How to Get Email Headers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trusted Root.Ai
SSL Certs Code Signing A Leader in Online Security Doc Signing & Authentication Solutions for over 10 years Digital IDs GlobalSign Trusted Root™ Global acceptance and trust for your Microsoft CA or Inhouse CA In recent years many enterprises and major organizations have established ubiquitous to be used without support issues. The time and cost associated their own Enterprise Certificate Authority (CA) such as the Microsoft CA with with an Embedding Program massively outweigh any advantage that would the primary goal of enhancing security for an ever increasing number of be associated with implementing an Enterprise CA solution. diverse web based business processes. For an enterprise to establish their Today, there is no need for such CAs to have their Root Certificate directly own Enterprise CA it must self-sign a CA Root Certificate, which is then used to embedded in browsers to create the necessary feeling of trust. GlobalSign has issue digital certificates to employees, extranet users and even machines and made available a simple solution for CAs to chain themselves under services. Such certificates can then be used to digitally sign and encrypt GlobalSign's embedded Root Certificate: Trusted Root™. communications and also to control access to web resources. However this self-signed Root CA Certificate is not automatically trusted by main-stream As a leading WebTrust accredited Certification Authority, GlobalSign has operating systems (such as Microsoft Windows), browsers (such as Microsoft maintained its own pioneering Root Embedding program GlobalSign Ready Internet Explorer, Mozilla Firefox) or email clients (such as Microsoft Outlook). for over 10 years and now the GlobalSign Root CA Certificate is trusted by This inability to trust causes warning messages to be displayed, resulting in a practically all mainstream browsers and applications. -

Znetlive SSL Compatible Applications, Platforms & Operating
ZNetLive SSL Compatible Applications, Platforms & Operating Systems Certificate Authority Root Apple MAC OS 9.0+ (circa 2002), includes 10.5.X and 10.6.X Future proof at 2048 bit, embedded in all Microsoft Windows XP, Vista, 7 and 8 (all devices and browsers and capable of upgrading versions inc 32/64 bit) weak encryption to a strong one is the most reliable Certificate Authority Root-GlobalSign. It is very important to ensure a flawless interaction of your online solutions with Default API Support within Hosting Control customers making connection with your web Panels server, reading emails, trusting your e- Ubersmith documents or running your code. Every WHMCS standard machine that uses trust of Public Key Infrastructure (PKI), e.g. S/MIME, SSL/TLS, Document Signing and Code Signing, has GlobalSign’s Root Certification present in it. Email Clients (S/MIME) ZNetLive’s SSL Certificates authenticated by GlobalSign have 2048 bit strength throughout Mulberry Mail complete Digital Certificate portfolio and Microsoft Outlook 99+ comply with recommendations of National Microsoft Entourage (OS/X) Institute of Standards and Technology (NIST) Qualcomm Eudora 6.2+ according to which all cryptographic keys Mozilla Thunderbird 1.0+ should be 2048 bit strength from 2011 onwards. Mail.app Anything weaker than 2048 bit encryption is Lotus Notes (6+) considered insecure. Because of this, the Netscape Communicator 4.51+ Certification Authorities and Browsers insists The Bat that all the EV SSL Certificates should be 2048 Apple Mail bit encryption. -

Mac OS 8 Update
K Service Source Mac OS 8 Update Known problems, Internet Access, and Installation Mac OS 8 Update Document Contents - 1 Document Contents • Introduction • About Mac OS 8 • About Internet Access What To Do First Additional Software Auto-Dial and Auto-Disconnect Settings TCP/IP Connection Options and Internet Access Length of Configuration Names Modem Scripts & Password Length Proxies and Other Internet Config Settings Web Browser Issues Troubleshooting • About Mac OS Runtime for Java Version 1.0.2 • About Mac OS Personal Web Sharing • Installing Mac OS 8 • Upgrading Workgroup Server 9650 & 7350 Software Mac OS 8 Update Introduction - 2 Introduction Mac OS 8 is the most significant update to the Macintosh operating system since 1984. The updated system gives users PowerPC-native multitasking, an efficient desktop with new pop-up windows and spring-loaded folders, and a fully integrated suite of Internet services. This document provides information about Mac OS 8 that supplements the information in the Mac OS installation manual. For a detailed description of Mac OS 8, useful tips for using the system, troubleshooting, late-breaking news, and links for online technical support, visit the Mac OS Info Center at http://ip.apple.com/infocenter. Or browse the Mac OS 8 topic in the Apple Technical Library at http:// tilsp1.info.apple.com. Mac OS 8 Update About Mac OS 8 - 3 About Mac OS 8 Read this section for information about known problems with the Mac OS 8 update and possible solutions. Known Problems and Compatibility Issues Apple Language Kits and Mac OS 8 Apple's Language Kits require an updater for full functionality with this version of the Mac OS. -

Getting Started with Eudora 5.1 for Windows 95/98/ME/NT/2000 Author Teresa Sakata
WIN9X003 July 2003 Getting Started with Eudora 5.1 For Windows 95/98/ME/NT/2000 Author Teresa Sakata Introduction ..............................................................................................................................................................1 POP and IMAP Servers ............................................................................................................................................2 Requirements ............................................................................................................................................................2 Changes From Version 4.3.x ....................................................................................................................................3 Issues ........................................................................................................................................................................3 Where do I get Eudora? ............................................................................................................................................4 Getting Started..........................................................................................................................................................4 Installation ................................................................................................................................................................4 Configuring Eudora ..................................................................................................................................................5 -

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Entourage: Interface Explained Instead of Mail, Ical and Address Book Is Such a Good Idea
Entourage Six programs for the price of one Get organised Tooled up Entourage 2004 is really six programs rolled into one, which is why using it Entourage: Interface explained instead of Mail, iCal and Address Book is such a good idea. We’ve already Fabulous folders The Entourage Toolbars As with all other email programs, Entourage uses Almost all of Entourage’s main tools, taken a look at the Mail feature, so here we’ll focus on the other uses for In the first part of a new series on Microsoft Office we turn folders to store and manage email. All the folders set including buttons for composing, sending the program, except Notes, which is just a basic way of typing memos. our attentions to Entourage and find out what PIM means up on your Mac appear here. Create new folders and printing messages can be accessed from the ‘File’ menu, drag and drop messages into from the toolbar at the top of the screen. Entourage’s Address Book is every them from other folders or create Schedules from the You can also turn the Toolbars off from bit as powerful as Apple’s, supports Although many diehard Mac users loathe ‘Tools’ menu to filter incoming messages. the ‘View’ menu. 1 anything that carries the Microsoft insignia, it’s vCards and even allows you to get impossible to ignore the fact that Microsoft driving directions from your street to Office is one of the best slabs of Mac software around. where your contacts live. In fact, many observers believe that Office is better on the Mac than it is on the PC. -

Volume 4, Number 7 July 1, 1998 [email protected]
About This Particular Macintosh™ 4.07: About the personal computing experience™ Volume 4, Number 7 July 1, 1998 Send requests for free subscriptions to: [email protected] Cover Art ©1998 Jamal Ghandour <[email protected]> We need new cover art every month! Write to us! Contributors Scott R. Boveia Scott Byers Martin Cox Simon Edison Jamal Ghandour Edward Goss [email protected] Tom Iovino Staci Trekles Robert Paul Leitao Robert Madill Mike Shields Michael Tsai Marc Zeedar Macintosh users like you Please write for ATPM! Check out the Guidelines Editorial Staff Publishers - Michael Tsai & Robert Paul Leitao Editor - Michael Tsai Managing Editor - Robert Paul Leitao Opinionated Associate Editor - Mike Shields Reviews Editor- Robert Madill Copy Editor - Christopher Turner Shareware Reviews Editor - Vacant Interviews Manager - Vacant Publicity Manager - Kyle Alexander Page o’ Linker - Vacant Welcome Author - Robert Paul Leitao List Server Manager - Michael Tsai Webzingers - Michael Tsai, Evan Trent Beta Testers - The Staff Columnists Jamal Ghandour Edward Goss Tom Iovino Robert Paul Leitao Mike Shields Michael Tsai Artwork & Design Graphics Director - Jamal Ghandour Layout/Design - Michael Tsai Blue Apple Icon Designs - Marc Robinson Typewriter-Style Section Headers - RD Novo The Tools Anarchie AppleWorks BBEdit DOCMaker Emailer Illustrator Kai’s PowerTools LetterRip Myrmidon Nisus Writer Online Army Knife Photoshop ResEdit Snapz Pro StuffIt The Fonts Carbonated Gothic Cheltenham Cloister Foundation Frutiger Garamond Geneva Gill Sans Helvetica Isla Bella Marydale Where to Find ATPM Online and downloadable issues are available at the ATPM Web Page: < h t t p : / / w w w . a t p m . c o m > and via anonymous FTP at: < f t p : / / f t p . -
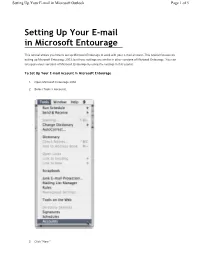
Setting up Your E-Mail in Microsoft Entourage
Setting Up Your E-mail in Microsoft Outlook Page 1 of 5 Setting Up Your E-mail in Microsoft Entourage This tutorial shows you how to set up Microsoft Entourage to work with your e-mail account. This tutorial focuses on setting up Microsoft Entourage 2003, but these settings are similar in other versions of Microsoft Entourage. You can set up previous versions of Microsoft Entourage by using the settings in this tutorial. To Set Up Your E-mail Account in Microsoft Entourage 1. Open Microsoft Entourage 2004. 2. Select Tools > Accounts. 3. Click "New." Setting Up Your E-mail in Microsoft Outlook Page 2 of 5 4. If the "Account Setup Assistant" window displays, click "Configure account manually." Setting Up Your E-mail in Microsoft Outlook Page 3 of 5 5. Select POP for the account type and click OK. 6. On the Edit Account window, enter your information as follows: Account name Enter a name for your account, for example: My Mail, Work, or Home. Name Enter your first and last name. E-mail address Enter your e-mail address. Account ID Enter your e-mail address, again. POP server Enter pop.secureserver.net as your incoming server Password Enter the password for your e-mail account. SMTP server Enter smtpout.secureserver.net for your outgoing mail server. Click "Click here for more advanced sending options." NOTE: "smtpout.secureserver.net" is an SMTP relay server. In order to use this server to send e-mails, you must first activate SMTP relay on your e-mail account. Log on to your Manage Email Accounts page to set up SMTP relay. -

School and Email Systems
Email system survey: Top 50 US Colleges US Note Email system Server queried Greeting News School ranking 1 Harvard University Mail2World imap.college.harvard.edu OK Mail2World IMAP4 Server 2.5 ready Sun Java SMS imap.princeton.edu OK [CAPABILITY IMAP4 IMAP4rev1 ACL QUOTA LITERAL+ NAMESPACE UIDPLUS CHILDREN BINARY LANGUAGE XSENDER X-NETSCAPE XSERVERINFO Princeton University 1 AUTH=PLAIN] Messaging Multiplexor (Sun Java(tm) System Messaging Server 6.2-5.05 (built Feb 16 2006)) Unknown mail.yale.edu OK [CAPABILITY IMAP4REV1 LOGIN-REFERRALS AUTH=PLAIN AUTH=LOGIN] pantheon-po14.its.yale.edu IMAP4rev1 2002.336 at Mon, 26 Jul 2010 14:10:23 Yale University 3 -0400 (EDT) Dovecot imap-server.its.caltech.edu OK Dovecot ready. Cyrus mail.alumni.caltech.edu OK posteaux1.caltech.edu Cyrus IMAP4 v2.2.12-Invoca-RPM-2.2.12-10.el4_8.4 server ready 4 California Institute of Technology Dovecot imap.gps.caltech.edu OK dovecot ready. Dovecot theory.caltech.edu OK dovecot ready. 4 Massachusetts Institute of Technology Unable to find a server to query (username.mail.mit.edu)Unknown 4 Stanford University Zimbra zm01.stanford.edu OK zm01.stanford.edu Zimbra IMAP4rev1 server ready Zimbra mailbox.zimbra.upenn.edu OK mailbox.zimbra.upenn.edu Zimbra IMAP4rev1 service ready 4 University of Pennsylvania Exchange 2010 webmail.wharton.upenn.edu OK The Microsoft Exchange IMAP4 service is ready. Dovecot imap.nevis.columbia.edu OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE AUTH=PLAIN] Dovecot ready. Lotus Domino equinox.law.columbia.edu OK Domino IMAP4 -

Introduction
Introduction WHO THIS BOOK IS FOR There’s no question that you’ll get some good out of this WHY WE WROTE THIS BOOK book no matter how much of a Mac expert you are. DP: Everybody who’s ever worked Heck, even if you throw away the book, the accompany- with a Mac already knows that you ing 600 MB of spectacular software will make you discard a file by moving its icon to mighty glad you picked it up. the Trash can, that you select text by dragging across it, and that you end But we may as well admit that this book completely the day by choosing Shut Down skips over the basics of using a Macintosh. If you don’t from the Special menu.The world already know how to point and click, open windows, doesn’t need another book to define insert a disk, use a menu, and open a control panel, you scroll bar. should take a moment to play with the animated pro- JS: So when we started writing gram called either Mouse Practice or Macintosh Basics this book, we worked from one that came with your Mac. Read a manual. Read Macs For simple, overarching concept: Under Dummies, a really good beginner’s book from IDG no circumstances would we define Books (written by one of your present authors). Do scroll bar. whatever you have to do. DP: Instead, we decided to tell As a matter of fact, here are the terms we’re going to secrets: secrets about how a Mac really be tossing around without any definition: works, secrets that software program- Ô-key, Ú menu, backup copy, click, control panel, mers buried in programs but forgot to cursor, Delete key, desktop, double-click, File menu, tell the manual writer, secrets that floppy disk, folder, font, hard drive, icon, K (kilobyte), answer some of the most frequently keyboard, launch a program, MB (megabyte), menu, asked (and seldom answered) quest- ions about Macintosh computing, menu command, monitor, mouse, numeric keypad, secrets such as how to recover a file Option key, point, quit a program, Return key, spacebar, after you’ve dragged it to the Trash — scroll bar, System 7, title bar (of a window), Trash. -
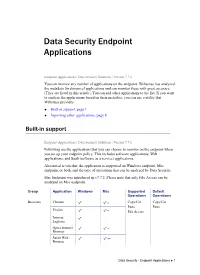
Data Security Endpoint Applications
Data Security Endpoint Applications Endpoint Applications | Data Security Solutions | Version 7.7.x You can monitor any number of applications on the endpoint. Websense has analyzed the metadata for dozens of applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 8 Built-in support Endpoint Applications | Data Security Solutions | Version 7.7.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy. This includes software applications, Web applications, and SaaS (software as a service) applications. Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by Data Security. Mac Endpoint was introduced in v7.7.2. Please note that only File Access can be analyzed on Mac endpoint. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome * Copy/Cut Copy/Cut Paste Paste Firefox * File Access Internet Explorer Opera Internet * Browser Safari Web ** Browser Data Security - Endpoint Applications 1 Data Security Endpoint Applications Group Application Windows Mac Supported Default Operations Operations CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility