Outsets for Non-Determinism and Real-Time Execution
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Programmable Fieldbus Controllers 61
Programmable Fieldbus Cont rollers ŻŻ Section 2 Ż Section 3.1 Prog rammable Fieldbus Cont rollers Section 3.3 Ź PERSPECTO ® Control Panels PFC200 • Decentralized intelligence based on Prog rammable Fieldbus Cont rolle r XT R fieldbus couplers • Merging control and visualization • Maximum performance in a minimum • Programmable to IEC 61131-3 For demanding applications where the • 8.9 cm ... 38.1 cm (3.5” … 15”) space • WAGO-I/O-SYSTEM 750, modular following are critical: • High processing speed • Extreme temperature stability • Additional operating controls • Immunity to interference and (e.g., start/stop switch) impulse-voltage withstand • Based on Linux® also in • Vibration and shock resistance high-level language Cont rolle rs 3 Programmable Fieldbus Controllers 61 Page General Product Information 62 Ve rsions 63 Inte rf aces and Configurations 63 Installation Inst ructions 64 Item Numbe r Keys 65 Standa rds and Rated Conditions 65 ETHERNET TCP S S Net/IP r OFIBU R BACnet/IP IP KNX P CANopen Ethe CPU MODBU Othe rs Description Item No. IEC 60870-5 750-880 66 32-bit x x IEC 61850 ETHERNET Controller IEC 61400-25 750-881 68 750-885 70 x x Media redundancy ETHERNET Controller 32-bit 750-882 72 MODBUS RTU IEC 60870-5 32-bit x x IEC 61850 Telecontrol Controller 750-872 74 IEC 61400-25 3.2 ETHERNET TCP/IP Controller, x x MODBUS RTU 76 32-bit RS-232 750-873 PFC 32-bit x x ETHERNET Controller 750-852 78 32-bit x x KNX IP Controller 750-889 80 x x BACnet/IP Controller 750-831 82 32 Bit x x BACnet/IP Controller 750-830 84 32 Bit x BACnet MS/TP -

IO-Link (Single-Drop Digital Communication System) for Sensors and Actuators
5 IO-Link (Single-Drop Digital Communication System) for Sensors and Actuators 5.1. Motivation.and.Objectives.for.a.New.Technology....................... 5-1 5.2. IO-Link.Technology.......................................................................... 5-2 Purpose.of.Technology. •. Positioning.within.the.Automation. Hierarchy. •. Wiring,.Connectors,.and.Power. •. Communication. Features.of.IO-Link. •. Role.of.a.Master. •. IO-Link. Configuration. •. Mapping.to.Fieldbuses.and.System. Integration. •. Implementation.and.Engineering.Support. •. Test.and. Wolfgang Stripf Certification. •. Profiles. •. Functional.Safety. •. Standardization PROFIBUS and PROFINET Abbreviations.................................................................................................5-8 International References.......................................................................................................5-9 5.1 Motivation and objectives for a new technology Th .increased.use.of.microcontrollers.embedded.in.low-cost.sensors.and.actuators.has.provided.oppor- tunities.for.adding.diagnosis.and.configuration.data.to.support.increasing.application.requirements. Th .driving.force.for.a.new.technology.called.IO-LinkTM*.has.been.the.need.of.these.low-cost.sensors. and.actuators.to.exchange.the.diagnosis.and.configuration.data.with.a.controller.(PC.or.PLC).using.a. low-cost.digital.communication.technology.while.maintaining.backward.compatibility.with.the.cur- rent.digital.input.and.digital.output.(DI/DO).signals. Another.driving.force.is.cost.reduction.and.substitution.of.error-prone.analog.transmission.such.as. 0–10.V..Using.IO-Link.avoids.digital/analog.conversion.on.the.sensor.side.and.analog/digital.conver- sion.on.the.controller.side. In.fieldbus.concepts,.the.IO-Link.defines.a.generic.interface.for.connecting.sensors.and.actuators.to. a.Master†.unit,.which.may.be.combined.with.gateway.capabilities.to.become.a.fieldbus.remote.I/O.node. Any.IO-Link-compliant.Device‡.can.be.attached.to.any.available.interface.port.of.the.Master..Devices. -

Building Functional Safety Into Industrial Robotics
BUILDING FUNCTIONAL SAFETY INTO INDUSTRIAL ROBOTICS Rian Whitton Principal Analyst EXECUTIVE SUMMARY TABLE OF CONTENTS Functional safety is critical to many modern robotic applications and will become more so. In the near future, many robots will run in areas where they interact directly Executive Summary ................................1 and indirectly with workers, and the tasks they perform will disproportionately relate The Market for Industrial Robotics ...........2 The Potential of the Robotics Industry .....................2 to production logistics and moving goods for the general public. If a robot malfunctions, New Robots, New Demands ...................................4 there is a risk to the surrounding workers, to product safety, and to public safety. This Functional Safety Is Crucial for the Industry to Meet risk amplifies as robots are increasingly required to handle multiple tasks and navigate Its Potential ............................................................5 Regulations .............................................................6 crowded environments. So, mitigating safety risks under these conditions will become Embedded Systems for Robotics ..............7 a fundamental requirement that cannot be addressed without considering security as RTOS and the Benefits of Microkernel an integral part of robot design. Architecture ............................................................8 Hypervisors-as-a-Solution .......................................9 This is where functional safety of the underlying software and -

Simulation Tool Based Structural Text Generation for Programmable Logic Controllers
Kaarle Patomäki Simulation Tool Based Structural Text Generation for Programmable Logic Controllers Thesis submitted for examination for the degree of Master of Science in Technology Turku 23.7.2020 Supervisor: Professori Kari Tammi Advisor: Juuso Kelkka Aalto University, P.O. BOX 11000, 00076 AALTO www.aalto.fi Abstract of master's thesis Author Kaarle Patomäki Title of thesis Simulation Tool Based Structural Text Generation for Programmable Logic Controllers Master programme Mechanical Engineering Code ENG25 Thesis supervisor Associate Professor Kari Tammi Thesis advisor(s) Juuso Kelkka, M. Sc. (Tech.) Date 23.7.2020 Number of pages 50+8 Language English Abstract Model-based design is a relatively new technique of developing software for embedded systems. It aims to reduce the cost of the software development process by generating the code from a simulation model. The code is generated automatically using a tool that is developed for this purpose. This way the errors in the system can be found and eliminated early in the development process compared to traditional software development project for embedded systems. As mentioned, the tools are at the time of this study still relatively new, and especially when considering code that has to comply with functional safety standards, the code has to fulfill certain requirements and it has to be clear enough so that it can be traced back to each function of the model. This study aims to determine how well these methods can be used with software development for embedded systems in mind. More precisely, this thesis focuses on MathWorks’ Simulink as the modelling software, and CODESYS as the coding language of the programmable logic controller and ultimately the compatibility of these with each other. -
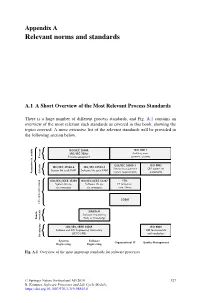
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

Standards Action Layout SAV3438.Fp5
PUBLISHED WEEKLY BY THE AMERICAN NATIONAL STANDARDS INSTITUTE 25 West 43rd Street, NY, NY 10036 VOL. 34, #38 September 19, 2003 Contents American National Standards Call for Comment on Standards Proposals................................................. 2 Call for Comment Contact Information........................................................ 5 Initiation of Canvasses.................................................................................. 7 Final Actions .................................................................................................. 8 Project Initiation Notification System (PINS) .............................................. 10 International Standards ISO Draft Standards ...................................................................................... 13 ISO Newly Published Standards .................................................................. 15 Registration of Organization Names in the U.S. ........................................... 18 Proposed Foreign Government Regulations ................................................ 18 Information Concerning.................................................................................. 19 Standards Action is now available via the World Wide Web For your convenience Standards Action can now be down- loaded from the following web address: http://www.ansi.org/news_publications/periodicals/standard s_action/standards_action.aspx?menuid=7 American National Standards Call for comment on proposals listed This section solicits your comments on proposed -

Guideline for Applying Functional Safety to Autonomous Systems in Mining
20200709_Guideline_for_Applying_Functional_Safety_to_Autonomous_Systems- GMG-AM-FS-v01-r01 GUIDELINE FOR APPLYING FUNCTIONAL SAFETY TO AUTONOMOUS SYSTEMS IN MINING SUBMITTED BY Functional Safety for Autonomous Equipment Sub-committee VERSION DATE 09 Jul 2020 APPROVED BY Autonomous Mining Working Group 31 Jul 2020 and GMG Executive Council 12 Aug 2020 PUBLISHED 18 Aug 2020 DATE DOCUMENT TO BE REVIEWED 18 Aug 2022 PREPARED BY THE FUNCTIONAL SAFETY FOR AUTONOMOUS EQUIPMENT SUB-COMMITTEE OF THE AUTONOMOUS MINING WORKING GROUP Global Mining Guidelines Group (GMG) ii | GUIDELINE FOR APPLYING FUNCTIONAL SAFETY TO AUTONOMOUS SYSTEMS IN MINING DISCLAIMER Although the Global Mining Guidelines Group (GMG) believes that the information on https://gmggroup.org, which includes guidelines, is reliable, GMG and the organizations involved in the preparation of the guidelines do not guarantee that it is accu- rate or complete. While the guidelines are developed by participants across the mining industry, they do not necessarily rep- resent the views of all of the participating organizations. This information does not replace or alter requirements of any national, state, or local governmental statutes, laws, regulations, ordinances, or other requirements. Your use of GMG guide- lines is entirely voluntary. CREDITS Organizations Involved in the Preparation of these Guidelines ABB, Abbott Risk Consulting, Agnico Eagle, Airobiotics, Alex Atkins & Associates, Ambuja Cements, AMOG Consulting, Antofa- gasta Minerals, Australian Droid + Robot, Autonomous Solutions, -

IO-LINK HANDBOOK Second Edition
IO-LINK HANDBOOK Second Edition www.maximintegrated.com/io-link Table of Contents Introduction .......................................................................................3 Thermal Performance..........................................................................................29 Section 1: Introduction to IO-Link..................................................4 Discrete Solution..........................................................................................31 Old School Sensor ............................................................................................ 4 Integrated Solution.......................................................................................32 Tiny Binary Sensor Drivers .............................................................................. 4 Selecting a TVS.....................................................................................................33 IO-Link: An Open, Low-Cost Sensor Interface .............................................5 IO-Link Protection..........................................................................................33 IO-Link Nodes .....................................................................................................5 How 65V (Abs Max) Helps with Protection (vs. 40V).........................33 IO-Link System................................................................................................... 6 Advantages of 65V Abs Max for Protection............................................33 IO-Link Interface Standardized -
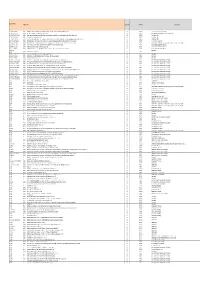
STANDARDS LIST Neu.Xlsx
Document‐Number Published Title Organization Committee Committee Title IEC 100/2536/CD * IEC 63002 2015‐07 IEC 63002, Ed. 1.0: Idenficaon and CommunicaonInteroperability Method for External Power Supplies Used WithPortable Compung Devices (TA 14) IEC IEC/TC 100 Audio, video and multimedia systems and equipment IEC 115/105/CD *IEC/TR 62978 2015‐01 IEC/TR 62978, Ed. 1: Guidelines on Asset Management forHVDC Installaons IEC IEC/TC 115 High Voltage Direct Current (HVDC) transmission for DC voltages above 100 kV IEC 118/29/DPAS* IEC/PAS 62746‐199 2013‐09 System interfaces and communication protocol profiles relevant for systems connected to the smart grid ‐ Open Automated Demand Response (OpenADR 2.0 Profile Specification) IEC IEC/PC 118 Smart grid user interface IEC 118/46/CD *IEC 62746‐10‐2 2014‐12 OASIS Energy Interoperation Version 1.0 Specification IEC IEC/PC 118 Smart grid user interface IEC 118/47/CD * IEC 62746‐10‐1 2015‐01 IEC 62746‐10‐1: Systems interface between customer energymanagement system and the power management system ‐ Part10 ‐1: Open Automated Demand Response (OpenADR 2.0bPro file Specificaon) IEC IEC/PC 118 Smart grid user interface IEC 22H/192/CD * IEC/TS 62040‐4‐1 2015‐04 IEC/TS 62040‐4‐1: Uninterrupble power systems (UPS) ‐ Part 4‐1: Environmental aspects ‐ Product Category Rules (PCR) for life Cycle Assessment and environmental declaraons IEC IEC/SC 22H Uninterruptible power systems (UPS) IEC 3/1224A/CD * IEC 81346‐2 2015‐05 Industrial systems, installaons and equipment and industrialproducts ‐ Structuring principles and reference designaons ‐ Part 2: Classificaon of objects and codes for classes IEC IEC/TC 3 Information structures and elements, identification and marking principles, documentation and graphical symbols IEC 3D/225A/CD * IEC 62656‐5 2014‐03 IEC 62656‐5, Ed. -

Standards for Enabling Trade— Mapping and Gap Analysis Study
Standards for Enabling Trade— Mapping and Gap Analysis Study An IA-CEPA Early Outcomes Initiative November 2017 Standards For Enabling Trade—Mapping and Gap Analysis Study 2 An IA-CEPA Early Outcomes Initiative – November 2017 Contents ListofFigures..............................................................................................................3 Abbreviations...............................................................................................................4 Terms..........................................................................................................................6 Acknowledgements......................................................................................................8 ExplanatoryNotes........................................................................................................8 Foreword.....................................................................................................................9 Recommendations.....................................................................................................10 ExecutiveSummary....................................................................................................11 Introduction................................................................................................................13 ProjectPurpose.........................................................................................................13 Objectives..................................................................................................................13 -

Internet of Things Risk Analysis and Assessment
Deliverable 3: Internet of Things Risk Analysis and Assessment PROJECT RISIOT: MARKET ANALYSIS AND RISK ASSESSMENT TO ACCELERATE THE ADOPTION OF THE INTERNET OF THINGS IN AUSTRIAN ENTERPRISES Sandra König, Stefan Schiebeck, Stefan Schauer, Martin Latzenhofer, Peter Mayer, Geraldine Fitzpatrick MAY, 2017 IoT Risks The project RISIoT - MARKET ANALYSIS AND RISK ASSESSMENT TO ACCELERATE THE ADOPTION OF THE INTERNET OF THINGS IN AUSTRIAN ENTERPRISES – is conducted between September 2016 and August 2017 by the following consortium: IDC Central Europe GmbH Austrian Institute of Technology GmbH Technical University of Vienna Austrian Computer Society The RISIoT project is co-funded under the „ICT of the Future“ programme by the Austrian Ministry for Transport, Innovation and Technology and the Austrian Research Promotion Agency (FFG). Project number: 855450 1 IoT Risks TABLE OF CONTENTS Table of Contents .......................................................................................................................................................2 List of Figures ..............................................................................................................................................................3 List of Tables ...............................................................................................................................................................3 1. Introduction ........................................................................................................................................................0 -

Programmable Fieldbus Controller XTR
Programmable Fieldbus Controller XTR Programmable Fieldbus Controller XTR ŻŻŻSection 2 ŻŻ Section 3.1 Ż Section 3.2 PERSPECTO® Control Panels PFC200 Programmable Fieldbus Controllers For demanding applications where the following are critical: • Merging control and visualization • Maximum performance in a minimum • Decentralized intelligence based on • Extreme temperature stability • 8.9 cm ... 38.1 cm (3.5” … 15”) space fieldbus couplers • Immunity to interference and • High processing speed • Programmable to IEC 61131-3 impulse-voltage withstand • Additional operating controls • WAGO-I/O-SYSTEM 750, modular • Vibration and shock resistance (e.g., start/stop switch) • Based on Linux® also in high-level language 3 Programmable Fieldbus Controller XTR 108 General Product Information Programmable Fieldbus Controller Link between Process Data and IT Application Superior reliability in extreme climates XTR: — Even under eXTReme Conditions Regardless of freezing cold, extreme heat and Taking it to the eXTReme — The controllers ideally combine real-time requi- high humidity, the WAGO-I/O-SYSTEM 750 XTR The standard for 750 XTR rements with IT functionality. They support both is engineered for absolute dependability in all MODBUS/TCP and ETHERNET/IP for use in indus- climatic conditions. The XTR version of the pro- grammable fieldbus coupler is unfazed by both Programmable XTR fieldbus controllers are trial environments. HTTP, SNTP, SNMP, FTP, BootP, freezing cold down to -40 °C and scorching heat easily recognized by their dark gray hous- DHCP, DNS and other protocols simplify integration ings. The WAGO-I/O-SYSTEM 750 XTR’s up to +70 °C. And this applies to both initial into IT environments. Integrated Web pages and start-up and daily operation.