GURPS Cyberpunk Is Copyright © 1990 by Steve Jackson Games Incorporated
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

GURPS Ultra-Lite Folds and and Much More
TM ULTRA-LITE About GURPS Steve Jackson Games is committed to full support of slit on the dotted line in the middle of the sheet, below pages GURPS players. Our address is SJ Games, P.O. Box INSTRUCTIONS 6 and Back and above 3 and 2; if you cut to either edge of 18957, Austin, TX 78760. Please include a self- After you print this PDF, lightly fold the second page on the paper, you went too far! addressed, stamped envelope (SASE) any time you the faint lines. (Make all folds in both directions to loosen Fold the paper in half lengthwise, text-side-out, and – write us! We can also be reached by e-mail: the creases.) With the page folded in half in either direction, holding the Front and page 1 in one hand and pages 5 and [email protected]. Resources include: the joining edges should match; if they don’t, trim the overly 4 in the other – bring your hands together, so that the pages long edge(s). Then unfold the page and lay it flat. on the top layer (6 and Back) pop up and the pages on the New supplements and adventures. GURPS continues Look at the sheet landscape style, so the Ultra-Lite cover bottom layer (2 and 3) pop down. Looked at from a certain to grow – see what’s new at www.sjgames.com/gurps. is in the upper-right corner (see picture). Make a horizontal view, it should resemble a plus (+) sign. e23. Our e-publishing division offers GURPS adven- Fold page 6 toward page 5, then fold page 1 toward page tures, play aids, and support in PDF form . -

Cyberpunk 2077 : the Complete Official Guide Pdf, Epub, Ebook
CYBERPUNK 2077 : THE COMPLETE OFFICIAL GUIDE PDF, EPUB, EBOOK Piggyback | 480 pages | 10 Dec 2020 | PIGGYBACK INTERACTIVE | 9781911015772 | English | none Cyberpunk 2077 : The Complete Official Guide PDF Book Here are nine very useful ways to prepare for the game's imminent release , and here's a look at the eight year wait for CD Projekt Red's massive RPG. One lucky person is about to have an amazing Christmas thanks to this incredible Lego Star Wars set worth R! Do you want to learn about Cyberpunk genre motifs, genre history, and most important works? Choose an option Softcover Hardcover Clear. Float Left Float Right. Collectible Hardcover Guide Includes: - Deluxe foil stamped hardcover strategy guide featuring exclusive art specifically created by the artists at CD Projekt Red. Prepare to meet a lot of intense characters like V or Johnny Silverhand , urban mercenaries of the future obsessed with body modifications and equipped with cybernetic enhancements. What size image should we insert? Regardless of your character's origin and play style, all new players going into Night City could benefit from this guide. Get your Pro tips now.? Hi-res maps of Night City: each annotated with locations of collectibles and points of interest. Jan 16, PST. Verily a tome of Tolstoyan proportions. With details on every last challenge and feature, the guide offers streamlined progression through the entire adventure, as well as a commanding expertise on all key systems. Explore the various districts, gangs, and history of Night City. Boutique is a participant in the Amazon Associates Program. Similar sponsored items Feedback on our suggestions - Similar sponsored items. -

Dragon Magazine #151
Issue #151 SPECIAL ATTRACTIONS Vol. XIV, No. 6 Into the Eastern Realms: November 1989 11 Adventure is adventure, no matter which side of the ocean you’re on. Publisher The Ecology of the Kappa David R. Knowles Jim Ward 14 Kappa are strange, but youd be wise not to laugh at them. Editor Soldiers of the Law Dan Salas Roger E. Moore 18 The next ninja you meet might actually work for the police. Fiction editor Earn Those Heirlooms! Jay Ouzts Barbara G. Young 22Only your best behavior will win your family’s prize katana. Assistant editors The Dragons Bestiary Sylvia Li Anne Brown Dale Donovan 28The wang-liang are dying out — and they’d like to take a few humans with them. Art director Paul Hanchette The Ecology of the Yuan-ti David Wellman 32To call them the degenerate Spawn of a mad god may be the only nice Production staff thing to say. Kathleen C. MacDonald Gaye OKeefe Angelika Lukotz OTHER FEATURES Subscriptions The Beastie Knows Best Janet L. Winters — Hartley, Patricia, and Kirk Lesser 36 What are the best computer games of 1989? You’ll find them all here. U.S. advertising Role-playing Reviews Sheila Gailloreto Tammy Volp Jim Bambra 38Did you ever think that undead might be . helpful? U.K. correspondent The Role of Books John C. Bunnell and U.K. advertising 46 New twists on an old tale, and other unusual fantasies. Sue Lilley The Role of Computers — Hartley, Patricia, and Kirk Lesser 52 Fly a Thunderchief in Vietnam — or a Silpheed in outer space. -

GURPS4E Ultra-Tech.Qxp
Written by DAVID PULVER, with KENNETH PETERS Additional Material by WILLIAM BARTON, LOYD BLANKENSHIP, and STEVE JACKSON Edited by CHRISTOPHER AYLOTT, STEVE JACKSON, SEAN PUNCH, WIL UPCHURCH, and NIKOLA VRTIS Cover Art by SIMON LISSAMAN, DREW MORROW, BOB STEVLIC, and JOHN ZELEZNIK Illustrated by JESSE DEGRAFF, IGOR FIORENTINI, SIMON LISSAMAN, DREW MORROW, E. JON NETHERLAND, AARON PANAGOS, CHRISTOPHER SHY, BOB STEVLIC, and JOHN ZELEZNIK Stock # 31-0104 Version 1.0 – May 22, 2007 STEVE JACKSON GAMES CONTENTS INTRODUCTION . 4 Adjusting for SM . 16 PERSONAL GEAR AND About the Authors . 4 EQUIPMENT STATISTICS . 16 CONSUMER GOODS . 38 About GURPS . 4 Personal Items . 38 2. CORE TECHNOLOGIES . 18 Clothing . 38 1. ULTRA-TECHNOLOGY . 5 POWER . 18 Entertainment . 40 AGES OF TECHNOLOGY . 6 Power Cells. 18 Recreation and TL9 – The Microtech Age . 6 Generators . 20 Personal Robots. 41 TL10 – The Robotic Age . 6 Energy Collection . 20 TL11 – The Age of Beamed and 3. COMMUNICATIONS, SENSORS, Exotic Matter . 7 Broadcast Power . 21 AND MEDIA . 42 TL12 – The Age of Miracles . 7 Civilization and Power . 21 COMMUNICATION AND INTERFACE . 42 Even Higher TLs. 7 COMPUTERS . 21 Communicators. 43 TECH LEVEL . 8 Hardware . 21 Encryption . 46 Technological Progression . 8 AI: Hardware or Software? . 23 Receive-Only or TECHNOLOGY PATHS . 8 Software . 24 Transmit-Only Comms. 46 Conservative Hard SF. 9 Using a HUD . 24 Translators . 47 Radical Hard SF . 9 Ubiquitous Computing . 25 Neural Interfaces. 48 CyberPunk . 9 ROBOTS AND TOTAL CYBORGS . 26 Networks . 49 Nanotech Revolution . 9 Digital Intelligences. 26 Mail and Freight . 50 Unlimited Technology. 9 Drones . 26 MEDIA AND EDUCATION . 51 Emergent Superscience . -

Theescapist 065.Pdf
The game was not terribly complex: The were quite familiar, encompassing ideas point of the game is, as CEO, to keep of companies that were no more, such as your fledgling dot-com in business. The “Butler-Hosted search engine,” or “Dot- Allen, I’m in the same boat as you on gameplay emerges through a careful Com Card Game” – whatever that is. this collectible card game thing – I don’t balance of personnel cards and skill And it was these cards that made the To The Editor: If Christian game get it. For those of you wondering, go cards, the personnel cards each carrying game really quite fun in a quirky sort of producers want to be taken seriously by have a read through Allen Varney’s an individual’s burn rate and his skill way, inspiring comments such as, “Wow, the mainstream market (in particularly article in this week’s issue of The level, and the skill cards representing an that really was a bad idea,” and “Yes! I the overseas European and Japanese Escapist, and you’ll see what I mean. action and the personnel skill required to remember the sock puppet!” market) they’re going to have to stop Perhaps this makes me a dimwit, as perform that action. designing their games as blatant well; certainly I’ll admit to some level of But I guess it’s easy to laugh in propaganda and misinformation. dimness on the topic, as many of these During the first couple of dot-com eras hindsight, knowing that these ideas were card games are a smashing success. -

MARCH 1St 2018
March 1st We love you, Archivist! MARCH 1st 2018 Attention PDF authors and publishers: Da Archive runs on your tolerance. If you want your product removed from this list, just tell us and it will not be included. This is a compilation of pdf share threads since 2015 and the rpg generals threads. Some things are from even earlier, like Lotsastuff’s collection. Thanks Lotsastuff, your pdf was inspirational. And all the Awesome Pioneer Dudes who built the foundations. Many of their names are still in the Big Collections A THOUSAND THANK YOUS to the Anon Brigade, who do all the digging, loading, and posting. Especially those elite commandos, the Nametag Legionaires, who selflessly achieve the improbable. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – The New Big Dog on the Block is Da Curated Archive. It probably has what you are looking for, so you might want to look there first. - - - - - - - – - - - - - - - - – - - - - - - - - - - - - - - – - - - - - – Don't think of this as a library index, think of it as Portobello Road in London, filled with bookstores and little street market booths and you have to talk to each shopkeeper. It has been cleaned up some, labeled poorly, and shuffled about a little to perhaps be more useful. There are links to ~16,000 pdfs. Don't be intimidated, some are duplicates. Go get a coffee and browse. Some links are encoded without a hyperlink to restrict spiderbot activity. You will have to complete the link. Sorry for the inconvenience. Others are encoded but have a working hyperlink underneath. Some are Spoonerisms or even written backwards, Enjoy! ss, @SS or $$ is Send Spaace, m3g@ is Megaa, <d0t> is a period or dot as in dot com, etc. -

Munchkin Cthulhu Guest Artist Edition Rules
® exaMPle oF CoMBat, running away suPer-sized MUNCHKIN with nuMBers and everything If nobody will help you . or if somebody tries to help, and CURSES Studies have shown that 8.4 out of 9.7 Munchkin players your fellow party members interfere so the two of you still cannot If drawn face-up during the Kick Open The Door phase, Curse just can’t get enough of the game. Here are some ideas to take Margot is a 4th-Level Cultist with the Frothing win . you must Run Away. You don’t get any levels or Treasure. cards apply to the person who drew them. your Munchkin games to new heights – or lows: enhancer (which gives her a +3 to her combat strength). You don’t even get to Loot the Room. And you don’t always Combining different Munchkin sets. You can mix two (or There is one other Cultist, Gene, so she has another +2. escape unharmed . If acquired some other way, such as by Looting The Room, She kicks open the door and finds the Grape Old Ones, a Curse cards go into your hand and may be played on any player at more) base sets and expansions together for a genre-crossing Level 12 monster with -2 against females. Margot’s at a 9 Roll the die. You escape on a 5 or more. Some abilities and any time. ANY time, do you hear me? Reducing someone’s abilities mega-Munchkin adventure! Space plus Old West? Kung fu and the Grape Old Ones are at a 10, so Margot is losing. -

I STEVE JACKSON GAMES ,; Ancient Howor Crawls Into the Dark Future
I STEVE JACKSON GAMES ,; Ancient Howor Crawls into the Dark Future By Chris W. McCubbin Edited by Scott D. Haring Cover by Albert Slark Illustrated by Dan Smith GURPS System Design by Steve Jackson Scott Haring, Managing Editor Page Layout, Typography and Interior Production by Rick Martin Cover Production by Jeff Koke Art Direction by Lillian Butler Print Buying by Andrew Hartsock and Monica Stephens Dana Blankenship, Sales Manager Thanks to Dm Smith Additional Material by David Ellis Dickerson Bibliographic information compiled by Chris Jarocha-Emst Proofreading by Spike Y. Jones Playtesters: Bob Angell, Sean Barrett, Kaye Barry, C. Milton Beeghly, James Cloos, Mike DeSanto, Morgan Goulet, David G. Haren, Dave Magnenat, Virginia L. Nelson, James Rouse, Karen Sakamoto, Michael Sullivan and Craig Tsuchiya GURPS and the all-seeing pyramid are registered trademarks of Steve Jackson Games Incorporated. Pyramid and the names of all products published by Steve Jackson Games Incorporated are registered trademarks or trademarks of Steve Jackson Games Incorporated, or used under license. Cull of Cihulhu is a trademark of Chaosium Inc. and is used by permission. Elder Sign art (p. 55) used by permission of Chaosium Inc. GURPS CihuIhuPunk is copyright 0 1995 by Steve Jackson Games Incorporated. All rights reserved. Printed in the U.S.A ISBN 1-55634-288-8 Introduction ................................ 4 Central and South America ..27 Hacker ..................................43 About GURPS ............................4 The Pacific Rim ...................27 -

BEYOND the EDGE Inside the Edgerunner Altcult C Ontents ST ILL
EDGEBOOK1a.qxd 12/19/07 12:06 PM Page 1 InsideInside thethe EdgerunnerEdgerunner AltcultAltcult Sample file THE CYBERPUNKS RETURN TO NIGHT CITY BEYOND THE EDGE 2 InsideInside thethe EdgerunnerEdgerunner AltcultAltcult MEE T TH E CAS T , CRE W AN D TH E LEG A L STU F F Cre w Co n t e n t s Wr i t e r s STI L L ON THE EDG E IN 20 3 X Ken MacKriell RIS E OF THE ‘R UN N E R S : THE KNO W N HIS T O R Y.. 4 Mike Pondsmith THE SEC R E T HIS T O R Y OF THE EDG E R U N N E R S .. 8 WHO RUN S THE EDG E R U N N E R S ? .. .1 3 Cover & Illustrations LEA D E R S .. .1 4 Jay Libby DYL A N MUR P H Y .. .1 4 Otto Blix SET H MEN D E Z .. .1 6 Mike Pondsmith MON I C A CHE U N G .. .1 8 VID A -M AR I A WES T .. .1 9 Layout & Design “P RI N C E ” LEO BAK H T I A R .. .2 1 VIN C E N T “S IL K ” FOU C A U L T.. .2 2 Mike Pondsmith THE PLAY E R S .. .2 4 Ty p o g r a p h y FATH E R KEV I N SUL L I VA N .. .2 4 Ted Tal s o r i a n OLE G MIK H A I L O V . -
Cyberpunk 2020
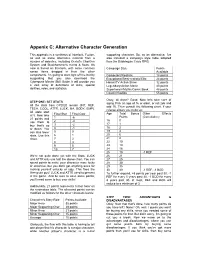
Appenix C: Alternative Character Generation This appendix is a synthesis of Interlock, Fuzion, supporting character. So, as an alternative, I've as well as some alternative material from a also included a campaign style table adapted number of websites, including Ocelot's CharGen from the Bubblegum Crisis RPG: System and Blackhammer's merits & flaws. It's core is based on Interlock, with some common Campaign Style Points sense items dragged in from the other Available components. I'm going to start right off the bat by Competent/Realistic 18 points suggesting that you also download the Exceptional/Semi-realistic/Elite 24 points Cyberpunk Master Skill Guide. It will provide you Heroic/TV Action Show 32 points a vast array of definitions of skills, special Legendary/Action Movie 40 points abilities, roles, and statistics. Superheroic/Mythic/Comic Book 48 points Cosmic/Godlike 55 points Okay, all done? Good. Now let's take care of STEP ONE: SET STATS aging. Pick an age of 16 or older, or roll 2d6 and All the stats from CP2020 remain (INT, REF, add 16. Then consult the following chart, if your TECH, COOL, ATTR, LUCK, MA, BODY, EMP). referee allows you to do so: All stats start Final Stat Final Cost Age Total Bonus Other Effects at 5. Now take Points (Cumulative) 21 points and 1 -6 16 0 use them to 2 -4 17 1 buy that’s up 3 -2 or down. You 4 -1 18 2 can also lower 5 0 19 4 stats. Use this 6 1 20 6 chart. 7 2 21 8 8 3 22 10 9 5 23 13 10 7 24 16 25 19 -1 REF We're not quite done yet with the Stats. -

Instant Netrunning a Fuzion Plug-In by Christian Conkle
Instant Netrunning A Fuzion Plug-In by Christian Conkle ([email protected], http://www.europa.com/~conkle) Introduction All computers connected to the Net are assigned LDL. This LDL serves as a kind of telephone number for This is a system of rules expanding the hacking rules that computer, to which other computers know where for Fuzion and Interlock. These rules draw heavily on to send information. In a futuristic setting, a Virtual Cyberpunk 2020's Netrunning rules and are intended Construct or Icon may substitute for the LDL. The Net to be native in a Cyberpunk environment where neural User connects their computer to a Virtual Reality Inter- cyber-interfaces are standard, though they are written face, within which companies pay for space and create generically enough to be useable in a modern setting as elaborate virtual constructs to represent their LDL, the well. VR equivalent of Internet Portal Sites such as Infos- eek or Yahoo! today. The Net User may now tour the These rules were designed to use existing Cyberpunk bustling 3D Virtual City regardless of gravity or speed. 2020 equipment and software with little modication. Corporate virtual constructs are like giant 3D advertise- There are several dierences from the original rules, how- ments, attempting to entice the average Net User into ever, that are intended to speed play and optimize sim- their Virtual Realities to sell products or services. Some plicity. First, these rules lack a grid. Movement within Virtual Realities actually provide useful services such the virtual environment of cyberspace is conceptual. To as information or online software applications. -

Sample File Table of Contents Runes by Stewart Wieck 3 Stewart Gives Us Insight Into WHITE WOLF's Future
Sample file Table of Contents Runes by Stewart Wieck 3 Stewart gives us insight into WHITE WOLF's future. From the Pack 4 Letters written by you in a column put together for you. Raiko by Nigel D. Findley 6 As Storm Knights quickly learn in this Torg adventure, Nippon corporations can sometimes fall victim to their own machinations. Curse by Richard Worzel 18 Time is proven a fickle beast in this short story based on the Time and Time Again roleplaying game. New Shamanic Totems by Berin Kinsman 23 Expand your spiritual devotions in this addition to the Shadowrun rules. Feature Review: Darksun by Berin Kinsman 26 Take a detailed look into the deadly and wondrous new world from TSR. Pulling No Punches by Greg Porter 28 If you've ever wanted to take a martial arts class, now's your chance, through the teachings of theSample designer offile CORPS. The Silicon Dungeon by Jim Trunzo 35 With reviews of some Christmas computer releases, you can now fly through space and become Conan! Deadly Legacy by Clay Gibson 40 Family members look disconcertingly alike in this AGE of RUIN adventure set in the American south. Items For Any Realm by Robert Wilson 46 A collection of magical items that can be incorporated into any fantasy game. The Scope of Magic by Christopher Barley 50 Some fun new spells that might save your life in the NightLife roleplaying game. Capsule Reviews by Line Reviewers 53 In this issue we take a look at new releases for AD&D, Shadowrun and WFRP.