Instant Netrunning a Fuzion Plug-In by Christian Conkle
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cyberpunk 2077 : the Complete Official Guide Pdf, Epub, Ebook
CYBERPUNK 2077 : THE COMPLETE OFFICIAL GUIDE PDF, EPUB, EBOOK Piggyback | 480 pages | 10 Dec 2020 | PIGGYBACK INTERACTIVE | 9781911015772 | English | none Cyberpunk 2077 : The Complete Official Guide PDF Book Here are nine very useful ways to prepare for the game's imminent release , and here's a look at the eight year wait for CD Projekt Red's massive RPG. One lucky person is about to have an amazing Christmas thanks to this incredible Lego Star Wars set worth R! Do you want to learn about Cyberpunk genre motifs, genre history, and most important works? Choose an option Softcover Hardcover Clear. Float Left Float Right. Collectible Hardcover Guide Includes: - Deluxe foil stamped hardcover strategy guide featuring exclusive art specifically created by the artists at CD Projekt Red. Prepare to meet a lot of intense characters like V or Johnny Silverhand , urban mercenaries of the future obsessed with body modifications and equipped with cybernetic enhancements. What size image should we insert? Regardless of your character's origin and play style, all new players going into Night City could benefit from this guide. Get your Pro tips now.? Hi-res maps of Night City: each annotated with locations of collectibles and points of interest. Jan 16, PST. Verily a tome of Tolstoyan proportions. With details on every last challenge and feature, the guide offers streamlined progression through the entire adventure, as well as a commanding expertise on all key systems. Explore the various districts, gangs, and history of Night City. Boutique is a participant in the Amazon Associates Program. Similar sponsored items Feedback on our suggestions - Similar sponsored items. -

MARCH 1St 2018
March 1st We love you, Archivist! MARCH 1st 2018 Attention PDF authors and publishers: Da Archive runs on your tolerance. If you want your product removed from this list, just tell us and it will not be included. This is a compilation of pdf share threads since 2015 and the rpg generals threads. Some things are from even earlier, like Lotsastuff’s collection. Thanks Lotsastuff, your pdf was inspirational. And all the Awesome Pioneer Dudes who built the foundations. Many of their names are still in the Big Collections A THOUSAND THANK YOUS to the Anon Brigade, who do all the digging, loading, and posting. Especially those elite commandos, the Nametag Legionaires, who selflessly achieve the improbable. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – The New Big Dog on the Block is Da Curated Archive. It probably has what you are looking for, so you might want to look there first. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – Don't think of this as a library index, think of it as Portobello Road in London, filled with bookstores and little street market booths and you have to talk to each shopkeeper. It has been cleaned up some, labeled poorly, and shuffled about a little to perhaps be more useful. There are links to ~16,000 pdfs. Don't be intimidated, some are duplicates. Go get a coffee and browse. Some links are encoded without a hyperlink to restrict spiderbot activity. You will have to complete the link. Sorry for the inconvenience. Others are encoded but have a working hyperlink underneath. Some are Spoonerisms or even written backwards, Enjoy! ss, @SS or $$ is Send Spaace, m3g@ is Megaa, <d0t> is a period or dot as in dot com, etc. -

BEYOND the EDGE Inside the Edgerunner Altcult C Ontents ST ILL
EDGEBOOK1a.qxd 12/19/07 12:06 PM Page 1 InsideInside thethe EdgerunnerEdgerunner AltcultAltcult Sample file THE CYBERPUNKS RETURN TO NIGHT CITY BEYOND THE EDGE 2 InsideInside thethe EdgerunnerEdgerunner AltcultAltcult MEE T TH E CAS T , CRE W AN D TH E LEG A L STU F F Cre w Co n t e n t s Wr i t e r s STI L L ON THE EDG E IN 20 3 X Ken MacKriell RIS E OF THE ‘R UN N E R S : THE KNO W N HIS T O R Y.. 4 Mike Pondsmith THE SEC R E T HIS T O R Y OF THE EDG E R U N N E R S .. 8 WHO RUN S THE EDG E R U N N E R S ? .. .1 3 Cover & Illustrations LEA D E R S .. .1 4 Jay Libby DYL A N MUR P H Y .. .1 4 Otto Blix SET H MEN D E Z .. .1 6 Mike Pondsmith MON I C A CHE U N G .. .1 8 VID A -M AR I A WES T .. .1 9 Layout & Design “P RI N C E ” LEO BAK H T I A R .. .2 1 VIN C E N T “S IL K ” FOU C A U L T.. .2 2 Mike Pondsmith THE PLAY E R S .. .2 4 Ty p o g r a p h y FATH E R KEV I N SUL L I VA N .. .2 4 Ted Tal s o r i a n OLE G MIK H A I L O V . -
Cyberpunk 2020
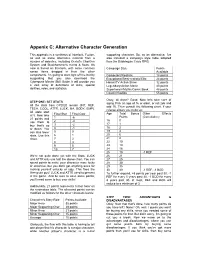
Appenix C: Alternative Character Generation This appendix is a synthesis of Interlock, Fuzion, supporting character. So, as an alternative, I've as well as some alternative material from a also included a campaign style table adapted number of websites, including Ocelot's CharGen from the Bubblegum Crisis RPG: System and Blackhammer's merits & flaws. It's core is based on Interlock, with some common Campaign Style Points sense items dragged in from the other Available components. I'm going to start right off the bat by Competent/Realistic 18 points suggesting that you also download the Exceptional/Semi-realistic/Elite 24 points Cyberpunk Master Skill Guide. It will provide you Heroic/TV Action Show 32 points a vast array of definitions of skills, special Legendary/Action Movie 40 points abilities, roles, and statistics. Superheroic/Mythic/Comic Book 48 points Cosmic/Godlike 55 points Okay, all done? Good. Now let's take care of STEP ONE: SET STATS aging. Pick an age of 16 or older, or roll 2d6 and All the stats from CP2020 remain (INT, REF, add 16. Then consult the following chart, if your TECH, COOL, ATTR, LUCK, MA, BODY, EMP). referee allows you to do so: All stats start Final Stat Final Cost Age Total Bonus Other Effects at 5. Now take Points (Cumulative) 21 points and 1 -6 16 0 use them to 2 -4 17 1 buy that’s up 3 -2 or down. You 4 -1 18 2 can also lower 5 0 19 4 stats. Use this 6 1 20 6 chart. 7 2 21 8 8 3 22 10 9 5 23 13 10 7 24 16 25 19 -1 REF We're not quite done yet with the Stats. -
NISEI Comprehensive Rules Document This Rules Document Is to Be Used As Reference Material
NISEI Comprehensive Rules Document This rules document is to be used as reference material. It is not intended to be read straight through. If you still have questions after consulting this document, please ask us online via email or Twitter. This is version 1.4 of this document, effective 20 December 2019. Summary of Changes Changes from version 1.3 are highlighted in orange. ● Added our email address. ● Performed a complete rewrite and reorganization of section 1.14 (Targets) and section 9 (Abilities). ● Updated imprecise terminology throughout the document to improve clarity now that terms like "using" and "instruction" are used extensively in the rules for abilities. ● Added rules for interrupts (section 9.8) and the interrupt symbol (rule 1.3.10). ● Added rules for double-sided identities (rule 1.5.4d, rule 1.6b, and rule 3.1.1a). ● Clarified that the terms "spend" and "pay" are synonyms (Rule 1.10.3c). ● Expanded the definition of the "source" of an ability and moved these rules from section 1.13.5 to section 9.1.3. ● Codified rules about inherent costs (rule 1.15.4a and rule 1.15.4b). ● Added “if you do" expressions to the list of ways nested costs can be formatted (section 1.15.10). ● Clarified that if a replacement effect replaces adding a card to a hand, score area, or discard pile, that card can still count as drawn, scored, stolen, or trashed (rule 1.8.5, rule 1.16.3f, and rule 1.18.1a). ● Defined "advanced card" (rule 1.17.3). ● Expanded rules on "reveal" and card visibility in general. -

The Top Runners' Quarterly
The Top Runners‘ Quarterly Newsletter of The Top Runners‘ Conference, The Official Netrunner Players‘ Organization Volume 3, Issue 2 Second Quarter, 1999 www.cyberjunkie.com/trc, www.geocities.com/sunsetstrip/basement/9666 World Domination 1999: Dreff's Revenge State of the Corp—June 1999 by Lukas Kautzsch by Jennifer Clarke Wilkes <[email protected]> <[email protected]> An der Roßweid 18a, 76229 Karlsruhe, Germany There’s little to report on the new cards front, I’m The qualification stage is over: A total of 184 players showed ® th afraid. The Pokémon madness has knocked all the other up in 25 World Domination Qualifier events from March 12 to April card games off balance a bit, though things are calming 25th, leading to 42 qualified players in addition to the 19 prequalified down now and real work can begin. It will probably mean ones (top places from last year’s World Domination and National/Regional championships). Of these players, 21 come from the the cards come out quite late, perhaps not until the end of the United States, 15 from Germany, 6 from the UK, 4 each from France, year. You can be sure I’ll let everyone know whenever I Canada, and Brazil, 2 each from Belgium and Switzerland, and 1 each have news. from the Netherlands, Australia, and New Zealand. However, Wizards of the Coast is supporting the first official US Netrunner Nationals! The tournament will There will be 7 World Domination round 1 tournaments: ® be held at GEN CON in Milwaukee, WI, on the weekend of 1. -

Datafortress 2020
Presents: INTERLOCK REVISED, REPAIRED, AND RE-EXAMINED A FAN PROJECT FOR FANS - THIS VERSION UPDATED 7-07-14 Written by Deric Bernier ([email protected] ) and R.Talsorian Games (with permission) Table of Contents: Art by Deric Bernier Introduction Pg 1 Indirect Fire Pg 42 ([email protected] ) and 1. Part 1: The Basics Pg 2 Reloads Carried Pg 42 R.Talsorian Games (with permission) Statistics Pg 2 Melee Combat Pg 43 2. Character Identity and Roles Pg 3 Key Attacks Pg 42 Contributions by: Joe Klemann, Ross Standard Roles Pg 3 Moving Attack Maneuvers Pg 46 Wynn, Cameron Jacobs, James Bernier, Multiple Roles Pg 3 Counter Attack Pg 46 Brandon Fleming, Jesse Miller, Richard Role Descriptions Pg 3 Melee Damage Pg 46 Balmer, Jason Parent, Ted Salonich, Paul 3. Skills Pg 5 Improvised Weapons Pg 46 Romine, Richard Harris, Gary Astleford, Learning New Skills Pg 5 Hand To Hand Penalties Pg 47 Tom Mosely, Suhiir, Trentin C Bergeron, IP Distribution Pg 5 Friendly Fighting Pg 47 Jim Lawrie, Omar (Blank Redge), Mike Skill list by era/setting Pg 7 Incapacitation/Nerve Clusters Pg 47 Van Atta, David Pietz, Steven Rennie, Skill Descriptions Pg 8 Death & Maiming Pg 47 Dan Winemiller, David Simpson, Karsten Languages Pg 14 Called Shots Pg 48 Voigt, Seth Skorkowsky, James Durand, Martial Arts Pg 15 Surprise Melee Attacks Pg 48 Sardukhar, Kyberpunkki, Richard Skills And Task Resolution Pg 16 Other Combat Rules Pg 49 Glendinning, Mark Cook, C. J. Maddox 4. Breathing Life Into Your Character Pg 17 Chink In The Armor Pg 49 Origins And Personal Style Pg 18 SP and Its Relation To SDP Pg 49 Playtesters: Motivations Pg 19 Taking It Like A Man Pg 49 Jeff Gray Life Events Pg 20 Falling Damage Pg 49 Matt Baldwin Friends & Enemies Pg 21 Impact Damage Pg 49 Andrew Steel Romantic Life Pg 21 Hard Road (vehicle rules) Pg 50 Al Bob Misc. -

Cyberpunk Red Errata Last Updated 06.02.2021
BY ANSELM ZIELONKA cyberpunk red errata last updated 06.02.2021 The following errata applies to the First and Second Printing of the Cyberpunk RED core rulebook. The changes have been applied to the digital version which is marked as v1.25. Copyright © 2020 by R. Talsorian Games, Inc., Cyberpunk is a registered trademark of CD Projekt Red S.A. All rights reserved under the Universal Copyrights Convention. All situations, governments, and people herein are fictional. Any similarities portrayed herein without satiric intent are strictly coincidental. 1 CYBERPUNK RED ERRATA Changes for v1.25/3rd Printing are noted with an @ at the front of the entry. Minor typos have been fixed throughout the book. Page 63: On the What Kind of Corp Do You Work For table you roll 1d10, not 1d6. Page 95: The Air Pistol listing on the Exotic Weapons table incorrectly notes it as a Very Heavy Pistol. It is a Medium Pistol. @ Page 102 and 356: The cost of High Fashion jewelry has been changed to 5,000 (Luxury). Page 114: The Description & Data for Grafted Muscle and Bone Lace has changed to clarify multiple instances stack. It now reads: Increases BODY by 2. The increase changes HP, Wound Threshold, and Death Save. Multiple installments stack. Cannot raise BODY above 10. Page 117: The EMP loss for the Cyberware packages are incorrect. They should read as follows: Rockerboy: -1 EMP • Solo: -2 EMP • Netrunner: -2 EMP • Tech: -2 EMP • Medtech: -2 EMP • Media: -1 EMP • Lawman: -1 EMP • Exec: -2 EMP • Fixer: -2 EMP • Nomad: -2 EMP @ Page 121: The chapter subheader has been changed to read 2023 (22 Years Ago). -

OVERVIEW of NETRUNNER Netrunner Is a Two-Player Deckmaster® Game Set in the World of R
Versione 1.0 – Dal sito http://www.incabrain.com/netrunner/rules.htm The contents of this page are ©1996 Wizards of the Coast, Inc. Cyberpunk 2020, Cyberpunk, and Netrunner therein are trademarks of R. Talsorian Games, Inc. Copyrights in certain text, graphic designs, characters, and places derived from Cyberpunk 2020® are the property of R. Talsorian Games, Inc., and are produced under license to Wizards of the Coast, Inc. Deckmaster, Wizards of the Coast, and Proteus™ are registered trademarks of Wizards of the Coast, Inc. This copy of the Netrunner rules was originally posted as a text file to Netrunner-L on April 18, 1996 by Marc Schmalz, a WotC employee who was netrepping at the time. i have reformatted the original text file to more closely match the original rulebook, since much of the formatting was lost in the text file (you'll note that many of the symbols are missing too). i have also added some text (from pp44-46) that was missing from the file. If anyone at WotC has an objection to my posting these rules, please feel free to contact me at azuay\at/incabrain\dot/com. OVERVIEW OF NETRUNNER Netrunner is a two-player Deckmaster® game set in the world of R. Talsorian's Cyberpunk® roleplaying game. There are two roles in Netrunner: the Runner, who is a high-tech data thief; and the Corporation. Using a computer that feeds output from a telecommunication link directly to his or her brain, the Runner navigates the virtual-reality environment of a global computer network known as the Net. -

JULY 25Th 2018
July 25th We love you, Archivist! JULY 25th 2018 Attention PDF authors and publishers: Da Archive runs on your tolerance. If you want your product removed from this list, just tell us and it will not be included. This is a compilation of pdf share threads since 2015 and the rpg generals threads. Some things are from even earlier, like Lotsastuff’s collection. Thanks Lotsastuff, your pdf was inspirational. And all the Awesome Pioneer Dudes who built the foundations. Many of their names are still in the Big Collections A THOUSAND THANK YOUS to the Anon Brigade, who do all the digging, loading, and posting. Especially those elite commandos, the Nametag Legionaires, who selflessly achieve the improbable. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – The New Big Dog on the Block is Da Curated Archive. It probably has what you are looking for, so you might want to look there first. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – Don't think of this as a library index, think of it as Portobello Road in London, filled with bookstores and little street market booths and you have to talk to each shopkeeper. It has been cleaned up some, labeled poorly, and shuffled about a little to perhaps be more useful. There are links to ~16,000 pdfs. Don't be intimidated, some are duplicates. Go get a coffee and browse. Some links are encoded without a hyperlink to restrict spiderbot activity. You will have to complete the link. Sorry for the inconvenience. Others are encoded but have a working hyperlink underneath. Some are Spoonerisms or even written backwards, Enjoy! ss, @SS or $$ is Send Spaace, m3g@ is Megaa, <d0t> is a period or dot as in dot com, etc. -

Cast and Crew
CAST AND CREW Writing and Design by Mike Pondsmith, James Hutt, Cody Pondsmith, Jay Parker, J Gray, David Ackerman, and Jaye Kovach Based on Material Originally Created by David Ackerman, Matt Anacleto, Mike Blum, Edward Bolme, Colin Fisk, Dave Friedland, Bruce Harlick, Scott Hedrick, Michael LaBossiere, Mike MacDonald, Will Moss, Lisa Pondsmith, Mike Pondsmith, Derek Quintanar, Mike Roter, Scott Ruggels, Craig Sheeley, Mark Schumann, Ross Winn, Benjamin Wright, and the many writers who worked on the Cyberpunk line in the past. Beat Chart Concepts Contributed by Flint Dille Lyrics for Black Dog and Never Fade Away by David Sandström and Dennis Lyxzén Business Management by Lisa Pondsmith Project Management by Cody Pondsmith and Mike Pondsmith Art Direction by Jaye Kovach Cover Illustration by Anselm Zielonka Interior Illustration and Graphics by Doug Anderson, Bad Moon Art Studio, Richard Bagnall, Santiago Betancur, Neil Branquinho, Alexander Dudar, Colin Fisk, Matthew S. Francella, Hélio Frazão, Huntang, J Gray, Maksym Harahulin, DariusK, Jaye Kovach, Bernard Kowalczuk, Adrian Marc, Jan Marek, Eddie Mendoza, Pedram Mohammadi, Alan Okamoto, Anna Podedworna, Sebastian Szmyd, Eve Ventrue, 望瑾 Jin Wang, Wavefront, and Anselm Zielonka Editing by Carol Darnell, Michael Matheson, Josh Vogt, and Dixie Cochran Layout and Page Design by J Gray, Irrgardless, and Adam Jury Product Consultation by Aron Tarbuck Playtesting and Beta Reading by James "ELH" Adams, Azalah, Jared Doyle Barnes, Ben, Gabriel Boleau, Naomi Calhoun, Matt "Sir Fluffles" Carroll, Kevin Diehl, Linda "Druttercup" Evans, James Fullerton, Allen Hawkins, Matthew House, Jay Jasti, Paul Khalifé, The MadQueen, Ashley Mayo, Leon "Leothedino" Mendez, Dan "F00d4Th0ught" Richardson, Ryan "Boss_Angler" St. -
GURPS Cyberpunk Is Copyright © 1990 by Steve Jackson Games Incorporated
GUMCYBERPUNK High-Tech Low-Life Roleplaying By Loyd Blankenship Edited by Steve Jackson and Creede Lambard Additional Material by Brian Edge, Cheryl G. Freedman, Steve Jackson, Mike Nystul, Creede Lambard, David Pulver, Alex Von Thorn, and Karl Wu Cover by David Schleinkofer Illustrated by Paul Mounts, Carl Anderson, Angela Bostick and Rick Lowry GURPS System Design by Steve Jackson Loyd Blankenship, Managing Editor Carl Anderson, Production Manager Page Layout and Typography by Loyd Blankenship Production by Carl Anderson and Dana Blankenship Proofreading by Chris McCubbin Hacking Consultants: The Legion of Doom Unsolicited Comments: United States Secret Service Dedicated with love to my wife, Whitney, who is my strength when I'm weak and my hope when I despair. Ideas and Comments: Randy Abel, Whitney Blankenship, John M. Ford, David Greig, Chris Goggans, Kerry Havas, Caroline Julian, Lisa Mackenzie and the Z-Team (Bill Ayers, Sheryl Beaver, Steven Drevik, Allen Hsu, Colin Klipsch, Tery Massey, Chris Peterson, Matt Riggsby and Tim VanBeke) Playtesters: Lowell Blankenship, John Boulton, Bill Brantley, Eric Brantley, Timothy M. Carroll, Bryan Case, Jay Charters, Mike Crhak, Loren Davie, Mike DeWolfe, Brian Edge, Aaron Johnson, Jason Johnson, Mark Johnson, Ben Kloepper, John Kono, Michael Lee, Dave Magnenat, Scott Paul Maykrantz, Kathy McClure, Scott McClure, Janet Naylor, Mike Naylor, David Pulver, Scott Smith, Steve Stevens, Jason Stiney, John Sullivan, Theresa Verity, Sasha Van Hellberg, Chris Vermeers, Jerry Westergaard, Tony Winkler, Richard Wu, Snowden Wyatt, Anna Yuzefov, Bryan Zarnett and Zlika GURPS, Rcleplayer and the all-seeing pyramid are registered trademarks and Supers is a trademark of Steve Jackson Games Incorporated.