Future of Defense Task Force Report 2020 Cover Photo Credit: NASA Future of Defense Task Force
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Rns Over the Long Term and Critical to Enabling This Is Continued Investment in Our Technology and People, a Capital Allocation Priority
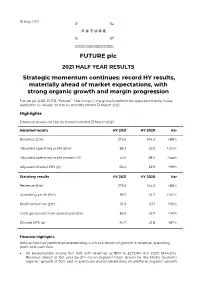
19 May 2021 FUTURE plc 2021 HALF YEAR RESULTS Strategic momentum continues: record HY results, materially ahead of market expectations, with strong organic growth and margin progression Future plc (LSE: FUTR, “Future”, “the Group”), the global platform for specialist media, today publishes its results for the six months ended 31 March 2021. Highlights Financial results for the six months ended 31 March 2021 Adjusted results HY 2021 HY 2020 Var Revenue (£m) 272.6 144.3 +89% Adjusted operating profit (£m)1 89.2 39.9 +124% Adjusted operating profit margin (%) 33% 28% +5ppt Adjusted diluted EPS (p) 65.4 32.9 +99% Statutory results HY 2021 HY 2020 Var Revenue (£m) 272.6 144.3 +89% Operating profit (£m) 59.7 24.7 +142% Profit before tax (£m) 56.9 27.1 +110% Cash generated from operations (£m) 85.9 35.7 +141% Diluted EPS (p) 40.7 21.8 +87% Financial highlights Robust first-half performance extending our track record of growth in revenue, operating profit and cash flow: An exceptionally strong first half, with revenue up 89% to £272.6m (HY 2020: £144.3m). Revenue ahead of last year by 21% on an organic2 basis, driven by the Media division’s organic2 growth of 30% and in particular digital advertising on-platform organic2 growth of 30% and eCommerce affiliates’ organic2 growth of 56%. US achieved revenue growth of 31% on an organic2 basis and UK revenues grew by 5% organically (UK has a higher mix of events and magazines revenues which were impacted more materially by the pandemic). -

(AFDD) 3-13, Information Operations
Cover Sheet for Air Force Doctrine Document (AFDD) 3-13, Information Operations OPR: LeMay Center/DD 28 July 2011 AFDD numbering has changed to correspond with the joint doctrine publication numbering architecture (the AFDD titles remain unchanged until the doctrine is revised). Any AFDD citations within the documents will list the old AFDD numbers until the doctrine is revised. The changed numbers follow: OLD NEW TITLE AFDD 2-1 changed to AFDD 3-1 Air Warfare AFDD 2-1.1 changed to AFDD 3-01 Counterair Operations AFDD 2-1.2 changed to AFDD 3-70 Strategic Attack AFDD 2-1.3 changed to AFDD 3-03 Counterland Operations AFDD 2-1.4 changed to AFDD 3-04 Countersea Operations AFDD 2-1.6 changed to AFDD 3-50 Personnel Recovery Operations AFDD 2-1.7 changed to AFDD 3-52 Airspace Control AFDD 2-1.8 changed to AFDD 3-40 Counter-CBRN AFDD 2-1.9 changed to AFDD 3-60 Targeting AFDD 2-10 changed to AFDD 3-27 Homeland Operations AFDD 2-12 changed to AFDD 3-72 Nuclear Operations AFDD 2-2 changed to AFDD 3-14 Space Operations AFDD 2-2.1 changed to AFDD 3-14.1 Counterspace Operations AFDD 2-3 changed to AFDD 3-24 Irregular Warfare AFDD 2-3.1 changed to AFDD 3-22 Foreign Internal Defense AFDD 2-4 changed to AFDD 4-0 Combat Support AFDD 2-4.1 changed to AFDD 3-10 Force Protection AFDD 2-4.2 changed to AFDD 4-02 Health Services AFDD 2-4.4 changed to AFDD 4-11 Bases, Infrastructure, and Facilities [Rescinded] AFDD 2-4.5 changed to AFDD 1-04 Legal Support AFDD 2-5 changed to AFDD 3-13 Information Operations AFDD 2-5.1 changed to AFDD 3-13.1 Electronic Warfare AFDD 2-5.3 changed to AFDD 3-61 Public Affairs Operations AFDD 2-6 changed to AFDD 3-17 Air Mobility Operations AFDD 2-7 changed to AFDD 3-05 Special Operations AFDD 2-8 changed to AFDD 6-0 Command and Control AFDD 2-9 changed to AFDD 2-0 ISR Operations AFDD 2-9.1 changed to AFDD 3-59 Weather Operations INFORMATION OPERATIONS Air Force Doctrine Document 3-13 11 January 2005 Incorporating Change 1, 28 July 2011 This document complements related discussion found in Joint Publication 3-13, Joint Doctrine for Information Operations. -

Toward an Enhanced Strategic Policy in the Philippines
Toward an Enhanced Strategic Policy in the Philippines EDITED BY ARIES A. ARUGAY HERMAN JOSEPH S. KRAFT PUBLISHED BY University of the Philippines Center for Integrative and Development Studies Diliman, Quezon City First Printing, 2020 UP CIDS No part of this book may be reprinted or reproduced or utilised in any form or by any electronic, mechanical, or other means, now known or hereafter invented, without written permission from the publishers. Recommended Entry: Towards an enhanced strategic policy in the Philippines / edited by Aries A. Arugay, Herman Joseph S. Kraft. -- Quezon City : University of the Philippines, Center for Integrative Studies,[2020],©2020. pages ; cm ISBN 978-971-742-141-4 1. Philippines -- Economic policy. 2. Philippines -- Foreign economic relations. 2. Philippines -- Foreign policy. 3. International economic relations. 4. National Security -- Philippines. I. Arugay, Aries A. II. Kraft, Herman Joseph S. II. Title. 338.9599 HF1599 P020200166 Editors: Aries A. Arugay and Herman Joseph S. Kraft Copy Editors: Alexander F. Villafania and Edelynne Mae R. Escartin Layout and Cover design: Ericson Caguete Printed in the Philippines UP CIDS has no responsibility for the persistence or accuracy of urls for external or third-party internet websites referred to in this publication, and does not guarantee that any content on such websites is, or will remain, accurate or appropriate. TABLE OF CONTENTS Acknowledgements ______________________________________ i Foreword Stefan Jost ____________________________________________ iii Teresa S. Encarnacion Tadem _____________________________v List of Abbreviations ___________________________________ ix About the Contributors ________________________________ xiii Introduction The Strategic Outlook of the Philippines: “Situation Normal, Still Muddling Through” Herman Joseph S. Kraft __________________________________1 Maritime Security The South China Sea and East China Sea Disputes: Juxtapositions and Implications for the Philippines Jaime B. -

The Chief Management Officer of the Department of Defense: an Assessment
DEFENSE BUSINESS BOARD Submitted to the Secretary of Defense The Chief Management Officer of the Department of Defense: An Assessment DBB FY 20-01 An assessment of the effectiveness, responsibilities, and authorities of the Chief Management Officer of the Department of Defense as required by §904 of the FY20 NDAA June 1, 2020 DBB FY20-01 CMO Assessment 1 Executive Summary Tasking and Task Force: The Fiscal Year (FY) 2020 National Defense Authorization Act (NDAA) (Public Law (Pub. L. 116-92) required the Secretary of Defense (SD) to conduct an independent assessment of the Chief Management Officer (CMO) with six specific areas to be evaluated. The Defense Business Board (DBB) was selected on February 3, 2020 to conduct the independent assessment, with Arnold Punaro and Atul Vashistha assigned to co-chair the effort. Two additional DBB board members comprised the task force: David Walker and David Van Slyke. These individuals more than meet the independence and competencies required by the NDAA. Approach: The DBB task force focused on the CMO office and the Department of Defense (DoD) business transformation activities since 2008 when the office was first established by the Congress as the Deputy Chief Management Officer (DCMO), and in 2018 when the Congress increased its statutory authority and elevated it to Executive Level (EX) II and the third ranking official in DoD. The taskforce reviewed all previous studies of DoD management and organizations going back twenty years and completed over ninety interviews, including current and former DoD, public and private sector leaders. The assessments of CMO effectiveness since 2008 are focused on the performance of the CMO as an organizational entity, and is not an appraisal of any administration or appointee. -

Team 4: Influencing Insurgent SVBIED
Team 4: Influencing Insurgent SVBIED Operations Using Traffic Control Points Enhanced with Unmanned Aerial System (UAS) Employment Strategies TEAM 4 MEMBERS The goal of the IDFW 15 effort was to determine the value of adding Unmanned Aerial Systems (UAS) to the Edward Teague aforementioned environment. Specifically, we looked to US Military Academy at West Point, US derive insights about semi-autonomous UAS with swarm Niki Goerger behaviors. Engineer Research and Development Center, US US Military Academy at West Point, US This extension can assist counterinsurgent forces in several ways. It will drive needs for UAS allocation and Brad Young Naval Post Graduate School, US development by identifying critical elements of semi- autonomous swarming behavior. In addition, it may Ng Chu Ngah highlight mission behavior that shows the most promise by Quek Kwang Ti Defence Science and Technology Agency, expanding the tasks and environment beyond this current Republic of Singapore set. Due to the complex nature of the problem, the current state of understanding in the field, and the exploratory nature INTRODUCTION of the research, insights vice specific answers are central in this research. Insurgents have effectively employed asymmetric tactics, such as the use of suicide bombers, as viable threats in urban PROBLEM STATEMENT environments. These threats are often devastating in their physical and emotional effects. They are hard to detect and This study addresses whether we can isolate factors needed have proven difficult to thwart or defeat. The U.S. Army has to identify effective semiautonomous UAS behaviors that recognized that improvised Explosive Devices (IEDs) pose a add value to the aforementioned SVBIED TCP study. -

Tell Me How This Ends Military Advice, Strategic Goals, and the “Forever War” in Afghanistan
JULY 2019 Tell Me How This Ends Military Advice, Strategic Goals, and the “Forever War” in Afghanistan AUTHOR Mark F. Cancian A Report of the CSIS INTERNATIONAL SECURITY PROGRAM JULY 2019 Tell Me How This Ends Military Advice, Strategic Goals, and the “Forever War” in Afghanistan AUTHOR Mark F. Cancian A Report of the CSIS International Security Program Lanham • Boulder • New York • London About CSIS Established in Washington, D.C., over 50 years ago, the Center for Strategic and International Studies (CSIS) is a bipartisan, nonprofit policy research organization dedicated to providing strategic in sights and policy solutions to help decisionmakers chart a course toward a better world. In late 2015, Thomas J. Pritzker was named chairman of the CSIS Board of Trustees. Mr. Pritzker succeeded former U.S. senator Sam Nunn (D-GA), who chaired the CSIS Board of Trustees from 1999 to 2015. CSIS is led by John J. Hamre, who has served as president and chief executive officer since 2000. Founded in 1962 by David M. Abshire and Admiral Arleigh Burke, CSIS is one of the world’s preeminent international policy in stitutions focused on defense and security; regional study; and transnational challenges ranging from energy and trade to global development and economic integration. For eight consecutive years, CSIS has been named the world’s number one think tank for defense and national security by the University of Pennsylvania’s “Go To Think Tank Index.” The Center’s over 220 full-time staff and large network of affiliated scholars conduct research and analysis and develop policy initiatives that look to the future and anticipate change. -

Drone Swarms As Networked Control Systems by Integration of Networking and Computing
sensors Review Drone Swarms as Networked Control Systems by Integration of Networking and Computing Godwin Asaamoning 1,2,* , Paulo Mendes 3,4 , Denis Rosário 5 and Eduardo Cerqueira 5 1 COPELABS, Universidade Lusofóna, 1749-024 Lisbon, Portugal 2 Bolgatanga Technical University, Sumbrungu UB-0964-8505, Ghana 3 School of Communication, Architecture, Arts and Information Technologies, Universidade Lusofóna, 1749-024 Lisbon, Portugal; [email protected] 4 Airbus Central Research and Technology, Willy-Messerschmitt-Str 1, Taufkirchen, 82024 Munich, Germany 5 Computer Science Faculty, Federal University of Pará, Belém 66075-110, Brazil; [email protected] (D.R.); [email protected] (E.C.) * Correspondence: [email protected] Abstract: The study of multi-agent systems such as drone swarms has been intensified due to their cooperative behavior. Nonetheless, automating the control of a swarm is challenging as each drone operates under fluctuating wireless, networking and environment constraints. To tackle these challenges, we consider drone swarms as Networked Control Systems (NCS), where the control of the overall system is done enclosed within a wireless communication network. This is based on a tight interconnection between the networking and computational systems, aiming to efficiently support the basic control functionality, namely data collection and exchanging, decision-making, and the distribution of actuation commands. Based on a literature analysis, we do not find revision papers about design of drone swarms as NCS. In this review, we introduce an overview of how to develop self-organized drone swarms as NCS via the integration of a networking system and a Citation: Asaamoning, G.; Mendes, computational system. In this sense, we describe the properties of the proposed components of a P.; Rosário, D.; Cerqueira, E. -

DEPARTMENT of DEFENSE Office of the Secretary, the Pentagon, Washington, DC 20301–1155 Phone, 703–545–6700
DEPARTMENT OF DEFENSE Office of the Secretary, The Pentagon, Washington, DC 20301–1155 Phone, 703–545–6700. Internet, www.defenselink.mil. SECRETARY OF DEFENSE ROBERT M. GATES DEPUTY SECRETARY OF DEFENSE WILLIAM LYNN III Under Secretary of Defense for Acquisition, ASHTON B. CARTER Technology, and Logistics Deputy Under Secretary of Defense (Business PAUL A. BRINKLEY Transformation) Deputy Under Secretary of Defense LOUIS W. ARNY III (Installations and Environment) Under Secretary of Defense for Policy MICHELE FLOURNOY Principal Deputy Under Secretary of Defense JAMES N. MILLER, JR. for Policy Assistant Secretary of Defense (International ALEXANDER R. VERSHBOW Security Affairs) Assistant Secretary of Defense (Special MICHAEL VICKERS Operations and Low-Intensity Conflict) Assistant Secretary of Defense (Homeland (VACANCY) Defense and America’s Security) Assistant Secretary of Defense (Global Strategic JOSEPH BENKERT Affairs Assistant Secretary of Defense (Asian and (VACANCY) Pacific Security Affairs) Deputy Assistant Secretary of Defense (Plans) JANINE DAVIDSON Deputy Under Secretary of Defense (VACANCY) (Technology Security Policy/Counter Proliferation) Deputy Under Secretary of Defense (Strategy, KATHLEEN HICKS Plans and Forces) Deputy Under Secretary of Defense (Policy PETER VERGA Integration and Chief of Staff) Principal Deputy Under Secretary of Defense WILLIAM J. CARR, Acting for Personnel and Readiness Assistant Secretary of Defense (Reserve Affairs) DAVID L. MCGINNIS, Acting Deputy Assistant Secretary of Defense (Reserve JENNIFER C. BUCK Affairs) Deputy Under Secretary of Defense (Program JEANNE FITES Integration) Deputy Under Secretary of Defense (Readiness) SAMUEL D. KLEINMAN Deputy Under Secretary of Defense (Military WILLIAM J. CARR Personnel Policy) Deputy Under Secretary of Defense (Military ARTHUR J. MYERS, Acting Community and Family Policy) Deputy Under Secretary of Defense (Plans) GAIL H. -

JP 3-33, Joint Task Force Headquarters
Joint Publication 3-33 Joint Task Force Headquarters 30 July 2012 PREFACE 1. Scope This publication provides joint doctrine for the formation and employment of a joint task force (JTF) headquarters to command and control joint operations. It provides guidance on the JTF headquarters’ role in planning, preparing, executing, and assessing JTF operations. 2. Purpose This publication has been prepared under the direction of the Chairman of the Joint Chiefs of Staff. It sets forth joint doctrine to govern the activities and performance of the Armed Forces of the United States in joint operations and provides the doctrinal basis for US military coordination with other US Government departments and agencies during operations and for US military involvement in multinational operations. It provides military guidance for the exercise of authority by combatant commanders and other joint force commanders (JFCs) and prescribes joint doctrine for operations, education, and training. It provides military guidance for use by the Armed Forces in preparing their appropriate plans. It is not the intent of this publication to restrict the authority of the JFC from organizing the force and executing the mission in a manner the JFC deems most appropriate to ensure unity of effort in the accomplishment of the overall objective. 3. Application a. Joint doctrine established in this publication applies to the Joint Staff, commanders of combatant commands, subunified commands, joint task forces, subordinate components of these commands, the Services, and combat support agencies. b. The guidance in this publication is authoritative; as such, this doctrine will be followed except when, in the judgment of the commander, exceptional circumstances dictate otherwise. -

Deploying Federal Civilians to the Battlefield: Incentives, Benefits, and Medical Care
Deploying Federal Civilians to the Battlefield: Incentives, Benefits, and Medical Care U.S. HOUSE OF REPRESENTATIVES • COMMITTEE ON ARMED SERVICES Subcommittee on Oversight & Investigations April 2008 HASC Committee Print No. 9 41-410 On the cover: The Defense of Freedom medal, created after the September 11th attacks, acknowledges civilian employees of the Department of Defense and other civilians in service to the Department of Defense who are killed or injured while on duty. It is the civilian equivalent to the Purple Heart. DEPLOYING FEDERAL CIVILIANS TO THE BATTLEFIELD: Incentives, Benefits, and Medical Care HASC OVERSIGHT & INVESTIGATIONS STAFF LORRY M. FENNER, STAFF LEAD STEVE J. DETERESA, PROJECT LEAD THOMAS HAWLEY ANDREW HYDE JOHN E. KRUSE GREGORY A. MARCHAND MICHAEL MCERLEAN SUZANNE MCKENNA MARK PARKER SASHA ROGERS ROGER I. ZAKHEIM DEPLOYING FEDERAL CIVILIANS TO THE BATTLEFIELD 3 ACKNOWLEDGEMENTS We want to thank our fellow subcommittee members and the subcommittee staff. We would also like to thank Chairman Skelton and Ranking Member Hunter, and staff members, Erin Conaton, Bob DeGrasse, Robert Simmons, Paul Oostburg Sanz, Paul Arcangeli, Cathy Garman, Debra Wada, Michael Higgins, David Kildee, Loren Dealy, Lara Battles, Christine Lamb, Josh Holly, Linda Burnette, Nancy Warner, Rebecca Ross, Cyndi Howard, and Derek Scott. Finally, we want to thank our own military legislative assistants (MLAs) and fellows, Dan Madden, James Lively, Justin Johnson, and Caryll Rice, as well as the rest of the subcommittee MLAs for all their assistance on this study. We also want to thank those outside the committee who assisted in this effort, including those from the Office of the Secretary of Defense, the Office of the Under Secretary of Defense for Personnel and Readiness, the Joint Staff, the military services, the Department of State, the U.S. -

Defense 2020 “Covid-19 and the U.S. Military”
Center for Strategic and International Studies TRANSCRIPT Defense 2020 “Covid-19 and the U.S. Military” RECORDING DATE Wednesday, April 1, 2020 GUESTS Steve Morrison Senior Vice President, and Director, Global Health Policy Center, CSIS Mark Cancian Senior Advisor, International Security Program, CSIS Christine Wormuth Director, International Security and Defense Policy Center, RAND Corporation Christine Wormuth Director, International Security and Defense Policy Center, RAND Corporation HOST Rear Admiral (Ret.) Tom Cullison Former Deputy Surgeon General of the U.S. Navy, and Adjunct Fellow, Global Health Policy Center, CSIS Transcript by Rev.com Kathleen Hicks: Hi, I'm Kathleen Hicks, Senior Vice President and Director of the International Security Program at the Center for Strategic and International Studies, and this is Defense 2020 a CSIS podcast examining critical defense issues in the United States is 2020 election cycle. We bring in defense experts from across the political spectrum to survey the debates over the US military strategy, missions and funding. This podcast is made possible by contributions from BAE systems, Lockheed Martin, Northrop Grumman, and the Thales Group. Kathleen Hicks: On this episode of Defense 2020, I hosted discussion with four experts on COVID-19 and the US military. Steve Morrison, Senior Vice President and Director of Global Health Policy at CSIS, Mark Cancian, Senior Advisor in the International Security Program at CSIS, Christine Wormuth, Director of the International Security and Defense Policy Center at the RAND Corporation and Rear Admiral (Ret.), Tom Cullison Former Deputy Surgeon General of the US Navy and an Adjunct Fellow in the Global Health Policy Center at CSIS. -

Battlefields and Boardrooms: Women's Leadership in the Military and Private Sector
Battlefields and Boardrooms JANUARY 2015 Women’s Leadership in the Military and the Private Sector By Nora Bensahel, David Barno, Katherine Kidder, and Kelley Sayler Acknowledgements The authors would like to thank the many people who contributed their time and energy to help bring this report to publication. We would like to thank our CNAS colleagues senior fellow Phil Carter and research intern Sam Arras for their important contributions throughout the development of the report. We thank Dafna Rand for managing this report’s publication and for her substantive editorial comments. We thank all of our other CNAS colleagues who provided valuable feedback on draft versions of the report. Outside of CNAS, we thank Lewis Runnion and Bank of America for their gener- ous support for this project. We thank the organizers and sponsors of the Cornell University Women Veterans Roundtable, the U.S. armed forces, and several Fortune 500 companies for generously sharing their expertise, insights, and people for interviews. We particularly thank the current and former executive level women leaders we interviewed for this report. We also thank the dozens of dedicated professionals from the U.S. Army, Navy, Air Force, and Marines, active and retired, who shared their insights and perspectives. We offer a special thanks to Liz Fontaine for her creative layout design. The authors alone are responsible for any error of fact, analysis, or omission. Cover Image U.S. Army Spc. Rebecca Buck, a medic from Headquarters and Headquarters Company, 1st Battalion, 14th Infantry Regiment, 2nd Stryker Brigade Combat Team, 25th Infantry Division, provides perimeter security outside an Iraqi police station in the Tarmiya Province of Iraq, March 30, 2008.