Cc Index.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ASEC REPORT Malicious Code Trend 5 6 Vol.17 Security Trend Web Security Trend
Disclosure to or reproduction for others without the specific written authorization of AhnLab is prohibited. ASEC Copyright (c) AhnLab, Inc. All rights reserved. REPORT VOL.17 | 2011.6 AhnLab Monthly Security Report AhnLab ASEC (AhnLab Security Emergency Response Center) is a Security global security response group consisting of virus analysts and CONTENTS Emergency security experts. This monthly report is published by ASEC, response and it focuses on the most significant security threats and the latest security technologies to guard against these threats. For 01. Malicious Code Trend 02. Security Trend Center further information about this report, please refer to AhnLab, a. Malicious Code Statistics 05 a. Security Statistics 14 Inc.’s homepage (www.ahnlab.com). - Top 20 Malicious Code Reports - Microsoft Security Updates- May 2011 - Top 20 Malicious Code Variant Reports b. Malicious Code Issues 16 - Breakdown of Primary Malicious Code Types - Comparison of Malicious Codes with - Zeus Source Code Leaked and Spyeye Trend Previous Month - Coreflood, a Banking Trojan - Monthly Malicious Code Reports - Online Banking Hacking Scam - Top 20 New Malicious Code Reports - Breakdown of New Malicious Code Types 03. Web Security Trend b. Malicious Code Issues 10 a. Web Security Statistics 17 - 'Dislike' Button Scam - Web Security Summary - AntiVirus AntiSpyware 2011 Scam - Monthly Blocked Malicious URLs - Scam Emails From Bobijou Inc. - Monthly Reported Types of Malicious Code - Spam Promising Nude Photo Spreads Malware - Monthly Domains with Malicious Code - Osama Bin Laden Themed Malware - Monthly URLs with Malicious Code - Distribution of Malicious Codes by Type - Top 10 Distributed Malicious Codes b. Web Security Issues 20 - May 2011 Malicious Code Intrusion: Website ASEC REPORT Malicious Code Trend 5 6 Vol.17 Security Trend Web Security Trend 01. -

Homeland Threats and Agency Responses”
STATEMENT OF ROBERT S. MUELLER, III DIRECTOR FEDERAL BUREAU OF INVESTIGATION BEFORE THE COMMITTEE ON HOMELAND SECURITY AND GOVERNMENTAL AFFAIRS UNITED STATES SENATE AT A HEARING ENTITLED “HOMELAND THREATS AND AGENCY RESPONSES” PRESENTED SEPTEMBER 19, 2012 Statement of Robert S. Mueller, III Director Federal Bureau of Investigation Before the Committee on Homeland Security and Governmental Affairs United States Senate At a Hearing Entitled “Homeland Threats and Agency Responses” Presented September 19, 2012 Good morning, Chairman Lieberman, Ranking Member Collins, and Members of the Committee. Thank you for the opportunity to appear before the Committee today and for your continued support of the men and women of the FBI. As you know, the Bureau has undergone unprecedented transformation in recent years. Since the attacks of September 11th, we have refocused our efforts to address and prevent emerging terrorist threats. The terrorist threat is more diverse than it was 11 years ago, but today, we in the FBI are better prepared to meet that threat. We also face increasingly complex threats to our nation’s cyber security. Nation-state actors, sophisticated organized crime groups, and hackers for hire are stealing trade secrets and valuable research from America’s companies, universities, and government agencies. Cyber threats also pose a significant risk to our nation’s critical infrastructure. As these threats continue to evolve, so too must the FBI change to counter those threats. We must continue to build partnerships with our law enforcement and private sector partners, as well as the communities we serve. Above all, we must remain firmly committed to carrying out our mission while protecting the civil rights and civil liberties of the people we serve. -

The Book of Apigee Edge Antipatterns V2.0
The Book of Apigee Edge Antipatterns Avoid common pitfalls, maximize the power of your APIs Version 2.0 Google Cloud Privileged and confidential. apigee 1 Contents Introduction to Antipatterns 3 What is this book about? 4 Why did we write it? 5 Antipattern Context 5 Target Audience 5 Authors 6 Acknowledgements 6 Edge Antipatterns 1. Policy Antipatterns 8 1.1. Use waitForComplete() in JavaScript code 8 1.2. Set Long Expiration time for OAuth Access and Refresh Token 13 1.3. Use Greedy Quantifiers in RegularExpressionProtection policy 16 1.4. Cache Error Responses 19 1.5. Store data greater than 512kb size in Cache 24 1.6. Log data to third party servers using JavaScript policy 27 1.7. Invoke the MessageLogging policy multiple times in an API proxy 29 1.8. Configure a Non Distributed Quota 36 1.9. Re-use a Quota policy 38 1.10. Use the RaiseFault policy under inappropriate conditions 44 1.11. Access multi-value HTTP Headers incorrectly in an API proxy 49 1.12. Use Service Callout policy to invoke a backend service in a No Target API proxy 54 Google Cloud Privileged and confidential. apigee 2 2. Performance Antipatterns 58 2.1. Leave unused NodeJS API Proxies deployed 58 3. Generic Antipatterns 60 3.1. Invoke Management API calls from an API proxy 60 3.2. Invoke a Proxy within Proxy using custom code or as a Target 65 3.3. Manage Edge Resources without using Source Control Management 69 3.4. Define multiple virtual hosts with same host alias and port number 73 3.5. -

A Strategy for Success in Libya
A Strategy for Success in Libya Emily Estelle NOVEMBER 2017 A Strategy for Success in Libya Emily Estelle NOVEMBER 2017 AMERICAN ENTERPRISE INSTITUTE © 2017 by the American Enterprise Institute. All rights reserved. The American Enterprise Institute (AEI) is a nonpartisan, nonprofit, 501(c)(3) educational organization and does not take institutional positions on any issues. The views expressed here are those of the author(s). Contents Executive Summary ......................................................................................................................1 Why the US Must Act in Libya Now ............................................................................................................................1 Wrong Problem, Wrong Strategy ............................................................................................................................... 2 What to Do ........................................................................................................................................................................ 2 Reframing US Policy in Libya .................................................................................................. 5 America’s Opportunity in Libya ................................................................................................................................. 6 The US Approach in Libya ............................................................................................................................................ 6 The Current Situation -
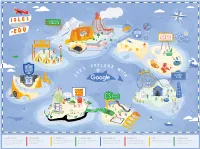
Google for Education National Parks VR Google Expeditions Google Arts & Culture Be Internet Awesome Made with Code CS First Google Science Fair
Google For Education National Parks VR Google Expeditions Google Arts & Culture Be Internet Awesome Made with Code CS First Google Science Fair Learn how tools built for teaching and learning, Discover the hidden worlds of our Take a field trip to virtually anywhere (even Explore works of art and stories from around Teach learners the fundamentals of digital Make the connection between coding and Learn the basics of Computer Science using the Create projects that show how Science, like Classroom, G Suite for Education, and National Parks on ranger-guided trips places school buses can’t go) using immersive the world with 360° tours of exhibits in over 70 safety and citizenship so they can be safe, creativity, empowering girls to engage with block-based programming language, Scratch. Technology, Engineering, and Math can be used Chromebooks, can increase engagement through virtual reality. AR and VR technology. different countries. confident explorers of the online world. technology and bring their ideas to life. to impact the world around us. and inspire curiosity. Google for National Google Google Arts Education Parks VR Expeditions & Culture Discover the hidden worlds of Explore works of art and stories Tools built for teaching and learning. Field trips to virtually anywhere. our National Parks. from around the world. Over 80 million teachers and students around the world Take a ranger-guided journey through the glaciers of What if you could journey to the surface of Mars or From The Metropolitan Museum of Art to Nairobi’s communicate and collaborate using Classroom and Alaska’s Kenai Fjords or get up close with active climb to the top of Machu Picchu without ever leaving Kenya National Archives, Google Arts & Culture offers G Suite for Education, while Chromebooks are the most volcanoes in Hawai’i. -

Code Girl Tracey Acosta Santa Clara University
Santa Clara University Scholar Commons Computer Engineering Senior Theses Engineering Senior Theses 6-1-2015 Code girl Tracey Acosta Santa Clara University Amanda Holl Santa Clara University Paige Rogalski Santa Clara University Follow this and additional works at: https://scholarcommons.scu.edu/cseng_senior Part of the Computer Engineering Commons Recommended Citation Acosta, Tracey; Holl, Amanda; and Rogalski, Paige, "Code girl" (2015). Computer Engineering Senior Theses. 43. https://scholarcommons.scu.edu/cseng_senior/43 This Thesis is brought to you for free and open access by the Engineering Senior Theses at Scholar Commons. It has been accepted for inclusion in Computer Engineering Senior Theses by an authorized administrator of Scholar Commons. For more information, please contact [email protected]. Code Girl by Tracey Acosta Amanda Holl Paige Rogalski Submitted in partial fulfillment of the requirements for the degrees of Bachelor of Science Computer Science and Engineering Bachelor of Science in Web Design and Engineering School of Engineering Santa Clara University Santa Clara, California June 1, 2015 Code Girl Tracey Acosta Amanda Holl Paige Rogalski Computer Science and Engineering Web Design and Engineering Santa Clara University June 1, 2015 ABSTRACT Despite the growing importance of technology and computing, fewer than 1% of women in college today choose to major in computer science.[1] Educational programs and games created to interest girls in computing, such as Girls Who Code and Made With Code, have been successful in engaging girls with interactive and creative learning environments, but they are too advanced for young girls to benefit from. To address the lack of educational, computer science games designed specifically for young girls, we developed a web-based application called Code Girl for girls age five to eight to customize their own avatar using Blockly, an open-source visual coding editor developed by Google. -

Pirates of the Isps: Tactics for Turning Online Crooks Into International Pariahs
21st CENTURY DEFENSE INITIATIVE CyBER SECuRITy #1 July 2011 Pirates of the ISPs: Tactics for Turning Online Crooks Into International Pariahs Noah Shachtman 1775 Massachusetts Ave., NW Washington, D.C. 20036 brookings.edu Pirates of the ISPs: Tactics for Turning Online Crooks Into International Pariahs Noah Shachtman CyberSeCurity #1 July 2011 21st CENTURY DEFENSE INITIATIVE Acknowledgements every research paper is a group effort, no mat- My Wired.com colleagues—ryan Singel, kevin ter what it says on the byline. this project relied Poulsen, kim Zetter and David kravets—cover more on outside assistance than most. brookings the cybersecurity beat better than anyone. this Senior fellows Peter Singer and ken lieberthal paper would have been impossible without them, were the ones who convinced me to explore the and without brian krebs, master investigator of broad topic of cybersecurity. the panel they as- the online underworld. sembled gave me new insight with every meeting; my colleague allan friedman was an especially bill Woodcock, rick Wesson, Jeff Cooper, tyler invaluable tutor and remarkably generous with Moore, audrey Plonk, Jim lewis, Dmitri alpero- his time. heather Messera and robert o’brien vitch, Paul Nicholas, Jessica herrera-flannigan, provided important research and logistical sup- Jart armin, richard bejtlich, Steve Schleien, Jona- port. My research assistant, adam rawnsley, was than Zittrain and many, many others steered me tireless in his exploration of the minutiae of ev- away from my worst ideas and towards those few erything from tort law to pirate havens. not-so-bad ones. for that, i am deeply in their debt. brookings recognizes that the value it provides to any supporter is in its absolute commitment to quality, independence and impact. -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -

The 2016 U.S. Election
April 2017, Volume 28, Number 2 $14.00 The 2016 U.S. Election William Galston John Sides, Michael Tesler, and Lynn Vavreck James Ceaser Nathaniel Persily Charles Stewart III The Modernization Trap Jack Snyder The Freedom House Survey for 2016 Arch Puddington and Tyler Roylance Sheriff Kora and Momodou Darboe on the Gambia Thomas Pepinsky on Southeast Asia Nic Cheeseman, Gabrielle Lynch, and Justin Willis on Ghana’s Elections Kai M. Thaler on Nicaragua Sean Yom on Jordan and Morocco The End of the Postnational Illusion Ghia Nodia The 2016 U.S. Election Longtime readers will be aware that this is the first time the Journal of Democracy has ever devoted a set of articles to the situation of democracy in the United States. Our traditional focus has been on the problems and prospects of democracy in developing and postcommunist countries. In the introduction to the group of essays in our October 2016 issue entitled “The Specter Haunting Europe,” we explained why we felt we had to redirect some of our attention to the growing vulnerability of democracy in the West, and promised that we would not refrain from examining the United States as well. This is an especially delicate task for us because our parent organization, the National Endowment for Democracy, is a reso- lutely bipartisan institution that seeks to steer clear of the controversies of U.S. domestic politics. We hope we have succeeded in avoiding the pitfalls of partisanship; but in an era when the trends that are weakening liberal democracy are increasingly global, an editorial version of “Ameri- can isolationism” no longer seemed a defensible policy. -

Successes and Failures in the Enactment of Humanitarian Intervention During the Obama Administration
“THE ROAD TO HELL AND BACK”: SUCCESSES AND FAILURES IN THE ENACTMENT OF HUMANITARIAN INTERVENTION DURING THE OBAMA ADMINISTRATION A Thesis submitted to the FaCulty of the Graduate SChool of Arts and SCiences of Georgetown University in partial fulfillment of the requirements for the degree of Master of Arts in ConfliCt Resolution By Justine T. Robinson, B.A. Washington, DC DeCember 10, 2020 Copyright 2020 by Justine T. Robinson All Rights Reserved ii “THE ROAD TO HELL AND BACK”: SUCCESSES AND FAILURES IN THE ENACTMENT OF HUMANITARIAN INTERVENTION DURING THE OBAMA ADMINISTRATION Justine T. Robinson, M.A. Thesis Advisor: Andrew Bennett, Ph.D. ABSTRACT This thesis examines how United States presidential administrations change over time in their poliCies on humanitarian intervention. More speCifiCally, how and why do AmeriCan presidential administrations (and the offiCials in those administrations) fail in some cases and sucCeed in others in enaCting ConfliCt resolution and genocide preventative measures? This thesis will focus on why offiCials in the two Obama administration sometimes used ambitious means of humanitarian intervention to prevent or mitigate genocide and other mass atrocities, as in the Cases of Libya and the Yazidis in Iraq, and sometimes took only limited steps to aChieve humanitarian goals, as in the case of the Syrian Civil War and Syrian refugees. This thesis is partiCularly interested in cases where earlier Obama administration aCtions and outComes forced the president and his advisors to rethink their approaCh to potential humanitarian intervention cases. The central hypothesis of this thesis is that poliCy changes on humanitarian intervention over time within U.S. -

P40 Layout 1
Egyptian female cyclists pedal for acceptance TUESDAY, JANUARY 27, 2015 36 All the contestants pose on stage during the Miss Universe pageant in Miami. (Inset) Miss Colombia Paulina Vega is crowned Miss Universe 2014.— AP/AFP photos Colombia’s Paulina Vega wins Miss Universe title olombia’s Paulina Vega was Venezuelan Gabriela Isler. She edged the map. Cuban soap opera star William Levy and crowned Miss Universe Sunday, out first runner-up, Nia Sanchez from the “We are persevering people, despite Philippine boxing great Manny Cbeating out contenders from the United States, hugging her as the win all the obstacles, we keep fighting for Pacquiao. The event is actually the 2014 United States, Ukraine, Jamaica and The was announced. what we want to achieve. After years of Miss Universe pageant. The competition Netherlands at the world’s top beauty London-born Vega dedicated her title difficulty, we are leading in several areas was scheduled to take place between pageant in Florida. The 22-year-old mod- to Colombia and to all her supporters. on the world stage,” she said earlier dur- the Golden Globes and the Super Bowl el and business student triumphed over “We are proud, this is a triumph, not only ing the question round. Colombian to try to get a bigger television audi- 87 other women from around the world, personal, but for all those 47 million President Juan Manuel Santos applaud- ence. and is only the second beauty queen Colombians who were dreaming with ed her, praising the brown-haired beau- The contest, owned by billionaire from Colombia to take home the prize. -

Crowdstrike Global Threat Intel Report
TWO THOUSAND FOURTEEN CROWDSTRIKE GLOBAL THREAT INTEL REPORT www.crowdstrike.com TWO THOUSAND FOURTEEN CROWDSTRIKE GLOBAL THREAT INTEL REPORT INTRODUCTION .........................................................................4 Table of KEY FINDINGS ............................................................................7 STATE OF THE UNION .............................................................9 Contents: NOTABLE ACTIVITY ............................................................... 13 Criminal ................................................................................ 13 State ...................................................................................... 19 Hacktivist/Nationalist ............................................................. 25 2014 Zero-Day Activity ........................................................... 34 Event-Driven Operations ......................................................... 39 KNOW THE ADVERSARY ....................................................49 Effect of Public Reporting on Adversary Activity ........................ 49 HURRICANE PANDA .................................................................50 GOTHIC PANDA ..........................................................................55 Overview of Russian Threat Actors ........................................... 57 2015 PREDICTIONS.................................................................61 CONCLUSION ........................................................................... 73 2 Introduction Intelligence