A Framework for the Implementation of Secure Bare-Based Web-Email System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

System Node Reference
IceWarp Unified Communications System Node Reference Version 10.4 Print ed on 10 December, 2012 Contents System Node 1 Services .......................................................................................................................................................................... 2 Service Ports ...................................................................................................................................................... 2 General .............................................................................................................................................................. 4 Service – Properties ............................................................................................................................... 7 Service – Logging ................................................................................................................................... 9 Service – Access ................................................................................................................................... 10 Service – Other .................................................................................................................................... 11 SOCKS and Minger Server .................................................................................................................... 12 SOCKS .................................................................................................................................................. 12 Minger Server ..................................................................................................................................... -

Leveraging Open Source Software
1 Leveraging Open Source Software (Text of talk delivered by Justice Yatindra Singh Judge Allahabad High Court at the 9th e- Governance conference on 3rd February 2006 at Kochi, Kerala) FUD is an abbreviation of fear, uncertainty and doubt; it is often a salesman's strategy: spreading false rumours regarding others' products. Open source software (OSS) is its victim. In our country FUD for OSS arises out of ignorance. I am glad that, we are discussing OSS as it has crucial role to play in the IT world. WHAT IS OSS? A computer programme consists of two parts: Source Code and Object Code. Nowadays, computer programmes are written in high level computer languages using compact English words. This part is known as source code. These languages also have a programme called compiler and with their help, source code is compiled into machine language so that computers may understand it. When it is so done, it is called object code or machine code. Description―if it complies with certain conditions―is protected as a Copyright. Source code is a kind of description and can be protected as copyright provided it is published or disclosed. In the proprietery software, source code is generally not disclosed and in such a situation it is protected as a trade secret or undisclosed information. There was a debate whether object code is protected as a copyright or not but after TRIPS, it has to be protected as a copyright and now object code is so protected. Everyone is not using copyrights to have rights in computer programme. -

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

AXIGEN Mail Server™ Has Been Designed to Enable Businesses to Cut Costs Without Cutting Corners
Combating the increasing cost of email Why you should read this white paper Businesses usually adopt a commonsense approach when it comes to spending the IT budget with cost being a major influencer in purchasing decisions. However, when it comes to choosing a mail server, many businesses seem to pay less attention to the costs and, as a result, end up spending far more money than is necessary. This white paper will explain how businesses can significantly reduce the costs of their email communication while continuing to provide users with a best-in-class messaging and collaboration solution. White paper Introduction Today, email is absolutely mission-critical. Communication and collaboration keep your business running. Email and electronically enabled collaboration have become so embedded in normal day-to-day operations that many businesses simply could not function without them. These services enable everything from productivity enhancing collaboration between employees to external communications with customers and business partners and demand 24x7 availability. Many businesses, however, have found that the cost of providing employees with the latest in messaging and collaboration technology is rapidly escalating. To meet modern business needs, mail servers have had to become more complex – and with that additional complexity come additional management burdens and costs. Furthermore, some mail servers have an upgrade process that is both extremely complex and extremely costly and which may necessitate the purchase of replacement server hardware. Combined, these factors place a considerable drain on corporate resources. The problem is especially severe for small and medium sized businesses (SMBs) which usually do not have access to the same financial or technical resources as large enterprises. -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Mailarchiva Enterprise Edition V1.9
MailArchiva Enterprise Edition Administration Guide Willkommen Bienvenidos Welkom Bienvenue Welcome MailArchiva Enterprise Edition v1.9 INSTALLATION AND AMINISTRATION GUIDE For Windows / Linux MailArchiva Enterprise Edition Administration Guide 1 INDEX 1 INDEX ............................................................................................................. 2 2 IMPORTANT NOTICE ....................................................................................... 4 3 CONTACT INFORMATION ................................................................................. 4 TECHNICAL REQUIREMENTS .................................................................................. 5 4 OVERVIEW ...................................................................................................... 6 5 HIGH-LEVEL FEATURES ................................................................................... 7 6 ARCHITECTURE ............................................................................................... 9 7 INSTALLATION .............................................................................................. 10 7.1 EXCHANGE SERVER CONFIGURATION .................................................................... 11 7.2 SERVER INSTALLATION (ON WINDOWS ) ................................................................ 14 7.3 SERVER INSTALLATION (ON LINUX ) ..................................................................... 15 7.4 MICROSOFT EXCHANGE ................................................................................... -

OSS Watch National Software Survey 2008
OSS Watch National Software Survey 2008 Ramón Casero Cañas Acknowledgements Publication information The survey was prepared and the report written by Ramón This survey report is licensed under the Creative Commons Casero Cañas (OSS Watch), and edited by Ross Gardler and Attribution-ShareAlike 2.0 England & Wales licence. Elena Blanco (OSS Watch), and Pete Cooper. OSS Watch National Software Survey 2008 However, there are many people who helped to make it pos- Ramón Casero Cañas sible. We would like to thank the ICT directors of the FE and HE institutions, who took the time to respond to the survey First edition, published February 2009. and send feedback to us; Dr Ellen Helsper (Oxford Internet Institute) for her advice, academic input and support; Randy Metcalfe, former OSS Watch Service Manager, who set us with this task and was always a source of encouragement and support; Michael Fraser, former OSS Watch Director, for his comments; Gabriel Hanganu, Stuart Yeates and Rowan Wilson (OSS Watch) for their comments, envelope stuffing, corrections and so much more; Laura Marriott and Beverley McNichols for their data collection; Jean Davis and Sally Hard- ing for envelope stuffing; Barry Cornelius, Dominic Hargreaves, Charles Hutchings, Liz Masterman, Denise McDonough, Stuart Lee, Janet McKnight, Howard Noble, Mark Norman, Catrin Radcliffe and Peter Robinson for their comments about the online questionnaire; Judy McAuliffe, Tina Dick, Leslie Ferguson, Fran Jackson, Bruce Shakespeare, Jane Truby and Wendy Simmonds for their help with administration -
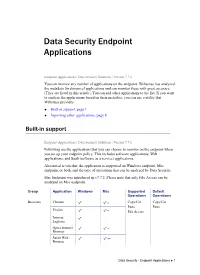
Data Security Endpoint Applications
Data Security Endpoint Applications Endpoint Applications | Data Security Solutions | Version 7.7.x You can monitor any number of applications on the endpoint. Websense has analyzed the metadata for dozens of applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 8 Built-in support Endpoint Applications | Data Security Solutions | Version 7.7.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy. This includes software applications, Web applications, and SaaS (software as a service) applications. Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by Data Security. Mac Endpoint was introduced in v7.7.2. Please note that only File Access can be analyzed on Mac endpoint. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome * Copy/Cut Copy/Cut Paste Paste Firefox * File Access Internet Explorer Opera Internet * Browser Safari Web ** Browser Data Security - Endpoint Applications 1 Data Security Endpoint Applications Group Application Windows Mac Supported Default Operations Operations CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility -
Malware: Computer Viruses, Spyware, and Key-Loggers
Certificates for cs.washington.edu 1 Certificates for GMail Important fields: Testing SSL Configuration (1) 3 Client completed verification of received certificate chain Testing SSL Configuration (2) 4 Received certificate chain (two certificates) Size of received certificate chain Testing SSL Configuration (3) 5 Issued session identifier (Session-ID) for stateful TLS resume. Example from “High Performance Browser Networking” Where to Use SSL? 6 Login page? Where else? What about JavaScript includes? Image includes? Why not encrypt everything? Where to Use SSL? 7 Some browsers may not support SSL SSL may decrease performance somewhat. If users are downloading large, public files, there may be a system burden to encrypt these each time. You will probably want the home page accessible via HTTP, so that users don't have to remember to type https to get to it. Firesheep (2010) 8 Assume you are using the facebook.com site over an unsecured Wi-Fi network such as in shopping malls and coffee shops. When you visit the Facebook site, you are required to enter the username and password. When you send that request and on successful login, Facebook sends you an authentication token in the clear which is then sent every time you browse Facebook pages Firesheep 9 Facebook Switches to HTTPS in 2012 10 Lab-2 11 Part 1 Part 2 Black-box fuzzing is far C programming is tricky from easy Bounds are far from obvious even when Very little insight into reasoning about a short program behavior function Makes you appreciate Makes you appreciate programming in Java or having access to C# where array accesses source code! are checked at runtime! Lab-2: Survey 12 Part 1 Part 2 A. -

Efficient Spam Filtering System Based on Smart Cooperative Subjective and Objective Methods*
Int. J. Communications, Network and System Sciences, 2013, 6, 88-99 http://dx.doi.org/10.4236/ijcns.2013.62011 Published Online February 2013 (http://www.scirp.org/journal/ijcns) Efficient Spam Filtering System Based on Smart * Cooperative Subjective and Objective Methods Samir A. Elsagheer Mohamed1,2 1College of Computer, Qassim University, Qassim, KSA 2Electrical Engineering Department, Faculty of Engineering, Aswan University, Aswan, Egypt Email: [email protected], [email protected] Received September 17, 2012; revised January 16, 2013; accepted January 25, 2013 ABSTRACT Most of the spam filtering techniques are based on objective methods such as the content filtering and DNS/reverse DNS checks. Recently, some cooperative subjective spam filtering techniques are proposed. Objective methods suffer from the false positive and false negative classification. Objective methods based on the content filtering are time con- suming and resource demanding. They are inaccurate and require continuous update to cope with newly invented spammer’s tricks. On the other side, the existing subjective proposals have some drawbacks like the attacks from mali- cious users that make them unreliable and the privacy. In this paper, we propose an efficient spam filtering system that is based on a smart cooperative subjective technique for content filtering in addition to the fastest and the most reliable non-content-based objective methods. The system combines several applications. The first is a web-based system that we have developed based on the proposed technique. A server application having extra features suitable for the enter- prises and closed work groups is a second part of the system. Another part is a set of standard web services that allow any existing email server or email client to interact with the system. -

Mail Box Server and Web Mail Server
OPS535 – Advanced Network Administration Mail Box Server Lab POP3 and IMAP Servers Web mail using squirrelmail Secure IMAP (Mail Box Server) server for user's remote mail access CentOS 7.0 rpm package: dovecot 2.2.10-4 CentOS7,0 Web Site: http://www.dovecot.org Configuration file: /etc/dovecot/dovecot.conf Starting/stopping dovecot use systemctl command - by default starts/stops pop3, pop3s, imap, imaps Logging: by default log messages send to /var/log/maillog file (syslog option) Very Useful Command: dovecot -n (display vital information about dovecot) On CentOS 7.0: [root@mail ~]# dovecot -n # 2.2.10: /etc/dovecot/dovecot.conf # OS: Linux 3.10.0-229.14.1.el7.x86_64 x86_64 CentOS Linux release 7.1.1503 (Core) mbox_write_locks = fcntl namespace inbox { inbox = yes location = mailbox Drafts { special_use = \Drafts } mailbox Junk { special_use = \Junk } mailbox Sent { special_use = \Sent } mailbox "Sent Messages" { special_use = \Sent } mailbox Trash { special_use = \Trash } prefix = } passdb { driver = pam } ssl = required ssl_cert = </etc/pki/dovecot/certs/dovecot.pem ssl_key = </etc/pki/dovecot/private/dovecot.pem userdb { driver = passwd } On CentOS 5.3: root@localhost ~]# dovecot -n # 1.0.7: /etc/dovecot.conf login_dir: /var/run/dovecot/login login_executable(default): /usr/libexec/dovecot/imap-login login_executable(imap): /usr/libexec/dovecot/imap-login login_executable(pop3): /usr/libexec/dovecot/pop3-login mail_executable(default): /usr/libexec/dovecot/imap mail_executable(imap): /usr/libexec/dovecot/imap mail_executable(pop3):