Guideline for Applying Functional Safety to Autonomous Systems in Mining
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

International Standards, Approaches and Frameworks Relevant to Software Quality Management and Software Process Improvement
International standards, approaches and frameworks relevant to Software Quality Management and Software Process Improvement To help organizations managing software quality and improving software processes several standards, models, approaches and frameworks have been developed during the last decades. The most widely known and recognized of them are presented in this document. • Capability Maturity Model (CMM) • CMM Integration (CMMI) • Personal Software Process (PSP) and Team Software Process (TSP) • ISO 9000 standards family • TickIT • ISO/IEC TR 15504 Information Technology - Software Process Assessment (SPICE) • ISO/IEC 12207 Information Technology - Software Life-Cycle Processes • BOOSTRAP • Rational Unified Process CMM Publication Date: Version 1.1 - February 1993 Description: The Capability Maturity Model for Software (SW-CMM or CMM) is a model used by organizations for appraising the maturity of their software processes and for identifying practices that will increase the maturity of those processes. It was developed by the Software Engineering Institute, in cooperation with industry representatives. The Software CMM has become a de facto standard for assessing and improving software processes. Through the SW-CMM, the SEI and community have put in place an effective means for modeling, defining, and measuring the maturity of the processes used by software professionals. The Capability Maturity Model for Software describes the principles and practices underlying software process maturity and is intended to help software organizations -

A Stone Man Version
Guide to the Software Engineering Body of Knowledge AA SSttoonnee MMaann Veerrssiioonn (Version 0.7) April 2000 A project of the Software Engineering Coordinating Committee (Joint IEEE Computer Society - ACM committee ) Corporate support by: Project managed by: Executive Editors: Alain Abran, Université du Québec à Montréal James W. Moore, The MITRE Corp. Editors: Pierre Bourque, Université du Québec à Montréal Robert Dupuis, Université du Québec à Montréal Chair of the Software Engineering Coordinating Committee Leonard L. Tripp, IEEE Computer Society Copyright © 2000, Institute of Electrical and Electronics Engineers, Inc. All rights reserved. PREFACE TO THE SWEBOK GUIDE 1. Software engineering is an emerging discipline but there are unmistakable trends indicating an 10. Purpose increasing level of maturity: 11. The purpose of this Guide is to provide a 2. w McMaster University (Canada), the consensually-validated characterization of the Rochester Institute of Technology (US), the bounds of the software engineering discipline University of Sheffield (UK), the and to provide a topical access to the Body of University of New South Wales (Australia) Knowledge supporting that discipline. The Body and other universities around the world now of Knowledge is subdivided into ten Knowledge offer undergraduate degrees in software Areas (KA) and the descriptions of the KAs are engineering. designed to discriminate among the various important concepts, permitting readers to find 3. w The Software Capability Maturity Model and ISO 9000 are used to certify their way quickly to subjects of interest. Upon organizational capability for software finding a subject, readers are referred to key engineering. papers or book chapters selected because they succinctly present the knowledge. -

Guide to the Software Engineering Body of Knowledge
Guide to the Software Engineering Body of Knowledge AA SSttoonnee MMaann VVeerrssiioonn (Version 0.5) October 1999 A project of the Software Engineering Coordinating Committee (Joint IEEE Computer Society - ACM committee ) Corporate support by: Project managed by: Co-Executive Editors: Alain Abran, Université du Québec à Montréal James W. Moore, The MITRE Corp. Editors: Pierre Bourque, Université du Québec à Montréal Robert Dupuis, Université du Québec à Montréal Project Champion: Leonard L. Tripp, IEEE Computer Society Table of Contents INTRODUCTORY TEXT FROM THE EDITORIAL TEAM KNOWLEDGE AREA DESCRIPTION : - Software Configuration Management - Software Construction - Software Design - Software Engineering Infrastructure - Software Engineering Management - Software Engineering Process - Software Evolution and Maintenance - Software Quality Analysis - Software Requirement Analysis - Software Testing APPENDIX A KNOWLEDGE AREA DESCRIPTION SPECIFICATIONS FOR THE STONE MAN VERSION OF THE GUIDE TO THE SOFTWARE ENGINEERING BODY OF KNOWLEDGE – VERSION 0.25 INTRODUCTORY TEXT FROM THE EDITORIAL TEAM The IEEE Computer Society and the Association for Computing Machinery are working on a joint project to develop a guide to the Software Engineering Body Of Knowledge (SWEBOK). This is the current draft (version 0.5 completed in September 1999) of the Stoneman version of the Guide1. Articulating a body of knowledge is an essential step toward developing a profession because it represents a broad consensus regarding the contents of the discipline. Without such a consensus, there is no way to validate a licensing examination, set a curriculum to prepare individuals for the examination, or formulate criteria for accrediting the curriculum. The project team is currently working on an update to this draft version of the Guide based on the results of the second review cycle. -

Voluntary Voting System Guidelines VVSG 2.0 Recommendations for Requirements for the Voluntary Voting System Guidelines 2.0
Voluntary Voting System Guidelines VVSG 2.0 Recommendations for Requirements for the Voluntary Voting System Guidelines 2.0 February 29, 202010, 2021 Prepared for the Election Assistance Commission At the direction of the Technical Guidelines Development Committee 1 Acknowledgements Chair of the TGDC: Dr. Walter G. Copan Director of the National Institute of Standards and Technology (NIST) Gaithersburg, MD Representing the EAC Standards Board: Robert Giles Paul Lux Director Supervisor of Elections New Jersey Division of Elections Okaloosa County Trenton, NJ Crestview, FL Representing the EAC Board of Advisors: Neal Kelley Linda Lamone Registrar of Voters Administrator of Elections Orange County Maryland State Board of Orange County, CA ElectionElections Annapolis, MD Representing the Architectural and Transportation Barrier, and Compliance Board (Access Board): Marc Guthrie Sachin Pavithran Public Board Member Public Board Member Newark, OH Logan, UT Representing the American National Standards Institute (ANSI): Mary Saunders Vice President, Government Relations & Public Policy American National Standards Institute Washington, DC Representing the Institute of Electrical and Electronics Engineers: Dan Wallach Professor, Electrical & Engineering Computer Science Rice University Houston, TX Representing the National Association of State Election Directors (NASED): Lori Augino Judd Choate Washington State Director of Elections State Elections Director Washington Secretary of State Colorado Secretary of State Olympia, WA Denver, CO 2 Requirements -

Building Functional Safety Into Industrial Robotics
BUILDING FUNCTIONAL SAFETY INTO INDUSTRIAL ROBOTICS Rian Whitton Principal Analyst EXECUTIVE SUMMARY TABLE OF CONTENTS Functional safety is critical to many modern robotic applications and will become more so. In the near future, many robots will run in areas where they interact directly Executive Summary ................................1 and indirectly with workers, and the tasks they perform will disproportionately relate The Market for Industrial Robotics ...........2 The Potential of the Robotics Industry .....................2 to production logistics and moving goods for the general public. If a robot malfunctions, New Robots, New Demands ...................................4 there is a risk to the surrounding workers, to product safety, and to public safety. This Functional Safety Is Crucial for the Industry to Meet risk amplifies as robots are increasingly required to handle multiple tasks and navigate Its Potential ............................................................5 Regulations .............................................................6 crowded environments. So, mitigating safety risks under these conditions will become Embedded Systems for Robotics ..............7 a fundamental requirement that cannot be addressed without considering security as RTOS and the Benefits of Microkernel an integral part of robot design. Architecture ............................................................8 Hypervisors-as-a-Solution .......................................9 This is where functional safety of the underlying software and -
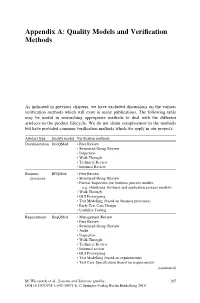
Appendix A: Quality Models and Verification Methods
Appendix A: Quality Models and Verification Methods As indicated in previous chapters, we have excluded discussions on the various verification methods which still exist in many publications. The following table may be useful in researching appropriate methods to deal with the different artefacts in the product lifecycle. We do not claim completeness in the methods but have provided common verification methods which we apply in our projects. Artefact type Quality model Verification methods Documentation DocQMod • Peer Review • Structured Group Review • Inspection • Walk Through • Technical Review • Informal Review Business BPQMod • Peer Review processes • Structured Group Review • Formal Inspection (on business process models, e.g. swimlanes, business and application process models) • Walk Through • GUI Prototyping • Test Modelling (based on business processes) • Early Test Case Design • Usability Testing Requirements ReqQMod • Management Review • Peer Review • Structured Group Review • Audit • Inspection • Walk Through • Technical Review • Informal review • GUI Prototyping • Test Modelling (based on requirements) • Test Case Specification (based on requirements) (continued) M. Wieczorek et al., Systems and Software Quality, 165 DOI 10.1007/978-3-642-39971-8, © Springer-Verlag Berlin Heidelberg 2014 166 Appendix A: Quality Models and Verification Methods Artefact type Quality model Verification methods Architecture ArchQMod • Peer Review • Structured Group Review • Formal Inspection • ATAM • Prototyping (including functional and non-functional testing) • FMEA Database DataQMod • Formal Inspection (on e.g. normalisation) • Peer Review (on indexing, SQL statements, stored procedures) • Structured Group Review • Functional Testing (by application) • Non-functional testing (including performance and security) Source code CodeQMod • Peer Review • Walk Through • Formal Inspection (e.g. style guides, coding standards) • Static Source Code Analysis (tool based) • Profiling (e.g. -

Appendix G Systems General Requirements
BROADWAY SUBWAY PROJECT Commercial in Confidence PROJECT AGREEMENT EXECUTION COPY SCHEDULE 4 Appendix G Systems General Requirements BROADWAY SUBWAY PROJECT Commercial in Confidence PROJECT AGREEMENT EXECUTION COPY SCHEDULE 4: APPENDIX G: SYSTEM GENERAL REQUIREMENTS - 2 - Table of Contents 1 APPENDIX G – Systems GENERAL REQUIREMENTS .................................................................. 7 1.1 Introduction .......................................................................................................................................... 7 1.2 Requirements Delivery ........................................................................................................................ 7 1.3 Standards .............................................................................................................................................. 8 1.4 Systems Plan ........................................................................................................................................ 8 1.5 Design Life of the Systems .................................................................................................................. 9 1.6 Systems Design Management .............................................................................................................. 9 1.6.1 Requirements Specification Overview ............................................................................................ 10 1.6.2 Requirements Analysis Overview .................................................................................................. -

The Evolution of Software Configuration Management
ISSN 2278-3091 Syahrul Fahmy et al., International Journal of AdvancedVolume Trends 9, No.1. in Computer3, 2020 Science and Engineering, 9(1.3), 2020, 50 - 63 International Journal of Advanced Trends in Computer Science and Engineering Available Online at http://www.warse.org/IJATCSE/static/pdf/file/ijatcse0891.32020.pdf https://doi.org/10.30534/ijatcse/2020/0891.32020 The Evolution of Software Configuration Management 1 2 3 1 1 Syahrul Fahmy , Aziz Deraman , Jamaiah Yahaya , Akhyari Nasir , Nooraida Shamsudin 1University CollegeTATI, Malaysia, [email protected] 2Universiti Malaysia Terengganu, Malaysia 3Universiti Kebangsaan Malaysia, Malaysia processing and implementation status, and verify compliance ABSTRACT with specified requirements” [3]. Software Configuration Management (SCM) is a discipline in “a management activity that applies technical and software engineering for managing changes to software administrative direction over the life cycle of a product, its products using standard processes and tools. This article configuration items, and related product configuration presents the evolution of SCM since its inception, information. It provides identification and traceability, the highlighting the components, application to other areas, status of achievement, and access to accurate information in change management and software quality. Research and all phases of the life cycle” [4]. development in SCM are highly motivated by the problems at hand in software development. SCM process and activities are This paper presents the evolution of SCM, discussing its sound, guided by international standards and industry best components, application to other areas, change management practice. Commercial and proprietary tools are aplenty, and and software quality. the underlying techniques are no longer confined to SCM. -
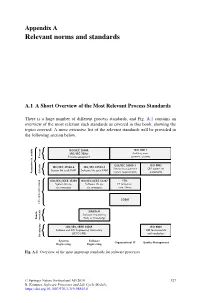
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

Manual on the Quality Management System for Aeronautical Information Services ______
Doc 9839 AN/xxx Manual on the Quality Management System for Aeronautical Information Services ________________________________ Approved by the Secretary General and published under his authority First Edition — XXXX International Civil Aviation Organization Published in English, .................... by the INTERNATIONAL CIVIL AVIATION ORGANIZATION 999 University Street, Montréal, Quebec, Canada H3C 5H7 For ordering information and for a complete listing of sales agents and booksellers, please go to the ICAO website at www.icao.int Doc 9839, Manual on the Quality Management System for Aeronautical Information Services Order Number: ISBN © ICAO 2010 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, without prior permission in writing from the International Civil Aviation Organization. AMENDMENTS Amendments are announced in the supplements to the Catalogue of ICAO Publications; the Catalogue and its supplements are available on the ICAO website at www.icao.int. The space below is provided to keep a record of such amendments. RECORD OF AMENDMENTS AND CORRIGENDA AMENDMENTS CORRIGENDA No. Date Entered by No. Date Entered by TABLE OF CONTENTS Page Foreword .......................................................................................................................................................... (vii) Acronyms ........................................................................................................................................................ -

Standards Action Layout SAV3438.Fp5
PUBLISHED WEEKLY BY THE AMERICAN NATIONAL STANDARDS INSTITUTE 25 West 43rd Street, NY, NY 10036 VOL. 34, #38 September 19, 2003 Contents American National Standards Call for Comment on Standards Proposals................................................. 2 Call for Comment Contact Information........................................................ 5 Initiation of Canvasses.................................................................................. 7 Final Actions .................................................................................................. 8 Project Initiation Notification System (PINS) .............................................. 10 International Standards ISO Draft Standards ...................................................................................... 13 ISO Newly Published Standards .................................................................. 15 Registration of Organization Names in the U.S. ........................................... 18 Proposed Foreign Government Regulations ................................................ 18 Information Concerning.................................................................................. 19 Standards Action is now available via the World Wide Web For your convenience Standards Action can now be down- loaded from the following web address: http://www.ansi.org/news_publications/periodicals/standard s_action/standards_action.aspx?menuid=7 American National Standards Call for comment on proposals listed This section solicits your comments on proposed -

Parameterization, Analysis, and Risk Management in a Comprehensive Management System with Emphasis on Energy and Performance (ISO 50001: 2018)
energies Article Parameterization, Analysis, and Risk Management in a Comprehensive Management System with Emphasis on Energy and Performance (ISO 50001: 2018) P. Pablo Poveda-Orjuela 1,*, J. Carlos García-Díaz 2 , Alexander Pulido-Rojano 3 and Germán Cañón-Zabala 4 1 ASTEQ Technology, 53 Street No. 53-15, Barranquilla 080020, Colombia 2 Centre for Quality and Change Management, Universitat Politècnica de València, Camino de Vera, s/n. 46022 Valencia, Spain; [email protected] 3 Industrial Engineering Department, Universidad Simón Bolívar, Av. 59 No. 59-92, Barranquilla 080020, Colombia; [email protected] 4 QUARA Group, 157 Street No. 13 B-20, Bogotá 110121, Colombia; [email protected] * Correspondence: [email protected] or [email protected]; Tel.: +57-3008897111 Received: 7 September 2020; Accepted: 13 October 2020; Published: 26 October 2020 Abstract: The future of business development relies on the effective management of risks, opportunities, and energy and water resources. Here, we evaluate the application of best practices to identify, analyze, address, monitor, and control risks and opportunities (R/O) according to ISO 31000 and 50000. Furthermore, we shed light on tools, templates, ISO guides, and international documents that contribute to classifying, identifying, formulating control, and managing R/O parameterization in a comprehensive management system model, namely CMS QHSE3+, which consists of quality (Q), health and safety (HS), environmental management (E), energy efficiency (E2), and other risk components (+) that include comprehensive biosecurity and biosafety. By focusing on the deployment of R/O-based thinking (ROBT) at strategic and operational levels, we show vulnerability reduction in CMS QHSE3+ by managing energy, efficiency, and sustainability.