Vol. 44 No. 4 [2018]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rothberger's Final Chapter Brings
To print, your print settings should be ‘fit to page size’ or ‘fit to printable area’ or similar. Problems? See our guide: https://atg.news/2zaGmwp ISSUE 2472 | antiquestradegazette.com | 19 December 2020 | UK £4.99 | USA $7.95 | Europe €5.50 koopman rare art antiques trade KOOPMAN (see Client Templates for issue versions) THE ART M ARKET WEEKLY [email protected] +44 (0)20 7242 7624 www.koopman.art Book trade on alert after smash Rothberger’s final and grab thefts chapter brings £1m by Laura Chesters A spate of thefts from central London shops has put the antiquarian book Pick Left: a large trade on high alert. Vienna porcelain Three dealers have been targeted. The of the model of an latest break-in took place at around 2am on week elephant from December 4 at Altea Gallery on Saint the Rothberger George Street when 48 antique maps were collection – stolen with a retail value well in excess of £97,000 at £100,000. Bonhams. Altea Gallery’s director Massimo De Martini said: “This was a typical smash and Below: Heinrich grab – they were in and out within 90 Rothberger and seconds. They were captured on the CCTV his niece Bertha but they were fully masked so you cannot Gutmann. see faces.” Well rehearsed “The thieves were very well rehearsed – it was smooth and quick. I think it is a strange thing to target me. We see this sort of thing in jewellery but not antique maps. “I have been here 20 years and, of course, we may get fraudulent purchases or shoplifting, but not this brutal forced entry.” In September, a similar theft took place at fellow rare book and map dealer Robert Frew in South Kensington when around 15 items were taken. -
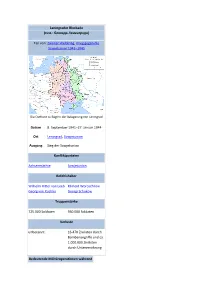
Leningrader Blockade (Russ.: Блокада Ленинграда) Teil
Leningrader Blockade (russ.: блокада Ленинграда) Teil von: Zweiter Weltkrieg, Krieg gegen die Sowjetunion 1941–1945 Die Ostfront zu Beginn der Belagerung von Leningrad Datum 8. September 1941–27. Januar 1944 Ort Leningrad, Sowjetunion Ausgang Sieg der Sowjetunion Konfliktparteien Achsenmächte Sowjetunion Befehlshaber Wilhelm Ritter von Leeb Kliment Woroschilow Georg von Küchler Georgi Schukow Truppenstärke 725.000 Soldaten 930.000 Soldaten Verluste unbekannt 16.470 Zivilisten durch Bombenangriffe und ca. 1.000.000 Zivilisten durch Unterernährung Bedeutende Militäroperationen während des Deutsch-Sowjetischen Krieges 1941: Białystok-Minsk – Dubno-Luzk- Riwne – Smolensk – Uman – Kiew – Odessa – Leningrader Blockade – Rostow – Wjasma-Brjansk – Moskau 1942: Charkow – Operation Blau – Operation Braunschweig – Operation Edelweiß – Stalingrad – Operation Mars 1943: Woronesch-Charkow – Operation Iskra – Nordkaukasus – Charkow – Unternehmen Zitadelle – Smolensk – Dnepr 1944: Dnepr-Karpaten-Operation – Leningrad-Nowgorod – Krim – Wyborg– Petrosawodsk – Weißrussland – Lwiw- Sandomierz – Iaşi–Chişinău – Belgrad – Petsamo-Kirkenes – Baltikum – Karpaten – Budapest 1945: Weichsel-Oder – Ostpreußen – Westkarpaten – Ostpommern – Plattensee – Oberschlesien – Wien – Berlin – Prag Als Leningrader Blockade (russisch: блокада Ленинграда) bezeichnet man die Belagerung Leningrads durch die deutsche Heeresgruppe Nord und finnische Truppen während des Zweiten Weltkrieges. Sie dauerte vom 8. September 1941 bis zum 27. Januar 1944. Schätzungen gehen von etwa 1,1 -

Dispatches Paid Bakersfield Ca Permit No 66 from Decision Games #28 SPRING 2015
PRESRT STD US POSTAGE DISPATCHES PAID BAKERSFIELD CA PERMIT NO 66 FROM DECISION GAMES #28 SPRING 2015 (661) 587-9633 | (661) 587-5031 fax | P.O. Box 21598 | Bakersfield CA 93390 | DECISIONGAMES.COM SAMPLE FROM STRATEGY & TACTICS #292 Waterloo by Christopher Perello aterloo is the most written about battle in human history, and for good reason. It had every conceivable dramatic W element: the fate of Europe in the balance, a duel between two of the greatest commanders of their time, indeed of all time, sweeping cavalry charges, a last-minute rescue, the final attack of one of the most storied corps in history, and a near victory turned into total rout. Such was the scope of that outcome the name has become synonymous with absolute, crushing, irretrievable defeat. It also cemented the Napoleonic paradigm—that of a decisive, war-ending battle—into the minds of military men around the world for generations to come. Situation Napoleon Bonaparte’s eleven month exile on Elba ended in March 1815 with his return to France. The French people welcomed him, but cautiously. They wanted no more wars, and Napoleon duly (and probably duplicitously) pledged peace to the French and all of Europe. His former opponents, then bickering in Vienna over the future of Europe, would have none of it. They formed the Seventh Coalition and put their Félix Philippoteaux’s classic painting of a French cavalry charge at Waterloo gives a good feel for the dense formations and the proximity of opposing soldiers. It is inaccurate on armies on a war footing; by early spring 800,000 men were under arms. -

Bee Round 3 – MIDDLE SCHOOL
IHBB Canadian Championships 2018 Bee Round 3 – MIDDLE SCHOOL Bee Round 3 – MIDDLE SCHOOL Regulation Questions (1) At this man's libel trial for accusing politicians of corruption in his newspaper, he gave a 6-hour speech in his own defence and the jury disregarded the judge's instructions and acquitted him. This man's advocacy made his colony the first to gain responsible government in 1848, and he had a provincial rivalry with Charles Tupper. For the point, name this reformist politician and editor of the Nova Scotian newspaper. ANSWER: Joseph Howe (2) This campaign began as a reply to Segesta’s request for aid, and it was doomed by the arrival of Gylippus’ reinforcements. This campaign received its first setback when the vandalization of the religious hermai statues was falsely blamed on commander Alcibiades [al-kih-bee-ah-deez], prompting him to defect to Sparta. For the point, name this disastrous Peloponnesian War expedition in which Athens attacked an Italian island. ANSWER: Sicilian Expedition (accept descriptions of Athens’ expedition to Sicily) (3) This politician names an informal rule that psychiatrists will not speak about politicians’ mental health without analyzing them in person. This politician published The Conscience of a Conservative in 1960, four years before his slogan “in your heart, you know he’s right” was mocked by his opponent’s slogan “in your guts, you know he’s nuts.” For the point, name this Arizona senator who lost the 1964 Presidential election to Lyndon Johnson. ANSWER: Barry Goldwater (4) A book by this man recounts how he heard the command “take up and read” while meditating in a garden and how he needlessly stole some pears from a neighboring orchard in his youth. -
Combat and Genocide on the Eastern Front: the German Infantry’S War, 1941–1944 Jeff Rutherford Index More Information
Cambridge University Press 978-1-107-05571-1 - Combat and Genocide on the Eastern Front: The German Infantry’s War, 1941–1944 Jeff Rutherford Index More information Index Aachen, 50 Brecht, Bertolt, 47 Adenauer, Konrad, 50 Breslau, 322 Adriatic Sea, 39 British Bomber Command, 347, 351 Allied strategic bombing, 347–8 Bucher, Wolfgang, 179 Alsace, 323 Busch, Ernst, 61, 78, 95, 99, 120, Amsterdam, 168 123, 198 antiguerilla policies. See anti-partisan warfare Athens, 168 Catholic Workers’ Union, 53 Austro-Hungarian Empire, 40 Caucasus, 8, 100, 250, 283 Center Party, 43, 53–5, 387 Backe, Herbert, 71–2, 174 Chemnitz, 203 Baden, 205 Christian Union, 53 Balkans, 56, 66, 203 Chudovo, 327, 374 Baltic region. See Baltic states collective measures, 17, 19, 88, 130–4, 163, Baltic Sea, 39, 359 167, 214–15 Baltic states, 6, 16, 57–61, 96, 98, 101, 106, Cologne, 50, 349 132, 135, 345, 357, 370, 373–4, Commissar Order, 13, 75, 78, 212, 254 381, 384. See also Estonia, Crimea, 8, 166, 170, 194, 249, 267 Latvia, Lithuania “Customs of War on Land,” 18 Bartenstein, 76 Battle of Berlin, 351 Demiansk, 7, 121, 126, 207, 217, 219–22, Battle of Britain, 56 224, 229, 234, 248, 256–71, Bauhaus school, 47 275, 278, 280–1, 287, 297–8, Belarus, 58, 132, 156, 171, 194, 336, 374 301, 303, 306, 308–10, 313–17, Belgium, 19, 56, 94, 378 320, 330, 339, 341, 375, 380–1 Belgrade, 168 withdrawal from, 306 Berlin, 5, 31–2, 40, 42, 45–50, 54–6, 68, Denmark, 56 70, 168, 205, 299, 308, 309, Dnieper river, 359 348, 351, 386–7 Dno, 308 Berlin-Brandenburg, 5, 32, 51, 55, 207, DNVP. -

Transformation Through Training II/2014
TABLE OF CONTENTS 4 The JFTC Going Strong as It Celebrates Its 10th Birthday 10 Different logics Underpinning the COPD Some Useful Foundations To Advice 4 The “TA” During Phase II 16 JFTC Hosts JFC Brunssum Trident Joust 14 Exercise 18 Interview with COM JFC Brunssum 20 Counter-Terrorism Policies 18 10 & the Cost to the West Part II - Gunpowder, Treason & Plot 29 2015 CWIX Is Promising to Be the Biggest Yet 31 CAX Forum 32 Life at the JFTC 32 2014 in Retrospect 29 2 • Transformation Through Training • Issue No: 6 • December 2014 „Transformation Through Training“ The aim of this magazine is to provide a forum for Publishing Institution: exchange of information and expertise among train- Joint Force Training Centre Bydgoszcz (JFTC) ing and educational institutions across NATO in the area of training, military professional education, and Managing director: related technological support. In the context of The Brigadier General László SZABÓ, NATO “Smart Defense” approach, there is grow- JFTC Deputy Commander / Chief of Staff ing importance for cooperation with partner states and international organizations, such as the United Chief Editor: Nations, the European Union, the Organization for MAJ Goran Pijetlovic, JFTC Public Affairs Officer Security and Cooperation in Europe and others. With the above in mind, the JFTC invites authors from Editorial Board: countries and institutions beyond the NATO envi- Mrs. Kamila SIERZPUTOWSKA, PhD, Kazimierz Wielki ronment, to publish in the Transformation Through University, Poland Training magazine. The magazine will focus on the BG Ing. Jaromír ZŮNA, MSc., PhD, Director of the Logistics best practices in the areas of command and staff train- Agency, Army of the Czech Republic ing, professional military education, simulations and simulation technologies, distributed training, military Advisory Committee: training development as well as other related areas. -

The Letters of Holocaust Victims Leave a Lasting Legacy
Why Do We Study History, If Not to Make a Better Future? Rebecca Lim Georgetown University, Class of 2011 NEW YORK – Why do we study history, if not to make a better future? That was the thought that filled my mind as the documentary ―A Film Unfinished‖ came to an end and the shades over the windows in the auditorium rolled up to reveal a magnificent sunset. The documentary, about the Nazi effort to make a propaganda film about the Warsaw Ghetto, was probably one of the most intense I’d ever seen, along with The Conscience of Nhem En (about a photographer who documented the Khmer Rouge genocide in Cambodia). It was the end of the first day on the FASPE journalism program and we had spent the day in discussions and seminars on the role of the press during the Holocaust and covering conflict. We had also been taken on a tour of the Jewish Heritage Museum in New York by a Holocaust survivor from Poland. We were warned that the film was hard to watch, but even then, there was a cloud of silence hanging over the room for a few minutes when it ended. I’m hardly ever at a loss for words, but in that moment, I was only able to come to terms with the horrific images I had just seen, by capturing images myself. I grabbed my camera and shot the sunset through the window. Being behind the lens made me feel safe again, even as the questions and thoughts were racing through my head about the people who shot that film in the ghetto, of the dead and dying, and the one man who recounted the process in an interview years later. -

British Land Mines and Firing Devices
BRITISH LAND MINES AND FIRING DEVICES I FEBRUARY 1945 © Nordavind eeNRDEffflAL RESTRICTED SECTION I BRITISH ANTI-TANK MINES a FUZES - 1 - RESTRICTED A/TK. MINE G.S.MK. II BRASS SLEEVE HEAD ___PLUNGER STRIKER SPRING LO C K IN G BALLS BRASS SAFETY SLEEVE STRIKER PERCUSSION CAP DETONATOR 2 assaB icgta____________________________________________ DIAMETER .......................... 7 -1 /2 in . BRITISH MIHE HEIGHT .......................... 3 -1 /4 in . TOTAL WEIGHT.................3 -1 /2 lb s . EXPLOSIVE WEIGHT . 4 lo s . EXPLOSIVE......................T.1J.T. or Earatol MATERIAL..........................S tool COLOR . ..................... Sides and top dark greon; G.S. MK.II bottom yollow, with cross (AHTI-TAl.X) of rod and groon. PUZS ..........................Ml no, con ta ct, a/ t, Ho. 1 Xk I I . PRESSURE REQUIRED. Approximately 350 lb s . (OBSOLETE) USE: Defense against armorod cars, tanks, or other vohlcl03. The nine will break tracks of light and modlura tanks and dlsablo other vohlcles. COMPOHEHTS: The O.S. Kk II Mino has threo sain components: loadod body, coyer, and fu z e . The mine covor f i t s ovor the body and is kept cloar of it by a loaf spring. Pins on tho 3ldes of the nino body ongage bayonet sockets in tho covor. The covor o f th is mine must never be renovod a fto r tho mine 13 armed. Words to that e ffe c t aro stamped on tho cover o f tho nino. (a) Mino Body: Tho mine body is cylindrical in shapo. Passing through tho contor of tho mino 13 a cavity fo r tho ln sortlon o f tho nine fu zo. -

Dispatches Paid Bakersfield Ca Permit No 66 from Decision Games #26 Spring 2014
PRESRT STD US POSTAGE DISPATCHES PAID BAKERSFIELD CA PERMIT NO 66 FROM DECISION GAMES #26 Spring 2014 (661) 587-9633 | (661) 587-5031 fax | P.O. Box 21598 | Bakersfield CA 93390 | decisiongames.com The Dragon: Chinese Special Forces By Terence Co Since soon after its founding on 1 August 1927, during the Nanchang uprising, the People’s Liberation Army (PLA) has conducted stealthy operations, even though it originated as a conventional military force organized from rebelling Kuomintang (KMT) National Revolutionary Army (NRA) units. From 1928 to 1945 the PLA had to adopt guerrilla strategies and tactics in order to survive attacks from the KMT as well as regional warlords and the Japanese. The “people’s war” concept pioneered by the PLA during that time emphasized a multi-stage insurgency strategy. Tactics included blending in with the populace, propaganda, infiltration, the creation of base areas behind enemy lines, sabotage, and attacking enemy rear-area military and economic targets. All those are the hallmarks of what are considered “special operations” by Western militaries. Even so, prior to 1949 the PLA had few units that could be considered special operations forces (SOF) by those same Western militaries. Rather, a multitude of regular and irregular units were trained to perform those missions. Dispatch #26 | DECISION GAMES 1 ❖ #11 | GREEK CIVIL WAR ISSUE MONTH FEATURE ARTICLES #286 | SPARTA VS. ATHENS 12 JUL 2014 Dragon vs. Bear: Possibilities for Chinese versus Russian operational confl ict with a look at both countries’ armed forces. ISSUE MONTH FEATURE ARTICLES • Chinese Special Forces • Operation Able Archer 287 JUL 2014 The Goeben: the story of the German cruiser that fought its way across • Air Ambush over Vietnam • War in Mali the Mediterranean in 1914-15. -

Built to Resist an Assessment of the Special Operations Executive’S Infrastructure in the United Kingdom During the Second World War, 1940-1946
Built to Resist An Assessment of the Special Operations Executive’s Infrastructure in the United Kingdom during the Second World War, 1940-1946 Derwin Gregory MA (cantab) MA PCIfA VOLUME I A thesis submitted in fulfilment of the requirements for the degree of Doctor of Philosophy in the School of History UNIVERSITY OF EAST ANGLIA 2015 This copy of the thesis has been supplied on condition that anyone who consults it is understood to recognise that its copyright rests with the author and that use of any information derived there from must be in accordance with current UK Copyright Law. In addition, any quotation or extract must include full attribution. Declaration I hereby declare that this thesis has not been and will not be submitted in whole or in part to any other University for the award of any other degree. Derwin Gregory i Abstract During the Second World War, the British Government established the Special Operations Executive (SOE) for the purpose of coordinating ‘all action, by way of subversion and sabotage, against the enemy overseas’. Although the overseas operations of this branch of the British Secret Services are relatively well known, no previous study has assessed the organisation’s UK based infrastructure. This thesis represents the first time the entire UK property portfolio of a clandestine government agency has been assessed. By addressing this gap in our knowledge, this thesis has increased the number of identified properties operated by SOE by 30%. This was achieved by undertaking a desk based assessment which combined pre-existing historical and archaeological methodologies. -

Master Europa Catalog
Master Europa Catalog Distributed By: Tom Johnson Games Tom Johnson 3704 West Country Club Lane Altoona, WI 54720 USA Revised: July 29, 2009 GAME MODULES MASTER EUROPA is a complete set of rules and charts replacing those in the GRD Games series Europa™. You must have the maps and counters provided with these games. MASTER EUROPA rules and charts bring the game into line with historical norms (movement, and combat results) while simplifying play in many areas. A. MASTER EUROPA Eastern Front This module covers the games "Fire in the East", "Scorched Earth", & "Urals". It contains 8 new counters for use with the logistics system. Catalog MOD-101 - $22.00 Western Invasion This module covers the game "Second Front". It contains 143 new counters for use with the logistics system. Catalog MOD-102 - $22.00 Western Front Blitzkrieg - This module covers the games "Fall of France" & "Their Finest Hour". It contains 19 new counters for use with the logistics system, 3 for the German OOB, and 49 for use with the naval system . It also includes Orders Of Battle (OOB) that allow a scenario showing the Western Front from Sept. 1939 on to be explored. Catalog MOD-103 - $22.00 Southern Front This module covers the game "War in the Desert" (Or the older "Torch"), "Western Desert". And "Near East" games. It contains 122 new counters for use with the logistics system. Catalog MOD-104 - $22.00 Southeastern Front This module covers the game "Balkan Front". It contains 47 new counters for use with the logistics system and 1 each for the German and Italian OOB. -

60137NCJRS.Pdf
If you have issues viewing or accessing this file contact us at NCJRS.gov. .' ) Instructor Text DEPARTMENT OF THE TREASURY Bureau of Alcohol, Tobacco & Firearms /I. f l Modular ISxplosives Training Program Introduction to Explosives I :c:: ATF P 4510.1 (12/76) replaces ATF Training 5145-12 To be used in conjunction with modules 1, 2 & 3 of Instructor Guide • INTRODUCT'ION TO EXPLOSIVES ',' 02 c. R. NEWHO USER .. CONTENTS Section Topic Page ONE EXPLOSIONS ............................•............. 3 TYPES OF EXPLOSIONS ......... • . .. 3 Mechanical Explosion Chemical Explosion At0":lic Explosion NATURE OF CHEMICAL EXPLOSIONS 4 Ordinary Combustion Explosion Detonation EFFECTS OF AN EXPLOSION 5 Blast Pressure Effect Fragmentation Effect I ncendiary Thermal Effect TWO EXPLOSIVES .... : . • . .. 15 COMPOSITION AND BEHAVIOR OF CHEMICAL EXPL.OSIVES ............................. 15 Explosive Mixtures Explosive Compounds Classification By Velocity Explosive Work EXPLOSIVE TRAINS ................................... 24 Low Explosive Trains High Explosive Trains A PUBLICATION OF The National Bomb Data CenfeE •. Research Division o A program funded by the Law Enforcement Assistance Administra tion of the United States Department of Justice. Dissemination of this document does not constitute U. S. Department of Justice endorsf3- ment or approval of content. Section Topic Page COMMON EXPLOSIVES ................................. 28 • Low Explosives , Primary High Explosives Secondary High Explosive Boosters Secondary High Explosive Main Charges THREE