Write Once, Pwn Anywhere
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sources of Information About the HP Noteb
9 Jan 2002 This file contains the most up-to-date information on the following topics: Sources of Information about the HP notebook computer and Windows Precautions Changing Display Settings Setting the Display after Docking (Windows 2000 or XP) Fixing Display Settings when Docking Using Wireless LAN Using HP Presentation Ready Setting Up a TV Undocking with MusicMatch (Windows 2000 or XP) Checking the Modem Dialing Setting Working with Graphic-Intensive Applications Running in MS-DOS Mode Windows 98 Disabling the Infrared Port before Recovering Software Windows 2000 Running the Tour of Windows 2000 Reinstalling HP One-Touch Windows XP Using Extended Desktop Microsoft Plus! Not Recommended Best Practices for Using Your HP Notebook Computer Physical Care General Use Sources of Information * The printed Startup Guide introduces the notebook computer and shows you the basics. It also contains troubleshooting information. * The online Reference Guide shows how to set up the operating system, install and connect accessories, and maintain and upgrade the computer (for Windows 98 or 2000, click Start, Programs, HP Library, or for Windows XP, click Start, Help and Support, HP Library). * The Microsoft Windows manual, shipped with your computer, contains information about using the standard features of your Windows operating system. * For updates to the BIOS and other technical documentation, connect to our website at http://www.hp.com/go/support. Precautions This section describes certain situations that could cause serious loss of data. Do not remove a data storage PC Card while it is actively reading or writing. This could cause its data to become corrupted. Certain applications, such as Intuit's Quicken, keep their working files open, and they update the files as you make changes. -

Interaction Between Web Browsers and Script Engines
IT 12 058 Examensarbete 45 hp November 2012 Interaction between web browsers and script engines Xiaoyu Zhuang Institutionen för informationsteknologi Department of Information Technology Abstract Interaction between web browser and the script engine Xiaoyu Zhuang Teknisk- naturvetenskaplig fakultet UTH-enheten Web browser plays an important part of internet experience and JavaScript is the most popular programming language as a client side script to build an active and Besöksadress: advance end user experience. The script engine which executes JavaScript needs to Ångströmlaboratoriet Lägerhyddsvägen 1 interact with web browser to get access to its DOM elements and other host objects. Hus 4, Plan 0 Browser from host side needs to initialize the script engine and dispatch script source code to the engine side. Postadress: This thesis studies the interaction between the script engine and its host browser. Box 536 751 21 Uppsala The shell where the engine address to make calls towards outside is called hosting layer. This report mainly discussed what operations could appear in this layer and Telefon: designed testing cases to validate if the browser is robust and reliable regarding 018 – 471 30 03 hosting operations. Telefax: 018 – 471 30 00 Hemsida: http://www.teknat.uu.se/student Handledare: Elena Boris Ämnesgranskare: Justin Pearson Examinator: Lisa Kaati IT 12 058 Tryckt av: Reprocentralen ITC Contents 1. Introduction................................................................................................................................ -

IE 5.5 and Netscape 4.75 - Why Upgrade? ..Page 1
In This Issue . IE 5.5 and Netscape 4.75 - Why Upgrade? ..page 1 WindowsME for Home Computing ..…..…..page 1 Critical Updates are Essential ……..……….page 1 Win 95/98 Web Browser Upgrade.…………page 2 Permanent LRC Stations…………...……….page 2 cc:Mail is Retiring ……..…………..………..page 2 The newsletter for IPFW computer users Information Technology Services October 2000 Courses & Resources…………….……….….page 2 IE 5.5 and Netscape for Home 4.75 - Why Upgrade? Computing Campus surfers should update their browsers to the Microsoft recently released its upgrade to Windows 98 latest versions of Netscape and Internet Explorer (IE). for home computing — Windows Millennium (WindowsMe). Windows users may do so by the following instructions on Follett's IPFW Bookstore is now offering the CD to students, page 2. Macintosh users may obtain the instructions for faculty, and staff as part of IU's licensing agreement with creating an alias for either or both programs from the Help Microsoft. Is the upgrade for you? Windows Millennium Desk (e-mail: [email protected]). includes: Very basic digital media editing tools Why upgrade? In general, obtaining the latest 4 IE 5.5 (also downloadable for Windows 98) version of your favorite browser helps ensure that you have 4 4 Media Player 7 (also downloadable for Windows 98) the most capable and secure browser for today's Web If you have no compelling need for the above features environment. Specifically, the newest and most significant or if you take the time to do wnload IE 5.5 and/or Media Player 7 features of each include: for Windows 98, you may want to skip this upgrade. -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -
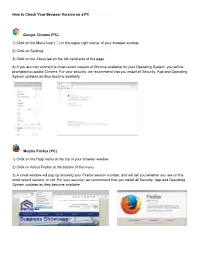
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Page 1 of 3 How to Enable NTLM 2 Authentication 2/8/2012 Http
How to enable NTLM 2 authentication Page 1 of 3 Article ID: 239869 - Last Review: January 25, 2007 - Revision: 4.7 How to enable NTLM 2 authentication System Tip This article applies to a different version of Windows than the one you are using. Content in this article may not be relevant to you. Visit the Windows 7 Solution Center This article was previously published under Q239869 SUMMARY Historically, Windows NT supports two variants of challenge/response authentication for network logons: • LAN Manager (LM) challenge/response • Windows NT challenge/response (also known as NTLM version 1 challenge/response) The LM variant allows interoperability with the installed base of Windows 95, Windows 98, and Windows 98 Second Edition clients and servers. NTLM provides improved security for connections between Windows NT clients and servers. Windows NT also supports the NTLM session security mechanism that provides for message confidentiality (encryption) and integrity (signing). Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. NTLM 2 has been available for Windows NT 4.0 since Service Pack 4 (SP4) was released, and it is supported natively in Windows 2000. You can add NTLM 2 support to Windows 98 by installing the Active Directory Client Extensions. After you upgrade all computers that are based on Windows 95, Windows 98, Windows 98 Second Edition, and Windows NT 4.0, you can greatly improve your organization's security by configuring clients, servers, and domain controllers to use only NTLM 2 (not LM or NTLM). -

Windows 95, Windows 98, Windows 98SE, and Windows ME Courtesy of Nashville Home Linux Solutions
Important information for users of Windows 95, Windows 98, Windows 98SE, and Windows ME courtesy of Nashville Home Linux Solutions FACT: As of July 2006, Microsoft has officially ended support for Windows 95, Windows 98, Windows 98SE, and Windows ME (Millennium Edition). What does this mean for you? Microsoft©s end-of-support announcement means that users of Windows 95, 98, and ME will no longer receive security updates, bug fixes, and other patches for their computer©s operating system. It also means that future releases of Microsoft software (such as Media Player, Internet Explorer, and Outlook Express) will no longer support these operating systems. Users of these versions of Windows will not benefit from enhanced features and security in these new versions. Why should I be concerned? Windows 95, 98, and ME are based around the DOS operating system, an inherently insecure operating system. Users of DOS-based Windows will become increasingly at risk for viruses, spyware, malware, and system intrusions as new holes and exploits are discovered in these operating systems and the older software that runs on them. In addition, software vendors (including makers of anti-virus and other security products) will be phasing out support for these operating systems now that Microsoft has ended its support. If you are connecting your DOS-based Windows operating system to the Internet, you need to take action to secure your computer. What are my options? If you would like to continue to operate on your current hardware, you have a few options available to you: 1. Upgrade Windows Microsoft©s only currently-available Windows workstation operating system is Windows XP (Home or Professional). -

Introductory Javascript Made Easy™Purposesv.1.0
A publication of TeachUcomp Incorporated. Copyright © TeachUcomp, Inc. 2014 only! Mastering Introductory JavaScript Made Easy™purposesv.1.0 teachUcomp, inc.® evaluation…it’s all about you for www.teachucomp.com at us Sample- Visit Mastering Introductory JavaScript Made Easy™ v.1.0 Copyright: Copyright © 2014 by TeachUcomp, Inc. All rights reserved. This publication, or any part thereof, may not be reproduced or stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, recording, photocopying, or otherwise, without the express written permission of TeachUcomp, Inc. For PDF manuals, TeachUcomp, Inc. allows the owner of the PDF manual to make up to 2 additional copies of the PDF manual that the owner may place on up to 2 additional non-sharedonly! computer hard drives for ease of use when using the accompanying video lessons. TeachUcomp, Inc. also grants unlimited personal printing rights to the owner, strictly limited to the purposes of personal or private education or research. The unauthorized reproduction or distribution of this copyrighted work is illegal. Criminal copyright infringement, including infringement without monetary gain, is investigated by the FBI and is punishable by up to five years in federal prison and a fine of $250,000. Trademark Acknowledgements: purposes Apple, Macromedia, Dreamweaver, CoffeeCup Software, eBay, Google, Intuit, Quicken, QuickBooks, QuickBooks Pro, QuickBooks Premier, Turbo Tax, EasyStep, QuickReports, and QuickZoom are registered trademarks of Intuit, Inc. Windows, Windows 95, Windows 98, Windows NT, Windows Me, Windows XP, Windows 7, Windows 8, Microsoft Word 97, Microsoft Word 2000, Microsoft Word XP, Microsoft Word 2003, Microsoft Word 2007, Microsoft Word 2013, Microsoft Excel 97, Microsoft Excel 2000, Microsoft Excel XP, Microsoft Excel 2003, Microsoft Excel 2007, Microsoft Excel 2013, and Outlook are registered trademarks of Microsoft Corporation. -

Rational Robot User's Guide
Rational Software Corporation® Rational® Robot User’s Guide VERSION: 2003.06.00 PART NUMBER: 800-026172-000 WINDOWS [email protected] http://www.rational.com Legal Notices ©1998-2003, Rational Software Corporation. All rights reserved. Part Number: 800-026172-000 Version Number: 2003.06.00 This manual (the "Work") is protected under the copyright laws of the United States and/or other jurisdictions, as well as various international treaties. Any reproduction or distribution of the Work is expressly prohibited without the prior written consent of Rational Software Corporation. The Work is furnished under a license and may be used or copied only in accordance with the terms of that license. Unless specifically allowed under the license, this manual or copies of it may not be provided or otherwise made available to any other person. No title to or ownership of the manual is transferred. Read the license agreement for complete terms. Rational Software Corporation, Rational, Rational Suite, Rational Suite ContentStudio, Rational Apex, Rational Process Workbench, Rational Rose, Rational Summit, Rational Unified Process, Rational Visual Test, AnalystStudio, ClearCase, ClearCase Attache, ClearCase MultiSite, ClearDDTS, ClearGuide, ClearQuest, PerformanceStudio, PureCoverage, Purify, Quantify, Requisite, RequisitePro, RUP, SiteCheck, SiteLoad, SoDa, TestFactory, TestFoundation, TestMate and TestStudio are registered trademarks of Rational Software Corporation in the United States and are trademarks or registered trademarks in other countries. The Rational logo, Connexis, ObjecTime, Rational Developer Network, RDN, ScriptAssure, and XDE, among others, are trademarks of Rational Software Corporation in the United States and/or in other countries. All other names are used for identification purposes only and are trademarks or registered trademarks of their respective companies. -

HTML5 for .NET Developers by Jim Jackson II Ian Gilman
S AMPLE CHAPTER Single page web apps, JavaScript, and semantic markup Jim Jackson II Ian Gilman FOREWORD BY Scott Hanselman MANNING HTML5 for .NET Developers by Jim Jackson II Ian Gilman Chapter 1 Copyright 2013 Manning Publications brief contents 1 ■ HTML5 and .NET 1 2 ■ A markup primer: classic HTML, semantic HTML, and CSS 33 3 ■ Audio and video controls 66 4 ■ Canvas 90 5 ■ The History API: Changing the game for MVC sites 118 6 ■ Geolocation and web mapping 147 7 ■ Web workers and drag and drop 185 8 ■ Websockets 214 9 ■ Local storage and state management 248 10 ■ Offline web applications 273 vii HTML5 and .NET This chapter covers ■ Understanding the scope of HTML5 ■ Touring the new features in HTML5 ■ Assessing where HTML5 fits in software projects ■ Learning what an HTML application is ■ Getting started with HTML applications in Visual Studio You’re really going to love HTML5. It’s like having a box of brand new toys in front of you when you have nothing else to do but play. Forget pushing the envelope; using HTML5 on the client and .NET on the server gives you the ability to create entirely new envelopes for executing applications inside browsers that just a few years ago would have been difficult to build even as desktop applications. The abil- ity to use the skills you already have to build robust and fault-tolerant .NET solu- tions for any browser anywhere gives you an advantage in the market that we hope to prove throughout this book. For instance, with HTML5, you can ■ Tap the new Geolocation API to locate your users anywhere -

Vbscript Programmer’S Reference Third Edition
VBScript Programmer’s Reference Third Edition Adrian Kingsley-Hughes Kathie Kingsley-Hughes Daniel Read Wiley Publishing, Inc. ffirs.indd iii 8/28/07 9:41:21 AM ffirs.indd vi 8/28/07 9:41:22 AM VBScript Programmer’s Reference Third Edition Introduction . xxv Chapter 1: A Quick Introduction to Programming . 1 Chapter 2: What VBScript Is — and Isn’t! . 31 Chapter 3: Data Types . 45 Chapter 4: Variables and Procedures . 83 Chapter 5: Control of Flow . 109 Chapter 6: Error Handling and Debugging . 129 Chapter 7: The Scripting Runtime Objects . 183 Chapter 8: Classes in VBScript (Writing Your Own COM Objects) . 209 Chapter 9: Regular Expressions . 233 Chapter 10: Client-Side Web Scripting . 261 Chapter 11: Windows Sidebars and Gadgets . 287 Chapter 12: Task Scheduler Scripting . 309 Chapter 13: PowerShell . 345 Chapter 14: Super-Charged Client-Side Scripting . 375 Chapter 15: Windows Script Host . 405 Chapter 16: Windows Script Components . 465 Chapter 17: Script Encoding . 489 Chapter 18: Remote Scripting . 509 Chapter 19: HTML Applications . 517 Chapter 20: Server-Side Web Scripting . 535 Chapter 21: Adding VBScript to Your VB and .NET Applications . 569 (Continued) ffirs.indd i 8/28/07 9:41:21 AM Appendix A: VBScript Functions and Keywords . 603 Appendix B: Variable Naming Convention . 675 Appendix C: Coding Conventions . 677 Appendix D: Visual Basic Constants Supported in VBScript . 681 Appendix E: VBScript Error Codes and the Err Object . 687 Appendix F: The Scripting Runtime Library Object Reference . 703 Appendix G: The Windows Script Host Object Model . 715 Appendix H: Regular Expressions . 723 Appendix I: The Variant Subtypes . -

Internet Explorer Users Are Required to Add the Portal URL to Trusted Sites
CLA Client Portal Browser and Silverlight FAQs 1. Question: I am receiving an “Error 500” when clicking the link to access the CLA Document Portal. Resolution: Verify with your IT department that the portal is not blocked by any internal monitoring or protection applications. 2. Question: How do I know if my computer has Microsoft Silverlight Installed? Resolution: The first time you try and login to the portal you will be prompted to install Silverlight from Microsoft’s website if you don’t have it already installed. The installation typically takes less than one minute and is completely safe. http://www.microsoft.com/getsilverlight/Get-Started/Install/Default.aspx If you cannot, or prefer not to, install Silverlight on your machine, a simplified version of the document portal that does not require Silverlight is available. Click on the Take me to the non- Silverlight login on the CLA Document Portal page (www.claconnect.com/docportal). 3. Question: I cannot access the CLA Document Portal. (Server error/Page not found) Resolution: Check that you are using a Microsoft Silverlight 4 compatible browser on all PC’s or MAC. A complete list of browsers and operating systems that support Silverlight 4 can be found at http://www.microsoft.com/getsilverlight/locale/en-us/html/installation-win-SL4.html Please note: Internet Explorer users are required to add the portal URL to Trusted Sites. Adding to Trusted Sites Internet Explorer settings 1. Open Internet Explorer and browse to https://portal.cchaxcess.com/Portal/. 2. In Internet Explorer, select Tools / Internet Options; then select the Security tab and click Trusted Sites and then Sites.