Guide to X86 Assembly
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pdp11-40.Pdf
processor handbook digital equipment corporation Copyright© 1972, by Digital Equipment Corporation DEC, PDP, UNIBUS are registered trademarks of Digital Equipment Corporation. ii TABLE OF CONTENTS CHAPTER 1 INTRODUCTION 1·1 1.1 GENERAL ............................................. 1·1 1.2 GENERAL CHARACTERISTICS . 1·2 1.2.1 The UNIBUS ..... 1·2 1.2.2 Central Processor 1·3 1.2.3 Memories ........... 1·5 1.2.4 Floating Point ... 1·5 1.2.5 Memory Management .............................. .. 1·5 1.3 PERIPHERALS/OPTIONS ......................................... 1·5 1.3.1 1/0 Devices .......... .................................. 1·6 1.3.2 Storage Devices ...................................... .. 1·6 1.3.3 Bus Options .............................................. 1·6 1.4 SOFTWARE ..... .... ........................................... ............. 1·6 1.4.1 Paper Tape Software .......................................... 1·7 1.4.2 Disk Operating System Software ........................ 1·7 1.4.3 Higher Level Languages ................................... .. 1·7 1.5 NUMBER SYSTEMS ..................................... 1-7 CHAPTER 2 SYSTEM ARCHITECTURE. 2-1 2.1 SYSTEM DEFINITION .............. 2·1 2.2 UNIBUS ......................................... 2-1 2.2.1 Bidirectional Lines ...... 2-1 2.2.2 Master-Slave Relation .. 2-2 2.2.3 Interlocked Communication 2-2 2.3 CENTRAL PROCESSOR .......... 2-2 2.3.1 General Registers ... 2-3 2.3.2 Processor Status Word ....... 2-4 2.3.3 Stack Limit Register 2-5 2.4 EXTENDED INSTRUCTION SET & FLOATING POINT .. 2-5 2.5 CORE MEMORY . .... 2-6 2.6 AUTOMATIC PRIORITY INTERRUPTS .... 2-7 2.6.1 Using the Interrupts . 2-9 2.6.2 Interrupt Procedure 2-9 2.6.3 Interrupt Servicing ............ .. 2-10 2.7 PROCESSOR TRAPS ............ 2-10 2.7.1 Power Failure .............. -

Lecture Notes in Assembly Language
Lecture Notes in Assembly Language Short introduction to low-level programming Piotr Fulmański Łódź, 12 czerwca 2015 Spis treści Spis treści iii 1 Before we begin1 1.1 Simple assembler.................................... 1 1.1.1 Excercise 1 ................................... 2 1.1.2 Excercise 2 ................................... 3 1.1.3 Excercise 3 ................................... 3 1.1.4 Excercise 4 ................................... 5 1.1.5 Excercise 5 ................................... 6 1.2 Improvements, part I: addressing........................... 8 1.2.1 Excercise 6 ................................... 11 1.3 Improvements, part II: indirect addressing...................... 11 1.4 Improvements, part III: labels............................. 18 1.4.1 Excercise 7: find substring in a string .................... 19 1.4.2 Excercise 8: improved polynomial....................... 21 1.5 Improvements, part IV: flag register ......................... 23 1.6 Improvements, part V: the stack ........................... 24 1.6.1 Excercise 12................................... 26 1.7 Improvements, part VI – function stack frame.................... 29 1.8 Finall excercises..................................... 34 1.8.1 Excercise 13................................... 34 1.8.2 Excercise 14................................... 34 1.8.3 Excercise 15................................... 34 1.8.4 Excercise 16................................... 34 iii iv SPIS TREŚCI 1.8.5 Excercise 17................................... 34 2 First program 37 2.1 Compiling, -

Appendix D an Alternative to RISC: the Intel 80X86
D.1 Introduction D-2 D.2 80x86 Registers and Data Addressing Modes D-3 D.3 80x86 Integer Operations D-6 D.4 80x86 Floating-Point Operations D-10 D.5 80x86 Instruction Encoding D-12 D.6 Putting It All Together: Measurements of Instruction Set Usage D-14 D.7 Concluding Remarks D-20 D.8 Historical Perspective and References D-21 D An Alternative to RISC: The Intel 80x86 The x86 isn’t all that complex—it just doesn’t make a lot of sense. Mike Johnson Leader of 80x86 Design at AMD, Microprocessor Report (1994) © 2003 Elsevier Science (USA). All rights reserved. D-2 I Appendix D An Alternative to RISC: The Intel 80x86 D.1 Introduction MIPS was the vision of a single architect. The pieces of this architecture fit nicely together and the whole architecture can be described succinctly. Such is not the case of the 80x86: It is the product of several independent groups who evolved the architecture over 20 years, adding new features to the original instruction set as you might add clothing to a packed bag. Here are important 80x86 milestones: I 1978—The Intel 8086 architecture was announced as an assembly language– compatible extension of the then-successful Intel 8080, an 8-bit microproces- sor. The 8086 is a 16-bit architecture, with all internal registers 16 bits wide. Whereas the 8080 was a straightforward accumulator machine, the 8086 extended the architecture with additional registers. Because nearly every reg- ister has a dedicated use, the 8086 falls somewhere between an accumulator machine and a general-purpose register machine, and can fairly be called an extended accumulator machine. -

Computer Organization & Architecture Eie
COMPUTER ORGANIZATION & ARCHITECTURE EIE 411 Course Lecturer: Engr Banji Adedayo. Reg COREN. The characteristics of different computers vary considerably from category to category. Computers for data processing activities have different features than those with scientific features. Even computers configured within the same application area have variations in design. Computer architecture is the science of integrating those components to achieve a level of functionality and performance. It is logical organization or designs of the hardware that make up the computer system. The internal organization of a digital system is defined by the sequence of micro operations it performs on the data stored in its registers. The internal structure of a MICRO-PROCESSOR is called its architecture and includes the number lay out and functionality of registers, memory cell, decoders, controllers and clocks. HISTORY OF COMPUTER HARDWARE The first use of the word ‘Computer’ was recorded in 1613, referring to a person who carried out calculation or computation. A brief History: Computer as we all know 2day had its beginning with 19th century English Mathematics Professor named Chales Babage. He designed the analytical engine and it was this design that the basic frame work of the computer of today are based on. 1st Generation 1937-1946 The first electronic digital computer was built by Dr John V. Atanasoff & Berry Cliford (ABC). In 1943 an electronic computer named colossus was built for military. 1946 – The first general purpose digital computer- the Electronic Numerical Integrator and computer (ENIAC) was built. This computer weighed 30 tons and had 18,000 vacuum tubes which were used for processing. -

Introduction to X86 Assembly
CS342 Computer Security Handout # 5 Prof. Lyn Turbak Monday, Oct. 04, 2010 Wellesley College Lab 4: Introduction to x86 Assembly Reading: Hacking, 0x250, 0x270 Overview Today, we continue to cover low-level programming details that are essential for understanding software vulnerabilities like buffer overflow attacks and format string exploits. You will get exposure to the following: • Understanding conventions used by compiler to translate high-level programs to low-level assembly code (in our case, using Gnu C Compiler (gcc) to compile C programs). • The ability to read low-level assembly code (in our case, Intel x86). • Understanding how assembly code instructions are represented as machine code. • Being able to use gdb (the Gnu Debugger) to read the low-level code produced by gcc and understand its execution. In tutorials based on this handout, we will learn about all of the above in the context of some simple examples. Intel x86 Assembly Language Since Intel x86 processors are ubiquitous, it is helpful to know how to read assembly code for these processors. We will use the following terms: byte refers to 8-bit quantities; short word refers to 16-bit quantities; word refers to 32-bit quantities; and long word refers to 64-bit quantities. There are many registers, but we mostly care about the following: • EAX, EBX, ECX, EDX are 32-bit registers used for general storage. • ESI and EDI are 32-bit indexing registers that are sometimes used for general storage. • ESP is the 32-bit register for the stack pointer, which holds the address of the element currently at the top of the stack. -
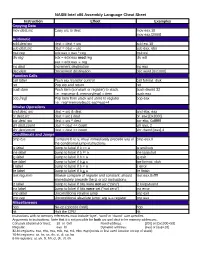
NASM Intel X86 Assembly Language Cheat Sheet
NASM Intel x86 Assembly Language Cheat Sheet Instruction Effect Examples Copying Data mov dest,src Copy src to dest mov eax,10 mov eax,[2000] Arithmetic add dest,src dest = dest + src add esi,10 sub dest,src dest = dest – src sub eax, ebx mul reg edx:eax = eax * reg mul esi div reg edx = edx:eax mod reg div edi eax = edx:eax reg inc dest Increment destination inc eax dec dest Decrement destination dec word [0x1000] Function Calls call label Push eip, transfer control call format_disk ret Pop eip and return ret push item Push item (constant or register) to stack. push dword 32 I.e.: esp=esp-4; memory[esp] = item push eax pop [reg] Pop item from stack and store to register pop eax I.e.: reg=memory[esp]; esp=esp+4 Bitwise Operations and dest, src dest = src & dest and ebx, eax or dest,src dest = src | dest or eax,[0x2000] xor dest, src dest = src ^ dest xor ebx, 0xfffffff shl dest,count dest = dest << count shl eax, 2 shr dest,count dest = dest >> count shr dword [eax],4 Conditionals and Jumps cmp b,a Compare b to a; must immediately precede any of cmp eax,0 the conditional jump instructions je label Jump to label if b == a je endloop jne label Jump to label if b != a jne loopstart jg label Jump to label if b > a jg exit jge label Jump to label if b > a jge format_disk jl label Jump to label if b < a jl error jle label Jump to label if b < a jle finish test reg,imm Bitwise compare of register and constant; should test eax,0xffff immediately precede the jz or jnz instructions jz label Jump to label if bits were not set (“zero”) jz looparound jnz label Jump to label if bits were set (“not zero”) jnz error jmp label Unconditional relative jump jmp exit jmp reg Unconditional absolute jump; arg is a register jmp eax Miscellaneous nop No-op (opcode 0x90) nop hlt Halt the CPU hlt Instructions with no memory references must include ‘byte’, ‘word’ or ‘dword’ size specifier. -

X86 Disassembly Exploring the Relationship Between C, X86 Assembly, and Machine Code
x86 Disassembly Exploring the relationship between C, x86 Assembly, and Machine Code PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 07 Sep 2013 05:04:59 UTC Contents Articles Wikibooks:Collections Preface 1 X86 Disassembly/Cover 3 X86 Disassembly/Introduction 3 Tools 5 X86 Disassembly/Assemblers and Compilers 5 X86 Disassembly/Disassemblers and Decompilers 10 X86 Disassembly/Disassembly Examples 18 X86 Disassembly/Analysis Tools 19 Platforms 28 X86 Disassembly/Microsoft Windows 28 X86 Disassembly/Windows Executable Files 33 X86 Disassembly/Linux 48 X86 Disassembly/Linux Executable Files 50 Code Patterns 51 X86 Disassembly/The Stack 51 X86 Disassembly/Functions and Stack Frames 53 X86 Disassembly/Functions and Stack Frame Examples 57 X86 Disassembly/Calling Conventions 58 X86 Disassembly/Calling Convention Examples 64 X86 Disassembly/Branches 74 X86 Disassembly/Branch Examples 83 X86 Disassembly/Loops 87 X86 Disassembly/Loop Examples 92 Data Patterns 95 X86 Disassembly/Variables 95 X86 Disassembly/Variable Examples 101 X86 Disassembly/Data Structures 103 X86 Disassembly/Objects and Classes 108 X86 Disassembly/Floating Point Numbers 112 X86 Disassembly/Floating Point Examples 119 Difficulties 121 X86 Disassembly/Code Optimization 121 X86 Disassembly/Optimization Examples 124 X86 Disassembly/Code Obfuscation 132 X86 Disassembly/Debugger Detectors 137 Resources and Licensing 139 X86 Disassembly/Resources 139 X86 Disassembly/Licensing 141 X86 Disassembly/Manual of Style 141 References Article Sources and Contributors 142 Image Sources, Licenses and Contributors 143 Article Licenses License 144 Wikibooks:Collections Preface 1 Wikibooks:Collections Preface This book was created by volunteers at Wikibooks (http:/ / en. -

Palmtree: Learning an Assembly Language Model for Instruction Embedding
PalmTree: Learning an Assembly Language Model for Instruction Embedding Xuezixiang Li Yu Qu Heng Yin University of California Riverside University of California Riverside University of California Riverside Riverside, CA 92521, USA Riverside, CA 92521, USA Riverside, CA 92521, USA [email protected] [email protected] [email protected] ABSTRACT into a neural network (e.g., the work by Shin et al. [37], UDiff [23], Deep learning has demonstrated its strengths in numerous binary DeepVSA [14], and MalConv [35]), or feed manually-designed fea- analysis tasks, including function boundary detection, binary code tures (e.g., Gemini [40] and Instruction2Vec [41]), or automatically search, function prototype inference, value set analysis, etc. When learn to generate a vector representation for each instruction using applying deep learning to binary analysis tasks, we need to decide some representation learning models such as word2vec (e.g., In- what input should be fed into the neural network model. More nerEye [43] and EKLAVYA [5]), and then feed the representations specifically, we need to answer how to represent an instruction ina (embeddings) into the downstream models. fixed-length vector. The idea of automatically learning instruction Compared to the first two choices, automatically learning representations is intriguing, but the existing schemes fail to capture instruction-level representation is more attractive for two reasons: the unique characteristics of disassembly. These schemes ignore the (1) it avoids manually designing efforts, which require expert knowl- complex intra-instruction structures and mainly rely on control flow edge and may be tedious and error-prone; and (2) it can learn higher- in which the contextual information is noisy and can be influenced level features rather than pure syntactic features and thus provide by compiler optimizations. -

X86 Assembly Language Reference Manual
x86 Assembly Language Reference Manual Part No: 817–5477–11 March 2010 Copyright ©2010 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related software documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are “commercial computer software” or “commercial technical data” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms setforth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle USA, Inc., 500 Oracle Parkway, Redwood City, CA 94065. -

Instruction Set Architecture
Instruction Set Architecture EE3376 1 –Adapted from notes from BYU ECE124 Topics to Cover… l MSP430 ISA l MSP430 Registers, ALU, Memory l Instruction Formats l Addressing Modes l Double Operand Instructions l Single Operand Instructions l Jump Instructions l Emulated Instructions – http://en.wikipedia.org/wiki/TI_MSP430 2 –Adapted from notes from BYU ECE124 Levels of Transformation –Problems –Algorithms – C Instructions –Language (Program) –Programmable –Assembly Language – MSP 430 ISA –Machine (ISA) Architecture –Computer Specific –Microarchitecture –Manufacturer Specific –Circuits –Devices 3 –Adapted from notes from BYU ECE124 Instruction Set Architecture l The computer ISA defines all of the programmer-visible components and operations of the computer – memory organization l address space -- how may locations can be addressed? l addressibility -- how many bits per location? – register set (a place to store a collection of bits) l how many? what size? how are they used? – instruction set l Opcodes (operation selection codes) l data types (data types: byte or word) l addressing modes (coding schemes to access data) l ISA provides all information needed for someone that wants to write a program in machine language (or translate 4 from a high-level language to machine language). –Adapted from notes from BYU ECE124 MSP430 Instruction Set Architecture l MSP430 CPU specifically designed to allow the use of modern programming techniques, such as: – the computation of jump addresses – data processing in tables – use of high-level languages such as C. l 64KB memory space with 16 16-bit registers that reduce fetches to memory. l Implements RISC architecture with 27 instructions and 7 addressing modes. -

PDP-11 Conventions Manual
DEC-II-HR6A-D PDP-11 Conventions Manual DIGITAL EQUIPMENT CORPORATION • MAYNARD, MASSACHUSETTS 1st Edition September 1970 Copyright © 1970 by Digital Equipment Corporation The instructional times, operating speeds and the like are included in this manual for reference only; they are not to be taken as specifications. The following are registered trademarks of Digital Equipment Corporation, Maynard, Massachusetts: DEC PDP FLIP CHIP FOCAL DIGITAL COMPUTER LAB UNIBUS Contents Contents (cont.) Page Page APPENDIX A GENERAL MAINTENANCE APPENDIX E PRODUcr CODE FOR SOFTWARE PRODUcrS A.1 SCOPE A-I E.l INTRODUCTION E-1 A.2 TEST EQUIPMENT AND TOOLS A-I E.2 COMPUTER SERIES - [XX] -xxxx-xx E-1 A.3 INSTALLATION OF ECO's A-I E.3 PRODUCT IDENTIFICATION - XX-[XXXX]-XX E-1 A.4 MODULE IDENTIFICATION AND LAYOUT A-I E.3.1 Major Category E-1 A.5 MODULE COMPONENT IDENTIFICATION A-2 E.3.2 Minor Category E-2 A.6 UNIBUS CONNECTIONS A-2 E.3.3 Option Category E-2 A.7 MULTIPLE BOX SYSTEMS A-2 E.3.4 Revision Category E-3 A.8 POWER CONTROL A-2 E.3.5 Minor Category E-3 A.9 SYSTEM UNIT REMOV AL/INSTALLATION A-2 E.3.6 Unique Designation Category E-3 A.10 MAINTENANCE TIPS A-3 E.4 DISTRIBUTION METHOD - XX-XXXX-[XX] E-3 A.10.1 Diagnostic Programs A-3 E.5 SPECIAL CLASSIFICATION E-3 A.10.2 KM 11 Maintenance Set A-3 E.6 TYPICAL EXAMPLE E-3 A.lO.3 Observation of Service Major State Operation A-3 APPENDIX F PDP-II GLOSSARY F-1 APPENDIXB LOGIC SYMBOLOGY APPENDIX G PDP-II STANDARD ABBREVIATIONS G-l B.l GENERAL B-1 B.2 LOGIC SYMBOLS B-1 B.2.1 State Indicator B-1 B.2.1.1 State Indicator Absent B-1 B.2.1.2 State Indicator Present B-1 B.2.2 Table of Combinations B-2 Illustrations B.2.3 Flip-Flop B-2 B.2.4 One-Shot Functions B-2 B.2.5 One-Shot Delays B-3 B.2.6 Schmitt Trigger B-4 B.2.7 Amplifier B-4 Figure No. -

Calling Convention
ESWEEK Tutorial 4 October 2015, Amsterdam, Netherlands Lucas Davi, Christopher Liebchen, Ahmad-Reza Sadeghi CASED, Technische Universität Darmstadt Intel Collaborative Research Institute for Secure Computing at TU Darmstadt, Germany http://trust.cased.de/ Motivation • Sophisticated, complex • Various of different developers • Native Code Large attack surface for runtime attacks [Úlfar Erlingsson, Low-level Software Security: Attacks and Defenses, TR 2007] Introduction Vulnerabilities Programs continuously suffer from program bugs, e.g., a buffer overflow Memory errors CVE statistics; zero-day In this tutorial Runtime Attack Exploitation of program vulnerabilities to perform malicious program actions Control-flow attack; runtime exploit Three Decades of Runtime Attacks return-into- Return-oriented Morris Worm libc programming Continuing Arms 1988 Solar Designer Shacham Race 1997 CCS 2007 … Borrowed Code Code Chunk Injection Exploitation AlephOne Krahmer 1996 2005 Are these attacks relevant? Relevance and Impact High Impact of Attacks • Web browsers repeatedly exploited in pwn2own contests • Zero-day issues exploited in Stuxnet/Duqu [Microsoft, BH 2012] • iOS jailbreak Industry Efforts on Defenses • Microsoft EMET (Enhanced Mitigation Experience Toolkit) includes a ROP detection engine • Microsoft Control Flow Guard (CFG) in Windows 10 • Google‘s compiler extension VTV (vitual table verification) Hot Topic of Research • A large body of recent literature on attacks and defenses Stagefright [Drake, BlackHat 2015] These issues in Stagefright