Vulnerability of Blockchain Technologies to Quantum Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Auditing Wallets in Cryptonote
Auditing wallets in CryptoNote sowle <[email protected]> Zano project, https://zano.org Cryptocurrency wallet auditing is the ability for a third party (the "auditor") to watch the transactions and to be able to calculate the correct balance without an ability to spend a coin. This article explores several possible implementations of expansion cryptocurrency protocol CryptoNote 2.0 [1] with such ability. In the original CryptoNote protocol auditing is only partially possible with the help of the tracking key, namely, an auditor is able to distinguish incoming transactions in the blockchain, but the full set of secret keys is required to filter out outgoing transactions. This article is intended for readers familiar with the general blockchain technology and “classic” cryptocurrencies, as well as with the basics of cryptography on elliptic curves. 1. Introduction What is CryptoNote? Surprisingly, most people interested in blockchain technology have never heard anything about CryptoNote, in spite of the fact that the technology has more than 300 forks, including Monero as the most famous. Back in 2014 in the cryptocurrency community there were mentions [2] about a project, titled Bytecoin. That project did not originate as a Bitcoin or other known project fork, having its own original codebase. It was very unusual at the time. Bytecoin general conception was to be an implementation of a privacy-technology named CryptoNote. There were two main privacy mechanisms: stealth-addresses and inputs` mixing-in with the help of ring signatures (at the time it was called "blockchain mixer"). Since Zcash existed only on paper / in theory at that time, CryptoNote became a competitive technology and has provoked much controversy in the cryptocurrency community. -

Linking Wallets and Deanonymizing Transactions in the Ripple Network
Proceedings on Privacy Enhancing Technologies ; 2016 (4):436–453 Pedro Moreno-Sanchez*, Muhammad Bilal Zafar, and Aniket Kate* Listening to Whispers of Ripple: Linking Wallets and Deanonymizing Transactions in the Ripple Network Abstract: The decentralized I owe you (IOU) transac- 1 Introduction tion network Ripple is gaining prominence as a fast, low- cost and efficient method for performing same and cross- In recent years, we have observed a rather unexpected currency payments. Ripple keeps track of IOU credit its growth of IOU transaction networks such as Ripple [36, users have granted to their business partners or friends, 40]. Its pseudonymous nature, ability to perform multi- and settles transactions between two connected Ripple currency transactions across the globe in a matter of wallets by appropriately changing credit values on the seconds, and potential to monetize everything [15] re- connecting paths. Similar to cryptocurrencies such as gardless of jurisdiction have been pivotal to their suc- Bitcoin, while the ownership of the wallets is implicitly cess so far. In a transaction network [54, 55, 59] such as pseudonymous in Ripple, IOU credit links and transac- Ripple [10], users express trust in each other in terms tion flows between wallets are publicly available in an on- of I Owe You (IOU) credit they are willing to extend line ledger. In this paper, we present the first thorough each other. This online approach allows transactions in study that analyzes this globally visible log and charac- fiat money, cryptocurrencies (e.g., bitcoin1) and user- terizes the privacy issues with the current Ripple net- defined currencies, and improves on some of the cur- work. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -
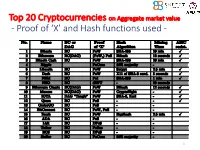
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Using Blockchain Technology to Secure the Internet of Things
Using Blockchain Technology to Secure the Internet of Things Presented by the Blockchain/ Distributed Ledger Working Group © 2018 Cloud Security Alliance – All Rights Reserved. You may download, store, display on your computer, view, print, and link to Using Blockchain Technology to Secure the Internet of Things subject to the following: (a) the Document may be used solely for your personal, informational, non- commercial use; (b) the Report may not be modified or altered in any way; (c) the Document may not be redistributed; and (d) the trademark, copyright or other notices may not be removed. You may quote portions of the Document as permitted by the Fair Use provisions of the United States Copyright Act, provided that you attribute the portions to the Using Blockchain Technology to Secure the Internet of Things paper. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 2 © Copyright 2018, Cloud Security Alliance. All rights reserved. ABOUT CSA The Cloud Security Alliance is a not-for-profit organization with a mission to promote the use of best practices for providing security assurance within Cloud Computing, and to provide education on the uses of Cloud Computing to help secure all other forms of computing. The Cloud Security Alliance is led by a broad coalition of industry practitioners, corporations, associations and other key stakeholders. For further information, visit us at www.cloudsecurityalliance.org and follow us on Twitter @cloudsa. Blockchain/Distributed Ledger Technology Working Group | Using Blockchain Technology to Secure the Internet of Things 3 © Copyright 2018, Cloud Security Alliance. All rights reserved. -

Hybrid Public/Anonymous Transactions on Monero, Cryptonote X-Cash
Hybrid public/anonymous transactions on Monero, Cryptonote X-Cash Zach Hildreth October 7, 2019 Abstract This yellow paper details the technical concepts and implementation of hybrid transactions (also known as FlexPrivacy c ), a feature enabling public and private transactions on the X- Cash public blockchain. In the first part, the paper aims at detailing how the hybrid transactions operate from a user’s perspective with some real-world use cases. A parallel is made between the digital money system and the economic behaviors associated with the current FIAT system. Secondly, a deeper understanding of the technology is given, explaining the implication on a blockchain perspective, as well as the edge cases and their approaches. Lastly, the last part consists in an in-depth approach of the mathematical concepts and technical implementation of the hybrid transaction in the X-Cash blockchain. Contents 1 Public transactions in the ringCT 4 2 Privacy in the inputs 4 3 A brief understanding of cryptonote transactions 4 4 Creation of a public address 6 5 How stealth addresses/outputs are decoded 6 6 How public transactions are created 7 1 Summary of the public transaction feature The hybrid transaction feature allows users to send and receive public or private transactions on the X-Network Blockchain X-Cash, which is based on the CryptoNote protocol. This feature is implemented on a per transaction basis where users can directly switch the privacy type by choosing the setting before attempting to send a transaction. In a public transaction, the following additional information is made public: • Sender’s address • Receiver’s address • Amount sent • Change amount sent back to the sender’s address However, the public transaction does not compromise the sender’s or receiver’s wallet full bal- ances nor the real mixin (number of signatures in the ring signature that authorizes the transaction) that provided the X-Cash balance. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Ethereum Classic Price Prediction 2030
1 Ethereum Classic Price Prediction 2030 Update [06-08-2021] There are various cryptocurrencies out now in the bitcoin market, and people worldwide and mostly in the countries like United States , are investing in these digital currencies. 00000001 Ethereum max 7d low Emax 7d high- 0. And this particular blockchain allows to grants investors security and also control for all of their digital assets. Firstly, we have to be sure about the amount of ETH in our wallet to cover our transaction fees. Once OKExChain supports EVM, developers can use the development tools and languages of Ethereum to develop smart contracts on OKExChain. The contract launched the Beacon Chain, the first stage in the ETH 2. Most are confident that Ethereum 2. Ethereum s Growing Transaction Fees Shouldn t Stop Users. Is Cardano or Ethereum a Better Investment. It was developed in 2017 by Charles Hoskinson, who was previously involved in creating Ethereum itself. In other words, we have defined proof, in the per-coin values of both Bitcoin and Ethereum, that increases of 500 , 1,000 and more are not unprecedented or wildly unreasonable in this market , especially for coins that started out at a few cents. And this has given the latter a significant advantage over the former. At the same time, it is also going to take many other alts with it to new highs. A 10k price is definitely on the cards with so many Decentralized finance apps shifting to their protocols. If Ethereum could hit 10k by the end of 2021 then it would cross the 1 trillion market cap and might become the 2nd cryptocurrency to do so. -

Impossibility of Full Decentralization in Permissionless Blockchains
Impossibility of Full Decentralization in Permissionless Blockchains Yujin Kwon*, Jian Liuy, Minjeong Kim*, Dawn Songy, Yongdae Kim* *KAIST {dbwls8724,mjkim9394,yongdaek}@kaist.ac.kr yUC Berkeley [email protected],[email protected] ABSTRACT between achieving good decentralization in the consensus protocol Bitcoin uses the proof-of-work (PoW) mechanism where nodes earn and not relying on a TTP exists. rewards in return for the use of their computing resources. Although this incentive system has attracted many participants, power has, CCS CONCEPTS at the same time, been significantly biased towards a few nodes, • Security and privacy → Economics of security and privacy; called mining pools. In addition, poor decentralization appears not Distributed systems security; only in PoW-based coins but also in coins that adopt proof-of-stake (PoS) and delegated proof-of-stake (DPoS) mechanisms. KEYWORDS In this paper, we address the issue of centralization in the consen- Blockchain; Consensus Protocol; Decentralization sus protocol. To this end, we first define ¹m; ε; δº-decentralization as a state satisfying that 1) there are at least m participants running 1 INTRODUCTION a node, and 2) the ratio between the total resource power of nodes Traditional currencies have a centralized structure, and thus there run by the richest and the δ-th percentile participants is less than exist several problems such as a single point of failure and corrup- or equal to 1 + ε. Therefore, when m is sufficiently large, and ε and tion. For example, the global financial crisis in 2008 was aggravated δ are 0, ¹m; ε; δº-decentralization represents full decentralization, by the flawed policies of banks that eventually led to many bank which is an ideal state. -

Exploring the Interconnectedness of Cryptocurrencies Using Correlation Networks
Exploring the Interconnectedness of Cryptocurrencies using Correlation Networks Andrew Burnie UCL Computer Science Doctoral Student at The Alan Turing Institute [email protected] Conference Paper presented at The Cryptocurrency Research Conference 2018, 24 May 2018, Anglia Ruskin University Lord Ashcroft International Business School Centre for Financial Research, Cambridge, UK. Abstract Correlation networks were used to detect characteristics which, although fixed over time, have an important influence on the evolution of prices over time. Potentially important features were identified using the websites and whitepapers of cryptocurrencies with the largest userbases. These were assessed using two datasets to enhance robustness: one with fourteen cryptocurrencies beginning from 9 November 2017, and a subset with nine cryptocurrencies starting 9 September 2016, both ending 6 March 2018. Separately analysing the subset of cryptocurrencies raised the number of data points from 115 to 537, and improved robustness to changes in relationships over time. Excluding USD Tether, the results showed a positive association between different cryptocurrencies that was statistically significant. Robust, strong positive associations were observed for six cryptocurrencies where one was a fork of the other; Bitcoin / Bitcoin Cash was an exception. There was evidence for the existence of a group of cryptocurrencies particularly associated with Cardano, and a separate group correlated with Ethereum. The data was not consistent with a token’s functionality or creation mechanism being the dominant determinants of the evolution of prices over time but did suggest that factors other than speculation contributed to the price. Keywords: Correlation Networks; Interconnectedness; Contagion; Speculation 1 1. Introduction The year 2017 saw the start of a rapid diversification in cryptocurrencies. -

Cryptonote Coin
CryptoNote Coin Michael Davis University of Miami April 2019 Proof of Work \scrypt" (used by Litecoin) has a uniform distribution of dependent lookups. Given a fast enough processor, it can be faster to only keep a small scratch-pad in memory and compute other dependencies on the fly. CryptoNight ensures that new blocks depend on all previous blocks, so CPU speed trades off with memory exponentially. Terminology I l = 2252 + 27742317777372353535851937790883648493 4 I A base point G = (x; − 5 ) I Hs a cryptographic hash function I Hp a deterministic hash function I Private keys are numbers a 2 [1; l − 1] I Public keys are points A = aG. I Private user keys are pairs (a; b) of private ec-keys I A standard address is a pair (A; B) derived from the private user key (a; b) Table of Contents Unlinkability Untraceability Alice ! Bob: Step 1 Alice reads Bob's public address (A; B). Alice ! Bob: Step 2 Alice generates r 2 [1; l − 1] and then computes P = Hs (rA)G + B. Alice ! Bob: Step 3 Alice generates the transaction. The transaction contains: I The transaction public key R = rG I The amount being transferred I The destination key P = Hs (rA)G + B Alice ! Bob: Step 4 Alice sends the transaction. Alice ! Bob: Step 5 Bob is listening on the stream of transactions. For each transaction, using R, the public key of the transaction, and a, one 0 of Bob's private ec-keys, Bob computes P = Hs (aR)G + B. If P0 = P (the destination key), then aR = arG = rA. -

The Relationship Between the Popularity of Cryptocurrencies and Their Prices, Returns and Trading Volumes: a Structural Break An
İstanbul İktisat Dergisi - Istanbul Journal of Economics 69, 2019/2, s. 133-157 ISSN: 2602-4152 E-ISSN: 2602-3954 RESEARCH ARTICLE / ARAŞTIRMA MAKALESİ The Relationship Between the Popularity of Cryptocurrencies and their Prices, Returns and Trading Volumes: A Structural Break and Comparative Analysis Kripto Paraların Bilinirliği ile Fiyat, Getiri ve İşlem Hacimleri Arasındaki İlişki: Yapısal Kırılmalı ve Karşılaştırmalı Bir Analiz Mustafa ÖZYEŞİL1 ABSTRACT In this study, the relationship between the popularity of cryptocurrencies and their price, return and trading volumes are examined through time series analysis. The popularity variable is determined according the frequency of cryptocurrencies being DOI: 10.26650/ISTJECON2019-0017 searched on the internet. Stationarity of series is examined by Vogelsang and Perron (1998) structural breaks ADF unit root test. According to the test results, all series are found to be stationary at level values. VAR analyses and impulse-response functions are performed to reveal dynamic interaction between the series. 1Assist. Prof. Dr., Istanbul Aydın University, According to impulse - response test results, returns of BITCOIN Anadolu BIL Vocational School, Department of Business Administration, Istanbul, Turkey decreased against a decreasing shock in the number searches on the internet and its price and trading volume followed a ORCID: M.Ö. 0000-0002-4442-7087 fluctuating course. In order to see the causality relationship Corresponding author/Sorumlu yazar: between variables the Granger causality test