A Systems Analysis of U.S. Army Operations in Cyberspace By
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Visual Motion Detection Circuit Suggested by Drosophila Connectomics
ARTICLE doi:10.1038/nature12450 A visual motion detection circuit suggested by Drosophila connectomics Shin-ya Takemura1, Arjun Bharioke1, Zhiyuan Lu1,2, Aljoscha Nern1, Shiv Vitaladevuni1, Patricia K. Rivlin1, William T. Katz1, Donald J. Olbris1, Stephen M. Plaza1, Philip Winston1, Ting Zhao1, Jane Anne Horne2, Richard D. Fetter1, Satoko Takemura1, Katerina Blazek1, Lei-Ann Chang1, Omotara Ogundeyi1, Mathew A. Saunders1, Victor Shapiro1, Christopher Sigmund1, Gerald M. Rubin1, Louis K. Scheffer1, Ian A. Meinertzhagen1,2 & Dmitri B. Chklovskii1 Animal behaviour arises from computations in neuronal circuits, but our understanding of these computations has been frustrated by the lack of detailed synaptic connection maps, or connectomes. For example, despite intensive investigations over half a century, the neuronal implementation of local motion detection in the insect visual system remains elusive. Here we develop a semi-automated pipeline using electron microscopy to reconstruct a connectome, containing 379 neurons and 8,637 chemical synaptic contacts, within the Drosophila optic medulla. By matching reconstructed neurons to examples from light microscopy, we assigned neurons to cell types and assembled a connectome of the repeating module of the medulla. Within this module, we identified cell types constituting a motion detection circuit, and showed that the connections onto individual motion-sensitive neurons in this circuit were consistent with their direction selectivity. Our results identify cellular targets for future functional investigations, and demonstrate that connectomes can provide key insights into neuronal computations. Vision in insects has been subject to intense behavioural1,physiological2 neuroanatomy14. Given the time-consuming nature of such recon- and anatomical3 investigations, yet our understanding of its underlying structions, we wanted to determine the smallest medulla volume, neural computations is still far from complete. -

A Pilot Trap Survey of Artificial Reefs in New Jersey for Monitoring of Black Sea Bass, Tautog, and Lobster
Final Report Submitted to the New Jersey Department of Environmental Protection, Division of Fish and Wildlife for the following project: Project Title: A Pilot Trap Survey of Artificial Reefs in New Jersey for Monitoring of Black Sea Bass, Tautog, and Lobster Organization Name: Rutgers, the State University of New Jersey Principal Investigator: Dr. Olaf P. Jensen, Associate Professor, Rutgers University ([email protected], 410-812-4842) Project Co-Investigator: Dr. Douglas Zemeckis, Postdoctoral Researcher, Rutgers University ([email protected], 848-932-3450) NJDEP Project Manager: Peter Clarke, Fisheries Biologist, NJDEP Division of Fish and Wildlife ([email protected]) Performance Period: January 1, 2016 through April 1, 2019 Total Budget: $201,905.00 Table of Contents Introduction……………………………………………………………………………………...1 Project Objectives……………………………………………………………………………….6 Methods………………………………………………………………………………………......8 Study Design: Locations and Times……………………………………………………....8 Protocol: Field and Laboratory Methods…………………………………………………10 2016 Spring Seasonal Monitoring of Artificial Reefs…………………………………….11 2016 Summer Seasonal Monitoring of Artificial Reefs…………………………………..12 2016 Fall Seasonal Monitoring of Artificial Reefs………………………………………13 2017 Spring Seasonal Monitoring of Artificial Reefs…………………………………….14 2017 Summer Seasonal Monitoring of Artificial Reefs……………………………..……15 2017 Fall Seasonal Monitoring of Artificial Reefs………………………………………17 2018 Spring Seasonal Monitoring of Artificial Reefs……………………………………18 2018 Summer Seasonal -

Monday/Tuesday Playoff Schedule
2013 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey1 Hockey2 Hockey3 Hockey4 Hockey5 Ulti A Soccer 3A Soccer 3B Cricket E1 Cricket E2 Cricket N1 Cricket N2 Field X 8:00 9:15 MI13 MI14 TI13 TI14 TI15 TI16 MI1 MI2 MI3 MI4 MI15 MI16 9:20 10:35 MI17 MI18 TI17 TI18 TI19 TI20 MI5 MI6 10:40 11:55 MI19 MI20 MC1 MC2 MC3 MI21 MI7 MI8 12:00 1:15 MI9* TI21* TI22 TI23 TI24 MI10 MI11 MI12 1:20 2:35 MI22 MC4 MC6 MC5 MI23 TC1 MI24 MI25 2:40 3:55 TI1 TI2 MC7 TI3 MI26 TC2 TR1 TR2 MI27 4:00 5:15 MC8* TC3 MC10 MC9 TI4 TC4 TR3 TR4 5:20 6:35 TC5* TI5 TI6 TI7 TI8 TC6 TR5 TR6 6:40 7:55 TI9* TC7 TI10 TI11 TI12 TC8 TR8 TR7 Games are to 15 points Half time at 8 points Games are 1 hour and 15 minutes long Soft cap is 10 minutes before the end of game, +1 to highest score 2 Timeouts per team, per game NO TIMEOUTS AFTER SOFT CAP Footblocks not allowed, unless captains agree otherwise 2013 TUC Monday Competitive Playoffs - 1st to 7th Place 3rd Place Bracket Loser of MC4 Competitive Teams Winner of MC9 MC9 Allth Darth (1) Allth Darth (1) 3rd Place Slam Dunks (2) Loser of MC5 The Ligers (3) Winner of MC4 MC4 Krash Kart (4) Krash Kart (4) The El Guapo Sausage Party (5) MC1 Wonky Pooh (6) Winner of MC1 Disc Horde (7) The El Guapo Sausage Winner of MC8 Party (5) MC8 Slam Dunks (2) Champions Winner of MC2 MC2 Disc Horde (7) MC5 The Ligers (3) Winner of MC5 MC3 Winner of MC3 Wonky Pooh (6) Time Hockey3 Score Spirit Hockey4 Score Spirit Hockey5 Score Spirit Score Spirit 10:40 Krash Kart (4) Slam Dunks (2) The Ligers (3) to vs. -

Evolution of Stickleback in 50 Years on Earthquake-Uplifted Islands
Evolution of stickleback in 50 years on earthquake-uplifted islands Emily A. Lescaka,b, Susan L. Basshamc, Julian Catchenc,d, Ofer Gelmondb,1, Mary L. Sherbickb, Frank A. von Hippelb, and William A. Creskoc,2 aSchool of Fisheries and Ocean Sciences, University of Alaska Fairbanks, Fairbanks, AK 99775; bDepartment of Biological Sciences, University of Alaska Anchorage, Anchorage, AK 99508; cInstitute of Ecology and Evolution, University of Oregon, Eugene, OR 97403; and dDepartment of Animal Biology, University of Illinois at Urbana–Champaign, Urbana, IL 61801 Edited by John C. Avise, University of California, Irvine, CA, and approved November 9, 2015 (received for review June 19, 2015) How rapidly can animal populations in the wild evolve when faced occur immediately after a habitat shift or environmental distur- with sudden environmental shifts? Uplift during the 1964 Great bance (26, 27). However, because of previous technological lim- Alaska Earthquake abruptly created freshwater ponds on multiple itations, few studies of rapid differentiation in the wild have islands in Prince William Sound and the Gulf of Alaska. In the short included genetic data to fully disentangle evolution from induced time since the earthquake, the phenotypes of resident freshwater phenotypic plasticity. The small numbers of markers previously threespine stickleback fish on at least three of these islands have available for most population genetic studies have not provided changed dramatically from their oceanic ancestors. To test the the necessary precision with which to analyze very recently diverged hypothesis that these freshwater populations were derived from populations (but see refs. 28 and 29). As a consequence, the fre- oceanic ancestors only 50 y ago, we generated over 130,000 single- quency of contemporary evolution in the wild is still poorly defined, nucleotide polymorphism genotypes from more than 1,000 individ- and its genetic and genomic basis remains unclear (30). -

Church Cmte Book VI: Part Two: the Middle Years (1914-1939)
PART Two THEMIDDLE YEARS (1914-1939) Sometime in 1915 the Japanese warship Amma went aground in Turtle Bay in the Gulf of Lower California. The presence of this vessel in that part of the world was not a total surprise as Japanese fleet units had been previously sighted a few times in the area. Earlier the Grand admiral of Sippon had paid a visit to Mexico, expounding a blood brother theme. What appeared to be somewhat incredible about this incident was that the formidable veterans of Tsushima could be so inept as to allow this accident to happen. Indeed, it sub- sequently became questionable that the event was an accident at all. According to Sidney Nashbir, an intelligence officer destined to gain fame with General Douglas MacArthur’s Allied Translator and Inter- preter Section during World WTar II, there were “unquestionable proofs that whole companies of Japanese soldiers had traversed a part of southern Arizona in 1916 during secret exercises, proceedings that could only have been associated with the Asam’s wallowing in the mud the previous year.” As an intelligence officer in 1916 with the First Arizona Infantry he had been detailed by that General Funston of Aguinaldo fame on a mission to seek the truth of rumors among Indians of Japanese columns present in northern Sonora in Mexico. Mashbir, who later acted as a gpy for America in Manchuria., tramped across the desert (which he knew well enough to make tihe first map of it our Army ever had). His knowledge of the desert told him that even the Japanese, incredible marchers that they were, could not ,have made the trip without violating Arizona territory to the north for water. -

2014 Tuc Monday/Tuesday Playoff Master Field Schedule
2014 TUC MONDAY/TUESDAY PLAYOFF MASTER FIELD SCHEDULE Start End Hockey 1 Hockey 2 Hockey 3 Hockey 4 Hockey 5 Hockey 6 Ulti A Rugby E1 Rugby E2 9:20 10:35 MI1 MI2 MC1 MC2 MI8 MI9 10:40 11:55 MI3 MI4 MC5 MC3 MC4 MI11 MI5 MI10 12:00 1:15 MI6 MI7 MC7 1:30 2:55 ASI1 ASI2 ASC1 ASC2 MC6 3:00 4:25 ASI3 ASI4 ASC4 ASC3 4:30 5:45 T5 T6 T2 T1 5:50 7:05 T7 T8 T4 T3 TOURNAMENT RULES Games are to 15 points Half time at 8 points Playoff games are 1 hour and 15 minutes long Hard cap is at 75 minutes (finish the point, only if tied do you play another), and there is no soft cap. 1 Timeout per half, per team (no timeouts if in overtime) Footblocks are not allowed, unless captains agree otherwise 2014 TUC Monday Competitive Playoffs - 1st to 6th Place Teams 3rd Place Deep (1) Deep (1) L - MC3 Allth Darth (2) 3rd Place MC7 naptime (3) W - MC3 MC3 Slam Dunks (4) Slam Dunks (4) L - MC4 El Guapo (5) MC1 Basic Bishes (6) W - MC1 5th Place El Guapo (5) Champions L - MC1 MC6 5th Place MC5 Allth Darth (2) L - MC2 MC4 naptime (3) W - MC4 MC2 W - MC2 Basic Bishes (6) Time Hockey 4 Score Spirit Hockey 6 Score Spirit 9:20 Slam Dunks (4) naptime (3) to vs. MC 1 vs. MC 2 10:35 El Guapo (5) Basic Bishes (6) Time Hockey 4 Score Spirit Hockey 6 Score Spirit Hockey 3 Score Spirit 10:40 Deep (1) Allth Darth (2) L - MC1 to vs. -
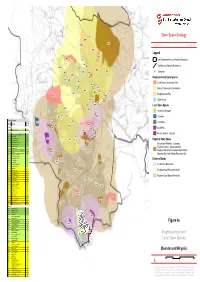
7929 GIS 104 Fig 4A Neighbourhood and Local Open Space
ML1 Open Space Strategy MR1 MF1 MR10 January 2014 7929 GIS 104 MR1 Legend MP2 MS3 MI6 East Dunbartonshire Local Authority Boundary MI7 MI5 Scottish Local Authority Boundaries MS4 MI9 BLF1 MR5 MI15 ! MP3 MI2 MR1 Allotments MR4 MI12 Neighbourhood Open Spaces MS7 MI4 MI1 Local Nature Conservation Site MI10 MI13 MI11 MI3 Natural / Semi-natural Greenspace MR6 MS6 Neighbourhood Park MS2 MR8 MI14 Sports Areas ML2 MR9 MR3 Local Open Spaces BI18 MI8 BI8 Amenity Greenspace BI1 BI2 BI15 MR7 Cemetery BI16 Fitness for Purpose BR6 Quality BF2 Civic Space Site Ref. Site Name MR2 Score BR5 BI14 Baldernock BI4 Local Park BLF1 Baldernock Cemetery 69 BR12 Bearsden BI6 BR2 Kilmardinny Loch Local Nature Reserve 85 Private Gardens / Grounds BR12 Mosshead Park 81 BI11 BP2 Glasgow Uni. Woods 79 BR3 BI10 Regional Open Space BR3 Langfaulds Field 78 BR2 BI17 Bearsden War Memorial 76 BR4 King George V Park 76 Recreational Walkway / Cycleway; BS2 Cairnhill Woods 76 Regional Historic / Natural Attraction; BR1 Colquhoun Park 74 BI4 Grampian Way and Cruchan Road O.S. 73 BI13 Regional Site of Nature Conservation Interest; BR7 Thorn Park 70 BR11 BR6 Heather Ave Open Space 68 Regional Sport and Outdoor Recreation Site BF1 New Kilpatrick Cemetery 67 BI15 Paterson Place O.S. 66 BR8 BS1 Templehill Woods 65 BF1 Distance Bands BR11 Antonine Park 65 BI12 BI18 Stockie Muir Road OS 2 65 Local Parks 400m buffer BI5 Braemar Cres. O.S. 65 BR8 Roman Park 64 BS3 Cairnhill Woods 64 BI17 Neighbourhood Parks 840m buffer BF2 Langfaulds Cemetery 63 BR7 BI2 Stockie Muir Road 1 63 BI16 Abercrombie Dr. -

Prosecuting Trafficking in Persons Cases: an Analysis of Local Strategies and Approaches, Final Report Author(S): Kristina Lugo-Graulich, Mark Myrent, Lisa M
The author(s) shown below used Federal funding provided by the U.S. Department of Justice to prepare the following resource: Document Title: Prosecuting Trafficking in Persons Cases: An Analysis of Local Strategies and Approaches, Final Report Author(s): Kristina Lugo-Graulich, Mark Myrent, Lisa M. Pierotte, Bradley T. Brick Document Number: 301296 Date Received: July 2021 Award Number: 2016-U-CX-0005 This resource has not been published by the U.S. Department of Justice. This resource is being made publically available through the Office of Justice Programs’ National Criminal Justice Reference Service. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. Department of Justice. Prosecuting Trafficking in Persons Cases: An Analysis of Local Strategies and Approaches Final Report Prepared for The National Institute of Justice Office of Justice Programs 810 Seventh Street NW Washington, DC 20531 by the Justice Research and Statistics Association 1000 Vermont Avenue NW, Suite 450, Washington, DC 20005 in partnership with the National District Attorney’s Association 1400 Crystal Drive, Suite 330, Arlington, VA 22202 Principal Investigator: Kristina Lugo-Graulich, Ph.D. October 2020 This report was supported by Cooperative Agreement No. 2016-U-CX-0005, awarded by the National Institute of Justice, Office of Justice Programs, U.S. Department of Justice to the Justice Research and Statistics Association. The opinions, findings, and conclusions or recommendations expressed are those of the authors and do not necessarily represent the official positions or policies of the U.S. Department of Justice. -

D 12 Cleveland
Acknowledgements The district-wide School Travel Plan (STP) for Cleveland Metropolitan School District (CMSD) was prepared by The Kleingers Group, TranSystems Corporation and MurphyEpson, in cooperation with the Ohio Department of Transportation (ODOT), Cleveland Metropolitan School District (CMSD), City of Cleveland (City Planning Commission, Traffic Engineering, Engineering and Construction, Police, Public Health, and Building and Housing), Northeast Ohio Areawide Coordinating Agency (NOACA), Bike Cleveland, Safe Routes to School (SRTS) National Partnership and staff members from other agencies and organizations that volunteered their time to develop and finalize this STP. A special thanks to the leaders and members of the Cleveland Safe Routes to School Team. The Cleveland Safe Routes to School Team would like to extend a special thanks to the following people for their help and support related to Safe Routes to School (SRTS) and the School Travel Plan for Cleveland: • Eric S. Gordon, CEO, Cleveland Metropolitan School District • Cleveland Metropolitan School District Board of Education Members: Denise W. Link, Chair Louise P. Dempsey, Esq., Vice Chair Anne E. Bingham Robert M. Heard, Sr. Willetta A. Milam Shaletha T. Mitchell Justin L. Monday, Esq. Stephanie Morales Lisa Thomas, Ph.D. Ronald M. Berkman, Ph.D., ex officio Alex Johnson, Ph.D., ex officio for Cleveland City Schools City Cleveland for School Travel Plan | Acknowledgements | | Acknowledgements i TABLE OF CONTENTS Introduction ....................................................................................................................................... -

Comparing Touchscreen and Mouse Input Performance by People with and Without Upper Body Motor Impairments
Accessibility CHI 2017, May 6–11, 2017, Denver, CO, USA Comparing Touchscreen and Mouse Input Performance by People With and Without Upper Body Motor Impairments Leah Findlater1, Karyn Moffatt3, Jon E. Froehlich2, Meethu Malu2, Joan Zhang2 1,2Human-Computer Interaction Lab 3ACT Research Group 1College of Information Studies | 2Dept. of Computer Science School of Information Studies University of Maryland, College Park, MD McGill University, Montreal, QC [email protected], {jonf, meethu}@cs.umd.edu, [email protected] [email protected] ABSTRACT Controlled studies of touchscreen input performance for users with upper body motor impairments remain relatively Pointing Crossing sparse. To address this gap, we present a controlled lab study of mouse vs. touchscreen performance with 32 participants (16 with upper body motor impairments and 16 without). Our Steering study examines: (1) how touch input compares to an indirect Dragging pointing device (a mouse); (2) how performance compares Figure 1. Cropped screenshots of the four study tasks, showing a range of orientations, target widths, and amplitudes. across a range of standard interaction techniques; and (3) how these answers differ for users with and without motor Despite the above body of work, controlled studies of impairments. While the touchscreen was faster than the touchscreen input performance for people with upper body mouse overall, only participants without motor impairments motor impairments are relatively sparse. Studies have benefited from a lower error rate on the touchscreen. Indeed, compared novel techniques (e.g., swabbing [17]) to a control participants with motor impairments had a three-fold condition such as tapping [9,10,17,20], but do not shed light increase in pointing (tapping) errors on the touchscreen on more general questions related to device comparisons compared to the mouse. -

PRAMS Phase 6 Questionnaire Topic Reference
PRAMS Phase 6 Questionnaire Topic Reference 1 TABLE OF CONTENTS ABOUT THIS DOCUMENT ............................................................................................................... 5 1. ABUSE ........................................................................................................................................ 6 A. PHYSICAL ................................................................................................................. 6 B. EMOTIONAL ............................................................................................................ 9 C. SEXUAL .................................................................................................................. 10 2. ASSISTED REPRODUCTION ...................................................................................................... 11 3. BREASTFEEDING ...................................................................................................................... 13 4. CHILD CARE .............................................................................................................................. 17 5. CONTRACEPTION ..................................................................................................................... 18 A. PRE-CONCEPTION ................................................................................................. 18 B. CONCEPTION ........................................................................................................ 18 C. POSTPARTUM ...................................................................................................... -

University of Groningen Design and Verification of Lock-Free Parallel
University of Groningen Design and verification of lock-free parallel algorithms Gao, Hui IMPORTANT NOTE: You are advised to consult the publisher's version (publisher's PDF) if you wish to cite from it. Please check the document version below. Document Version Publisher's PDF, also known as Version of record Publication date: 2005 Link to publication in University of Groningen/UMCG research database Citation for published version (APA): Gao, H. (2005). Design and verification of lock-free parallel algorithms. s.n. Copyright Other than for strictly personal use, it is not permitted to download or to forward/distribute the text or part of it without the consent of the author(s) and/or copyright holder(s), unless the work is under an open content license (like Creative Commons). Take-down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. Downloaded from the University of Groningen/UMCG research database (Pure): http://www.rug.nl/research/portal. For technical reasons the number of authors shown on this cover page is limited to 10 maximum. Download date: 27-09-2021 Appendix A For lock-free dynamic hash tables A.1 Invariants Some abbreviations. Find(r, a) , r = null ∨ a = ADR(r) LeastFind(a, n) , (∀m<n : ¬Find(Y[key(a, curSize, m)], a)) ∧ Find(Y[key(a, curSize, n)], a)) LeastFind(h, a, n) , (∀m<n : ¬Find(h.table[key(a, h.size, m)], a)) ∧ Find(h.table[key(a, h.size, n)], a)) Axioms on functions key and ADR.