. de. C.V. APJ Myanmar SAP SAP System Application and Products Asia Myanmar Limited APJ New Zealand SAP SAP New Zealand Limited APJ Philippines SAP SAP Philippines, Inc. APJ Philippines SAP SuccessFactors SuccessFactors (Philippines), Inc. APJ Singapore Emarsys Emarsys Pte Ltd APJ Singapore Qualtrics QSL Technologies Pte. Ltd. APJ Singapore SAP SAP Asia Pte Ltd APJ Singapore SAP Ariba Ariba International Singapore Pte Ltd APJ Singapore SAP Concur Concur Technologies (Singapore) Pte Ltd APJ Taiwan, China SAP SAP Taiwan Co., Ltd. -

2018 Annual Report Letter from the Chairman
1 2018 ANNUAL REPORT LETTER FROM THE CHAIRMAN 2018 ANNUAL REPORT 2 2018 ANNUAL REPORT CHAPTER 3 CONTENTS _CORPORATE ACTIVITIES AND BUSINESS 49 Description of the Industrial Sector 50 The Gaming Industry in Latin America 50 The Tourism and Hotel Industry in Latin America 56 Industry Trends 60 LETTER FROM THE CHAIRMAN 3 _ Description of the Business 62 CHAPTER 1 CHAPTER 4 OUR COMPANY 5 ANNUAL PERFORMANCE 2018 65 _ _ Information about the Entity 6 2018 Main Figures 66 About Enjoy 7 Financial Management 70 Our Operations 10 Material Events 74 Value Proposal 21 Market Information 77 Adding Value to the Business 28 Risk Factors 79 History 31 Investment Plans 83 Sustainable Management 84 CHAPTER 2 CORPORATE GOVERNANCE 33 CHAPTER 5 _ FINANCIAL STATEMENTS 109 _ Board of Directors 34 Information on Subsidiaries/Associates and Investments with Senior Executives as of January 31, 2019 39 110 Corporate Governance Practices and Policies 42 other Companies Ownership Structure and Major Shareholders 43 Financial Statements 150 Summary of Comments and Proposals by Shareholders and Earnings Reports 48 Directors’ Committee Statement of Responsibility 3 2018 ANNUAL REPORT LETTER FROM THE CHAIRMAN LETTER FROM THE CHAIRMAN Dear Shareholders: 2018 has been a year of major milestones for our Company and the first step in a transformation that marks the start of a new era for Enjoy. Among the most important events, we presented very attractive proposals for 4 casino operating licenses and were granted all 4. The Coquimbo, Viña del Mar and Pucón casinos will remain under Enjoy operation, and they will be joined by our newest operating license for the Puerto Varas Casino. -

Sap Agm 2017
Annual General Meeting of Shareholders – May 10, 2017 CEO Speech – Bill McDermott The spoken word applies Guten Morgen Meine Damen und Herren. Willkommen in der SAP Arena. The video message you just watched tells a powerful story. Michael Dell built one of the most significant companies in the world. Now he is reinventing his company for the 21st century with SAP. For more than 350,000 customers in 193 countries, SAP is THE trusted innovator. As you will hear in my remarks today, SAP has never been a stronger company. We have never been more dedicated to serving our customers or creating value for our shareholders. From this position of immense strength, we will discuss the very bright future of SAP. This is especially important when you consider our unique past. SAP’s distinguished Chairman, Hasso Plattner, is a once-in-a-generation innovator. Together with his co-founders, he gave us a legacy of excellence that we work to honor each and every day. To help carry that legacy forward, I proudly welcome Adaire Fox-Martin and Jennifer Morgan to the Executive Board of SAP. Congratulations Adaire and Jen. -------- Dear Chairman, Dear Supervisory Board members, thank you for your continued confidence and support. Nothing that we achieve would be possible without SAP’s 85,571 employees. Please join me in thanking them for their outstanding work. (Applause) 1 Now let’s discuss our past, present and future. SAP’s record of success: 2010 – present I’ll begin by looking back. In 2010, we set out to make SAP the world’s most innovative growth company. -

SAP Capital Markets Day, November 2019, Presentation
NOVEMBER 12, 2019 THANK YOU FOR BEING WITH US TODAY FOR A SPECIAL SAP Capital Markets Day 2019 CAPITAL MARKETS DAY NOVEMBER 12, 2019 Growth and Operational Excellence 9:30 – 9:35 am Welcome Stefan Gruber, Head of Investor Relations 9:35 – 10:25 am The Co-CEO Perspective Jennifer Morgan, Co-CEO Christian Klein, Co-CEO 10:25 – 10:50 am Experience Management Update Ryan Smith, CEO Qualtrics 10:50 – 11:00 am Coffee Break 11:00 – 11:35 am The Innovation and Customer Perspective Adaire Fox-Martin, Member of the Executive Board, Global Customer Operations Thomas Saueressig, Member of the Executive Board, Product Engineering 11:35 – 12:15 pm The Financial Perspective Luka Mucic, CFO 12:15 – 1:00 pm Q&A Adaire Fox-Martin, Christian Klein, Jennifer Morgan, Luka Mucic, Thomas Saueressig 1:00 – 2:00 pm Buffet Lunch Reception with SAP Executives ©2019 SAP SE or an SAP affiliate company. All rights reserved. 2 CAPITAL MARKETS DAY NOVEMBER 12, 2019 WELCOME TO A SPECIAL SAP Capital Markets Day 2019 CHRISTIAN JENNIFER ADAIRE LUKA THOMAS RYAN KLEIN MORGAN FOX-MARTIN MUCIC SAUERESSIG SMITH Co-CEO Co-CEO Global Customer CFO Product CEO & Co-Founder Operations Engineering Qualtrics ©2019 SAP SE or an SAP affiliate company. All rights reserved. 3 CAPITAL MARKETS DAY NOVEMBER 12, 2019 Safe Harbor Statement Any statements contained in this document that are not historical facts are forward-looking statements as defined in the U.S. Private Securities Litigation Reform Act of 1995. Words such as “anticipate,” “believe,” “estimate,” “expect,” “forecast,” “intend,” “may,” “plan,” “project,” “predict,” “should” and “will” and similar expressions as they relate to SAP are intended to identify such forward-looking statements. -

SAP's Integration Strategy & Update
SAP’s Integration Strategy & Update Intelligent Enterprises are Integrated Enterprises Webinar for the SAP User Groups, October 22nd 2020 Katrin von Ahsen, Product Management Intelligent Enterprise Technology Udo Paltzer, Product Management SAP Cloud Platform Integration Suite SAP SE Disclaimer The information in this presentation is confidential and proprietary to SAP and may not be disclosed without the permission of SAP. Except for your obligation to protect confidential information, this presentation is not subject to your license agreement or any other service or subscription agreement with SAP. SAP has no obligation to pursue any course of business outlined in this presentation or any related document, or to develop or release any functionality mentioned therein. This presentation, or any related document and SAP's strategy and possible future developments, products and or platforms directions and functionality are all subject to change and may be changed by SAP at any time for any reason without notice. The information in this presentation is not a commitment, promise or legal obligation to deliver any material, code or functionality. This presentation is provided without a warranty of any kind, either express or implied, including but not limited to, the implied warranties of merchantability, fitness for a particular purpose, or non-infringement. This presentation is for informational purposes and may not be incorporated into a contract. SAP assumes no responsibility for errors or omissions in this presentation, except if such damages were caused by SAP’s intentional or gross negligence. All forward-looking statements are subject to various risks and uncertainties that could cause actual results to differ materially from expectations.