Tips for Survivors of High-Tech Abuse and Stalking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS 8 Update
K Service Source Mac OS 8 Update Known problems, Internet Access, and Installation Mac OS 8 Update Document Contents - 1 Document Contents • Introduction • About Mac OS 8 • About Internet Access What To Do First Additional Software Auto-Dial and Auto-Disconnect Settings TCP/IP Connection Options and Internet Access Length of Configuration Names Modem Scripts & Password Length Proxies and Other Internet Config Settings Web Browser Issues Troubleshooting • About Mac OS Runtime for Java Version 1.0.2 • About Mac OS Personal Web Sharing • Installing Mac OS 8 • Upgrading Workgroup Server 9650 & 7350 Software Mac OS 8 Update Introduction - 2 Introduction Mac OS 8 is the most significant update to the Macintosh operating system since 1984. The updated system gives users PowerPC-native multitasking, an efficient desktop with new pop-up windows and spring-loaded folders, and a fully integrated suite of Internet services. This document provides information about Mac OS 8 that supplements the information in the Mac OS installation manual. For a detailed description of Mac OS 8, useful tips for using the system, troubleshooting, late-breaking news, and links for online technical support, visit the Mac OS Info Center at http://ip.apple.com/infocenter. Or browse the Mac OS 8 topic in the Apple Technical Library at http:// tilsp1.info.apple.com. Mac OS 8 Update About Mac OS 8 - 3 About Mac OS 8 Read this section for information about known problems with the Mac OS 8 update and possible solutions. Known Problems and Compatibility Issues Apple Language Kits and Mac OS 8 Apple's Language Kits require an updater for full functionality with this version of the Mac OS. -

Volume 4, Number 7 July 1, 1998 [email protected]
About This Particular Macintosh™ 4.07: About the personal computing experience™ Volume 4, Number 7 July 1, 1998 Send requests for free subscriptions to: [email protected] Cover Art ©1998 Jamal Ghandour <[email protected]> We need new cover art every month! Write to us! Contributors Scott R. Boveia Scott Byers Martin Cox Simon Edison Jamal Ghandour Edward Goss [email protected] Tom Iovino Staci Trekles Robert Paul Leitao Robert Madill Mike Shields Michael Tsai Marc Zeedar Macintosh users like you Please write for ATPM! Check out the Guidelines Editorial Staff Publishers - Michael Tsai & Robert Paul Leitao Editor - Michael Tsai Managing Editor - Robert Paul Leitao Opinionated Associate Editor - Mike Shields Reviews Editor- Robert Madill Copy Editor - Christopher Turner Shareware Reviews Editor - Vacant Interviews Manager - Vacant Publicity Manager - Kyle Alexander Page o’ Linker - Vacant Welcome Author - Robert Paul Leitao List Server Manager - Michael Tsai Webzingers - Michael Tsai, Evan Trent Beta Testers - The Staff Columnists Jamal Ghandour Edward Goss Tom Iovino Robert Paul Leitao Mike Shields Michael Tsai Artwork & Design Graphics Director - Jamal Ghandour Layout/Design - Michael Tsai Blue Apple Icon Designs - Marc Robinson Typewriter-Style Section Headers - RD Novo The Tools Anarchie AppleWorks BBEdit DOCMaker Emailer Illustrator Kai’s PowerTools LetterRip Myrmidon Nisus Writer Online Army Knife Photoshop ResEdit Snapz Pro StuffIt The Fonts Carbonated Gothic Cheltenham Cloister Foundation Frutiger Garamond Geneva Gill Sans Helvetica Isla Bella Marydale Where to Find ATPM Online and downloadable issues are available at the ATPM Web Page: < h t t p : / / w w w . a t p m . c o m > and via anonymous FTP at: < f t p : / / f t p . -

School and Email Systems
Email system survey: Top 50 US Colleges US Note Email system Server queried Greeting News School ranking 1 Harvard University Mail2World imap.college.harvard.edu OK Mail2World IMAP4 Server 2.5 ready Sun Java SMS imap.princeton.edu OK [CAPABILITY IMAP4 IMAP4rev1 ACL QUOTA LITERAL+ NAMESPACE UIDPLUS CHILDREN BINARY LANGUAGE XSENDER X-NETSCAPE XSERVERINFO Princeton University 1 AUTH=PLAIN] Messaging Multiplexor (Sun Java(tm) System Messaging Server 6.2-5.05 (built Feb 16 2006)) Unknown mail.yale.edu OK [CAPABILITY IMAP4REV1 LOGIN-REFERRALS AUTH=PLAIN AUTH=LOGIN] pantheon-po14.its.yale.edu IMAP4rev1 2002.336 at Mon, 26 Jul 2010 14:10:23 Yale University 3 -0400 (EDT) Dovecot imap-server.its.caltech.edu OK Dovecot ready. Cyrus mail.alumni.caltech.edu OK posteaux1.caltech.edu Cyrus IMAP4 v2.2.12-Invoca-RPM-2.2.12-10.el4_8.4 server ready 4 California Institute of Technology Dovecot imap.gps.caltech.edu OK dovecot ready. Dovecot theory.caltech.edu OK dovecot ready. 4 Massachusetts Institute of Technology Unable to find a server to query (username.mail.mit.edu)Unknown 4 Stanford University Zimbra zm01.stanford.edu OK zm01.stanford.edu Zimbra IMAP4rev1 server ready Zimbra mailbox.zimbra.upenn.edu OK mailbox.zimbra.upenn.edu Zimbra IMAP4rev1 service ready 4 University of Pennsylvania Exchange 2010 webmail.wharton.upenn.edu OK The Microsoft Exchange IMAP4 service is ready. Dovecot imap.nevis.columbia.edu OK [CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE AUTH=PLAIN] Dovecot ready. Lotus Domino equinox.law.columbia.edu OK Domino IMAP4 -

Introduction
Introduction WHO THIS BOOK IS FOR There’s no question that you’ll get some good out of this WHY WE WROTE THIS BOOK book no matter how much of a Mac expert you are. DP: Everybody who’s ever worked Heck, even if you throw away the book, the accompany- with a Mac already knows that you ing 600 MB of spectacular software will make you discard a file by moving its icon to mighty glad you picked it up. the Trash can, that you select text by dragging across it, and that you end But we may as well admit that this book completely the day by choosing Shut Down skips over the basics of using a Macintosh. If you don’t from the Special menu.The world already know how to point and click, open windows, doesn’t need another book to define insert a disk, use a menu, and open a control panel, you scroll bar. should take a moment to play with the animated pro- JS: So when we started writing gram called either Mouse Practice or Macintosh Basics this book, we worked from one that came with your Mac. Read a manual. Read Macs For simple, overarching concept: Under Dummies, a really good beginner’s book from IDG no circumstances would we define Books (written by one of your present authors). Do scroll bar. whatever you have to do. DP: Instead, we decided to tell As a matter of fact, here are the terms we’re going to secrets: secrets about how a Mac really be tossing around without any definition: works, secrets that software program- Ô-key, Ú menu, backup copy, click, control panel, mers buried in programs but forgot to cursor, Delete key, desktop, double-click, File menu, tell the manual writer, secrets that floppy disk, folder, font, hard drive, icon, K (kilobyte), answer some of the most frequently keyboard, launch a program, MB (megabyte), menu, asked (and seldom answered) quest- ions about Macintosh computing, menu command, monitor, mouse, numeric keypad, secrets such as how to recover a file Option key, point, quit a program, Return key, spacebar, after you’ve dragged it to the Trash — scroll bar, System 7, title bar (of a window), Trash. -

Emailer and a Review of Owen Linzmayer's Book, the Mac Bathroom Reader
to About Thiiis Partiiiculllar Maciiintosh® 1.06 September 6th, 1995 WELCOME TO THE six-month mark, celebrated in brand-new relationships, brand-new puppies, and brand-new publications. ATPM has been continuously published for six months. Yowza, indeed. Yes, the changes have slowed. You'll note only a few, minor changes from the last issue of ATPM to this one. A by-line here, a title tweak there. You see, I got that job I was looking for, and I've gone and lost almost all of the free time in which I used to write the magazine. But do not despair, faithful readers. ATPM is reaching the point where it can begin to publish itself. Sort of. Roughly speaking, ten percent of this issue was written by someone other than myself, and that means less time required of me for each issue. Ultimately, this will lead to a broader, more timely publication. I hope. If you're interested in helping, let me know how. Whatever you do, please do continue to write and submit your work. See the endnotes. In this issue you'll find an evolution of last month's news column: a regular feature called AppleSauce. Now, that's not sauce as in "saucy," but rather sauce as in... well... you'll see. This month's issue also features a review of Claris Emailer and a review of Owen Linzmayer's book, The Mac Bathroom Reader. In addition, the new shareware reviews debut with a contribution from Brian Bergstrand (I hope he'll write for ATPM again). -

Fall 2003 Class News by Michelle Sweetser I Hope Everyone Had a Good Summer! It’S Been a Crazy Fall Here in Ann Arbor As I Wrap up Classes and Begin the Job Search
Alma Matters The Class of 1999 Newsletter Fall 2003 Class News by Michelle Sweetser I hope everyone had a good summer! It’s been a crazy fall here in Ann Arbor as I wrap up classes and begin the job search. I have no idea where I’ll be after December - maybe in your area! It’s both frightening and exciting. This being the first newslet- ter after the summer wedding sea- son, expect to read about a number of marriages in the coming pages. West The first of the marriage an- nouncements is that of Christopher Rea and Julie Ming Wang, who mar- ried on June 2 in Yosemite National Park. In attendance were Russell Talbot, Austin Whitman, Jessica Reiser ’97, Jon Rivinus, Christian Bennett, Genevieve Bennett ’97, Pete Land and Wendy Pabich '88 stop to pose in front of the the Jennifer Mui, and Stephen Lee. Bremner Glacier and the Chugach Mountains in Wrangell - St. The couple honeymooned in Greece Elias National Park, Alaska. Wendy and Pete were there working and are now living in New York City. as consultants for the Wild Gift, a new fellowship program for Both Cate Mowell and environmental students that includes a three-week trek through the Alaskan wilderness. Caroline Kaufmann wrote in about Anna Kate Deutschendorf’s beau- tiful wedding to Jaimie Hutter ’96 in Aspen. It was Cate quit her job at Nicole Miller in August a reportedly perfect, cool, sunny day, and the touch- and is enjoying living at the beach in Santa Monica, ing ceremony took place in front of a gorgeous view CA. -

Hurricane Football
ACCENT SPORTS INSIDE NEWS: Miami Herald • The UM Ring • The 12th-ranked Miami investigative journalists _*&£ Hurricanes look to rebound from Jeff Leen and Don Van Theatre's latest Natta spoke to students production is a their disappointing Orange Bowl Wednesday morning. smashing success. loss against a high-powered Page 4 •£__fl_]__5? Rutgers offense. OPINION: Is "Generation X" a Page 8 PaaelO misnomer? Pago 6 MlVEfftlTY OF •II •! _ - SEP 3 01994 BEJERVE W$t jWiamt hurricane VOLUME 72, NUMBER 9 CORAL GABLES, FLA. FRIDAY. SEPTEMBER 30. 1994 Erws Elections Commission improves voting process ByCOMJANCKO According to Commissioner-at- students will be allowed to cam make voting more convenient, and Large Jordan Schwartsberg, the paign." Office of Registrar Records in the BRIEFS Hurricane Staff Writer increase the total voter turnout. Ashe Building, room 249. Student Government has made Elections Commission is working The elections will be held Oct. In the past, approximately 500 to changes in the way elections will be to make the election system run 24 to 26. Students will vote on 600 students out of a total 8,000 RAT MASCOT run and how students will vote. smoothly. computers in the residential col on campus voted in the elections. The senate positions for each of The Elections Commission, a "To help make the campaigning leges and in computer labs. To vote, students need to pick up the residence halls, the Apartment NAMED AT PROMO easier for the candidates, we plan Last year students travelled to branch of SG, appoint commission their Personal Identification Num Area, Fraternity Row, Commuter ers for one-year terms to plan and to make many of the regulations the specific voting booths around North, Commuter Central, and The Rathskeller Advisory Board implement the logistics of elec clearer," Schwartsberg said. -

Attribute-Based, Usefully Secure Email
Dartmouth College Dartmouth Digital Commons Dartmouth College Ph.D Dissertations Theses and Dissertations 8-1-2008 Attribute-Based, Usefully Secure Email Christopher P. Masone Dartmouth College Follow this and additional works at: https://digitalcommons.dartmouth.edu/dissertations Part of the Computer Sciences Commons Recommended Citation Masone, Christopher P., "Attribute-Based, Usefully Secure Email" (2008). Dartmouth College Ph.D Dissertations. 26. https://digitalcommons.dartmouth.edu/dissertations/26 This Thesis (Ph.D.) is brought to you for free and open access by the Theses and Dissertations at Dartmouth Digital Commons. It has been accepted for inclusion in Dartmouth College Ph.D Dissertations by an authorized administrator of Dartmouth Digital Commons. For more information, please contact [email protected]. Attribute-Based, Usefully Secure Email A Thesis Submitted to the Faculty in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science by Christopher P. Masone DARTMOUTH COLLEGE Hanover, New Hampshire August, 2008 Examining Committee: (chair) Sean W. Smith, Ph.D. David F. Kotz, Ph.D. Christopher J. Bailey-Kellogg, Ph.D. Denise L. Anthony, Ph.D. M. Angela Sasse, Ph.D. Charles K. Barlowe, PhD Dean of Graduate Studies Abstract A secure system that cannot be used by real users to secure real-world processes is not really secure at all. While many believe that usability and security are diametrically opposed, a growing body of research from the field of Human-Computer Interaction and Security (HCISEC) refutes this assumption. All researchers in this field agree that focusing on aligning usability and security goals can enable the design of systems that will be more secure under actual usage. -

Spamsieve 2.1.4 Manual
SpamSieve 2.1.4 Manual Michael Tsai c-command.com April 15, 2004 Contents 1 Introduction 6 1.1 What Is SpamSieve? ............................... 6 1.2 Identifying Spam ................................. 6 1.3 Integration ..................................... 7 1.4 Main Features ................................... 8 1.5 Why Choose SpamSieve? ............................. 9 2 Installing and Updating 10 2.1 Requirements ................................... 10 2.2 Updating From a Previous Version ....................... 11 2.3 Installing SpamSieve ............................... 11 2.4 Uninstalling SpamSieve .............................. 11 3 Using SpamSieve With Your E-Mail Client 12 3.1 Apple Mail .................................... 13 3.1.1 Installing on Mac OS X 10.3.x ...................... 13 3.1.2 Installing on Mac OS X 10.2.x ...................... 14 3.1.3 Training SpamSieve ............................ 16 3.1.4 Manually Processing Messages ...................... 16 3.2 Emailer ...................................... 17 3.2.1 Installing ................................. 17 3.2.2 Training SpamSieve ............................ 19 3.2.3 Manually Processing Messages ...................... 19 3.3 Entourage ..................................... 19 3.3.1 Installing ................................. 19 3.3.2 Training SpamSieve ............................ 21 3.3.3 Manually Processing Messages ...................... 22 3.3.4 IMAP Accounts .............................. 22 3.3.5 Advanced Rules .............................. 22 3.4 Eudora 6 -
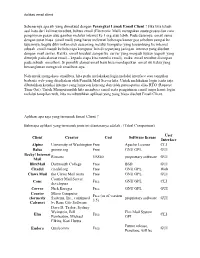
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

Final Report University of Maryland Student Email
FINAL REPORT UNIVERSITY OF MARYLAND STUDENT EMAIL COMMITTEE May 15, 2011 COMMITTEE MEMBERS Michael Ball, Smith School of Business, Prof & Assoc Dean (Chair) David Barks, OIT-TSS-Enterprise Internet Svcs, Manager (non-voting) Patrick Beasley, Alumni Association, Assistant Director of Technology Anne Bowden, President’s Office, University Counsel (non-voting) Bill Dorland, Undergraduate Studies - Honors College, Prof & Director Allison Druin, iSchool, Associate Dean Jeff McKinney, Electrical and Computer Eng, Director of Computer Services Dan Navarro, BSOS, Director of Academic Computing Services Dai-An Tran, Student Affairs Resident Life, Assistant Director Amitabh Varshney, Institute for Advanced Computer Studies, Prof & Director Luigi Alvarado, Grad Student Zach Cohen, Student – BSOS, Legislator SGA Mariela Garcia Colberg, Grad student Jacob Crider, Student – ARHU, Legislator SGA Tomek Kott, Grad Student Elizabeth Moran, Student, Smith School of Business, Legislator SGA Morgan Parker, Student, CMPS Legislator SGA Background In the Fall of 2010, the University’s Office of Information Technology (OIT) examined alternatives for providing student email services in the 2011-2012 academic year and beyond. This examination was motivated by several factors, including these prominent two: • the existing Mirapoint-based system was outdated and in need of hardware and software upgrades; • there were many attractive competing alternatives. OIT investigated this issue. Their investigation included a survey of students and also an identification and analysis of several alternatives. Their report to the University IT Council is attached (Appendix 1). The OIT analysis found that a number of important non-technical issues, including privacy and security concerns, should be taken into account in making this decision. Therefore, it was recommended that a campus-wide committee be formed to address this issue. -

Instalación Y Administración De Servicios De Correo Electrónico
Servicios de red e internet Instalación y administración de servicios de correo electrónico Raquel Castellanos Crespo Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo INDICE Características del servicio de correo electrónico Elementos del servicio de correo electrónico -Agentes de correo electrónico. - Servidores de correo electrónico. Open relay y Smart host - Clientes de correo electrónico: entorno-DOS, gráficos y navegadores. - Direcciones, cuentas de correo y servidores DNS - Protocolos y servicios de descarga de correo: SMPT, ESMTP, POP, IMAP. Funcionamiento del servicio de correo electrónico Cuentas de correo, alias y buzones de correo Estructura de mensajes de correo electrónico - Cabecera, cuerpo, MIME Monitorización y registros del servicio de correo electrónico Servicio de correo electrónico vía web Correo seguro - Firma digital y cifrado de mensajes Veracidad del correo - Correo basura ("SPAM”) fraude, engaño, cadenas y virus informáticos 2 Servicios de red e internet | Instalación y administración de servicios de correo electrónico Servicios de red e internet Raquel Castellanos Crespo Características del servicio de correo electrónico Correo electrónico (correo-e, conocido también como e-mail ), es un servicio de red que permite a los usuarios enviar y recibir mensajes y archivos rápidamente (también denominados mensajes electrónicos o cartas electrónicas) mediante sistemas de comunicación electrónicos. Principalmente se usa este nombre para denominar al sistema que provee este servicio en Internet, mediante el protocolo SMTP, aunque por extensión también puede verse aplicado a sistemas análogos que usen otras tecnologías. Por medio de mensajes de correo electrónico se puede enviar, no solamente texto, sino todo tipo de documentos digitales.