Archiving Online Data to Optical Disk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 12: Mass-Storage Systems
Chapter 12: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space Management RAID Structure Disk Attachment Stable-Storage Implementation Tertiary Storage Devices Operating System Issues Performance Issues Objectives Describe the physical structure of secondary and tertiary storage devices and the resulting effects on the uses of the devices Explain the performance characteristics of mass-storage devices Discuss operating-system services provided for mass storage, including RAID and HSM Overview of Mass Storage Structure Magnetic disks provide bulk of secondary storage of modern computers Drives rotate at 60 to 200 times per second Transfer rate is rate at which data flow between drive and computer Positioning time (random-access time) is time to move disk arm to desired cylinder (seek time) and time for desired sector to rotate under the disk head (rotational latency) Head crash results from disk head making contact with the disk surface That’s bad Disks can be removable Drive attached to computer via I/O bus Busses vary, including EIDE, ATA, SATA, USB, Fibre Channel, SCSI Host controller in computer uses bus to talk to disk controller built into drive or storage array Moving-head Disk Mechanism Overview of Mass Storage Structure (Cont.) Magnetic tape Was early secondary-storage medium Relatively permanent and holds large quantities of data Access time slow Random access ~1000 times slower than disk Mainly used for backup, storage of infrequently-used data, transfer medium between systems Kept in spool and wound or rewound past read-write head Once data under head, transfer rates comparable to disk 20-200GB typical storage Common technologies are 4mm, 8mm, 19mm, LTO-2 and SDLT Disk Structure Disk drives are addressed as large 1-dimensional arrays of logical blocks, where the logical block is the smallest unit of transfer. -
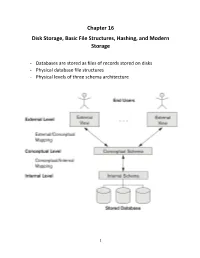
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage
Chapter 16 Disk Storage, Basic File Structures, Hashing, and Modern Storage - Databases are stored as files of records stored on disks - Physical database file structures - Physical levels of three schema architecture 1 - The collection of data in a DB must be stored on some storage medium. The DBMS software can retrieve, update, and process this data as needed - Storage media forms a hierarchy 2 -primary, secondary, tertiary, etc.. - offline storage, archiving databases (larger capacity, less cost, slower access, not directly accessible by CPU) Memory Hierarchies and Storage Devices - Cache, static RAM (Prefetch, Pipeline) - Dynamic RAM (main memory( Secondary and Tertiary Storage -mass storage (magnetic disks, CD, DVD (measured in KB, MB, TB, PB - programs are in main memory (DRAM) -permanent databases reside in secondary storage - main memory buffers are used to read and write to secondary storage - Flash memory: non volatile, NAND and NOR flash based - Optical disks: CDs (700MB) and DVDs (4.5 – 15GB), Blue Ray (54GB) - Magnetic Tapes and Juke Boxes Depending upon the intended use and application requirements, data is kept in one or more levels of hierarchy 3 Storage Organization of Database -Large amount of data that must persist for a long period of time (called persistent data) - parts of this data are accessed and processed repeatedly during the storage period - transient data during the period of execution - most DBs are stored on secondary storage (magnetic disks) - DB is too large to fit in main memory - permanent loss on disk is less likely - less cost on disk than primary storage 4 5 6 - A range of cylinders have the same number of sectors per arc. -

Olympus Optical Disc Archiving Systems & Discstor 900 Optical
Olympus Optical Disc Archiving Systems & DiscStor 900 Optical Disc Storage System Solution Overview All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Company – All Pro Solutions, Inc. – Leading manufacturer of automated disc duplicating, printing & publishing systems. – Started in 1996 manufacturing floppy disk duplication systems. – Family-owned and operated. – In South Carolina since 2009. – Provides services like document scanning, imaging, converting. – Expanded into data storage and archiving industry. – Whatever the problem, we find a solution. All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Challenge Worldwide Corporate Data Growth Unstructured text Structured data Source: IDC The Digital Universe 2010 80% of Corporate Data is Unstructured File Data Active Less Active Inactive Hot Cold 10% Warm 20% 70% All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations LAN Primary Network Servers All Pro Solutions, Inc. | 1351 E. Black Street, Rock Hill, SC 29730 USA | Tel: +1.803.980.4141 | Web: www.allprosolutions.com | Email: [email protected] The Solution Blu-Ray Disc – The ideal media for long-term archival • Longevity • Capacity - Extendable • Security • Removability • Data Migration • Accessibility • Compliance • Compatibility • Green Technology • Power Consumption Networked Client Workstations Olympus Archiving System LAN DiscStor 900 Storage System Primary Network Servers All Pro Solutions, Inc. -

Secure Data Storage – White Paper Storage Technologies 2008
1 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Long time archiving from extensive data supplies requires more then only big storage capacity to be economical. Different requirements need different solutions! A technology comparison repays. Author: Dr. Klaus Engelhardt Dr. K. Engelhardt 2 Secure Data Storage – White Paper Storage Technologies 2008 Secure Data Storage - An overview of storage technology - Author: Dr. Klaus Engelhardt Audit-compliant storage of large amounts of data is a key task in the modern business world. It is a mistake to see this task merely as a matter of storage technology. Instead, companies must take account of essential strategic and economic parameters as well as legal regulations. Often one single technology alone is not sufficient to cover all needs. Thus storage management is seldom a question of one solution verses another, but a combination of solutions to achieve the best possible result. This can frequently be seen in the overly narrow emphasis in many projects on hard disk-based solutions, an approach that is heavily promoted in advertising, and one that imprudently neglects the considerable application benefits of optical storage media (as well as those of tape-based solutions). This overly simplistic perspective has caused many professional users, particularly in the field of long-term archiving, to encounter unnecessary technical difficulties and economic consequences. Even a simple energy efficiency analysis would provide many users with helpful insights. Within the ongoing energy debate there is a simple truth: it is one thing to talk about ‘green IT’, but finding and implementing a solution is a completely different matter. -

The Future of Data Storage Technologies
International Technology Research Institute World Technology (WTEC) Division WTEC Panel Report on The Future of Data Storage Technologies Sadik C. Esener (Panel Co-Chair) Mark H. Kryder (Panel Co-Chair) William D. Doyle Marvin Keshner Masud Mansuripur David A. Thompson June 1999 International Technology Research Institute R.D. Shelton, Director Geoffrey M. Holdridge, WTEC Division Director and ITRI Series Editor 4501 North Charles Street Baltimore, Maryland 21210-2699 WTEC Panel on the Future of Data Storage Technologies Sponsored by the National Science Foundation, Defense Advanced Research Projects Agency and National Institute of Standards and Technology of the United States government. Dr. Sadik C. Esener (Co-Chair) Dr. Marvin Keshner Dr. David A. Thompson Prof. of Electrical and Computer Director, Information Storage IBM Fellow Engineering & Material Sciences Laboratory Research Division Dept. of Electrical & Computer Hewlett-Packard Laboratories International Business Machines Engineering 1501 Page Mill Road Corporation University of California, San Diego Palo Alto, CA 94304-1126 Almaden Research Center 9500 Gilman Drive Mail Stop K01/802 La Jolla, CA 92093-0407 Dr. Masud Mansuripur 650 Harry Road Optical Science Center San Jose, CA 95120-6099 Dr. Mark H. Kryder (Co-Chair) University of Arizona Director, Data Storage Systems Center Tucson, AZ 85721 Carnegie Mellon University Roberts Engineering Hall, Rm. 348 Pittsburgh, PA 15213-3890 Dr. William D. Doyle Director, MINT Center University of Alabama Box 870209 Tuscaloosa, AL 35487-0209 INTERNATIONAL TECHNOLOGY RESEARCH INSTITUTE World Technology (WTEC) Division WTEC at Loyola College (previously known as the Japanese Technology Evaluation Center, JTEC) provides assessments of foreign research and development in selected technologies under a cooperative agreement with the National Science Foundation (NSF). -

3 Secondary Storage.PDF
CAPE COMPUTER SCIENCE SECONDARY STORAGE Secondary storage is needed 1. because there is a limit on the size of primary memory (due to cost) and 2. because RAM is volatile and so data needed for future use must be stored somewhere else so that it can be retrieved when necessary. Secondary storage is also used for backup and archives. When we consider secondary storage devices we must bear in mind the following characteristics of each device : Capacity Access speed Access method and portability Floppy Disk This is a 3.5 inch magnetic disk of flexible material which until recently was a standard feature on most microcomputers. Typically it stores 1.44 MB of data. It’s a thin plastic circle coated with a magnetic material and encased in a rigid plastic to protect it. A metal sliding access shuttle opens when the disk is in the machine allowing the read/write head access to the disk. Data can be written to and erased from a floppy disk. A write protect tab can be used to prevent accidental overwriting of data. Before data can be written to a disk, it must be formatted. This prepares the disk for use by creating a magnetic map on the disks surface. This map consists of tracks and sectors. Formatting also prepares the file allocation table (FAT). The address of a file on a floppy disk is comprised of the track number and the sector number. Floppy disks are direct access devices but they are slow compared to hard disks. The floppies great advantage has been its use as a device to help transport small files between machines. -

Computer Files & Data Storage
STORAGE & FILE CONCEPTS, UTILITIES (Pages 6, 150-158 - Discovering Computers & Microsoft Office 2010) I. Computer files – data, information or instructions residing on secondary storage are stored in the form of a file. A. Software files are also called program files. Program files (instructions) are created by a computer programmer and generally cannot be modified by a user. It’s important that we not move or delete program files because your computer requires them to perform operations. Program files are also referred to as “executables”. 1. You can identify a program file by its extension:“.EXE”, “.COM”, “.BAT”, “.DLL”, “.SYS”, or “.INI” (there are others) or a distinct program icon. B. Data files - when you select a “save” option while using an application program, you are in essence creating a data file. Users create data files. 1. File naming conventions refer to the guidelines followed while assigning file names and will vary with the operating system and application in use (see figure 4-1). File names in Windows 7 may be up to 255 characters, you're not allowed to use reserved characters or certain reserved words. File extensions are used to identify the application that was used to create the file and format data in a manner recognized by the source application used to create it. FALL 2012 1 II. Selecting secondary storage media A. There are three type of technologies for storage devices: magnetic, optical, & solid state, there are advantages & disadvantages between them. When selecting a secondary storage device, certain factors should be considered: 1. Capacity - the capacity of computer storage is expressed in bytes. -

Digital Preservation Guide: 3.5-Inch Floppy Disks Caralie Heinrichs And
DIGITAL PRESERVATION GUIDE: 3.5-Inch Floppy Disks Digital Preservation Guide: 3.5-Inch Floppy Disks Caralie Heinrichs and Emilie Vandal ISI 6354 University of Ottawa Jada Watson Friday, December 13, 2019 DIGITAL PRESERVATION GUIDE 2 Table of Contents Introduction ................................................................................................................................................. 3 History of the Floppy Disk ......................................................................................................................... 3 Where, when, and by whom was it developed? 3 Why was it developed? 4 How Does a 3.5-inch Floppy Disk Work? ................................................................................................. 5 Major parts of a floppy disk 5 Writing data on a floppy disk 7 Preservation and Digitization Challenges ................................................................................................. 8 Physical damage and degradation 8 Hardware and software obsolescence 9 Best Practices ............................................................................................................................................. 10 Storage conditions 10 Description and documentation 10 Creating a disk image 11 Ensuring authenticity: Write blockers 11 Ensuring reliability: Sustainability of the disk image file format 12 Metadata 12 Virus scanning 13 Ensuring integrity: checksums 13 Identifying personal or sensitive information 13 Best practices: Use of hardware and software 14 Hardware -

CS100: Introduction to Computer Science
In-class Exercise: CS100: Introduction to n What is a flip-flop? n What are the properties of flip-flops? Computer Science n Draw a simple flip-flop circuit? Lecture 3: Data Storage -- Mass storage & representing information Review: bits, their storage and main memory Mass Storage or Secondary Storage n Bits n Magnetic disks n Boolean operations n CDs n Gates n DVDs n Flip-flops (store a single bit) n Magnetic tapes n Main memory (RAM) n Flash drives q Cell, Byte, Address Mass Storage or Secondary Storage Mass Storage Systems n On-line versus off-line n Magnetic Systems q Online - connected and readily available to the q Hard Disk machine q Floppy Disk q Offline - human intervention required q Tape n Typically larger than main memory n Optical Systems n Typically less volatile than main memory q CD n Typically slower than main memory q DVD n Flash Drives 1 Figure 1.9 A magnetic disk storage Magnetic Disks system n Floppy disk q Low capacity n 3.5 inch diskettes 1.44MB q A single plastic disk n Hard Disk system q High capacity systems q Multiple disks mounted on a spindle, multiple read/write heads move in unison n Cylinder: a set of tracks n Platter : a flat circular disk q Heads do not tough the surface of disks Measuring the Performance of Hard Disk Capacity of Hard Disk Systems Systems n (1) seek time n 5MB (1956 by IBM) q The time to move heads from one track to another n 20MB (1980s) n (2) rotation delay n 1 GB (1990s) q Half the time required for the disk to make a complete rotation n 20 GB – 768 GB (3/4) (2006) n (3) access time -

Unit 5: Memory Organizations
Memory Organizations Unit 5: Memory Organizations Introduction This unit considers the organization of a computer's memory system. The characteristics of the most important storage technologies are described in detail. Basically memories are classified as main memory and secondary memory. Main memory with many different categories are described in Lesson 1. Lesson 2 focuses the secondary memory including the details of floppy disks and hard disks. Lesson 1: Main Memory 1.1 Learning Objectives On completion of this lesson you will be able to : • describe the memory organization • distinguish between ROM, RAM, PROM, EEPROM and • other primary memory elements. 1.2 Organization Computer systems combine binary digits to form groups called words. The size of the word varies from system to system. Table 5.1 illustrates the current word sizes most commonly used with the various computer systems. Two decades ago, IBM introduced their 8-bit PC. This was Memory Organization followed a few years later by the 16-bit PC AT microcomputer, and already it has been replaced with 32- and 64-bit systems. The machine with increased word size is generally faster because it can process more bits of information in the same time span. The current trend is in the direction of the larger word size. Microcomputer main memories are generally made up of many individual chips and perform different functions. The ROM, RAM, Several types of semi- PROM, and EEPROM memories are used in connection with the conductor memories. primary memory of a microcomputers. The main memory generally store computer words as multiple of bytes; each byte consisting of eight bits. -

SŁOWNIK POLSKO-ANGIELSKI ELEKTRONIKI I INFORMATYKI V.03.2010 (C) 2010 Jerzy Kazojć - Wszelkie Prawa Zastrzeżone Słownik Zawiera 18351 Słówek
OTWARTY SŁOWNIK POLSKO-ANGIELSKI ELEKTRONIKI I INFORMATYKI V.03.2010 (c) 2010 Jerzy Kazojć - wszelkie prawa zastrzeżone Słownik zawiera 18351 słówek. Niniejszy słownik objęty jest licencją Creative Commons Uznanie autorstwa - na tych samych warunkach 3.0 Polska. Aby zobaczyć kopię niniejszej licencji przejdź na stronę http://creativecommons.org/licenses/by-sa/3.0/pl/ lub napisz do Creative Commons, 171 Second Street, Suite 300, San Francisco, California 94105, USA. Licencja UTWÓR (ZDEFINIOWANY PONIŻEJ) PODLEGA NINIEJSZEJ LICENCJI PUBLICZNEJ CREATIVE COMMONS ("CCPL" LUB "LICENCJA"). UTWÓR PODLEGA OCHRONIE PRAWA AUTORSKIEGO LUB INNYCH STOSOWNYCH PRZEPISÓW PRAWA. KORZYSTANIE Z UTWORU W SPOSÓB INNY NIŻ DOZWOLONY NA PODSTAWIE NINIEJSZEJ LICENCJI LUB PRZEPISÓW PRAWA JEST ZABRONIONE. WYKONANIE JAKIEGOKOLWIEK UPRAWNIENIA DO UTWORU OKREŚLONEGO W NINIEJSZEJ LICENCJI OZNACZA PRZYJĘCIE I ZGODĘ NA ZWIĄZANIE POSTANOWIENIAMI NINIEJSZEJ LICENCJI. 1. Definicje a."Utwór zależny" oznacza opracowanie Utworu lub Utworu i innych istniejących wcześniej utworów lub przedmiotów praw pokrewnych, z wyłączeniem materiałów stanowiących Zbiór. Dla uniknięcia wątpliwości, jeżeli Utwór jest utworem muzycznym, artystycznym wykonaniem lub fonogramem, synchronizacja Utworu w czasie z obrazem ruchomym ("synchronizacja") stanowi Utwór Zależny w rozumieniu niniejszej Licencji. b."Zbiór" oznacza zbiór, antologię, wybór lub bazę danych spełniającą cechy utworu, nawet jeżeli zawierają nie chronione materiały, o ile przyjęty w nich dobór, układ lub zestawienie ma twórczy charakter. -

EE 4504 Computer Organization Overview
Overview Historically, the limiting factor in a computer’s performance has been memory access time – Memory speed has been slow compared to the speed of the processor EE 4504 – A process could be bottlenecked by the memory Computer Organization system’s inability to “keep up” with the processor Our goal in this section is to study the development of an effective memory Section 3 organization that supports the processing Computer Memory power of the CPU – General memory organization and performance – “Internal” memory components and their use – “External” memory components and their use Reading: Text, chapters 4 and 5 EE 4504 Section 3 1 EE 4504 Section 3 2 1 Terminology Capacity: the amount of information that Access time: can be contained in a memory unit -- – For RAM, the time to address the unit and usually in terms of words or bytes perform the transfer Word: the natural unit of organization in – For non-random access memory, the time to position the R/W head over the desired location the memory, typically the number of bits used to represent a number Memory cycle time: Access time plus any other time required before a second access Addressable unit: the fundamental data can be started element size that can be addressed in the memory -- typically either the word size or Access technique: how are memory individual bytes contents accessed – Random access: Unit of transfer: The number of data » Each location has a unique physical address elements transferred at a time -- usually » Locations can be accessed in any order and bits in main