Table of Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Courts' Indecipherable Approach to Encryption
WARNING—WEAK PASSWORD: THE COURTS’ INDECIPHERABLE APPROACH TO ENCRYPTION AND THE FIFTH AMENDMENT Matthew J. Weber TABLE OF CONTENTS I. Introduction ......................................................................................... 456 II. Background ......................................................................................... 458 A. The Rise of Encryption ................................................................ 458 B. What Is Encryption? .................................................................... 458 C. Encryption and Tech Companies ................................................. 459 III. Analysis ............................................................................................... 461 A. Existing Framework/Legal History ............................................. 461 1. Fisher v. United States .......................................................... 461 2. Doe v. United States .............................................................. 462 3. United States v. Hubbell ........................................................ 463 B. Applying the Existing Framework to Encryption Cases ............. 464 1. Boucher I and II ..................................................................... 465 2. United States v. Friscosu ....................................................... 468 3. United States v. Doe (In re Grand Jury Subpoena Duces Tecum Dated March 25, 2011) .............................................. 468 C. Encryption Law in the Future/Current Events ............................ -
![Secrets at Apple's Core [Entire Talk]](https://docslib.b-cdn.net/cover/9898/secrets-at-apples-core-entire-talk-1499898.webp)
Secrets at Apple's Core [Entire Talk]
Stanford eCorner Secrets at Apple's Core [Entire Talk] Adam Lashinsky, Author May 23, 2012 Video URL: http://ecorner.stanford.edu/videos/2973/Secrets-at-Apples-Core-Entire-Talk Adam Lashinsky, Fortune senior editor-at-large, shares an insider look at Apple, one of the world's most iconic and secretive companies. Based on his research into the technology giant's internal processes and approaches to leadership and building products, Lashinsky offers insights and surprises from his book, Inside Apple: How America's Most Admired--and Secretive-- Company Really Works. Transcript Almost exactly a year-ago this week I published an article in Fortune magazine with the same title as you see in front of you, Inside Apple. We decided at Fortune that in Apple we had a company that the entire world thought they knew a lot about because the world knew about Apple's products. And they knew about Apple's advertising and its image and its brand and its logo and so on. When in fact the world knew and really still does know very little about how Apple does what it does, what goes on inside Apple? There is a reason for that and it's a major part of my thesis and what I've learned in researching this company intensely over the last year and that is that Apple doesn't want us to know what goes on inside Apple. Apple is professionally focused on telling us, telling you about its products. Not about it. As a business journalist, my job is not to be concerned with what Apple is interested in us knowing, but what my readers at Fortune magazine ought to know and want to know. -

'19 Contents It's Frustrating That Preview in Mojave Isn'
A Publication of the Silicon Mountain Macintosh User Group Colorado Springs Metro Area It’s Frustrating That Preview in Mojave Isn’t Better April ’19 by ADAM ENGST Volume 35 Issue 4 I haven’t done much with Take Control since we sold the business to Joe Kissell in 2017 (see “Take Contents Control Books Acquired by Joe Kissell,” 1 May 2017), but I recently found myself back in the saddle to update Take Control of Preview. Josh Centers and I co-wrote the book about the version of Preview SIG News 2 that shipped with macOS 10.11 El Capitan, back in July 2016, and while I have continued to rely on the Club News 3 app every day, not much seemed to change with Preview in 10.12 Sierra or 10.13 High Sierra. When Door Prize Winners 6 10.14 Mojave rolled around, however, its Continuity Camera and screenshot features directly impacted Preview, so I decided it was time to do a deep dive and see what else might have changed in Preview. Joy of Tech 7 Unfortunately, the results of my investigation weren’t particularly Apple Special Event 8 positive. The new features in Preview don’t add much value, one Macs, iPads & Apple change is actively bad, and Apple introduced a handful of bugs. Don’t get me wrong—I still think Preview is a snazzy little app Watch 18 that’s far more useful than most people realize, and I probably use it Siri Tips & Tricks 22 more than any other Apple app on my Mac (because I prefer Chrome to Safari and Mailplane to Mail). -

300Tage Tim Cook
300 Tage Tim Cook Wie führt er Apple? Tim Cook führt Apple bei Redaktionsschluss seit 300 Tagen. Erste eigene Schritte hat Cook an der Spitze des desig- nverliebten Unternehmens mit den kühnen Produktvisionen absolviert, sein eigenes Profil hat er noch nicht gefunden. Dirk Kunde Tim Cook stellt die dritte Generation des iPad im Yerba Buena Center in San Francisco vor. FOTO: Getty Images / Kevork Djansezian Redaktionelles News & Trends Headliner Testlabor Mac Help Mac Life 109 ungenannter Branchenexperte in einem der wenigen Artikel, die man über Cook in US-Archiven findet. Die Summe ist natürlich zu hoch gegriffen, doch so ein Gerät unter 1.000 Dollar anbieten zu können, ist eine Meisterleistung. Genau für diese Aufgabe wirbt ihn Jobs im Frühjahr 1998 bei Compaq ab. Zu diesem Zeit- punkt betreibt Apple eigene Fabriken. Cook senkt die Zahl der Zulieferer von mehreren Hundert auf 24. Für Produkte wie Drucker oder den Newton kommt das as hat selbst Steve Aus. Neun von zehn Lagerhäuser werden geschlos- Jobs beeindruckt. Der sen. Bis dahin stehen für zwei Monate fertige Pro- sonst so ruhige und dukte in den Regalen. Cook senkt das auf zwei Tage. stille Tim Cook stei- Der Schnitt entschlackt die Bilanz um 500 Millionen gert sich in einer Tele- US-Dollar, denn Inventar ist totes Kapital. Just-In-Time- fonkonferenz in ein Produktion ist das Schlagwort Ende der 90er Jahre und minutenlanges Apple- somit ist die Auslagerung nach Asien unausweichlich. Glaubensbekenntnis. Jobs will Kontrolle über die Produkte von der Entwick- Es fallen Sätze wie lung bis zum Verkauf, und so treibt Cook den Aufbau D „Wir sind auf der Erde, eigener Läden voran. -

Augmented Reality - Bloomberg More Stories by Mark Gurman • March 20, 2017, 4:00 AM MDT
Apple’s Next Big Thing: Augmented Reality - Bloomberg More stories by Mark Gurman • March 20, 2017, 4:00 AM MDT Tim Cook has talked up a lot of technologies since becoming Apple Inc.'s chief executive in 2011. Driverless cars. Artificial intelligence. Streaming television. But no technology has fired up Cook quite like augmented reality, which overlays images, video and games on the real world. Cook has likened AR's game-changing potential to that of the smartphone. At some point, he said last year, we will all "have AR experiences every day, almost like eating three meals a day. It will become that much a part of you." Investors impatient for Apple's next breakthrough will be happy to know that Cook is very serious about AR. People with knowledge of the company's plans say Apple has embarked on an ambitious bid to bring the technology to the masses—an effort Cook and his team see as the best way for the company to dominate the next generation of gadgetry and keep people wedded to its ecosystem. Apple has built a team combining the strengths of its hardware and software veterans with the expertise of talented outsiders, say the people, who requested anonymity to discuss internal strategy. Run by a former Dolby Laboratories executive, the group includes engineers who worked on the Oculus and HoloLens virtual reality headsets sold by Facebook and Microsoft as well as digital-effects wizards from Hollywood. Apple has also acquired several small firms with knowledge of AR hardware, 3D gaming and virtual reality software. -

Halaman Judul Halaman Pengesahan Pembimbing
PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI HALAMAN JUDUL PENGARUH KUALITAS PRODUK, HARGA, DAN PROMOSI TERHADAP KEPUTUSAN PEMBELIAN SMARTPHONE IPHONE (studi kasus konsumen Iphone di kampus 1 Universitas Sanata Dharma) Skripsi Diajukan dalam Rangka Menulis Skripsi Program Studi Manajemen, Jurusan Manajemen Fakultas Ekonomi Universitas Sanata Dharma Oleh : Leonardus Niko Andira NIM: 152214089 PROGRAM STUDI MANAJEMEN JURUSAN MANAJEMEN FAKULTAS EKONOMI UNIVERSITAS SANATA DHARMA YOGYAKARTA 2019 HALAMAN PENGESAHAN PEMBIMBING PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI HALAMAN JUDUL PENGARUH KUALITAS PRODUK, HARGA, DAN PROMOSI TERHADAP KEPUTUSAN PEMBELIAN SMARTPHONE IPHONE (studi kasus konsumen Iphone di kampus 1 Universitas Sanata Dharma) Skripsi Diajukan dalam Rangka Menulis Skripsi Program Studi Manajemen, Jurusan Manajemen Fakultas Ekonomi Universitas Sanata Dharma Oleh : Leonardus Niko Andira NIM: 152214089 PROGRAM STUDI MANAJEMEN JURUSAN MANAJEMEN FAKULTAS EKONOMI UNIVERSITAS SANATA DHARMA YOGYAKARTA 2019 HALAMAN PENGESAHAN PEMBIMBING i PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI Moto dan Persembahan “Kamu harus bisa menghibur dirimu, karena kebahagian tidak datang dari manapun melainkan dari dalam dirimu sendiri” (CakNun) “Apa yang membuatmu bahagia lakukanlah dan apa yang membuatmu bersedih tinggalkan” Skripsi ini saya persembahkan untuk : Tuhan Yesus Kristus dan Bunda Maria yang selalu memberkati saya dalam mengerjakan skripsi dari awal hingga selesai. Ayah dan -

Apple Inc. This Article Is About the Technology Company
Apple Inc. This article is about the technology company. For other companies named "Apple", see Apple (disambiguation). Apple Inc. Type Public Traded as NASDAQ: AAPL NASDAQ-100 Component S&P 500 Component Industry Computer hardware Computer software Consumer electronics Digital distribution Founded April 1, 1976 (incorporated January 3, 1977 as Apple Computer, Inc.) Founder(s) Steve Jobs Steve Wozniak Ronald Wayne[1] Headquarters Apple Campus, 1 Infinite Loop, Cupertino, California, U.S. Number of 357 retail stores(as of October 2011) locations Area served Worldwide Key people Tim Cook (CEO) Arthur Levinson (Chairman)[2] Sir Jonathan Ive (SVP, Industrial Design) Steve Jobs (Chairman, 1976-1985/2011; CEO, 1997– 2011) Products Products list[show] Services Services list[show] [3] Revenue US$ 108.249 billion (FY 2011) [3] Operating income US$ 33.790 billion (FY 2011) [3] Profit US$ 25.922 billion (FY 2011) [3] Total assets US$ 116.371 billion (FY 2011) [3] Total equity US$ 76.615 billion (FY 2011) Employees 60,400 (2011)[4] Subsidiaries Braeburn Capital FileMaker Inc. Anobit Website Apple.com Apple Inc. (NASDAQ: AAPL ; formerly Apple Computer, Inc.) is an American multinational corporation that designs and sellsconsumer electronics, computer software, and personal computers. The company's best-known hardware products are the Macintoshline of computers, the iPod, the iPhone and the iPad. Its software includes the Mac OS X operating system; the iTunes media browser; the iLife suite of multimedia and creativity software; the iWork suite of productivity software; Aperture, a professional photography package; Final Cut Studio, a suite of professional audio and film-industry software products; Logic Studio, a suite of music production tools; the Safari web browser; and iOS, a mobile operating system. -

Mosk: Later That Day
MOSK: LATER THAT DAY There’s a whole other show waiting. Today, Jeff Gamet joins us to Tuesday, August 28, 2012 Tuesday, discuss all the Apple news that’s fit to pretend- print. Cross-Platform Zero-Day Vulnerability Found for Java 7; Affects Windows, Linux and OS X Tap If you’ve got Java 7 installed on your computer you seem to have a Here to serious security risk on your hands. Infoworld says “hackers are Listen! exploiting a zero-day vulnerability in Java 7,” one that “can be exploited through any browser running on any operating system, from Windows and Linux to OS X, that has Java installed...” According to the piece, "the vulnerability is not in Java 6, it's in new functionality in Java 7." While Apple stopped bundling Java in OS X with last year’s Lion release, the piece says users can and do install it on their own when they encounter a site that employs a Java applet. So far all of the known exploits in the wild have targeted Windows machines, though the piece says there’s nothing to stop an exploit aimed at the Mac. Security experts recommend disabling Java until Oracle delivers a patch. Java can be disabled on a Mac in the preferences of your chosen browser or browsers... and thanks to Information Security pro George Starcher for sending me this story... and freaking me the freak out. 1 The Apple v. Samsung Aftermath Continues Samsung Bashes Apple for Litigiousness Post Apple v. Samsung v. Apple Verdict August 28, 2012 Since the Apple v. -
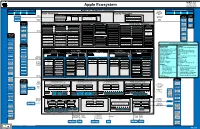
Apple Ecosystem Y
Apple Inc. One Apple Park Way Cupertino, CA 95014 Apple Ecosystem Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Hiring / Training Legal Stock Market Ernst & Young Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Apple Ecosystem Cupertino, CA 95014 Phone: (408) 996-1010
Apple Inc. One Apple Park Way Apple Ecosystem Cupertino, CA 95014 Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Legal Stock Market Ernst & Young Hiring / Training Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Steve Jobs "Top 100"
DEFENDANT'S EXHIBIT NO. 489.245 Subject: Re: Top 100 - A From: "Michael Tchao" <[email protected]> To: "Philip Schiller" <[email protected]> Date: 2010-10-25T15:36:31Z Thanks. This helps a lot. [m] On Oct 25, 2010, at 8:26 AM, Philip Schiller wrote: FYI - DO NOT FORWARD Begin forwarded message: From: Steve Jobs <[email protected]> Date: October 24, 2010 6:12:41 PM PDT To: ET <[email protected]> Subject: Top 100 - A Here's my current cut. Steve 1. 2011 Strategy - SJ - who are we? - headcount, average age, ... - VP count, senior promotions in last year - percent new membership at this meeting - what do we do? - pie chart of units/product line and revenues/product line - same charts with tablets + phones merged together - Post PC era - Apple is the first company to get here - Post PC products now 66% of our revenues - iPad outsold Mac within 6 months - Post PC era = more mobile (smaller, thinner, lighter) + communications + apps + cloud services - 2011: Holy War with Google - all the ways we will compete with them - primary reason for this Top 100 meeting - you will hear about what we're doing in each presentation - 2011: Year of the Cloud - we invented Digital Hub concept Highly Confidential - Attorneys' Eyes Only APLNDC630-0001195522 DEFENDANT'S EXHIBIT NO. 489.246 - PC as hub for all your digital assets - contacts, calendars, bookmarks, photos, music, videos - digital hub (center of our universe) is moving from PC to cloud - PC now just another client alongside iPhone, iPad, iPod touch, ... - Apple is in danger of hanging on to old paradigm too long (innovator's dilemma) - Google and Microsoft are further along on the technology, but haven't quite figured it out yet - tie all of our products together, so we further lock customers into our ecosystem - 2015: new campus 2. -

Apple 1 Crisis Communication Plan #2: Technical-Error Harm Purpose
Crisis Communication Plan #2: Technical-Error Harm Purpose: In the event that iTunes user accounts and the servers are hacked, we must take immediate action to respond and inform all our publics of the situation. We will provide systematic tips and preventative measures to ensure other user accounts are not hacked or fraudulent use of a user account occurs. Apple’s focus is to respond to this crisis through ensuring all parties have the most available information. This will allow information to be communicated consistently, openly, and accurately to all parties. The resolution to the crisis can be obtained through an efficient and quick response, leading to open communication with all parties at all times. This path will allow all communication barriers to cease and stop any other problems at the source. Objectives: 1. Assess the crisis situation: a. Locate source of problem. 2. Assemble the CMT (Crisis Management Team) as outlined in the staff directory. 3. Setup Crisis Control Center and start preparation of all-important materials needed for the response. 4. CMT will take the assessments and data gathered to determine the appropriate strategies to respond to the situation. 5. CMT Lead will assign and implement the use of the Methods of Communication Chart to the appropriate key publics. 6. CMT Lead will need to be the first to be notified of the situation. CMT will refer to List of key publics to know who takes priority to contact from first to last. 7. Have a data and system analyst collect all available data from the network and all other available resources.