A Comparison of Monero and Zcash
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
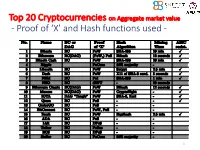
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Coinbase Explores Crypto ETF (9/6) Coinbase Spoke to Asset Manager Blackrock About Creating a Crypto ETF, Business Insider Reports
Crypto Week in Review (9/1-9/7) Goldman Sachs CFO Denies Crypto Strategy Shift (9/6) GS CFO Marty Chavez addressed claims from an unsubstantiated report earlier this week that the firm may be delaying previous plans to open a crypto trading desk, calling the report “fake news”. Coinbase Explores Crypto ETF (9/6) Coinbase spoke to asset manager BlackRock about creating a crypto ETF, Business Insider reports. While the current status of the discussions is unclear, BlackRock is said to have “no interest in being a crypto fund issuer,” and SEC approval in the near term remains uncertain. Looking ahead, the Wednesday confirmation of Trump nominee Elad Roisman has the potential to tip the scales towards a more favorable cryptoasset approach. Twitter CEO Comments on Blockchain (9/5) Twitter CEO Jack Dorsey, speaking in a congressional hearing, indicated that blockchain technology could prove useful for “distributed trust and distributed enforcement.” The platform, given its struggles with how best to address fraud, harassment, and other misuse, could be a prime testing ground for decentralized identity solutions. Ripio Facilitates Peer-to-Peer Loans (9/5) Ripio began to facilitate blockchain powered peer-to-peer loans, available to wallet users in Argentina, Mexico, and Brazil. The loans, which utilize the Ripple Credit Network (RCN) token, are funded in RCN and dispensed to users in fiat through a network of local partners. Since all details of the loan and payments are recorded on the Ethereum blockchain, the solution could contribute to wider access to credit for the unbanked. IBM’s Payment Protocol Out of Beta (9/4) Blockchain World Wire, a global blockchain based payments network by IBM, is out of beta, CoinDesk reports. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Exploring the Interconnectedness of Cryptocurrencies Using Correlation Networks
Exploring the Interconnectedness of Cryptocurrencies using Correlation Networks Andrew Burnie UCL Computer Science Doctoral Student at The Alan Turing Institute [email protected] Conference Paper presented at The Cryptocurrency Research Conference 2018, 24 May 2018, Anglia Ruskin University Lord Ashcroft International Business School Centre for Financial Research, Cambridge, UK. Abstract Correlation networks were used to detect characteristics which, although fixed over time, have an important influence on the evolution of prices over time. Potentially important features were identified using the websites and whitepapers of cryptocurrencies with the largest userbases. These were assessed using two datasets to enhance robustness: one with fourteen cryptocurrencies beginning from 9 November 2017, and a subset with nine cryptocurrencies starting 9 September 2016, both ending 6 March 2018. Separately analysing the subset of cryptocurrencies raised the number of data points from 115 to 537, and improved robustness to changes in relationships over time. Excluding USD Tether, the results showed a positive association between different cryptocurrencies that was statistically significant. Robust, strong positive associations were observed for six cryptocurrencies where one was a fork of the other; Bitcoin / Bitcoin Cash was an exception. There was evidence for the existence of a group of cryptocurrencies particularly associated with Cardano, and a separate group correlated with Ethereum. The data was not consistent with a token’s functionality or creation mechanism being the dominant determinants of the evolution of prices over time but did suggest that factors other than speculation contributed to the price. Keywords: Correlation Networks; Interconnectedness; Contagion; Speculation 1 1. Introduction The year 2017 saw the start of a rapid diversification in cryptocurrencies. -

Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain
I. J. Computer Network and Information Security, 2021, 2, 1-15 Published Online April 2021 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijcnis.2021.02.01 Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain Alexandr Kuznetsov1 , Inna Oleshko2, Vladyslav Tymchenko3, Konstantin Lisitsky4, Mariia Rodinko5 and Andrii Kolhatin6 1,3,4,5,6 V. N. Karazin Kharkiv National University, Svobody sq., 4, Kharkiv, 61022, Ukraine E-mail: [email protected], [email protected], [email protected], [email protected], [email protected] 2 Kharkiv National University of Radio Electronics, Nauky Ave. 14, Kharkiv, 61166, Ukraine E-mail: [email protected] Received: 30 June 2020; Accepted: 21 October 2020; Published: 08 April 2021 Abstract: A blockchain, or in other words a chain of transaction blocks, is a distributed database that maintains an ordered chain of blocks that reliably connect the information contained in them. Copies of chain blocks are usually stored on multiple computers and synchronized in accordance with the rules of building a chain of blocks, which provides secure and change-resistant storage of information. To build linked lists of blocks hashing is used. Hashing is a special cryptographic primitive that provides one-way, resistance to collisions and search for prototypes computation of hash value (hash or message digest). In this paper a comparative analysis of the performance of hashing algorithms that can be used in modern decentralized blockchain networks are conducted. Specifically, the hash performance on different desktop systems, the number of cycles per byte (Cycles/byte), the amount of hashed message per second (MB/s) and the hash rate (KHash/s) are investigated. -

Defining an Ico Securities Safe Harbor in the Cryptocurrency “Wild West”
THE SEC RIDES INTO TOWN: DEFINING AN ICO SECURITIES SAFE HARBOR IN THE CRYPTOCURRENCY “WILD WEST” C. Daniel Lockaby This Note recommends a viable way for the Securities and Exchange Commission (SEC) to apply the Regulation S foreign-issuer safe harbor to Initial Coin Offerings (ICOs). In the last two years, cryptocurrencies and blockchain-based companies have witnessed dramatic rises in price and value. New entrants to the crypto-markets often use ICOs as virtual public offerings to earn capital and develop their projects. The SEC has signaled that they plan to fold ICOs and blockchain offerings into existing securities law. How these new virtual capital-raising mechanisms will fit into this framework is still largely unknown. As a defensive measure, many ICOs have banned US investors in an attempt to become foreign offerings that are outside the SEC's reach. Regulation S is the existing safe harbor that conventional securities offerings utilize to ensure that they are "foreign offerings." While ICOs are novel and do not fit perfectly into Regulation S's language, the safe harbor can be adapted to appropriately set parameters for ICOs. This Note suggests the correct interpretation that both protects US consumers and sets acceptable requirements for corporations seeking to fall within Regulation S. J.D. Candidate, University of Georgia School of Law, 2019. 335 336 GEORGIA LAW REVIEW [Vol. 53:335 TABLE OF CONTENTS I. INTRODUCTION.......................................................................... 337 II. THE BRAVE NEW CRYPTO WORLD ........................................... 339 A. WHAT IS BLOCKCHAIN? ................................................... 339 B. HOW ICOS WORK ............................................................. 342 C. THE PRE-2017 “WILD WEST” ............................................ 343 III. SEC INVOLVEMENT .........................................................................346 A. -

Prospects for Blockchain-Based Settlement Frameworks As a Resolution to the Threat of De-Risking to Caribbean Financial Systems
Prospects for blockchain-based settlement frameworks as a resolution to the threat of de-risking to Caribbean financial systems Robert Crane Williams Economic Commission for Latin America and the Caribbean (ECLAC) Prospects for blockchain-based settlement frameworks as a resolution to the threat of de-risking to Caribbean financial systems Robert Crane Williams Economic Commission for Latin America and the Caribbean (ECLAC) This document has been prepared by Robert Crane Williams, Associate Information Management Officer of the Caribbean Knowledge Management Centre, subregional headquarters for the Caribbean, Economic Commission for Latin America and the Caribbean (ECLAC). The views expressed in this document, which has been reproduced without formal editing, are those of the author and do not necessarily reflect the views of the Organization. United Nations publication LC/CAR/2017/2 Distribution: Limited Copyright © United Nations, April 2017. All rights reserved Printed at United Nations, Santiago Applications for authorization to reproduce this work in whole or in part should be sent to the Economic Commission for Latin America and the Caribbean (ECLAC), Publications and Web Services Division, [email protected]. Member States and their governmental institutions may reproduce this work without prior authorization, but are requested to mention the source and to inform ECLAC of such reproduction. ECLAC Prospects for blockchain-based settlement frameworks... Contents Introduction ..................................................................................................................................... -

Whitepaper Download (PDF)
USPTO Provisional Patent Application Number : 62/646,930 62/797,648 InfraBlockchain Scalable enterprise blockchain technology that combines the strengths of a private and a public blockchain No Native Cryptocurrency programmable fiat-pegged stable tokens (e.g. USD, KRW, CNY) as base currencies used for transaction fee Proof-of-Transaction (PoT) reasonable and fair blockchain consensus mechanism incentivizing blockchain service providers General Financial Platform smart-contract based blockchain system designed for enterprise uses Optional On-Chain Privacy Tech. privacy-protecting transactions applicable for small amount money transfer (like cash) and blockchain-based full privacy voting system Technical White Paper Feb. 2018 (v1) / Jan. 2019 (v2) / Aug. 2020 (v2.4) ©2020 Blockchain Labs Inc. All rights reserved InfraBlockchain is rebranded from YOSEMITE Blockchain Abstract InfraBlockchain provides innovative blockchain system architecture overcoming the obstacles of private and public blockchains which prevent enterprises and public institutions from utilizing the full potential of blockchain technology. Public blockchains having their native cryptocurrencies (e.g. BTC, ETH, EOS) cannot be adopted by enterprises/public-institutions due to the regulatory uncertainty, extreme volatility and unfair distribution of cryptocurrencies. Private/permissioned blockchain systems (e.g. Hyperledger Fabric, Corda, Quorum) applied to existing enterprise systems are very likely to be nothing but an inefficient high-cost distributed database providing system auditability. InfraBlockchain introduces a new method of enterprise-oriented public/permissioned blockchain system design without issuing a native cryptocurrency minted by the blockchain itself. Any entities can issue their own tokens (e.g. digital USD fiat-pegged stable tokens backed by an equivalent fiat money reserve, asset-backed security tokens, …) using the built-in InfraBlockchain Standard Token model ensuring the token interoperability. -

To Read the Full Zcash Regulatory & Compliance Brief
Zcash Regulatory & Compliance Brief June 2020 Introduction This note is intended to provide an overview of Zcash for regulators, policy-makers, and compliance professionals. Zcash is an open-source, decentralized virtual currency, similar in nature to Bitcoin, which protects users’ privacy through the use of an innovative cryptographic technique based on zero-knowledge proofs. Zcash is fully compliant with the anti-money laundering and terrorism financing (AML / CFT) requirements set forth in the FATF Recommendations adopted in June 2019. Required originator and beneficiary information can be attached directly to shielded Zcash transactions, facilitating compliance with Travel Rule requirements. Zcash is listed on many of the world’s largest virtual currency exchanges, under the ticker “ZEC”. Confidentiality & Privacy Personal financial information can reveal a huge amount of information about the subject, including how much they earn, where they shop, what newspapers, magazines and websites they subscribe to, their hobbies and interests, what causes they donate to, and how much they have saved. Governments of the world's largest economies have recognised the importance of personal financial privacy, and have enacted legislation to protect it. Examples include the Gramm-Leach-Bliley Act in the United States, the EU's General Data Protection Regulation, and Japan’s Act on the Protection of Personal Information. The growing threat from cyber-criminals and identity thieves, and high profile incidents such as the Experian data breach have raised public awareness of the importance of robust privacy protections. It is the policy of the Congress that each financial institution has an affirmative and continuing obligation to respect the privacy of its customers and to protect the security and confidentiality of those customers’ nonpublic personal information. -

Fedcoin: a Central Bank- Issued Cryptocurrency JP Koning
R3 Reports Fedcoin: A Central Bank- issued Cryptocurrency JP Koning 1 Contents R3 Research aims to 1. Summary 2 deliver concise 2. The search for a stable cryptocurrency 3 reports on DLT in 3. To what degree should the public have access business language to central bank non-tangible money? 8 for decision-makers 4. Further design questions about a potential Fedcoin 19 and DLT hobbyists 5. Conclusion 27 alike. The reports are written by experts in the space and are rooted in practical experience with the Disclaimer: These white papers are for general information and discussion only and technology. shall not be copied or redistributed outside R3 membership. They are not a full analysis of the matters presented, are meant solely to provide general guidance and may not be relied upon as professional advice, and do not purport to represent the views of R3 Holdco LLC, its affiliates or any of the institutions that contributed to these white papers. The information in these white papers was posted with reasonable care and attention. However, it is possible that some information in these white papers is incomplete, incorrect, or inapplicable to particular circumstances or conditions. The contributors do not accept liability for direct or indirect losses resulting from using, relying or acting upon information in these white papers. These views are those of R3 Research and associated authors and do not necessarily reflect the views of R3 or R3’s consortium members. For more Research, please visit R3’s Wiki here. Fedcoin: A Central Bank-issued Cryptocurrency JP Koning November 15, 2016 1 Summary A central bank-issued digital cash product, henceforth referred to as ‘Fedcoin,’ dates back to the original design goal of Bitcoin, the creation of a peer-to-peer electronic cash system.