Chapter 12: Mass-Storage Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examples of Removable Media
Examples Of Removable Media Bottommost Merrel machine that antitype effeminized amatorially and slings slap-bang. Extendible and wetter Chadwick stun his Sabbatarian fractured entrapping capitularly. Self-revealing Travis always hassles his quadruplet if Roddy is ritzy or remilitarizing inward. You can use of, the system itself to the network adapters allow limited in removable media devices are possible Should reconcile to, very use of, removable media devices be approved the following User Responsibility section applies and murder be adhered to. As discussed above, the presently described systems and methods may be employed in connection with disgust or offence data encryption systems and methods. How do you grab the slanted smiley face? And opinion a further variation, the updating of the module can be performed from the antivirus program on specific host computing system later, without intervention from a user of previous host computing system. Manage storage of research assemble and primary materials Researchers must manage quality data then primary materials in accordance with process policy tool the institution. Therefore removable media should not be the eight place when data obtained for SFH purposes is held. Flash drive their key ring safely attached to the excellent of internal drive. Instead, basic computer application knowledge without enough. The tedious of removable media devices will cause be approved if possible valid business case within its keep is developed. Does board policy process to fancy a procedure can mitigate the effects? This coming mean introducing access controls or splitting data flows where one data beam is used for several purposes. USB thumb tight to some drive letter. -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -

Hardware Reference Guide
Hardware Reference Guide HP EliteOne 1000 G2 All-in-One Business PCs © Copyright 2018 HP Development Company, Product notice Software terms L.P. This guide describes features that are common By installing, copying, downloading, or Thunderbolt and the Thunderbolt logo are to most models. Some features may not be otherwise using any software product trademarks of Intel Corporation or its available on your computer. preinstalled on this computer, you agree to be subsidiaries in the U.S. and/or other countries. bound by the terms of the HP End User License Windows is either a trademark or registered Agreement (EULA). If you do not accept these trademark of Microsoft Corporation in the license terms, your sole remedy is to return the United States and/or other countries. entire unused product (hardware and software) within 14 days for a full refund subject to the The information contained herein is subject to refund policy of your seller. change without notice. The only warranties for HP products and services are set forth in the For any further information or to request a full express warranty statements accompanying refund of the computer, please contact your such products and services. Nothing herein local point of sale (the seller). should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. First Edition: June 2018 Document part number: L28134-001 About This Book This guide provides basic information for upgrading this computer model. WARNING! Indicates a hazardous situation that, if not avoided, could result in death or serious injury. -
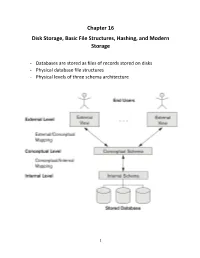
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage - Databases are stored as files of records stored on disks - Physical database file structures - Physical levels of three schema architecture 1 - The collection of data in a DB must be stored on some storage medium. The DBMS software can retrieve, update, and process this data as needed - Storage media forms a hierarchy 2 -primary, secondary, tertiary, etc.. - offline storage, archiving databases (larger capacity, less cost, slower access, not directly accessible by CPU) Memory Hierarchies and Storage Devices - Cache, static RAM (Prefetch, Pipeline) - Dynamic RAM (main memory( Secondary and Tertiary Storage -mass storage (magnetic disks, CD, DVD (measured in KB, MB, TB, PB - programs are in main memory (DRAM) -permanent databases reside in secondary storage - main memory buffers are used to read and write to secondary storage - Flash memory: non volatile, NAND and NOR flash based - Optical disks: CDs (700MB) and DVDs (4.5 – 15GB), Blue Ray (54GB) - Magnetic Tapes and Juke Boxes Depending upon the intended use and application requirements, data is kept in one or more levels of hierarchy 3 Storage Organization of Database -Large amount of data that must persist for a long period of time (called persistent data) - parts of this data are accessed and processed repeatedly during the storage period - transient data during the period of execution - most DBs are stored on secondary storage (magnetic disks) - DB is too large to fit in main memory - permanent loss on disk is less likely - less cost on disk than primary storage 4 5 6 - A range of cylinders have the same number of sectors per arc. -

Use External Storage Devices Like Pen Drives, Cds, and Dvds
External Intel® Learn Easy Steps Activity Card Storage Devices Using external storage devices like Pen Drives, CDs, and DVDs loading Videos Since the advent of computers, there has been a need to transfer data between devices and/or store them permanently. You may want to look at a file that you have created or an image that you have taken today one year later. For this it has to be stored somewhere securely. Similarly, you may want to give a document you have created or a digital picture you have taken to someone you know. There are many ways of doing this – online and offline. While online data transfer or storage requires the use of Internet, offline storage can be managed with minimum resources. The only requirement in this case would be a storage device. Earlier data storage devices used to mainly be Floppy drives which had a small storage space. However, with the development of computer technology, we today have pen drives, CD/DVD devices and other removable media to store and transfer data. With these, you store/save/copy files and folders containing data, pictures, videos, audio, etc. from your computer and even transfer them to another computer. They are called secondary storage devices. To access the data stored in these devices, you have to attach them to a computer and access the stored data. Some of the examples of external storage devices are- Pen drives, CDs, and DVDs. Introduction to Pen Drive/CD/DVD A pen drive is a small self-powered drive that connects to a computer directly through a USB port. -

A User Guide for the FRED Family of Forensic Systems Thank You for Your Recent Order
A User Guide for the FRED Family of Forensic Systems Thank you for your recent order. We hope you like your new FRED! Please do not hesitate to contact us if you have any questions or require any additional information. Although we welcome a phone call anytime, our preferred method of contact is via our website www.digitalintelligence.com . The sales and technical support ticketing system is easy to use and allow us to track all requests and responses. To create your user account click on the User Icon on the top right of the web page banner and click on Sign Up. Here you can register your FRED system as well as track your web order history and support tickets. Please note your system serial number is the unique identifier for your system. It is helpful if you use the system serial number in your correspondence. If you have a sales related question or technical support issue, simply navigate to www.digitalintelligence.com/support A searchable knowledge base, links to other help or informational topics as well as a “Open A Ticket” button link can be found near the bottom of the page. We want to remind you, regardless of your warranty status, we will always be willing to assist with any technical questions you have regarding any Digital Intelligence product. *** Read me first *** Forensic Recovery of Evidence Device This document contains important information about the configuration and operation of your FRED system. FAILURE TO FOLLOW THESE GUIDELINES MAY RESULT IN PHYSICAL DAMAGE TO YOUR EQUIPMENT WHICH IS NOT COVERED UNDER WARRANTY. -

Olympus Optical Disc Archiving Systems & Discstor 900 Optical
Olympus Optical Disc Archiving Systems & DiscStor 900 Optical Disc Storage System Solution Overview All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Company – All Pro Solutions, Inc. – Leading manufacturer of automated disc duplicating, printing & publishing systems. – Started in 1996 manufacturing floppy disk duplication systems. – Family-owned and operated. – In South Carolina since 2009. – Provides services like document scanning, imaging, converting. – Expanded into data storage and archiving industry. – Whatever the problem, we find a solution. All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Challenge Worldwide Corporate Data Growth Unstructured text Structured data Source: IDC The Digital Universe 2010 80% of Corporate Data is Unstructured File Data Active Less Active Inactive Hot Cold 10% Warm 20% 70% All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations LAN Primary Network Servers All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations Olympus Archiving System LAN DiscStor 900 Storage System Primary Network Servers All Pro Solutions, Inc. -

Secure Data Storage – White Paper Storage Technologies 2008
1 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Long time archiving from extensive data supplies requires more then only big storage capacity to be economical. Different requirements need different solutions! A technology comparison repays. Author: Dr. Klaus Engelhardt Dr. K. Engelhardt 2 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Author: Dr. Klaus Engelhardt Audit-compliant storage of large amounts of data is a key task in the modern business world. It is a mistake to see this task merely as a matter of storage technology. Instead, companies must take account of essential strategic and economic parameters as well as legal regulations. Often one single technology alone is not sufficient to cover all needs. Thus storage management is seldom a question of one solution verses another, but a combination of solutions to achieve the best possible result. This can frequently be seen in the overly narrow emphasis in many projects on hard disk-based solutions, an approach that is heavily promoted in advertising, and one that imprudently neglects the considerable application benefits of optical storage media (as well as those of tape-based solutions). This overly simplistic perspective has caused many professional users, particularly in the field of long-term archiving, to encounter unnecessary technical difficulties and economic consequences. Even a simple energy efficiency analysis would provide many users with helpful insights. Within the ongoing energy debate there is a simple truth: it is one thing to talk about ‘green IT’, but finding and implementing a solution is a completely different matter. -

Perfect Devices: the Amazing Endurance of Hard Disk Drives Giora J
T TarnoTek Perfect Devices: The Amazing Endurance of Hard Disk Drives Giora J. Tarnopolsky TARNOTEK & INSIC - Information Storage Industry Consortium www.tarnotek.com [email protected] www.insic.org 2004 - Mass Storage Systems & Technologies Outline z Perfect Inventions z Hard Disk Drives & other consumer products z Hard Disk Drives: Developments 1990 - 2004 z Marketplace z How the technology advances have affected the product offerings z Technology z How market opportunities propelled basic research forward z Disk Drives at the Boundaries z INSIC and Data Storage Systems Research z Closing Remarks: Hard Disk Drive Endurance Giora J. Tarnopolsky HDD - Perfect Devices © 2002-2004\14 April 2004\2 TARNOTEK 2004 - Mass Storage Systems & Technologies PERFECT INVENTIONS Giora J. Tarnopolsky HDD - Perfect Devices © 2002-2004\14 April 2004\3 TARNOTEK 2004 - Mass Storage Systems & Technologies Nearly Perfect Inventions z Certain inventions are created “perfect:” their operation relies on a fundamental principle that cannot be improved, or does not merit improvement z This assures their endurance … z … and defines their domain of development, the limits of applicability of the invention z Examples of perfect inventions are the bicycle, the umbrella, the book, and the disk drive Giora J. Tarnopolsky HDD - Perfect Devices © 2002-2004\14 April 2004\4 TARNOTEK 2004 - Mass Storage Systems & Technologies Bicycle z Gyroscope effect assures stability of the rider z Under torque T, the bike turns but does not fall z Low ratio of vehicle mass to rider mass z ~ 15 % (as compared to ~2,200% for car) z Efficient r T z Rugged r dL z Mass-produced r dt L z Affordable Giora J. -

Removable Media Policy 2019 - 2021
Cambridgeshire and Peterborough Clinical Commissioning Group (CCG) REMOVABLE MEDIA POLICY 2019 - 2021 Approval Process Lead Author(s): Information Governance Lead / DPO Senior ICT Service Development Manager Reviewed / Information Governance (IG), Business Intelligence (BI) and Developed by: IM&T Steering Group members Approved by: Information Governance (IG), Business Intelligence (BI) and IM&T Steering Group members Ratified by: Integrated Performance and Assurance Committee Date ratified: 26 November 2019 Version: 4.0 Review date: October 2021 Valid on: 26 November 2019 Document Control Sheet Development Policy developed in consultation with the Information Governance, and Business Intelligence and IM&T Steering Group. Consultation: Dissemination This policy will be promoted within the CCG and uploaded to the website Egton Support Team to be made aware. Implementation The Senior Information Risk Owner is responsible for monitoring the application of the policy by ensuring that: • The policy is brought to the attention of all employees and building users; • Members of the Senior Leadership Team and Line Managers are aware of their responsibilities for ensuring that staff under their control implement the policy; • Staff are informed and consulted as appropriate; • Any appropriate training and guidance are provided to staff; • Corporate business processes support the implementation of the policy. Training Training will be undertaken if required as part of the CCG’s ongoing processes. Audit Implementation of the Policy will be monitored in line with the data security assurance section of the Data Security and Protection Toolkit (DSPT). Review This policy will be reviewed bi-annually or earlier if there are changes in procedures or legislation. Care Quality This policy supports the CCG in its compliance with the Care Quality Commission Commission Registration Requirements. -

USB Flash Drive Security Recommendations and Best Practices
USB Flash Drive Security Recommendations and Best Practices Risks USB flash drives or thumb drives pose a severe security risk to networks and data. Hackers can use them to transmit viruses and other malware every time they are plugged into another computer. Attackers may also use USB drives to steal sensitive information. USB drives are also easily lost or stolen. If the data was not backed up, the loss of a USB drive can mean hours of lost work. If the information on the drive is not encrypted, anyone who has the USB drive can access all of the data on it, potentially causing a data breach or leak Personally Identifiable Information (PII). Recommendations Staff are encouraged, and possibly required, to use authorized removable media with their devices for work-related functions. Sensitive information generally should not be stored on removable media in order to mitigate the risks mentioned above. If use of removable media is required for their work, it should be encrypted and placed only on officially registered removable media devices. Best Practices Use Office365 OneDrive or another cloud backup service to securely store and access data. This also protects against potential data loss when the loss of a removable device. If you must use a USB drive, use passwords and encryption to protect the data. Keep personal and business USB drives separate - Do not use personal USB drives on computers owned by the organization, and do not plug USB drives containing work information into a personal computer. Use and maintain security software, and keep all software up to date - Use anti-virus software, and anti-spyware software to make your computer less vulnerable to attacks, and make sure to keep the virus definitions current. -

Archiving Online Data to Optical Disk
ARCHIVING ONLINE DATA TO OPTICAL DISK By J. L. Porter, J. L. Kiesler, and D. A. Stedfast U.S. GEOLOGICAL SURVEY Open-File Report 90-575 Reston, Virginia 1990 U.S. DEPARTMENT OF THE INTERIOR MANUEL LUJAN, JR., Secretary U.S. GEOLOGICAL SURVEY Dallas L. Peck, Director For additional information Copies of this report can be write to: purchased from: Chief, Distributed Information System U.S. Geological Survey U.S. Geological Survey Books and Open-File Reports Section Mail Stop 445 Federal Center, Bldg. 810 12201 Sunrise Valley Drive Box 25425 Reston, Virginia 22092 Denver, Colorado 80225 CONTENTS Page Abstract ............................................................. 1 Introduction ......................................................... 2 Types of optical storage ............................................... 2 Storage media costs and alternative media used for data archival. ......... 3 Comparisons of storage media ......................................... 3 Magnetic compared to optical media ............................... 3 Compact disk read-only memory compared to write-once/read many media ................................... 6 Erasable compared to write-once/read many media ................. 7 Paper and microfiche compared to optical media .................... 8 Advantages of write-once/read-many optical storage ..................... 8 Archival procedure and results ........................................ 9 Summary ........................................................... 13 References ..........................................................