University of Sheffieldacademic Computing Services
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -
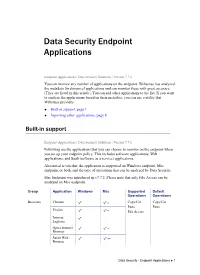
Data Security Endpoint Applications
Data Security Endpoint Applications Endpoint Applications | Data Security Solutions | Version 7.7.x You can monitor any number of applications on the endpoint. Websense has analyzed the metadata for dozens of applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 8 Built-in support Endpoint Applications | Data Security Solutions | Version 7.7.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy. This includes software applications, Web applications, and SaaS (software as a service) applications. Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by Data Security. Mac Endpoint was introduced in v7.7.2. Please note that only File Access can be analyzed on Mac endpoint. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome * Copy/Cut Copy/Cut Paste Paste Firefox * File Access Internet Explorer Opera Internet * Browser Safari Web ** Browser Data Security - Endpoint Applications 1 Data Security Endpoint Applications Group Application Windows Mac Supported Default Operations Operations CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility -
Malware: Computer Viruses, Spyware, and Key-Loggers
Certificates for cs.washington.edu 1 Certificates for GMail Important fields: Testing SSL Configuration (1) 3 Client completed verification of received certificate chain Testing SSL Configuration (2) 4 Received certificate chain (two certificates) Size of received certificate chain Testing SSL Configuration (3) 5 Issued session identifier (Session-ID) for stateful TLS resume. Example from “High Performance Browser Networking” Where to Use SSL? 6 Login page? Where else? What about JavaScript includes? Image includes? Why not encrypt everything? Where to Use SSL? 7 Some browsers may not support SSL SSL may decrease performance somewhat. If users are downloading large, public files, there may be a system burden to encrypt these each time. You will probably want the home page accessible via HTTP, so that users don't have to remember to type https to get to it. Firesheep (2010) 8 Assume you are using the facebook.com site over an unsecured Wi-Fi network such as in shopping malls and coffee shops. When you visit the Facebook site, you are required to enter the username and password. When you send that request and on successful login, Facebook sends you an authentication token in the clear which is then sent every time you browse Facebook pages Firesheep 9 Facebook Switches to HTTPS in 2012 10 Lab-2 11 Part 1 Part 2 Black-box fuzzing is far C programming is tricky from easy Bounds are far from obvious even when Very little insight into reasoning about a short program behavior function Makes you appreciate Makes you appreciate programming in Java or having access to C# where array accesses source code! are checked at runtime! Lab-2: Survey 12 Part 1 Part 2 A. -

C3000 Microsoft Outlook User Manual
C3000 Microsoft Outlook User Manual Rel. 1.7 SP2 18-11-2008 © 2008 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and accurate at the time of printing, Avaya Inc. can assume no liability for any errors. Changes and corrections to the information in this document may be incorporated in future releases. For full legal page information, please see the complete document, Avaya Legal Page for Software Documentation, Document number 03-600758. To locate this document on the website, simply go to http://www.avaya.com/support and search for the document number in the search box. Documentation disclaimer Avaya Inc. is not responsible for any modifications, additions, or deletions to the original published version of this documentation unless such modifications, additions, or deletions were performed by Avaya. Customer and/or End User agree to indemnify and hold harmless Avaya, Avaya's agents, servants and employees against all claims, lawsuits, demands and judgments arising out of, or in connection with, subsequent modifications, additions or deletions to this documentation to the extent made by the Customer or End User. Link disclaimer Avaya Inc. is not responsible for the contents or reliability of any linked Web sites referenced elsewhere within this documentation, and Avaya does not necessarily endorse the products, services, or information described or offered within them. We cannot guarantee that these links will work all of the time and we have no control over the availability of the linked pages. Warranty Avaya Inc. provides a limited warranty on this product. -

Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM
Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM Sign In Sign-Up We have copied this page for reference in case it disappears from the web. The copyright notice appears at the end. If you want the latest version go to the original page: http://www.expita.com/nomime.html Turning Off HTML or MIME to use a Remailer System. Index (5 topics) Introduction E-mail client programs (Turning Off HTML or MIME to use a Remailer System) Suggestions for HTML users Examples of HTML/MIME messages References What is wrong with sending HTML or MIME messages? There are now six main reasons for NOT doing this: 1. Many E-mail and Usenet News reader programs, usually the mail and news reader programs that come with browser packages, allow users to include binary attachments (MIME or other encoding) or HTML (normally found on web pages) within their E-mail messages. This makes URLs into clickable links and it means that graphic images, formatting, and even color coded text can also be included in E-mail messages. While this makes your E-mail interesting and pretty to look at, it can cause problems for other people who receive your E- mail because they may use different E-mail programs, different computer systems, and different application programs whose files are often not fully compatible with each other. Any of these can cause trouble with in-line HTML (or encoded attachments). Most of the time all they see is the actual HTML code behind the message. And if someone replies to the HTML formatted message, the quoting can render the message even more unreadable. -

Review, Email Clients with Source Code Editing
Review, Email Clients with Source Code Editing By Micheline Johnson Updated 2013-12-05 Why is source code editing desirable? It enables the addition of variable indenting and hanging indents, tables, images, charts, videos etc. the replacement of <p> tags with <div> tags, if para spacing is not required. Wikipedia lists most email clients. Of these, the free Windows or cross-platform GUI email clients are included in the Appendix. Of these, the current mainstream desktop GUI email clients include: 1. Outlook, overkill for most purposes, and is not free. 2. Outlook Express, not available for Windows 7 3. Windows Live Mail 4. Mozilla Thunderbird, does not natively support HTML editing or tables. 5. Eudora v7.1, runs on Microsoft Windows XP/2000 (http://www.eudora.com/download/). It has problems with Windows 7, see http://mcaf.ee/cxsw8 . It runs on Windows XP, and does not appear to support editing HTML source code, or tables. 6. Eureka Email. It is very difficult to uninstall, see http://mcaf.ee/1q0ka , so I did not test it. 7. Pegasus Mail. Pegasus v4.63 allows the insertion of a table and the editing of the number of rows or columns of that table; but it does not support editing of HTML source code. It supports hanging indents to increments of one tab spacing, which is very crude. 8. DreamMail 9. FoxMail 10. SeaMonkey. http://www.seamonkey-project.org/. Allows inserting of tables. Appears to allow insertion of HTML code, but does not allow viewing of the entire HTML source code. 11. Netscape Messenger used to have an HTML editor. -

Application Support with TRITON AP-ENDPOINT DLP
Application Support with TRITON AP-ENDPOINT DLP Endpoint Applications| TRITON AP-ENDPOINT DLP | Version 8.1.x You can monitor any number of applications for data loss on endpoint clients when they are off network. Websense has analyzed the metadata for more than a hundred applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 11 Built-in support Endpoint Applications | TRITON AP-ENDPOINT DLP | Version 8.1.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy in the Data Security manager. This includes software applications, web applications, and cloud applications. Endpoint Applications 1 Application Support with TRITON AP-ENDPOINT DLP Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by TRITON AP-DATA. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome Copy/Cut Copy/Cut Paste Paste Firefox File Access Internet Explorer Internet Explorer 10, 11 (store app) Opera Internet Browser Safari Web Browser Torch Browser CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility Nero Burning ROM Roxio Creator Classic iTunes 2 TRITON AP-ENDPOINT -
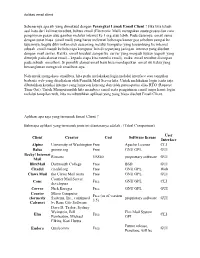
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

A Framework for the Implementation of Secure Bare-Based Web-Email System
GSTF Journal on Computing (JoC) Vol.4 No.3, October 2015 DOI 10.7603/s40601-014-0018-4 A Framework for the Implementation of Secure Bare-Based Web-Email System Patrick Appiah-Kubi, Anthony Tsetse, and Alae Loukili Received 29 Jun 2015 Accepted 27 Jul 2015 Abstract - Webmail systems have being developed for services to ensure email exchanges. Figure 1 presents a different OS-based platforms. These OS-based systems pictorial illustration of email exchanges between the present their own benefits and treats. Framework and white various email services. papers for developing these systems are available but there is no specific framework available for the implementation of user mail such systems on Bare PC. Implementation of such systems on agent a Bare PC poses daunting challenges and innovative HTTP/TLS server Request SMTP/POP3 opportunities that are revolutionary in server designs. Web server / Building such systems for security could even be more Mail Agent challenging. Secure Webmail systems are complex, large and require intricate components to develop. As a result, a lean system was developed for this research. The lean concept also SQL Queries helps to build small protocol suite, intertwining of protocols, limited requirement space, simple user interfaces and minimal design options. The paper provides a detail framework for the design and implementation, experimental setup and the results of experiments conducted. Performance Database is evaluated by measuring the processing time, throughput, the CPU Utilization and load distribution. The results show Figure 1: Conventional Email Exchanges that the performance of the Bare PC Webmail server is significantly better than that of the OS-based servers. -

Freeware-List.Pdf
FreeWare List A list free software from www.neowin.net a great forum with high amount of members! Full of information and questions posted are normally answered very quickly 3D Graphics: 3DVia http://www.3dvia.com...re/3dvia-shape/ Anim8or - http://www.anim8or.com/ Art Of Illusion - http://www.artofillusion.org/ Blender - http://www.blender3d.org/ CreaToon http://www.creatoon.com/index.php DAZ Studio - http://www.daz3d.com/program/studio/ Freestyle - http://freestyle.sourceforge.net/ Gelato - http://www.nvidia.co...ge/gz_home.html K-3D http://www.k-3d.org/wiki/Main_Page Kerkythea http://www.kerkythea...oomla/index.php Now3D - http://digilander.li...ng/homepage.htm OpenFX - http://www.openfx.org OpenStages http://www.openstages.co.uk/ Pointshop 3D - http://graphics.ethz...loadPS3D20.html POV-Ray - http://www.povray.org/ SketchUp - http://sketchup.google.com/ Sweet Home 3D http://sweethome3d.sourceforge.net/ Toxic - http://www.toxicengine.org/ Wings 3D - http://www.wings3d.com/ Anti-Virus: a-squared - http://www.emsisoft..../software/free/ Avast - http://www.avast.com...ast_4_home.html AVG - http://free.grisoft.com/ Avira AntiVir - http://www.free-av.com/ BitDefender - http://www.softpedia...e-Edition.shtml ClamWin - http://www.clamwin.com/ Microsoft Security Essentials http://www.microsoft...ity_essentials/ Anti-Spyware: Ad-aware SE Personal - http://www.lavasoft....se_personal.php GeSWall http://www.gentlesec...m/download.html Hijackthis - http://www.softpedia...ijackThis.shtml IObit Security 360 http://www.iobit.com/beta.html Malwarebytes' -

Introduction to Email Compatibility
Galion Public Library Introduction to email Page 1 introduction to email Ever since computers have been networked together, people have used the network to send messages back and forth. There are several ways to send messages over the internet, but email is the most popular. If you have an email account, you can send a message to anyone else who also has an email account, provided you know their email address. The really convenient thing about email is that it automatically adjusts to everyone's schedule: you send messages whenever you get around to it, and the recipients can read compatibility and answer them whenever they get around to doing so. People often ask: "If my friend When you sign up with an internet service provider, one of has email through one service the services they usually provide for you is an email provider, and I get email through a account. Using your email account, together with software different provider, can I send called a mailreader (see page 6), you can send and receive email to my friend?" messages over the internet. The mailreader can get your mail, store it for future reference, show it to you, let you The short answer is, "Yes." organize it, and let you write and send your own messages. The longer answer is that there Once you have an email are technical standards that account, people can send you govern the underlying details of email at any time, even when how the parts of the message are you are not connected. represented as they are When someone sends you a message, it goes to a special transmitted from place to place.