The Courts' Indecipherable Approach to Encryption
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

'19 Contents It's Frustrating That Preview in Mojave Isn'
A Publication of the Silicon Mountain Macintosh User Group Colorado Springs Metro Area It’s Frustrating That Preview in Mojave Isn’t Better April ’19 by ADAM ENGST Volume 35 Issue 4 I haven’t done much with Take Control since we sold the business to Joe Kissell in 2017 (see “Take Contents Control Books Acquired by Joe Kissell,” 1 May 2017), but I recently found myself back in the saddle to update Take Control of Preview. Josh Centers and I co-wrote the book about the version of Preview SIG News 2 that shipped with macOS 10.11 El Capitan, back in July 2016, and while I have continued to rely on the Club News 3 app every day, not much seemed to change with Preview in 10.12 Sierra or 10.13 High Sierra. When Door Prize Winners 6 10.14 Mojave rolled around, however, its Continuity Camera and screenshot features directly impacted Preview, so I decided it was time to do a deep dive and see what else might have changed in Preview. Joy of Tech 7 Unfortunately, the results of my investigation weren’t particularly Apple Special Event 8 positive. The new features in Preview don’t add much value, one Macs, iPads & Apple change is actively bad, and Apple introduced a handful of bugs. Don’t get me wrong—I still think Preview is a snazzy little app Watch 18 that’s far more useful than most people realize, and I probably use it Siri Tips & Tricks 22 more than any other Apple app on my Mac (because I prefer Chrome to Safari and Mailplane to Mail). -

Augmented Reality - Bloomberg More Stories by Mark Gurman • March 20, 2017, 4:00 AM MDT
Apple’s Next Big Thing: Augmented Reality - Bloomberg More stories by Mark Gurman • March 20, 2017, 4:00 AM MDT Tim Cook has talked up a lot of technologies since becoming Apple Inc.'s chief executive in 2011. Driverless cars. Artificial intelligence. Streaming television. But no technology has fired up Cook quite like augmented reality, which overlays images, video and games on the real world. Cook has likened AR's game-changing potential to that of the smartphone. At some point, he said last year, we will all "have AR experiences every day, almost like eating three meals a day. It will become that much a part of you." Investors impatient for Apple's next breakthrough will be happy to know that Cook is very serious about AR. People with knowledge of the company's plans say Apple has embarked on an ambitious bid to bring the technology to the masses—an effort Cook and his team see as the best way for the company to dominate the next generation of gadgetry and keep people wedded to its ecosystem. Apple has built a team combining the strengths of its hardware and software veterans with the expertise of talented outsiders, say the people, who requested anonymity to discuss internal strategy. Run by a former Dolby Laboratories executive, the group includes engineers who worked on the Oculus and HoloLens virtual reality headsets sold by Facebook and Microsoft as well as digital-effects wizards from Hollywood. Apple has also acquired several small firms with knowledge of AR hardware, 3D gaming and virtual reality software. -

Halaman Judul Halaman Pengesahan Pembimbing
PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI HALAMAN JUDUL PENGARUH KUALITAS PRODUK, HARGA, DAN PROMOSI TERHADAP KEPUTUSAN PEMBELIAN SMARTPHONE IPHONE (studi kasus konsumen Iphone di kampus 1 Universitas Sanata Dharma) Skripsi Diajukan dalam Rangka Menulis Skripsi Program Studi Manajemen, Jurusan Manajemen Fakultas Ekonomi Universitas Sanata Dharma Oleh : Leonardus Niko Andira NIM: 152214089 PROGRAM STUDI MANAJEMEN JURUSAN MANAJEMEN FAKULTAS EKONOMI UNIVERSITAS SANATA DHARMA YOGYAKARTA 2019 HALAMAN PENGESAHAN PEMBIMBING PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI HALAMAN JUDUL PENGARUH KUALITAS PRODUK, HARGA, DAN PROMOSI TERHADAP KEPUTUSAN PEMBELIAN SMARTPHONE IPHONE (studi kasus konsumen Iphone di kampus 1 Universitas Sanata Dharma) Skripsi Diajukan dalam Rangka Menulis Skripsi Program Studi Manajemen, Jurusan Manajemen Fakultas Ekonomi Universitas Sanata Dharma Oleh : Leonardus Niko Andira NIM: 152214089 PROGRAM STUDI MANAJEMEN JURUSAN MANAJEMEN FAKULTAS EKONOMI UNIVERSITAS SANATA DHARMA YOGYAKARTA 2019 HALAMAN PENGESAHAN PEMBIMBING i PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI Moto dan Persembahan “Kamu harus bisa menghibur dirimu, karena kebahagian tidak datang dari manapun melainkan dari dalam dirimu sendiri” (CakNun) “Apa yang membuatmu bahagia lakukanlah dan apa yang membuatmu bersedih tinggalkan” Skripsi ini saya persembahkan untuk : Tuhan Yesus Kristus dan Bunda Maria yang selalu memberkati saya dalam mengerjakan skripsi dari awal hingga selesai. Ayah dan -
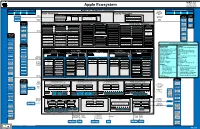
Apple Ecosystem Y
Apple Inc. One Apple Park Way Cupertino, CA 95014 Apple Ecosystem Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Hiring / Training Legal Stock Market Ernst & Young Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Apple Ecosystem Cupertino, CA 95014 Phone: (408) 996-1010
Apple Inc. One Apple Park Way Apple Ecosystem Cupertino, CA 95014 Phone: (408) 996-1010 www.apple.com Outside Relationships Apple Inc. (California Corporation) Securities Outside Relationships Regulation and Regulators Capital Suppliers Customers NASDAQ Listing Customers Suppliers Capital Regulators Debt Structure Equity Structure Rules Bond Debt ( $107B @ 9/28/19) Credit Ratings: Aa1 (Moody’s), AA+ (S&P) Equity Securities Public Debt Financing Common Stock Significant Regulators Common Stock (12.6 Billion Authorized; Holders Senior Floating Senior Fixed Rate Notes ($97.5B), Repurchases Shareholders 4.443 Million Shares Outstanding) US Securities Commercial Rate Notes bearing interest at 0.875% to 3.6% Vanguard Commercial Commercial Paper (9- Equity and Paper ($4.25B) and maturing 2022 to 2042 Group Banks months or less) ($6 billion) $175 Billion Share Repurchase Program Capital Exchange (7.36%) Commission Professional Berkshire Services Governance Human Resources Sales and Marketing Finance and Accounting Corporate Matters Hathaway The NASDAQ Board of Directors Research & (5.6%) Legal Stock Market Ernst & Young Hiring / Training Advertising Budget Support Development Arthur D. Levinson (C) Albert Gore Jr. (C, N) Susan L. Wagner (N, A) Real Estate IP Management BlackRock (Auditors) New Technologies Pension Plans Retail Accounts Internal Audit Fund TBWA/Media Tim Cook Andrea Jung (C, N) Ronald D. Sugar (A) Transactions Subsidiary Management Existing Product Advisors Professional Compensation E Commerce Accounting Arts Lab Enhancements -

Steve Jobs "Top 100"
DEFENDANT'S EXHIBIT NO. 489.245 Subject: Re: Top 100 - A From: "Michael Tchao" <[email protected]> To: "Philip Schiller" <[email protected]> Date: 2010-10-25T15:36:31Z Thanks. This helps a lot. [m] On Oct 25, 2010, at 8:26 AM, Philip Schiller wrote: FYI - DO NOT FORWARD Begin forwarded message: From: Steve Jobs <[email protected]> Date: October 24, 2010 6:12:41 PM PDT To: ET <[email protected]> Subject: Top 100 - A Here's my current cut. Steve 1. 2011 Strategy - SJ - who are we? - headcount, average age, ... - VP count, senior promotions in last year - percent new membership at this meeting - what do we do? - pie chart of units/product line and revenues/product line - same charts with tablets + phones merged together - Post PC era - Apple is the first company to get here - Post PC products now 66% of our revenues - iPad outsold Mac within 6 months - Post PC era = more mobile (smaller, thinner, lighter) + communications + apps + cloud services - 2011: Holy War with Google - all the ways we will compete with them - primary reason for this Top 100 meeting - you will hear about what we're doing in each presentation - 2011: Year of the Cloud - we invented Digital Hub concept Highly Confidential - Attorneys' Eyes Only APLNDC630-0001195522 DEFENDANT'S EXHIBIT NO. 489.246 - PC as hub for all your digital assets - contacts, calendars, bookmarks, photos, music, videos - digital hub (center of our universe) is moving from PC to cloud - PC now just another client alongside iPhone, iPad, iPod touch, ... - Apple is in danger of hanging on to old paradigm too long (innovator's dilemma) - Google and Microsoft are further along on the technology, but haven't quite figured it out yet - tie all of our products together, so we further lock customers into our ecosystem - 2015: new campus 2. -

Apple 1 Crisis Communication Plan #2: Technical-Error Harm Purpose
Crisis Communication Plan #2: Technical-Error Harm Purpose: In the event that iTunes user accounts and the servers are hacked, we must take immediate action to respond and inform all our publics of the situation. We will provide systematic tips and preventative measures to ensure other user accounts are not hacked or fraudulent use of a user account occurs. Apple’s focus is to respond to this crisis through ensuring all parties have the most available information. This will allow information to be communicated consistently, openly, and accurately to all parties. The resolution to the crisis can be obtained through an efficient and quick response, leading to open communication with all parties at all times. This path will allow all communication barriers to cease and stop any other problems at the source. Objectives: 1. Assess the crisis situation: a. Locate source of problem. 2. Assemble the CMT (Crisis Management Team) as outlined in the staff directory. 3. Setup Crisis Control Center and start preparation of all-important materials needed for the response. 4. CMT will take the assessments and data gathered to determine the appropriate strategies to respond to the situation. 5. CMT Lead will assign and implement the use of the Methods of Communication Chart to the appropriate key publics. 6. CMT Lead will need to be the first to be notified of the situation. CMT will refer to List of key publics to know who takes priority to contact from first to last. 7. Have a data and system analyst collect all available data from the network and all other available resources. -
Printing How Tim Cook Made Apple His
TECH How Tim Cook Made Apple His Own The industrial engineer has turned Steve Jobs’s creation into a corporate colossus, delivering one of the most lucrative business successions in history. By Tripp Mickle Afer Steve Jobs’s death, Silicon Valley anticipated Apple Inc.’s business would falter. Wall Street fretted about the road ahead. And loyal customers agonized about the future of a beloved product innovator. Today, Apple shares are at record highs. The company’s market valuation is $1.9 trillion—bigger than the GDP of Canada, Russia or Spain. And Apple, now the world’s largest company, continues to dominate the smartphone market. It is a testament to how an industrial engineer—a man Bono called the Zen master—has turned Steve Jobs’s creation into Tim Cook’s Apple, delivering one of the most lucrative business successions in history through a triumph of method over magic. Where Mr. Jobs orchestrated great leaps of innovation, generally defined by new products capable of upending industries, Mr. Cook has made Apple more reflective of himself. The 59-year-old CEO, like the company he leads, is cautious, collaborative and tactical.Mr. Cook’s Apple, many former senior Apple executives say, is a corporate colossus pursuing growth by building an Apple, many former senior Apple executives say, is a corporate colossus pursuing growth by building an empire of products and services around his predecessor’s revolutionary inventions. Its success in wooing customers in China has helped sales soar while its drive for efciency has kept costs under control.Transitions from dominant leader to successor are seldom successful. -

Faussesadressesde Streamingsurleweb
Grand Big Mac® Big Mac® MacJr.® Ab 25.03.2019 /mcdlu As long as stockslast. ©2019McDonald’s N°2649 MARDI Fausses adresses de 2 AVRIL 2019 Luxembourg 7 Les frontaliers contraints à un changement de train streaming sur le web 350 euros d’abonnement annuel pour regar- ne fournissent même aucun contenu en der des films ou des séries en streaming. streaming. Le Centre européen des consom- C’est la somme folle réclamée par de faus- mateurs (CEC) a lancé un avertissement à ses plateformes de streaming diffusant du tous les consommateurs résidents pour leur contenu sur Internet. Le plus souvent, elles éviter de tomber dans le piège. PAGE 3 Nipsey People 16 Le manager Hussle de Rita Ora fait le tri abattu parmi ses prétendants MUSIQUE Le rappeur améri- cain nominé aux Grammy Awards Nipsey Hussle a été tué par balles diman- che à Los Angeles. Âgé de 33 ans, il a été abattu à bout portant, devant son propre magasin de vête- ments, par un homme qui s’est enfui en voiture. Deux autres personnes Sports 25 ont été blessées. Selon le Charles Leclerc entrevoit «Los Angeles Times», le meurtre était «probable- un avenir en vainqueur ment planifié et lié à un gang». De nombreuses stars ont rendu hommage au rappeur, qui à défaut de succès commercial, avait l’estime du monde du hip-hop. «Parti trop tôt», a écrit le rappeur Snoop Dogg. PAGE 18 «Cela n’a aucun sens! Mon Dieu, faites que son âme repose en Météo 28 paix!» MATIN APRÈS-MIDI Rihanna 7° 14° La chanteuse barbadienne a Nipsey Hussle, né Ermias Asghedom, a été abattu devant son propre magasin de vêtements. -

Town of Trumbull CONNECTICUT
WATER POLLUTION CONTROL AUTHORITY Town of Trumbull CONNECTICUT TOWN HALL 5866 MAIN STREET (203) 452-5048 TRUMBULL, CT 06611 JUNE 24, 2020 AGENDA NOTICE is hereby given that the Water Pollution Control Authority of the Town of Trumbull, Connecticut will hold a meeting on Wednesday, June 24, 2020 at 7:00 p.m. via videoconference for the following purpose: Water Pollution Control Authority Regular Meeting Wednesday, June 24, 2020 at 7:00 PM Join the meeting online: https://zoom.us/j/93059190411?pwd=TUpTZjJralQzOGI3S2UwY004NlJTUT09 Webinar ID: 930 5919 0411 Password: 655128 Join by telephone: (301) 715-8592 or (833) 548 0282 (Toll Free) / Webinar ID: 930 5919 0411 _____________________________________________________________________ 1. Call to Order 2. Approval of Minutes: • May 27, 2020 meeting minutes 3. New Business: • 38 MacDonald Road Sewer Connection 4. Old Business: • Sewer Usage Bill Freeze • Bridgeport WPCA FY 2020-2021 Budget • Beardsley Pump Station Force Main Update • Beardsley Pump Station Rehabilitation Update • Old Town and Reservoir Avenue Pump Stations Update 5. Any Other Business That May Come Before the Authority 6. Adjournment 1 WATER POLLUTION CONTROL AUTHORITY Town of Trumbull CONNECTICUT TOWN HALL 5866 MAIN STREET (203) 452-5048 TRUMBULL, CT 06611 MAY 27, 2020 MINUTES Call to Order: The Chair called the May 27, 2020 the virtual meeting to order at 7:00 p.m. The Chair asked that each speaker to identify themselves when they speak, where appropriate to provide their title. The Chair also reminded those present only one person should speak at a time and all votes would be taken by roll call of the WPCA Commissioners present. -

1 United States District Court for The
Case 1:18-cv-03534 Document 1 Filed 04/23/18 Page 1 of 25 UNITED STATES DISTRICT COURT FOR THE SOUTHERN DISTRICT OF NEW YORK ZOMM, LLC, ) ) Plaintiff, ) Case No.: 1:18-cv-03534 ) v. ) DEMAND FOR JURY TRIAL ) APPLE INC., ) ) Defendant. ) _______________________________________) COMPLAINT Plaintiff Zomm, LLC (“Zomm”), for its complaint against Apple Inc. (“Apple”) alleges as follows: THE PARTIES 1. Plaintiff Zomm is a limited liability company organized and existing under the laws of the State of Delaware, with its principal place of business at 8620 South Peoria Avenue, Tulsa, Oklahoma, 74132. 2. Upon information and belief, Defendant Apple is a California corporation organized under the laws of the State of California, with its principal place of business at 1 Infinite Loop, Cupertino, California 95014. NATURE OF THE ACTION 3. This is an action for patent infringement of U.S. Pat. No. 8,351,895 (“the ’895 Patent”) in violation of the United States patent laws, 35 U.S.C. § 100, et seq., unfair competition and for breach of contract under the laws of the State of New York. 1 Case 1:18-cv-03534 Document 1 Filed 04/23/18 Page 2 of 25 JURISDICTION AND VENUE 4. This Court has subject matter jurisdiction over the patent claim pursuant to 28 U.S.C. §§ 1331 and 1338(a). 5. This Court has subject matter jurisdiction over the breach of contract under 28 U.S.C. § 1337(a) (supplemental jurisdiction) because this claim is so related to the patent claim that it forms part of the same case or controversy. -

Second Report of the External Compliance Monitor : U.S. V. Apple, Inc., Et
Case 1:12-cv-03394-DLC-MHD Document 549 Filed 10/15/14 Page 1 of 163 Second Report of the External Compliance Monitor United States v. Apple, Inc., et al., No. 1:12-CV-2826, and The State of Texas, et al. v. Penguin Group (USA) Inc., et al., No. 1:12-CV-3394 Michael R. Bromwich External Compliance Monitor October 14, 2014 Case 1:12-cv-03394-DLC-MHD Document 549 Filed 10/15/14 Page 2 of 163 Executive Summary This is the second semi-annual report (“Report”) submitted by the External Compliance Monitor (the “Monitor”) in United States v. Apple, Inc., et al., No. 12-cv-2826, and State of Texas et al. v. Penguin Group (USA) Inc., et al., No. 12 cv-3394 (“ebooks Litigation”). In the September 5, 2013 Final Judgment and Order Entering Permanent Injunction (the “Final Judgment”), this Court ordered the Monitor to submit reports every six months “setting forth his . assessment of Apple’s internal antitrust compliance policies, procedures, and training and, if appropriate, making recommendations reasonably designed to improve Apple’s policies, procedures, and training for ensuring antitrust compliance.”1 The Monitor is required to evaluate whether Apple’s policies and procedures are “reasonably designed to detect and prevent violations of the antitrust laws” and whether Apple’s antitrust training program is “sufficiently comprehensive and effective.”2 We issued our “First Report” on April 14, 2014. At that time, for reasons set forth in detail in the First Report, we had very little information on which to assess the comprehensiveness and effectiveness of Apple’s antitrust policies, procedures, and training (Apple’s “Antitrust Compliance Program” or “Program”).