Examples of Removable Media
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 12: Mass-Storage Systems
Chapter 12: Mass-Storage Systems Overview of Mass Storage Structure Disk Structure Disk Attachment Disk Scheduling Disk Management Swap-Space Management RAID Structure Disk Attachment Stable-Storage Implementation Tertiary Storage Devices Operating System Issues Performance Issues Objectives Describe the physical structure of secondary and tertiary storage devices and the resulting effects on the uses of the devices Explain the performance characteristics of mass-storage devices Discuss operating-system services provided for mass storage, including RAID and HSM Overview of Mass Storage Structure Magnetic disks provide bulk of secondary storage of modern computers Drives rotate at 60 to 200 times per second Transfer rate is rate at which data flow between drive and computer Positioning time (random-access time) is time to move disk arm to desired cylinder (seek time) and time for desired sector to rotate under the disk head (rotational latency) Head crash results from disk head making contact with the disk surface That’s bad Disks can be removable Drive attached to computer via I/O bus Busses vary, including EIDE, ATA, SATA, USB, Fibre Channel, SCSI Host controller in computer uses bus to talk to disk controller built into drive or storage array Moving-head Disk Mechanism Overview of Mass Storage Structure (Cont.) Magnetic tape Was early secondary-storage medium Relatively permanent and holds large quantities of data Access time slow Random access ~1000 times slower than disk Mainly used for backup, storage of infrequently-used data, transfer medium between systems Kept in spool and wound or rewound past read-write head Once data under head, transfer rates comparable to disk 20-200GB typical storage Common technologies are 4mm, 8mm, 19mm, LTO-2 and SDLT Disk Structure Disk drives are addressed as large 1-dimensional arrays of logical blocks, where the logical block is the smallest unit of transfer. -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -

Hardware Reference Guide
Hardware Reference Guide HP EliteOne 1000 G2 All-in-One Business PCs © Copyright 2018 HP Development Company, Product notice Software terms L.P. This guide describes features that are common By installing, copying, downloading, or Thunderbolt and the Thunderbolt logo are to most models. Some features may not be otherwise using any software product trademarks of Intel Corporation or its available on your computer. preinstalled on this computer, you agree to be subsidiaries in the U.S. and/or other countries. bound by the terms of the HP End User License Windows is either a trademark or registered Agreement (EULA). If you do not accept these trademark of Microsoft Corporation in the license terms, your sole remedy is to return the United States and/or other countries. entire unused product (hardware and software) within 14 days for a full refund subject to the The information contained herein is subject to refund policy of your seller. change without notice. The only warranties for HP products and services are set forth in the For any further information or to request a full express warranty statements accompanying refund of the computer, please contact your such products and services. Nothing herein local point of sale (the seller). should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. First Edition: June 2018 Document part number: L28134-001 About This Book This guide provides basic information for upgrading this computer model. WARNING! Indicates a hazardous situation that, if not avoided, could result in death or serious injury. -

Use External Storage Devices Like Pen Drives, Cds, and Dvds
External Intel® Learn Easy Steps Activity Card Storage Devices Using external storage devices like Pen Drives, CDs, and DVDs loading Videos Since the advent of computers, there has been a need to transfer data between devices and/or store them permanently. You may want to look at a file that you have created or an image that you have taken today one year later. For this it has to be stored somewhere securely. Similarly, you may want to give a document you have created or a digital picture you have taken to someone you know. There are many ways of doing this – online and offline. While online data transfer or storage requires the use of Internet, offline storage can be managed with minimum resources. The only requirement in this case would be a storage device. Earlier data storage devices used to mainly be Floppy drives which had a small storage space. However, with the development of computer technology, we today have pen drives, CD/DVD devices and other removable media to store and transfer data. With these, you store/save/copy files and folders containing data, pictures, videos, audio, etc. from your computer and even transfer them to another computer. They are called secondary storage devices. To access the data stored in these devices, you have to attach them to a computer and access the stored data. Some of the examples of external storage devices are- Pen drives, CDs, and DVDs. Introduction to Pen Drive/CD/DVD A pen drive is a small self-powered drive that connects to a computer directly through a USB port. -

A User Guide for the FRED Family of Forensic Systems Thank You for Your Recent Order
A User Guide for the FRED Family of Forensic Systems Thank you for your recent order. We hope you like your new FRED! Please do not hesitate to contact us if you have any questions or require any additional information. Although we welcome a phone call anytime, our preferred method of contact is via our website www.digitalintelligence.com . The sales and technical support ticketing system is easy to use and allow us to track all requests and responses. To create your user account click on the User Icon on the top right of the web page banner and click on Sign Up. Here you can register your FRED system as well as track your web order history and support tickets. Please note your system serial number is the unique identifier for your system. It is helpful if you use the system serial number in your correspondence. If you have a sales related question or technical support issue, simply navigate to www.digitalintelligence.com/support A searchable knowledge base, links to other help or informational topics as well as a “Open A Ticket” button link can be found near the bottom of the page. We want to remind you, regardless of your warranty status, we will always be willing to assist with any technical questions you have regarding any Digital Intelligence product. *** Read me first *** Forensic Recovery of Evidence Device This document contains important information about the configuration and operation of your FRED system. FAILURE TO FOLLOW THESE GUIDELINES MAY RESULT IN PHYSICAL DAMAGE TO YOUR EQUIPMENT WHICH IS NOT COVERED UNDER WARRANTY. -

Removable Media Policy 2019 - 2021
Cambridgeshire and Peterborough Clinical Commissioning Group (CCG) REMOVABLE MEDIA POLICY 2019 - 2021 Approval Process Lead Author(s): Information Governance Lead / DPO Senior ICT Service Development Manager Reviewed / Information Governance (IG), Business Intelligence (BI) and Developed by: IM&T Steering Group members Approved by: Information Governance (IG), Business Intelligence (BI) and IM&T Steering Group members Ratified by: Integrated Performance and Assurance Committee Date ratified: 26 November 2019 Version: 4.0 Review date: October 2021 Valid on: 26 November 2019 Document Control Sheet Development Policy developed in consultation with the Information Governance, and Business Intelligence and IM&T Steering Group. Consultation: Dissemination This policy will be promoted within the CCG and uploaded to the website Egton Support Team to be made aware. Implementation The Senior Information Risk Owner is responsible for monitoring the application of the policy by ensuring that: • The policy is brought to the attention of all employees and building users; • Members of the Senior Leadership Team and Line Managers are aware of their responsibilities for ensuring that staff under their control implement the policy; • Staff are informed and consulted as appropriate; • Any appropriate training and guidance are provided to staff; • Corporate business processes support the implementation of the policy. Training Training will be undertaken if required as part of the CCG’s ongoing processes. Audit Implementation of the Policy will be monitored in line with the data security assurance section of the Data Security and Protection Toolkit (DSPT). Review This policy will be reviewed bi-annually or earlier if there are changes in procedures or legislation. Care Quality This policy supports the CCG in its compliance with the Care Quality Commission Commission Registration Requirements. -

USB Flash Drive Security Recommendations and Best Practices
USB Flash Drive Security Recommendations and Best Practices Risks USB flash drives or thumb drives pose a severe security risk to networks and data. Hackers can use them to transmit viruses and other malware every time they are plugged into another computer. Attackers may also use USB drives to steal sensitive information. USB drives are also easily lost or stolen. If the data was not backed up, the loss of a USB drive can mean hours of lost work. If the information on the drive is not encrypted, anyone who has the USB drive can access all of the data on it, potentially causing a data breach or leak Personally Identifiable Information (PII). Recommendations Staff are encouraged, and possibly required, to use authorized removable media with their devices for work-related functions. Sensitive information generally should not be stored on removable media in order to mitigate the risks mentioned above. If use of removable media is required for their work, it should be encrypted and placed only on officially registered removable media devices. Best Practices Use Office365 OneDrive or another cloud backup service to securely store and access data. This also protects against potential data loss when the loss of a removable device. If you must use a USB drive, use passwords and encryption to protect the data. Keep personal and business USB drives separate - Do not use personal USB drives on computers owned by the organization, and do not plug USB drives containing work information into a personal computer. Use and maintain security software, and keep all software up to date - Use anti-virus software, and anti-spyware software to make your computer less vulnerable to attacks, and make sure to keep the virus definitions current. -

Removable Media Policy
Removable Media Policy Version: 2.0 Date: March 2016 Version Control Date Version Comments June 2013 1.1 Updated following comments from IMG November 2013 1.2 Updated following comments from ITPARG July 2013 1.3 Updated following comments September 2015 1.4 Policy subject to full review December 2015 1.5 Draft approved at IMG February 2016 1.5 Union Consultation March 2016 2.0 Approved by Executive Decision V.2.0 Removable Media Policy Page 2 of 8 Table of Contents 1 Introduction ............................................................................................................................... 4 2 Policy Statement ....................................................................................................................... 4 3 Scope ....................................................................................................................................... 4 4 Handling Removable Media ...................................................................................................... 4 5 Responsibilities ......................................................................................................................... 7 Information Management Group (IMG) ......................................................................................... 7 Business IT .................................................................................................................................. 7 Internal Audit ............................................................................................................................... -

Westernu Computer Requirements
WesternU Computer Requirements Academic Year: 2018 – 2019 Minimum Specifications Recommended Specifications Processor/CPU Intel Core i5 Dual Core (equivalent or better) Intel Core i5 Quad Core (equivalent or better) Display/Screen Screen capable of 1024x768 resolution Screen capable of 1440 x 900 resolution or higher System Memory/RAM 8GB RAM 16GB RAM Hard Drive 250GB+ (SSD highly recommended, but not required) 250GB+ SSD (Solid-State Drive) Graphics/Video Integrated Intel HD (equivalent or better) Dedicated video card Removable Media CD/DVD combo drive (internal or external) CD-RW/DVD-RW combo drive (internal or external) Operating System Windows 7, 8.1, 10 or macOS High Sierra (10.13+) Windows 10 (64-Bit) or macOS High Sierra (10.13+) Ports USB 2.0 USB 3.0 Software • Microsoft Office (Office 365 acct. provided for free) • Microsoft Office (Office 365 acct. provided for free) • Internet Explorer 11 (Safari 11 for Mac) • Internet Explorer 11 (Safari 11 for Mac) • Adobe Reader (updated to newest version) • Adobe Reader (updated to newest version) • Anti-Virus w/ updatable virus definitions • Anti-Virus w/ updatable virus definitions o Win7: MS Security Essentials (free download) o Win7: MS Security Essentials (free download) o Win8/10: Windows Defender (included) o Win8/10: Windows Defender (included) • VLC Media Player (updated to newest version) • VLC Media Player (updated to newest version) • Java (updated to newest version) • Java (updated to newest version) • Flash (updated to newest version) • Flash (updated to newest version) Ethernet • 10/100 internal or adapter (e.g. USB to Ethernet) • 10/100/1000 internal or adapter (i.e. USB to Ethernet) • Ethernet cable • Ethernet cable Wireless/Ethernet • • Not required Not required Webcam • Not required • Built-in or external webcam Warranty • Not required, but highly recommended • 4-Year warranty (warranty duration should match or o See recommended column → exceed the years in your program/degree) WesternU students may use either Windows-based or Apple computers. -

Eventtracker: Removable Media Device Monitoring Version 7.X
EventTracker: Removable Media Device Monitoring Version 7.x EventTracker 8815 Centre Park Drive Columbia MD 21045 Publication Date: Dec 21, 2011 www.eventtracker.com EventTracker: Removable Media Device Monitoring Abstract With the introduction of newer portable devices, the security needs of protecting integrity and confidential data has been changed. An increasing need of portable access to the data has also increased the risk of sensitive or confidential data exposure. Therefore, to keep a record of removable media device activities has become one of the most important compliance factor for the enterprise. EventTracker’s advanced removable media monitoring capacity protects and monitors system(s) from illegal access or data theft. EventTracker helps user(s) to disable the unauthorized access to the machine and allow the trusted devices connection. Purpose This document will help you to enable the removable device monitoring and explains the procedure to find the Device ID and USB serial number. It also monitors insertion/removal and files written to and read from removable media such as CD/DVD and USB. Intended Audience Administrators who are assigned the task to monitor and manage events using EventTracker. Scope The configurations detailed in this guide are consistent with EventTracker Enterprise version 7.x. The instructions can be used while working with later releases of EventTracker Enterprise. The information contained in this document represents the current view of Prism Microsystems Inc. on the issues discussed as of the date of publication. Because Prism Microsystems must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Prism Microsystems, and Prism Microsystems cannot guarantee the accuracy of any information presented after the date of publication. -
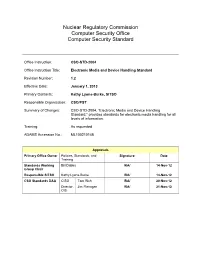
Cso-Std-2004
Nuclear Regulatory Commission Computer Security Office Computer Security Standard Office Instruction: CSO-STD-2004 Office Instruction Title: Electronic Media and Device Handling Standard Revision Number: 1.2 Effective Date: January 1, 2013 Primary Contacts: Kathy Lyons-Burke, SITSO Responsible Organization: CSO/PST Summary of Changes: CSO-STD-2004, “Electronic Media and Device Handling Standard,” provides standards for electronic media handling for all levels of information. Training: As requested ADAMS Accession No.: ML100210148 Approvals Primary Office Owner Policies, Standards, and Signature Date Training Standards Working Bill Dabbs /RA/ 14-Nov-12 Group Chair Responsible SITSO Kathy Lyons-Burke /RA/ 14-Nov-12 CSO Standards DAA CISO Tom Rich /RA/ 20-Nov-12 Director, Jim Flanagan /RA/ 21-Nov-12 OIS CSO Standard CSO-STD-2004 Page i TABLE OF CONTENTS 1 PURPOSE ................................................................................................................ 1 2 GENERAL REQUIREMENTS .................................................................................. 1 3 SPECIFIC REQUIREMENTS ................................................................................... 2 3.1 MEDIA SENSITIVITY LEVEL DETERMINATION ......................................................................................... 2 3.2 MANAGEMENT AND HANDLING OF REMOVABLE ELECTRONIC MEDIA ...................................................... 3 3.3 ENCRYPTED ELECTRONIC MEDIA AND DEVICE HANDLING .................................................................... -

Personal Computer Hardware from Wikipedia, the Free Encyclopedia (Redirected from Computer Hardware)
Personal computer hardware From Wikipedia, the free encyclopedia (Redirected from Computer hardware) Personal computer hardware are component devices which are typically installed into or peripheral to a computer case to create a personal computer upon which system software is installed including a firmware interface such as a BIOS and an operating system which supports application software that performs the operator's desired functions. Operating systems usually communicate with devices through hardware buses by using software device drivers. Contents 1 Motherboard 2 Power supply 3 Removable media devices 4 Secondary storage 5 Sound card Hardware of a modern personal computer 6 Input and output peripherals 1. Monitor 6.1 Input 2. Motherboard 6.2 Output 3. CPU 7 See also 4. RAM 5. Expansion cards 6. Power supply 7. Optical disc drive Motherboard 8. Hard disk drive 9. Keyboard Main article: Motherboard 10. Mouse The motherboard is the main component inside the case. It is a large rectangular board with integrated circuitry that connects the other parts of the computer including the CPU, the RAM, the disk drives (CD, DVD, hard disk, or any others) as well as any peripherals connected via the ports or the expansion slots. Components directly attached to the motherboard include: The central processing unit (CPU) performs most of the calculations which enable a computer to function, and is sometimes referred to as the "brain" of the computer. It is usually cooled by a heat sink and fan. Newer CPUs include an on-die Graphics Processing Unit (GPU). The chip set mediates communication between the CPU and the other components of the system, including main memory.