51% Attack” January 2019
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Peer Co-Movement in Crypto Markets
Peer Co-Movement in Crypto Markets G. Schwenkler and H. Zheng∗ February 4, 2021y Abstract We show that peer linkages induce significant price co-movement in crypto markets in excess of common risk factors and correlated demand shocks. When large abnormal return shocks hit one crypto, its peers experience unusually large abnormal returns of the opposite sign. These effects are primarily concentrated among smaller peers and revert after several weeks, resulting in predictable returns. We develop trading strategies that exploit this rever- sal, and show that they are profitable even after accounting for trading fees and frictions. We establish our results by identifying crypto peers through co-mentions in online news using novel natural language processing technologies. Keywords: Cryptocurrencies, peers, co-movement, competition, natural language pro- cessing. JEL codes: G12, G14, C82. ∗Schwenkler is at the Department of Finance, Santa Clara University Leavey School of Business. Zheng is at the Department of Finance, Boston University Questrom School of Business. Schwenkler is corresponding author. Email: [email protected], web: http://www.gustavo-schwenkler.com. yThis is a revision of a previous paper by the two authors called \Competition or Contagion: Evidence from Cryptocurrency Markets." We are grateful to Jawad Addoum (discussant), Daniele Bianchi (discussant), Will Cong, Tony Cookson, Sanjiv Das, Seoyoung Kim, Andreas Neuhierl, Farzad Saidi, and Antoinette Schoar, seminar participants at Boston University and the Society for Financial Econometrics, and the participants at the 2020 Finance in the Cloud III Virtual Conference, the 2020 MFA Annual Meeting, the 3rd UWA Blockchain, Cryptocurrency and FinTech Conference, and the 2020 INFORMS Annual Meeting for useful comments and suggestions. -

Characterizing Ethereum's Mining Power Decentralization at a Deeper
Characterizing Ethereum’s Mining Power Decentralization at a Deeper Level Liyi Zeng∗§, Yang Chen†§, Shuo Chen†, Xian Zhang†, Zhongxin Guo†, Wei Xu∗, Thomas Moscibroda‡ ∗Institute for Interdisciplinary Information Sciences, Tsinghua University †Microsoft Research ‡Microsoft Azure §Contacts: [email protected], [email protected] Abstract—For proof-of-work blockchains such as Ethereum, than 50% of the total power has grown from several the mining power decentralization is an important discussion hundred to several thousand. Overall, the power is more point in the community. Previous studies mostly focus on the decentralized at the participant level than 4 years ago. aggregated power of the mining pools, neglecting the pool participants who are the source of the pools’ power. In this paper, However, we also find that this number varied signif- we present the first large-scale study of the pool participants icantly over time, which means it requires continuous in Ethereum’s mining pools. Pool participants are not directly tracking. Additionally, as our current data and method- observable because they communicate with their pools via private ology cannot de-anonymize the participants, it’s possible channels. However, they leave “footprints” on chain as they that some participants split themselves into many smaller use Ethereum accounts to anonymously receive rewards from mining pools. For this study, we combine several data sources ones for various reasons, which could make our estima- to identify 62,358,646 pool reward transactions sent by 47 tion inaccurate if not completely off the target. Further pools to their participants over Ethereum’s entire near 5-year study to improve the estimation accuracy is important. -

Crypto Research Report ‒ April 2019 Edition
April 2019 Edition VI. “When the Tide Goes Out…” Investments: Gold and Bitcoin, Stronger Together Technical Analysis: Spring Awakening? Cryptocurrency Mining in Theory and Practice Demelza Kelso Hays Mark J. Valek We would like to express our profound gratitude to our premium partners for supporting the Crypto Research Report: www.cryptofunds.li Contents Editorial ............................................................................................................................................... 4 In Case You Were Sleeping: When the Tide Goes Out…............................................................... 5 Back to the Roots ............................................................................................................................................. 6 How Long Will This Bear Market Last .............................................................................................................. 7 A Tragic Story Traverses the World ................................................................................................................. 9 When the tide goes out… ............................................................................................................................... 10 A State Cryptocurrency? ................................................................................................................................ 12 Support is Increasing ..................................................................................................................................... 14 -

Bitcoin Tumbles As Miners Face Crackdown - the Buttonwood Tree Bitcoin Tumbles As Miners Face Crackdown
6/8/2021 Bitcoin Tumbles as Miners Face Crackdown - The Buttonwood Tree Bitcoin Tumbles as Miners Face Crackdown By Haley Cafarella - June 1, 2021 Bitcoin tumbles as Crypto miners face crackdown from China. Cryptocurrency miners, including HashCow and BTC.TOP, have halted all or part of their China operations. This comes after Beijing intensified a crackdown on bitcoin mining and trading. Beijing intends to hammer digital currencies amid heightened global regulatory scrutiny. This marks the first time China’s cabinet has targeted virtual currency mining, which is a sizable business in the world’s second-biggest economy. Some estimates say China accounts for as much as 70 percent of the world’s crypto supply. Cryptocurrency exchange Huobi suspended both crypto-mining and some trading services to new clients from China. The plan is that China will instead focus on overseas businesses. BTC.TOP, a crypto mining pool, also announced the suspension of its China business citing regulatory risks. On top of that, crypto miner HashCow said it would halt buying new bitcoin mining rigs. Crypto miners use specially-designed computer equipment, or rigs, to verify virtual coin transactions. READ MORE: Sustainable Mineral Exploration Powers Electric Vehicle Revolution This process produces newly minted crypto currencies like bitcoin. “Crypto mining consumes a lot of energy, which runs counter to China’s carbon neutrality goals,” said Chen Jiahe, chief investment officer of Beijing-based family office Novem Arcae Technologies. Additionally, he said this is part of China’s goal of curbing speculative crypto trading. As result, bitcoin has taken a beating in the stock market. -

User Manual Ledger Nano S
User Manual Ledger Nano S Version control 4 Check if device is genuine 6 Buy from an official Ledger reseller 6 Check the box contents 6 Check the Recovery sheet came blank 7 Check the device is not preconfigured 8 Check authenticity with Ledger applications 9 Summary 9 Learn more 9 Initialize your device 10 Before you start 10 Start initialization 10 Choose a PIN code 10 Save your recovery phrase 11 Next steps 11 Update the Ledger Nano S firmware 12 Before you start 12 Step by step instructions 12 Restore a configuration 18 Before you start 19 Start restoration 19 Choose a PIN code 19 Enter recovery phrase 20 If your recovery phrase is not valid 20 Next steps 21 Optimize your account security 21 Secure your PIN code 21 Secure your 24-word recovery phrase 21 Learn more 22 Discover our security layers 22 Send and receive crypto assets 24 List of supported applications 26 Applications on your Nano S 26 Ledger Applications on your computer 27 Third-Party applications on your computer 27 If a transaction has two outputs 29 Receive mining proceeds 29 Receiving a large amount of small transactions is troublesome 29 In case you received a large amount of small payments 30 Prevent problems by batching small transactions 30 Set up and use Electrum 30 Set up your device with EtherDelta 34 Connect with Radar Relay 36 Check the firmware version 37 A new Ledger Nano S 37 A Ledger Nano S in use 38 Update the firmware 38 Change the PIN code 39 Hide accounts with a passphrase 40 Advanced Passphrase options 42 How to best use the passphrase feature 43 -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Asymmetric Proof-Of-Work Based on the Generalized Birthday Problem
Equihash: Asymmetric Proof-of-Work Based on the Generalized Birthday Problem Alex Biryukov Dmitry Khovratovich University of Luxembourg University of Luxembourg [email protected] [email protected] Abstract—The proof-of-work is a central concept in modern Long before the rise of Bitcoin it was realized [20] that cryptocurrencies and denial-of-service protection tools, but the the dedicated hardware can produce a proof-of-work much requirement for fast verification so far made it an easy prey for faster and cheaper than a regular desktop or laptop. Thus the GPU-, ASIC-, and botnet-equipped users. The attempts to rely on users equipped with such hardware have an advantage over memory-intensive computations in order to remedy the disparity others, which eventually led the Bitcoin mining to concentrate between architectures have resulted in slow or broken schemes. in a few hardware farms of enormous size and high electricity In this paper we solve this open problem and show how to consumption. An advantage of the same order of magnitude construct an asymmetric proof-of-work (PoW) based on a compu- is given to “owners” of large botnets, which nowadays often tationally hard problem, which requires a lot of memory to gen- accommodate hundreds of thousands of machines. For prac- erate a proof (called ”memory-hardness” feature) but is instant tical DoS protection, this means that the early TLS puzzle to verify. Our primary proposal Equihash is a PoW based on the schemes [8], [17] are no longer effective against the most generalized birthday problem and enhanced Wagner’s algorithm powerful adversaries. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -

Zcash Protocol Speci Cation
Zcash Protocol Specication Version 2018.0-beta-14 Daira Hopwood† Sean Bowe† — Taylor Hornby† — Nathan Wilcox† March 11, 2018 Abstract. Zcash is an implementation of the Decentralized Anonymous Payment scheme Zerocash, with security xes and adjustments to terminology, functionality and performance. It bridges the exist- ing transparent payment scheme used by Bitcoin with a shielded payment scheme secured by zero- knowledge succinct non-interactive arguments of knowledge (zk-SNARKs). It attempts to address the problem of mining centralization by use of the Equihash memory-hard proof-of-work algorithm. This specication denes the Zcash consensus protocol and explains its differences from Zerocash and Bitcoin. Keywords: anonymity, applications, cryptographic protocols, electronic commerce and payment, nancial privacy, proof of work, zero knowledge. Contents 1 1 Introduction 5 1.1 Caution . .5 1.2 High-level Overview . .5 2 Notation 7 3 Concepts 8 3.1 Payment Addresses and Keys . .8 3.2 Notes...........................................................9 3.2.1 Note Plaintexts and Memo Fields . .9 3.3 The Block Chain . 10 3.4 Transactions and Treestates . 10 3.5 JoinSplit Transfers and Descriptions . 11 3.6 Note Commitment Trees . 11 3.7 Nullier Sets . 12 3.8 Block Subsidy and Founders’ Reward . 12 3.9 Coinbase Transactions . 12 † Zerocoin Electric Coin Company 1 4 Abstract Protocol 12 4.1 Abstract Cryptographic Schemes . 12 4.1.1 Hash Functions . 12 4.1.2 Pseudo Random Functions . 13 4.1.3 Authenticated One-Time Symmetric Encryption . 13 4.1.4 Key Agreement . 13 4.1.5 Key Derivation . 14 4.1.6 Signature . 15 4.1.6.1 Signature with Re-Randomizable Keys . -
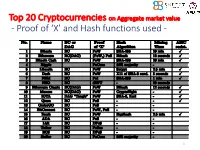
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Cryptocurrency: the Economics of Money and Selected Policy Issues
Cryptocurrency: The Economics of Money and Selected Policy Issues Updated April 9, 2020 Congressional Research Service https://crsreports.congress.gov R45427 SUMMARY R45427 Cryptocurrency: The Economics of Money and April 9, 2020 Selected Policy Issues David W. Perkins Cryptocurrencies are digital money in electronic payment systems that generally do not require Specialist in government backing or the involvement of an intermediary, such as a bank. Instead, users of the Macroeconomic Policy system validate payments using certain protocols. Since the 2008 invention of the first cryptocurrency, Bitcoin, cryptocurrencies have proliferated. In recent years, they experienced a rapid increase and subsequent decrease in value. One estimate found that, as of March 2020, there were more than 5,100 different cryptocurrencies worth about $231 billion. Given this rapid growth and volatility, cryptocurrencies have drawn the attention of the public and policymakers. A particularly notable feature of cryptocurrencies is their potential to act as an alternative form of money. Historically, money has either had intrinsic value or derived value from government decree. Using money electronically generally has involved using the private ledgers and systems of at least one trusted intermediary. Cryptocurrencies, by contrast, generally employ user agreement, a network of users, and cryptographic protocols to achieve valid transfers of value. Cryptocurrency users typically use a pseudonymous address to identify each other and a passcode or private key to make changes to a public ledger in order to transfer value between accounts. Other computers in the network validate these transfers. Through this use of blockchain technology, cryptocurrency systems protect their public ledgers of accounts against manipulation, so that users can only send cryptocurrency to which they have access, thus allowing users to make valid transfers without a centralized, trusted intermediary. -
![Can Ethereum Classic Reach 1000 Dollars Update [06-07-2021] 42 Loss in the Last 24 Hours](https://docslib.b-cdn.net/cover/0683/can-ethereum-classic-reach-1000-dollars-update-06-07-2021-42-loss-in-the-last-24-hours-490683.webp)
Can Ethereum Classic Reach 1000 Dollars Update [06-07-2021] 42 Loss in the Last 24 Hours
1 Can Ethereum Classic Reach 1000 Dollars Update [06-07-2021] 42 loss in the last 24 hours. At that time Bitcoin reached its all-time high of 20,000 and so did Ethereum ETH which surpassed 1,000. 000 to reach 1; Tezos XTZ is priced at 2. In the unlikely event of a significant change for the worst, we expect the Bitcoin price to continue appreciating. ERC-721 started as a EIP draft written by dete and first came to life in the CryptoKitties project by Axiom Zen. ERC-721 A CLASS OF UNIQUE TOKENS. It does not mandate a standard for token metadata or restrict adding supplemental functions. Think of them like rare, one-of-a-kind collectables. The Standard. Institutions are mandating that they invest in clean green technologies and that s what ethereum is becoming, she said. Unlike bitcoin s so-called proof of work, which rewards miners who are competing against each other to use computers and energy to record and confirm transactions on its blockchain, ethereum plans to adopt the more efficient proof of stake model, which chooses a block validator at random based on how much ether it controls. Kaspar explained her thesis Friday on Yahoo Finance Live, citing new updates coming to the cryptocurrency s network later this year. 42 loss in the last 24 hours. At that time Bitcoin reached its all-time high of 20,000 and so did Ethereum ETH which surpassed 1,000. 000 to reach 1; Tezos XTZ is priced at 2. In the unlikely event of a significant change for the worst, we expect the Bitcoin price to continue appreciating.