Attribute-Based, Usefully Secure Email
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Hany Farid [email protected]
Hany Farid [email protected] APPOINTMENTS University of California, Berkeley 2019 – Professor, Electrical Engineering and Computer Sciences (50%) Professor, School of Information (50%) Member, Berkeley Artificial Intelligence Lab Member, Center for Innovation in Vision and Optics Member, Vision Science Program Dartmouth College, Department of Computer Science 1999 – 2019 Albert Bradley 1915 Third Century Professor 2016 – 2019 Professor 2011 – 2016 William H. Neukom 1964 Distinguished Professor of Computational Science 2008 – 2011 David T. McLaughlin Distinguished Professor of Computer Science 2007 – 2008 Professor 2006 – 2007 Associate Professor 2004 – 2006 Assistant Professor 1999 – 2004 Dartmouth College, Tuck School of Business 2016 – 2019 Adjunct Professor of Business Administration Dartmouth College, Neukom Institute for Computational Science 2008 – 2011 Director PROFESSIONAL AI Foundation 2019 – present Board of Directors & Global AI Council Center for Investigative Reporting 2020 – present Advisory Committee Counter Extremism Project 2016 – present Senior Advisor Cyber Civil Rights Initiative 2019 – present Advisory Committee Fourandsix Technologies, Inc. 2011 – 2018 Chief Technology Officer & Co-founder Human Rights Center, University of California, Berkeley, School of Law 2019 – present Advisory Board Office of the Prosecutor, International Criminal Court 2018 – present Technology Advisory Board TikTok 2020 – present Content Advisory Council Truepic, Inc. 2018 – present Senior Advisor & Board of Advisors EDUCATION Massachusetts Institute of Technology 1997 – 1999 Postdoctoral Fellow, Brain and Cognitive Sciences (advisor: Ted Adelson) University of Pennsylvania 1993 – 1997 Ph.D., Computer Science (advisor: Eero Simoncelli) State University of New York at Albany 1990 – 1992 M.S., Computer Science University of Rochester 1984 – 1988 B.S., Computer Science with Applied Mathematics AWARDS National Academy of Inventors (NAI), Fellow, 2016 John Simon Guggenheim Fellowship, 2006 Alfred P. -

ESSAY Untangling Attribution David D. Clark* and Susan Landau**
ESSAY Untangling Attribution David D. Clark* and Susan Landau** I. Introduction In February 2010, former Director of the National Security Agency Mike McConnell wrote, "We need to develop an early-warning system to monitor cyberspace, identify intrusions and locate the source of attacks with a trail of evidence that can support diplomatic, military and legal options and we must be able to do this in milliseconds. More specifically, we need to reengineer the Internet to make attribution, geolocation, intelligence analysis and impact assessment - who did it, from where, why and what was the result - more manageable."I The Internet was not designed with the goal of deterrence in mind, and perhaps a future Internet should be designed differently. McConnell's statement is part of a recurring theme that a secure Internet must provide better attribution for actions occurring on the network. Although attribution generally means assigning a cause to an action, as used here attribution refers to identifying the agent responsible for the action (specifically, "determining * David Clark, Senior Research Scientist, MIT, Cambridge MA 02139, ddc acsail.mit.edu. Clark's effort on this work was funded by the Office of Naval Research under award number N00014-08-1-0898. Any opinions, findings, and conclusions or recommendations expressed in this Essay are those of the authors and do not necessarily reflect the views of the Office of Naval Research. " Susan Landau, Fellow, Radcliffe Institute for Advanced Study, Harvard University, Cambridge, MA 02138, susan.landau(a) rivacvink.oru. An earlier version of this Essay appeared in COMMI. ON DLTLRRING CYBERATTACKS, NAT'L RLSLARCH COUNCIL, PROCELDINGS OF A WORKSHOP ON DLTLRRING CYBLRATTACKS: INFORMING STRATEGILS AND DLVLLOPING OPTIONS FOR U.S. -

Pgpfone Pretty Good Privacy Phone Owner’S Manual Version 1.0 Beta 7 -- 8 July 1996
Phil’s Pretty Good Software Presents... PGPfone Pretty Good Privacy Phone Owner’s Manual Version 1.0 beta 7 -- 8 July 1996 Philip R. Zimmermann PGPfone Owner’s Manual PGPfone Owner’s Manual is written by Philip R. Zimmermann, and is (c) Copyright 1995-1996 Pretty Good Privacy Inc. All rights reserved. Pretty Good Privacy™, PGP®, Pretty Good Privacy Phone™, and PGPfone™ are all trademarks of Pretty Good Privacy Inc. Export of this software may be restricted by the U.S. government. PGPfone software is (c) Copyright 1995-1996 Pretty Good Privacy Inc. All rights reserved. Phil’s Pretty Good engineering team: PGPfone for the Apple Macintosh and Windows written mainly by Will Price. Phil Zimmermann: Overall application design, cryptographic and key management protocols, call setup negotiation, and, of course, the manual. Will Price: Overall application design. He persuaded the rest of the team to abandon the original DOS command-line approach and designed a multithreaded event-driven GUI architecture. Also greatly improved call setup protocols. Chris Hall: Did early work on call setup protocols and cryptographic and key management protocols, and did the first port to Windows. Colin Plumb: Cryptographic and key management protocols, call setup negotiation, and the fast multiprecision integer math package. Jeff Sorensen: Speech compression. Will Kinney: Optimization of GSM speech compression code. Kelly MacInnis: Early debugging of the Win95 version. Patrick Juola: Computational linguistic research for biometric word list. -2- PGPfone Owner’s -

School and Email Systems
Email system survey: Top 50 US Colleges US Note Email system Server queried Greeting News School ranking 1 Harvard University Mail2World imap.college.harvard.edu OK Mail2World IMAP4 Server 2.5 ready Sun Java SMS imap.princeton.edu OK [CAPABILITY IMAP4 IMAP4rev1 ACL QUOTA LITERAL+ NAMESPACE UIDPLUS CHILDREN BINARY LANGUAGE XSENDER X-NETSCAPE XSERVERINFO Princeton University 1 AUTH=PLAIN] Messaging Multiplexor (Sun Java(tm) System Messaging Server 6.2-5.05 (built Feb 16 2006)) Unknown mail.yale.edu OK [CAPABILITY IMAP4REV1 LOGIN-REFERRALS AUTH=PLAIN AUTH=LOGIN] pantheon-po14.its.yale.edu IMAP4rev1 2002.336 at Mon, 26 Jul 2010 14:10:23 Yale University 3 -0400 (EDT) Dovecot imap-server.its.caltech.edu OK Dovecot ready. Cyrus mail.alumni.caltech.edu OK posteaux1.caltech.edu Cyrus IMAP4 v2.2.12-Invoca-RPM-2.2.12-10.el4_8.4 server ready 4 California Institute of Technology Dovecot imap.gps.caltech.edu OK dovecot ready. Dovecot theory.caltech.edu OK dovecot ready. 4 Massachusetts Institute of Technology Unable to find a server to query (username.mail.mit.edu)Unknown 4 Stanford University Zimbra zm01.stanford.edu OK zm01.stanford.edu Zimbra IMAP4rev1 server ready Zimbra mailbox.zimbra.upenn.edu OK mailbox.zimbra.upenn.edu Zimbra IMAP4rev1 service ready 4 University of Pennsylvania Exchange 2010 webmail.wharton.upenn.edu OK The Microsoft Exchange IMAP4 service is ready. Dovecot imap.nevis.columbia.edu OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE AUTH=PLAIN] Dovecot ready. Lotus Domino equinox.law.columbia.edu OK Domino IMAP4 -

Digital Forensics and Preservation 1
01000100 01010000 Digital 01000011 Forensics 01000100 and Preservation 01010000 Jeremy Leighton John 01000011 01000100 DPC Technology Watch Report 12-03 November 2012 01010000 01000011 01000100 01010000 Series editors on behalf of the DPC 01000011 Charles Beagrie Ltd. Principal Investigator for the Series 01000100 Neil Beagrie 01010000 01000011DPC Technology Watch Series © Digital Preservation Coalition 2012 and Jeremy Leighton John 2012 Published in association with Charles Beagrie Ltd. ISSN: 2048-7916 DOI: http://dx.doi.org/10.7207/twr12-03 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, without the prior permission in writing from the publisher. The moral right of the author has been asserted. First published in Great Britain in 2012 by the Digital Preservation Coalition. Foreword The Digital Preservation Coalition (DPC) is an advocate and catalyst for digital preservation, ensuring our members can deliver resilient long-term access to digital content and services. It is a not-for- profit membership organization whose primary objective is to raise awareness of the importance of the preservation of digital material and the attendant strategic, cultural and technological issues. It supports its members through knowledge exchange, capacity building, assurance, advocacy and partnership. The DPC’s vision is to make our digital memory accessible tomorrow. The DPC Technology Watch Reports identify, delineate, monitor and address topics that have a major bearing on ensuring our collected digital memory will be available tomorrow. They provide an advanced introduction in order to support those charged with ensuring a robust digital memory, and they are of general interest to a wide and international audience with interests in computing, information management, collections management and technology. -

Fall 2003 Class News by Michelle Sweetser I Hope Everyone Had a Good Summer! It’S Been a Crazy Fall Here in Ann Arbor As I Wrap up Classes and Begin the Job Search
Alma Matters The Class of 1999 Newsletter Fall 2003 Class News by Michelle Sweetser I hope everyone had a good summer! It’s been a crazy fall here in Ann Arbor as I wrap up classes and begin the job search. I have no idea where I’ll be after December - maybe in your area! It’s both frightening and exciting. This being the first newslet- ter after the summer wedding sea- son, expect to read about a number of marriages in the coming pages. West The first of the marriage an- nouncements is that of Christopher Rea and Julie Ming Wang, who mar- ried on June 2 in Yosemite National Park. In attendance were Russell Talbot, Austin Whitman, Jessica Reiser ’97, Jon Rivinus, Christian Bennett, Genevieve Bennett ’97, Pete Land and Wendy Pabich '88 stop to pose in front of the the Jennifer Mui, and Stephen Lee. Bremner Glacier and the Chugach Mountains in Wrangell - St. The couple honeymooned in Greece Elias National Park, Alaska. Wendy and Pete were there working and are now living in New York City. as consultants for the Wild Gift, a new fellowship program for Both Cate Mowell and environmental students that includes a three-week trek through the Alaskan wilderness. Caroline Kaufmann wrote in about Anna Kate Deutschendorf’s beau- tiful wedding to Jaimie Hutter ’96 in Aspen. It was Cate quit her job at Nicole Miller in August a reportedly perfect, cool, sunny day, and the touch- and is enjoying living at the beach in Santa Monica, ing ceremony took place in front of a gorgeous view CA. -

Design Principles and Patterns for Computer Systems That Are
Bibliography [AB04] Tom Anderson and David Brady. Principle of least astonishment. Ore- gon Pattern Repository, November 15 2004. http://c2.com/cgi/wiki? PrincipleOfLeastAstonishment. [Acc05] Access Data. Forensic toolkit—overview, 2005. http://www.accessdata. com/Product04_Overview.htm?ProductNum=04. [Adv87] Display ad 57, February 8 1987. [Age05] US Environmental Protection Agency. Wastes: The hazardous waste mani- fest system, 2005. http://www.epa.gov/epaoswer/hazwaste/gener/ manifest/. [AHR05a] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Fighting Phishing Attacks: A Lightweight Trust Architecture for Detecting Spoofed Emails (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AHR05b] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Separable Identity- Based Ring Signatures: Theoretical Foundations For Fighting Phishing Attacks (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AIS77] Christopher Alexander, Sara Ishikawa, and Murray Silverstein. A Pattern Lan- guage: towns, buildings, construction. Oxford University Press, 1977. (with Max Jacobson, Ingrid Fiksdahl-King and Shlomo Angel). [AKM+93] H. Alvestrand, S. Kille, R. Miles, M. Rose, and S. Thompson. RFC 1495: Map- ping between X.400 and RFC-822 message bodies, August 1993. Obsoleted by RFC2156 [Kil98]. Obsoletes RFC987, RFC1026, RFC1138, RFC1148, RFC1327 [Kil86, Kil87, Kil89, Kil90, HK92]. Status: PROPOSED STANDARD. [Ale79] Christopher Alexander. The Timeless Way of Building. Oxford University Press, 1979. 429 430 BIBLIOGRAPHY [Ale96] Christopher Alexander. Patterns in architecture [videorecording], October 8 1996. Recorded at OOPSLA 1996, San Jose, California. [Alt00] Steven Alter. Same words, different meanings: are basic IS/IT concepts our self-imposed Tower of Babel? Commun. AIS, 3(3es):2, 2000. -

Hurricane Football
ACCENT SPORTS INSIDE NEWS: Miami Herald • The UM Ring • The 12th-ranked Miami investigative journalists _*&£ Hurricanes look to rebound from Jeff Leen and Don Van Theatre's latest Natta spoke to students production is a their disappointing Orange Bowl Wednesday morning. smashing success. loss against a high-powered Page 4 •£__fl_]__5? Rutgers offense. OPINION: Is "Generation X" a Page 8 PaaelO misnomer? Pago 6 MlVEfftlTY OF •II •! _ - SEP 3 01994 BEJERVE W$t jWiamt hurricane VOLUME 72, NUMBER 9 CORAL GABLES, FLA. FRIDAY. SEPTEMBER 30. 1994 Erws Elections Commission improves voting process ByCOMJANCKO According to Commissioner-at- students will be allowed to cam make voting more convenient, and Large Jordan Schwartsberg, the paign." Office of Registrar Records in the BRIEFS Hurricane Staff Writer increase the total voter turnout. Ashe Building, room 249. Student Government has made Elections Commission is working The elections will be held Oct. In the past, approximately 500 to changes in the way elections will be to make the election system run 24 to 26. Students will vote on 600 students out of a total 8,000 RAT MASCOT run and how students will vote. smoothly. computers in the residential col on campus voted in the elections. The senate positions for each of The Elections Commission, a "To help make the campaigning leges and in computer labs. To vote, students need to pick up the residence halls, the Apartment NAMED AT PROMO easier for the candidates, we plan Last year students travelled to branch of SG, appoint commission their Personal Identification Num Area, Fraternity Row, Commuter ers for one-year terms to plan and to make many of the regulations the specific voting booths around North, Commuter Central, and The Rathskeller Advisory Board implement the logistics of elec clearer," Schwartsberg said. -

(Literary) Special Effect: (Inter)Mediality in the Contemporary US-American Novel and the Digital Age
The (Literary) Special Effect: (Inter)Mediality in the Contemporary US-American Novel and the Digital Age Dissertation zur Erlangung des philosophischen Doktorgrades an der Philosophischen Fakultät der Georg-August-Universität Göttingen vorgelegt von Bogna Kazur aus Lodz, Polen Göttingen 2018 Contents 1 Introduction ......................................................................................................................... 3 2 The Question of Medium Specificity in the Digital Age .................................................. 29 3 House of Leaves (2000) and the Uncanny Dawn of the Digital........................................ 39 3.1 Digital Paranoia: Arriving on Ash Tree Lane ........................................................... 39 3.2 Writing about House of Leaves ................................................................................. 43 3.3 Intermedial Overabundance: Taming House of Leaves ............................................. 49 3.4 An “Explicit” Approach to the Digital Age ............................................................... 54 3.5 What Kind of Movie is THE NAVIDSON RECORD? ..................................................... 68 4 In the Midst of the Post-Cinematic Age: Marisha Pessl’s Night Film (2013) .................. 88 4.1 Meant for Adaptation: Night Film and the Fallacy of First Impressions ................... 88 4.2 The Post-Cinematic Reception of Film ..................................................................... 96 4.3 The Last Enigma: Cordova’s Underworld .............................................................. -
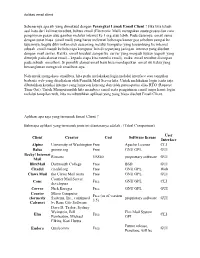
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

Final Report University of Maryland Student Email
FINAL REPORT UNIVERSITY OF MARYLAND STUDENT EMAIL COMMITTEE May 15, 2011 COMMITTEE MEMBERS Michael Ball, Smith School of Business, Prof & Assoc Dean (Chair) David Barks, OIT-TSS-Enterprise Internet Svcs, Manager (non-voting) Patrick Beasley, Alumni Association, Assistant Director of Technology Anne Bowden, President’s Office, University Counsel (non-voting) Bill Dorland, Undergraduate Studies - Honors College, Prof & Director Allison Druin, iSchool, Associate Dean Jeff McKinney, Electrical and Computer Eng, Director of Computer Services Dan Navarro, BSOS, Director of Academic Computing Services Dai-An Tran, Student Affairs Resident Life, Assistant Director Amitabh Varshney, Institute for Advanced Computer Studies, Prof & Director Luigi Alvarado, Grad Student Zach Cohen, Student – BSOS, Legislator SGA Mariela Garcia Colberg, Grad student Jacob Crider, Student – ARHU, Legislator SGA Tomek Kott, Grad Student Elizabeth Moran, Student, Smith School of Business, Legislator SGA Morgan Parker, Student, CMPS Legislator SGA Background In the Fall of 2010, the University’s Office of Information Technology (OIT) examined alternatives for providing student email services in the 2011-2012 academic year and beyond. This examination was motivated by several factors, including these prominent two: • the existing Mirapoint-based system was outdated and in need of hardware and software upgrades; • there were many attractive competing alternatives. OIT investigated this issue. Their investigation included a survey of students and also an identification and analysis of several alternatives. Their report to the University IT Council is attached (Appendix 1). The OIT analysis found that a number of important non-technical issues, including privacy and security concerns, should be taken into account in making this decision. Therefore, it was recommended that a campus-wide committee be formed to address this issue. -

Jason I. Hong
Jason I. Hong Human Computer Interaction Institute Office: +1 412 268 1251 School of Computer Science Fax: +1 412 268 1266 Carnegie Mellon University Email: jasonh at cs cmu edu 5000 Forbes Ave Web: http://www.cs.cmu.edu/~jasonh 3523 Newell Simon Hall GScholar: https://scholar.google.com/citations?user=MoFbcc0AAAAJ Pittsburgh, PA 15213‐3891 Citizenship: USA ORCID: http://orcid.org/0000‐0002‐9856‐9654 Research Interests In the near future, our smart devices will know almost everything about us. How can we make use of all of this rich sensor and behavioral data to improve our lives? At the same time, this same data poses many new kinds of risks. How can we make privacy and security easily understandable by people who are not experts? How can we ensure that machine learning models built on this data is fair, accountable, transparent, and ethical? In my research, I draw on ideas and methods from human‐computer interaction, systems, behavioral sciences, and machine learning. Most of my current work centers on smartphones and the emerging Internet of Things. I also make use of data from crowdsourcing or social media, both to better understand people’s behaviors as well as to “outsource” the labor required to manage privacy and security. Education 2005 Ph.D., Computer Science, University of California at Berkeley Advisor: James Landay Thesis topic: An Architecture for Privacy‐Sensitive Ubiquitous Computing 1997 B.S., Discrete Mathematics, Georgia Institute of Technology Highest honors 1997 B.S., Computer Science, Georgia Institute of Technology