American National Standard Pascal Computer Programming Language
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vcf Pnw 2019
VCF PNW 2019 http://vcfed.org/vcf-pnw/ Schedule Saturday 10:00 AM Museum opens and VCF PNW 2019 starts 11:00 AM Erik Klein, opening comments from VCFed.org Stephen M. Jones, opening comments from Living Computers:Museum+Labs 1:00 PM Joe Decuir, IEEE Fellow, Three generations of animation machines: Atari and Amiga 2:30 PM Geoff Pool, From Minix to GNU/Linux - A Retrospective 4:00 PM Chris Rutkowski, The birth of the Business PC - How volatile markets evolve 5:00 PM Museum closes - come back tomorrow! Sunday 10:00 AM Day two of VCF PNW 2019 begins 11:00 AM John Durno, The Lost Art of Telidon 1:00 PM Lars Brinkhoff, ITS: Incompatible Timesharing System 2:30 PM Steve Jamieson, A Brief History of British Computing 4:00 PM Presentation of show awards and wrap-up Exhibitors One of the defining attributes of a Vintage Computer Festival is that exhibits are interactive; VCF exhibitors put in an amazing amount of effort to not only bring their favorite pieces of computing history, but to make them come alive. Be sure to visit all of them, ask questions, play, learn, take pictures, etc. And consider coming back one day as an exhibitor yourself! Rick Bensene, Wang Laboratories’ Electronic Calculators, An exhibit of Wang Labs electronic calculators from their first mass-market calculator, the Wang LOCI-2, through the last of their calculators, the C-Series. The exhibit includes examples of nearly every series of electronic calculator that Wang Laboratories sold, unusual and rare peripheral devices, documentation, and ephemera relating to Wang Labs calculator business. -

Chapter 1 a Mistake.” Wang Qishan, Mayor of Beijing Introduction
c01:chapter-01 10/6/2010 10:43 PM Page 3 ““No one can avoid making a mistake, but one should not repeat Chapter 1 a mistake.” Wang Qishan, Mayor of Beijing Introduction The quotation that opens this chapter, which appeared in a popular Beijing newspaper, is very telling about life in China today. Years ago, one would not admit to having made a mistake, as there could be serious consequences. Today, as Chinese thinking merges more and more with that of the West, it is becoming more common to admit to one’s mistakes. But the long-held fear of being wrong continues, as the second part of the quotation indicates. It is okay to be wrong about something once, but not twice. In China, one works very hard to be right. Sometimes, to avoid being wrong, a Chinese person will choose not to act. This topic takes us to the subject of business leadership. What does it take to be a great leader in China? What is different about leadership in China compared to elsewhere in the world? Leadership is a huge issue for businesses in China, especially today. This book is intended to provide answers to those questions, as well as to outline what companies in China—both foreign and local firms—canCOPYRIGHTED do now to improve the abilitiesMATERIAL of their leaders. Thousands of books have been written on business leadership. Many of these have been translated into Chinese and have been read by Chinese business people. China has an enormous need to improve the quality of its leadership, and its current and future leaders have a craving for information that will help them get to the top. -

Wang Laboratories 2200 Series
C21-908-101 Programmable Terminals Wang Laboratories 2200 Series MANAGEMENT SUMMARY A series of five minicomputer systems that Wang Laboratories' 2200 Series product line currently offer both batch and interactive communica consists of the 2200VP, 2200MVP, 2200LVP and tions capabilities. 2200SVP processors, all of which are multi-user or multi user upgradeable systems. The 2200 Series product line Emulation packages are provided for standard also includes the 2200 PCS-I1I, a packaged system which Teletype communications; IBM 2741 emula is single-user oriented. tion; IBM 2780, 3780, and 3741 batch terminal communications; and IBM 3270 The CPU and floppy disk drive are packaged together interactive communications. with appropriate cables and a cabinet to produce an integrated system. The 2200 PCS-I1I includes the CPU, A basic 2200PCS-1II with 32K bytes of user CRT, keyboard and single-sided double density memory, a CRT display, and a minidiskette minidiskette drive in a standard CRT-size enclosure as drive is priced at $6,500. Prices range well as an optional disk multiplexer controller. The upward to $21,000 for a 2200MVP proc number of peripherals that can be attached to a given essor with 256K bytes of user memory, system depends on the number of I/O slots that are excluding peripherals. Leases and rental plans available, with most peripherals requiring one slot. In all are also available. 2200 Series CPUs, highly efficient use of memory is achieved through the use of separate control memory to store the BASIC-2 interpreter and operating system. CHARACTERISTICS Wang began marketing the original 2200 Series in the VENDOR: Wang Laboratories,lnc., One Industrial Avenue, Spring of 1973. -

Validated Products List, 1995 No. 3: Programming Languages, Database
NISTIR 5693 (Supersedes NISTIR 5629) VALIDATED PRODUCTS LIST Volume 1 1995 No. 3 Programming Languages Database Language SQL Graphics POSIX Computer Security Judy B. Kailey Product Data - IGES Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 July 1995 QC 100 NIST .056 NO. 5693 1995 NISTIR 5693 (Supersedes NISTIR 5629) VALIDATED PRODUCTS LIST Volume 1 1995 No. 3 Programming Languages Database Language SQL Graphics POSIX Computer Security Judy B. Kailey Product Data - IGES Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 July 1995 (Supersedes April 1995 issue) U.S. DEPARTMENT OF COMMERCE Ronald H. Brown, Secretary TECHNOLOGY ADMINISTRATION Mary L. Good, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Arati Prabhakar, Director FOREWORD The Validated Products List (VPL) identifies information technology products that have been tested for conformance to Federal Information Processing Standards (FIPS) in accordance with Computer Systems Laboratory (CSL) conformance testing procedures, and have a current validation certificate or registered test report. The VPL also contains information about the organizations, test methods and procedures that support the validation programs for the FIPS identified in this document. The VPL includes computer language processors for programming languages COBOL, Fortran, Ada, Pascal, C, M[UMPS], and database language SQL; computer graphic implementations for GKS, COM, PHIGS, and Raster Graphics; operating system implementations for POSIX; Open Systems Interconnection implementations; and computer security implementations for DES, MAC and Key Management. -

Dissolving a Half Century Old Problem About the Implementation of Procedures
JID:SCICO AID:2123 /FLA [m3G; v1.221; Prn:28/08/2017; 16:24] P.1(1-12) Science of Computer Programming ••• (••••) •••–••• Contents lists available at ScienceDirect Science of Computer Programming www.elsevier.com/locate/scico Dissolving a half century old problem about the implementation of procedures Gauthier van den Hove CWI, SWAT, Science Park 123, 1098 XG Amsterdam, The Netherlands a r t i c l e i n f o a b s t r a c t Article history: We investigate the semantics of the procedure concept, and of one of the main techniques Received 21 June 2014 introduced by E. W. Dijkstra in his article Recursive Programming to implement it, namely Received in revised form 11 July 2017 the “static link,” sometimes also called “access link” or “lexical link.” We show that a Accepted 14 July 2017 confusion about that technique persists, even in recent textbooks. Our analysis is meant to Available online xxxx clarify the meaning of that technique, and of the procedure concept. Our main contribution Keywords: is to propose a better characterization of the “static link.” © Static link 2017 Elsevier B.V. All rights reserved. Block Closure Lexical scope Procedure 1. Introduction One of the first concepts introduced in the development of programming languages is the procedure concept. Its first precise definition appears in the ALGOL 60 Report, together with the static (or lexical) scope rule. Its implementation poses a number of difficulties, and the now classical solution to solve these difficulties, for ALGOL-like languages, was proposed by Dijkstra in his article Recursive Programming [1]. -

Steven Adriaensen, on the Semi-Automated Design Of
Faculty of Science and Bio-Engineering Sciences Department of Computer Science Artificial Intelligence Laboratory On the Semi-automated Design of Reusable Heuristics with applications to hard combinatorial optimization Dissertation submitted in fulfilment of the requirements for the degree of Doctor of Science: Computer Science Steven Adriaensen Promotor: Prof. Dr. Ann Nowé (Vrije Universiteit Brussel) © 2018 Steven Adriaensen All rights reserved. No parts of this book may be reproduced or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the author. Abstract These days, many scientific and engineering disciplines rely on standardization and auto- mated tools. Somewhat ironically, the design of the algorithms underlying these tools is often a highly manual, ad hoc, experience- and intuition-driven process, commonly regarded as an “art” rather than a “science”. The research performed in the scope of this dissertation is geared towards improving the way we design algorithms. Here, we treat algorithm design itself as a computational problem, which we refer to as the Algorithm Design Problem (ADP). In a sense, we study “algorithms for designing algorithms”. The main topic we investigate in this framework is the possibility of solving the ADP automatically. Letting computers, rather than humans, design algorithms has numerous potential benefits. The idea of automating algorithm design is definitely not “new”. At- tempts to do so can be traced back to the origins of computer science, and, ever since, the ADP, in one form or another, has been considered in many different research communities. Therefore, we first present an overview of this vast and highly fragmented field, relating the different approaches, discussing their respective strengths and weaknesses, towards enabling a more unified approach to automated algorithm design. -
Timeline of Computer History
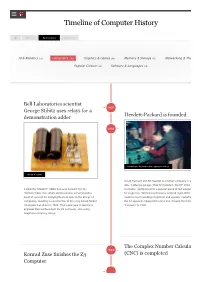
Timeline of Computer History By Year By Category Search AI & Robotics (55) Computers (145)(145) Graphics & Games (48) Memory & Storage (61) Networking & The Popular Culture (50) Software & Languages (60) Bell Laboratories scientist 1937 George Stibitz uses relays for a Hewlett-Packard is founded demonstration adder 1939 Hewlett and Packard in their garage workshop “Model K” Adder David Packard and Bill Hewlett found their company in a Alto, California garage. Their first product, the HP 200A A Called the “Model K” Adder because he built it on his Oscillator, rapidly became a popular piece of test equipm “Kitchen” table, this simple demonstration circuit provides for engineers. Walt Disney Pictures ordered eight of the 2 proof of concept for applying Boolean logic to the design of model to test recording equipment and speaker systems computers, resulting in construction of the relay-based Model the 12 specially equipped theatres that showed the movie I Complex Calculator in 1939. That same year in Germany, “Fantasia” in 1940. engineer Konrad Zuse built his Z2 computer, also using telephone company relays. The Complex Number Calculat 1940 Konrad Zuse finishes the Z3 (CNC) is completed Computer 1941 The Zuse Z3 Computer The Z3, an early computer built by German engineer Konrad Zuse working in complete isolation from developments elsewhere, uses 2,300 relays, performs floating point binary arithmetic, and has a 22-bit word length. The Z3 was used for aerodynamic calculations but was destroyed in a bombing raid on Berlin in late 1943. Zuse later supervised a reconstruction of the Z3 in the 1960s, which is currently on Operator at Complex Number Calculator (CNC) display at the Deutsches Museum in Munich. -

Machine Models for Type-2 Polynomial-Time Bounded Functionals
Syracuse University SURFACE College of Engineering and Computer Science - Former Departments, Centers, Institutes and College of Engineering and Computer Science Projects 1997 Semantics vs. Syntax vs. Computations: Machine models for type-2 polynomial-time bounded functionals James S. Royer Syracuse University, School of Computer and Information Science, [email protected] Follow this and additional works at: https://surface.syr.edu/lcsmith_other Part of the Computer Sciences Commons Recommended Citation Royer, James S., "Semantics vs. Syntax vs. Computations: Machine models for type-2 polynomial-time bounded functionals" (1997). College of Engineering and Computer Science - Former Departments, Centers, Institutes and Projects. 19. https://surface.syr.edu/lcsmith_other/19 This Article is brought to you for free and open access by the College of Engineering and Computer Science at SURFACE. It has been accepted for inclusion in College of Engineering and Computer Science - Former Departments, Centers, Institutes and Projects by an authorized administrator of SURFACE. For more information, please contact [email protected]. Semantics vs. Syntax vs. Computations Machine Models for Type-2 Polynomial-Time Bounded Functionals Intermediate Draft, Revision 2 + ǫ James S. Royer School of Computer and Information Science Syracuse University Syracuse, NY 13244 USA Email: [email protected] Abstract This paper investigates analogs of the Kreisel-Lacombe-Shoen®eld Theorem in the con- text of the type-2 basic feasible functionals. We develop a direct, polynomial-time analog of effective operation in which the time boundingon computationsismodeled after Kapronand Cook's scheme fortheirbasic poly- nomial-time functionals. We show that if P = NP, these polynomial-time effective op- erations are strictly more powerful on R (the class of recursive functions) than the basic feasible functions. -

Syntactic Control of Interference Revisited
Syracuse University SURFACE College of Engineering and Computer Science - Former Departments, Centers, Institutes and College of Engineering and Computer Science Projects 1995 Syntactic Control of Interference Revisited Peter W. O'Hearn Syracuse University A. J. Power University of Edinburgh M. Takeyama University of Edinburgh R. D. Tennent Queen's University Follow this and additional works at: https://surface.syr.edu/lcsmith_other Part of the Programming Languages and Compilers Commons Recommended Citation O'Hearn, Peter W.; Power, A. J.; Takeyama, M.; and Tennent, R. D., "Syntactic Control of Interference Revisited" (1995). College of Engineering and Computer Science - Former Departments, Centers, Institutes and Projects. 12. https://surface.syr.edu/lcsmith_other/12 This Article is brought to you for free and open access by the College of Engineering and Computer Science at SURFACE. It has been accepted for inclusion in College of Engineering and Computer Science - Former Departments, Centers, Institutes and Projects by an authorized administrator of SURFACE. For more information, please contact [email protected]. OHearn et al Syntactic Control of Interference Revisited P W OHearn Syracuse University Syracuse New York USA A J Power and M Takeyama University of Edinburgh Edinburgh Scotland EH JZ R D Tennent Queens University Kingston Canada KL N Dedicated to John C Reynolds in honor of his th birthday Abstract In Syntactic Control of Interference POPL J C Reynolds prop oses three design principles intended to constrain the scop e -

High-Tech Giants
spring08 The Magazine for University College and the School of Professional and Continuing Studies Alumni and Friends high-tech GIantS Alumni PersPectives on working for technology Pioneers: Digital EquipmEnt Corporation, primE ComputEr, anD Wang laboratoriEs >BoB Bozeman [uC ’78] alumni Travel Program: TUSCANY ocToBeR 22–30, 2008 trip highlights • spend seven nights in the ancient etruscan city of cortona, wonderfully situated in the heart of tuscany and the inspiration for the book Under the Tuscan Sun by frances mayes. • explore the tranquility of Assis and the graceful gothic ambience in siena. • marvel at the architectural wonders of renaissance florence. • experience the prodigious medieval history in Perugia, the well-preserved jewel of umbria. • learn the essence of tuscan cooking—the incomparable blend of olive oil, sun-ripened tomatoes, and herbs—at a demonstration by the chef of the award-winning restaurant tonino. space is limited so reserve your spot today! For more Information: contact Paula vogel at [email protected] or 617.373.2727. Registration: register online at http://nortea.ahitravel.com/ or call the northeastern university travel Program at 1.800.323.7373. the alumni travel program is sponsored by the school of Professional and continuing studies. emergency medical professionals conference upcoming JUne 14 BurlingTon Campus alumnievents Conference for EMt and Paramedics. lunch with dean hopey JUne 18 Cape Cod, MA Enjoy lunch with fellow alumni and the School of Professional and Continuing Studies is committed Dean Hopey on the Cape. to making connections with alumni and also connecting alumni to students. With that in mind, we have created social, networking, preparing for college and educational events for alumni. -

Sequential Program Structures
Jim Welsh, John Elder and David Bustard Sequential Program Structures C. A. R. HOARE SERIES EDITOR SEQUENTIAL PROGRAM STRUCTURES St. Olaf College JUL 3 1984 Science Library Prentice-Hall International Series in Computer Science C. A. R. Hoare, Series Editor Published backhouse, r. c.. Syntax of Programming Languages: Theory and Practice de barker, J. w„ Mathematical Theory of Program Correctness bjorner, D, and jones, c„ Formal Specification and Software Development clark, k. L. and McCabe, f. g„ micro-PROLOG: Programming in Logic dromey, r. G., How to Solve it by Computer duncan, f.. Microprocessor Programming and Software Development goldschlager, l. and lister, a., Computer Science: A Modern Introduction henderson, p.. Functional Programming: Application and Implementation inmos ltd., The Occam Programming Manual jackson, m. a., System Development jones, c, b., Software Development: A Rigorous Approach Joseph, m., prasad, v. r., and natarajan, n„ A Multiprocessor Operating System MacCALLUM, I. Pascal for the Apple Reynolds, J. c„ The Craft of Programming tennent, r. d., Principles of Programming Languages welsh, j., and elder, j.. Introduction to Pascal, 2nd Edition welsh, J., elder, j. and bustard, d., Sequential Program Structures welsh, j., and McKEag, m.. Structured System Programming SEQUENTIAL PROGRAM STRUCTURES JIM WELSH University of Queensland, Australia JOHN ELDER Queen's University of Belfast and DAVID BUSTARD Queen's University of Belfast St. Olaf College JUL 3 1984 Science Library Prentice/Hall International ENGLEWOOD CLIFFS, NEW JERSEY LONDON NEW DELHI RIO DE JANEIRO SINGAPORE SYDNEY TOKYO TORONTO WELLINGTON Library of Congress Cataloging in Publication Data Welsh, Jim, 1943- Sequential program structures. Bibliography: p. Includes index. -

OECD and APEC Since Vancouver 1995
OECD and APEC since Vancouver 1995 Risaburo NEZU Senior Executive Fellow Fujitsu Research Institute 15 January 2003 Honolulu Hawaii USA Japanese disappeared from the world IT competition Source: Business Week, June 24, 2002 Data: Standard & Poor ’s 1 Electronic machinery production 250 200 150 JAPAN 100 USA GERMANY 50 0 1 3 5 7 9 199 199 199 199 199 2001 Source: OECD STAN 2 ICT equipment Exports (1990- 2000) Value in millions of current USD and growth in percentages Average annual growth Exports 1990 1995 2000 (1995/90) (2000/95) Computer US 23,005 34,476 54,685 8.4 9.7 equipment Japan 18,854 29,521 27,558 9.4 -1.4 EU 40,119 66,460 94,131 10.6 7.2 Communication US 4,063 10,933 20,680 21.7 13.6 equipment Japan 5,614 6,904 8,106 4.3 3.3 EU 9,541 26,440 69,179 22.7 21.2 Electronic US 13,826 27,668 70,001 14.9 20.4 component Japan 14,678 43,270 50,348 24.2 3.1 EU 16,330 36,393 55,972 17.5 9.0 Source: OECD, ITS database, January 2002 3 Value chain of IT equipments Integrated approach VS Modular approach US Fabless (silicon valley) and Foundry (Taiwan) Japan does everything at home 【Structure of value chain】 After-sales, R&D, D&D Service, Support Procurement Logistics Manufacturing TIME Source: Nikkei Business July 8, 2002 4 Procurement of IT products / components from Taiwan by US, Japanese and EU companies Total of top 10 Total of top 5 $100M Companies Companies 350 300 US 250 US JPN EU 200 150 100 JPN 50 EU 0 95 96 97 98 99 '00 '01 Source:adapted from Ministry of Economic Affairs ( Taiwan ) 5 World laptop computer shipments(2001) by Taiwan “ If you own a Dell Laptop, there is a better-than- evens chance that it was made in Quanta’s factory.